1. Executive Summary
A. Fingerprinting
- MD5:
459aad8cc95d9fe2bd1d3199966289f7 - SHA256:
eb22d542b3b6e69a98801ff7843fa6981b13ca8628a5382cfdc0f713cdb72cba - VirusTotal Report:
https://www.virustotal.com/gui/file/eb22d542b3b6e69a98801ff7843fa6981b13ca8628a5382cfdc0f713cdb72cba
B. Classification
Infostealer, used to harvest stored credentials and session objects from browsers installed on the machine.
C. Behavioral Summary
The malware is a PyInstaller packed executable, with slight obfuscation. When the sample is executed, it extracts the packed Python bytecode, and required libraries into a temporary folder. It then proceeds to spawn a child process by executing itself again, sets/adds the temporary folder into its DLL directories, unpacks and unmarshall the Python bytecode on the fly in the memory. After all required functions and libraries are loaded into the memory, it then looks for stored credentials and session data from commonly known web browser folders, collects the credentials, and exfiltrates the stolen data over secure HTTPS connection to a legitimate web application’s (Discord) webhook. After successful execution of the child, it deletes all the temporary files created by the parent process and both processes exit.
2. Static Analysis
Strings
- After looking at the strings, the executable appears to be a pyInstaller packed binary.


- The Python version used appears to be version 3.9

Advanced Static Analysis
- As demonstrated in Fortiguard Labs Threat Research Blog, this can be extracted and then decompiled on a linux machine
- The first challenge is encountered as there is no
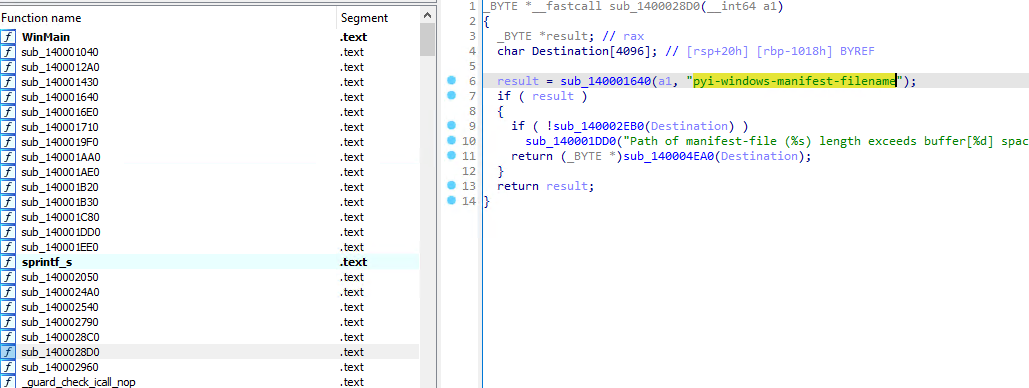
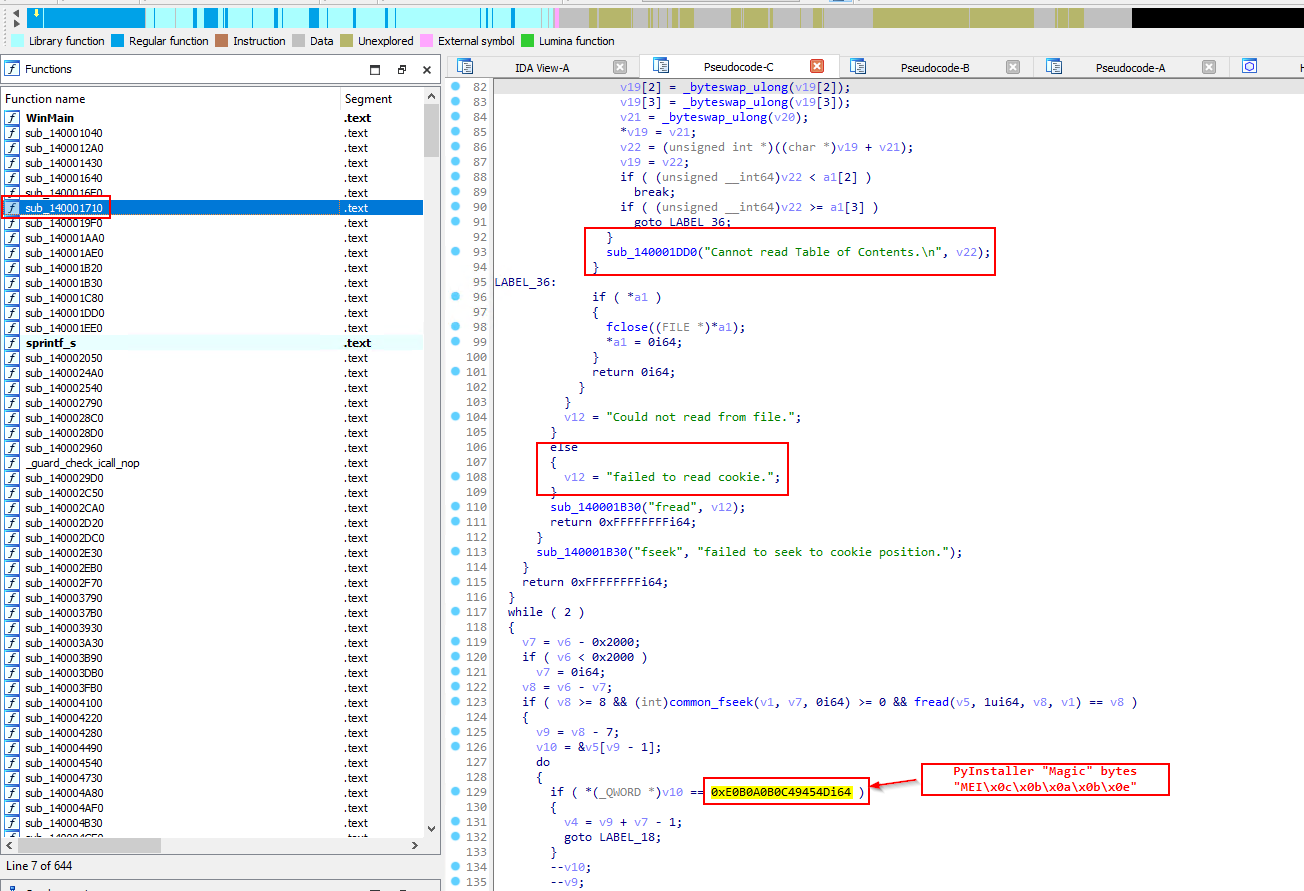
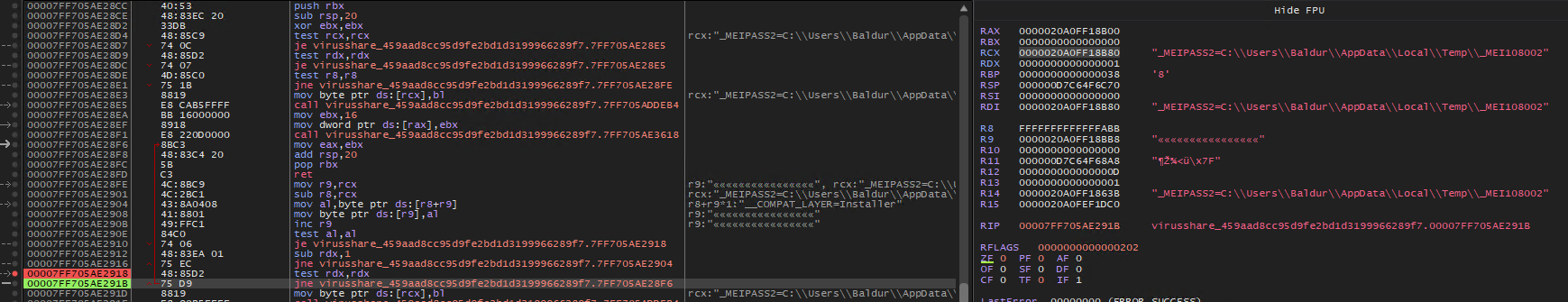
pydatasection in the binary, hinting towards possible obfuscation. This was later tackled by running a dynamic analysis and observing the files which were dropped by the binary. - There is an unpacker built into the malware. which unpacks the PyInstaller file itself. Following picture depicts the difference between a standard pyinstaller app (
app_1) and this malware.
