Executive summary: 摘要:
- Deep Instinct’s Threat Research team has identified a new campaign from the “MuddyWater” group
Deep Instinct 的威胁研究团队已经确定了来自“MuddyWater”组的新活动 - The campaign has been observed attacking two Israeli targets
据观察,该战役袭击了两个以色列目标 - The campaign exhibits updated TTPs to previously reported MuddyWater activity
该活动展示了先前报告的 MuddyWater 活动的更新的 TTP