- The function
sub_14001710()is the unpacker from following indicators
3. Dynamic Analysis
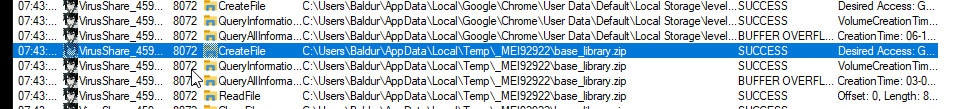
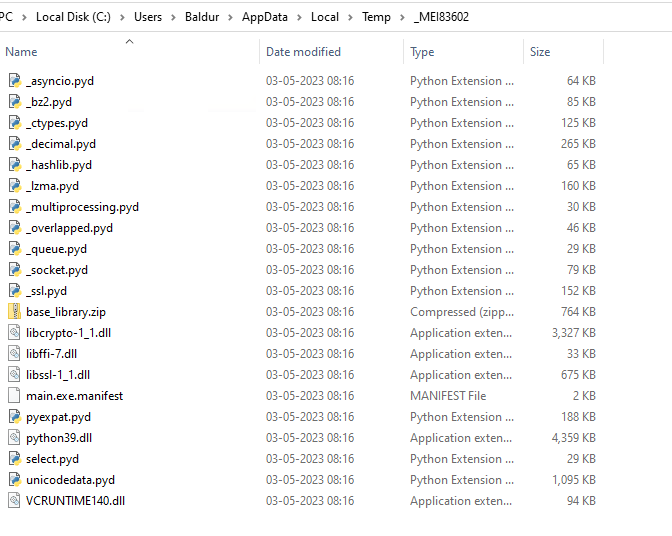
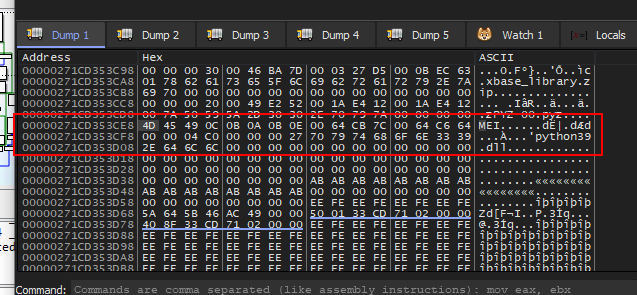
- On execution, an archive was created in
C:\Users\<username>\AppData\LocalTemp\_MEI<5_digits>\base_library.zip
- The executable deleted all the files prior to exiting.

- To prevent this from happening, the binary was loaded into the debugger and breakpoints were set after observing the execution multiple times.

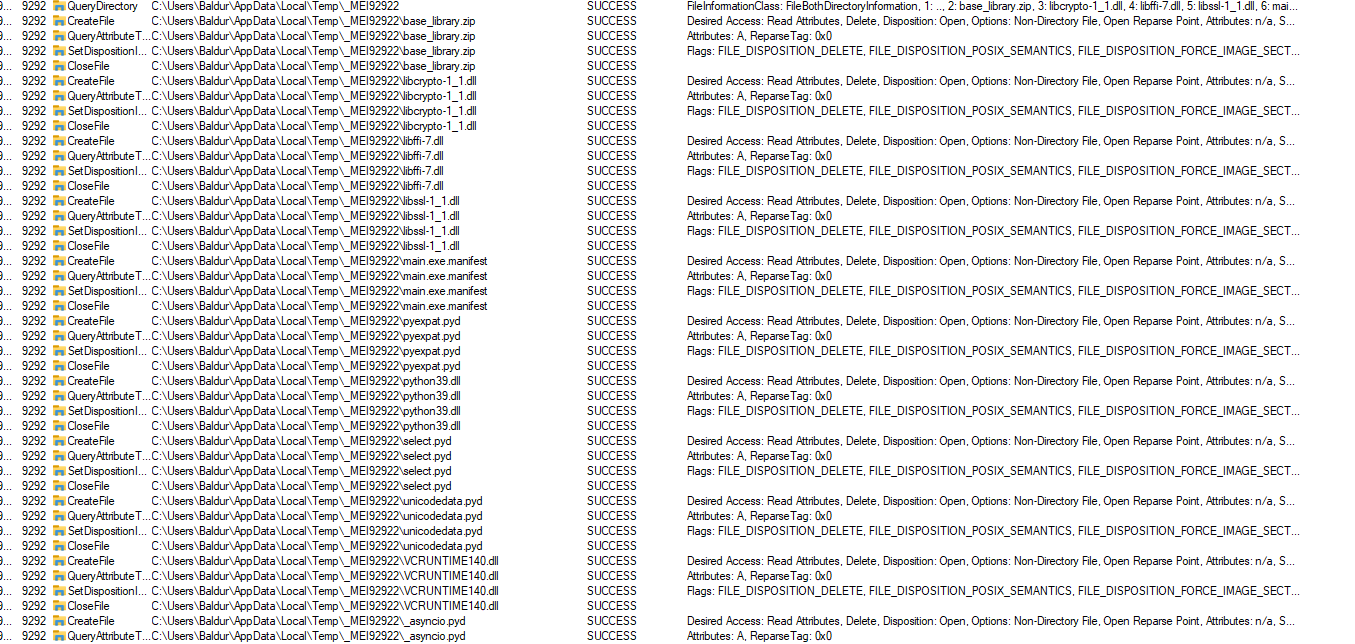
- On examining the directory, multiple python bytecode files were found.

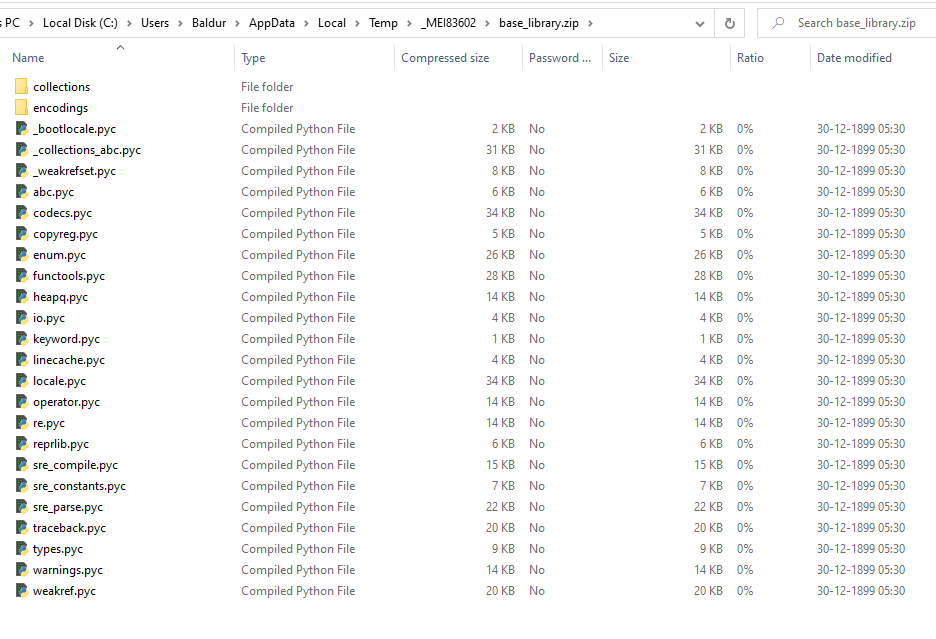
- Contents of
base_library.zip:
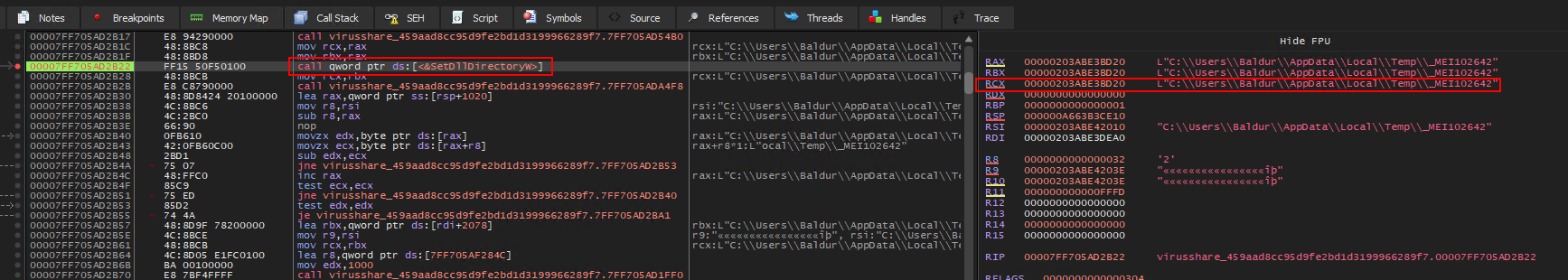
- The application spawns a child process by calling itself and adding the temporary directory to DLL directories using
SetDllDirectory. Debugging the child process was quite difficult since manual attaching to the process had to be done really fast, as the child exited very quickly. Thankfully, DbgChild exist to ease this process. It is a stand alone tool for debugging child processes (auto attach). DbgChild can be used in conjunction with a plugin for a debugger. Currently DbgChild supports a plugin for the x86/x64 x64dbg debugger.
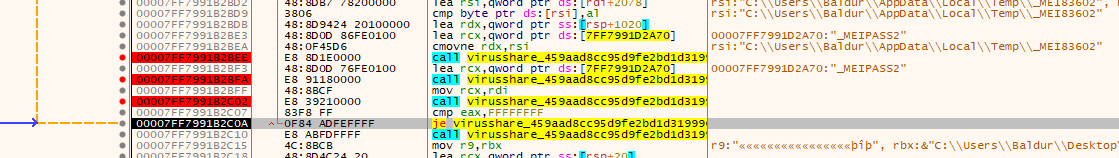
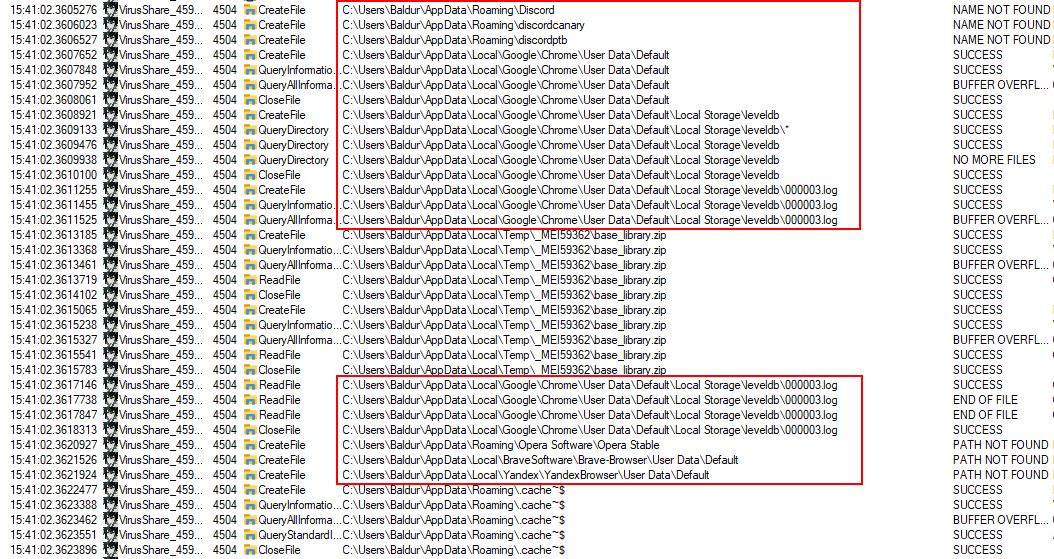
- The child process identifies the PyInstaller package in the memory


- After it loaded all the required functions and libraries in the memory, it looked for data to collect in the common web browser directories.

Network Based Indicators
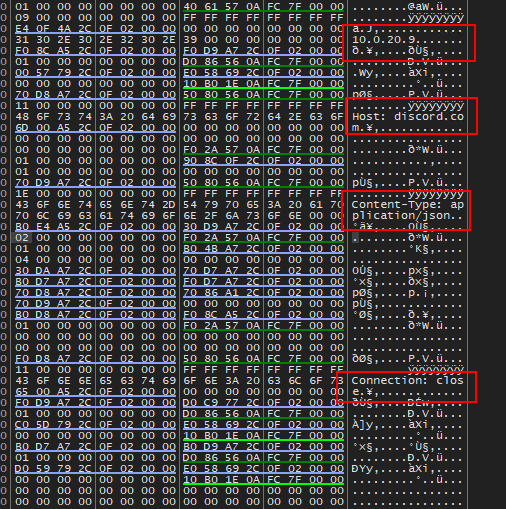
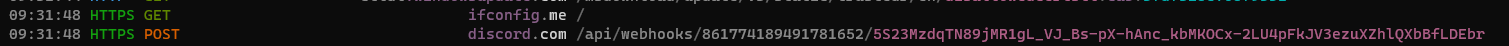
getaddrinfowas invoked to querydiscord:443

- Traffic was intercepted and observed using
MITMProxy
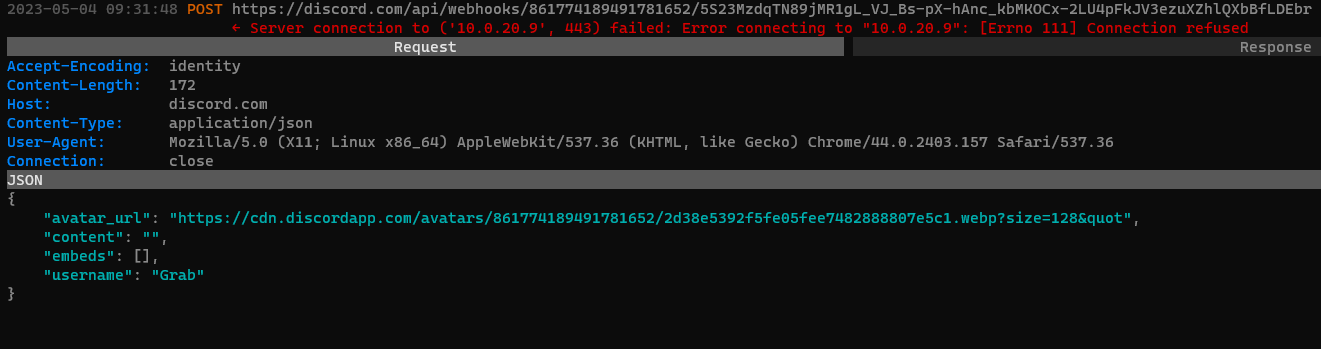
- Contents of the POST request to the Discord URL:

Files Dropped
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_asyncio.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\base_library.zip
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_bz2.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_ctypes.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_decimal.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_hashlib.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\libcrypto-1_1.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\libffi-7.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\libssl-1_1.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_lzma.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\main.exe.manifest
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_multiprocessing.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_overlapped.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\pyexpat.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\python39.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_queue.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\select.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_socket.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\_ssl.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\unicodedata.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI25242\VCRUNTIME140.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_asyncio.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\base_library.zip
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_bz2.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_ctypes.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_decimal.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_hashlib.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\libcrypto-1_1.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\libffi-7.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\libssl-1_1.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_lzma.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\main.exe.manifest
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_multiprocessing.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_overlapped.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\pyexpat.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\python39.dll
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_queue.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\select.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_socket.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\_ssl.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\unicodedata.pyd
C:\Users\Baldur\AppData\Local\Temp\_MEI82282\VCRUNTIME140.dll
4. YARA Rules and IOCs
| Type | Value |
|---|---|
| URL | hxxps[:]//discord[.]com/api/webhooks/861774189491781652/5S23MzdqTN89jMR1gL_VJ_Bs-pX-hAnc_kbMKOCx-2LU4pFkJV3ezuXZhlQXbBfLDEbr |
| Domain | ifconfig[.]me |
原文始发于Mayank Malik:Malware Analysis and Triage : DeathNote Infostealer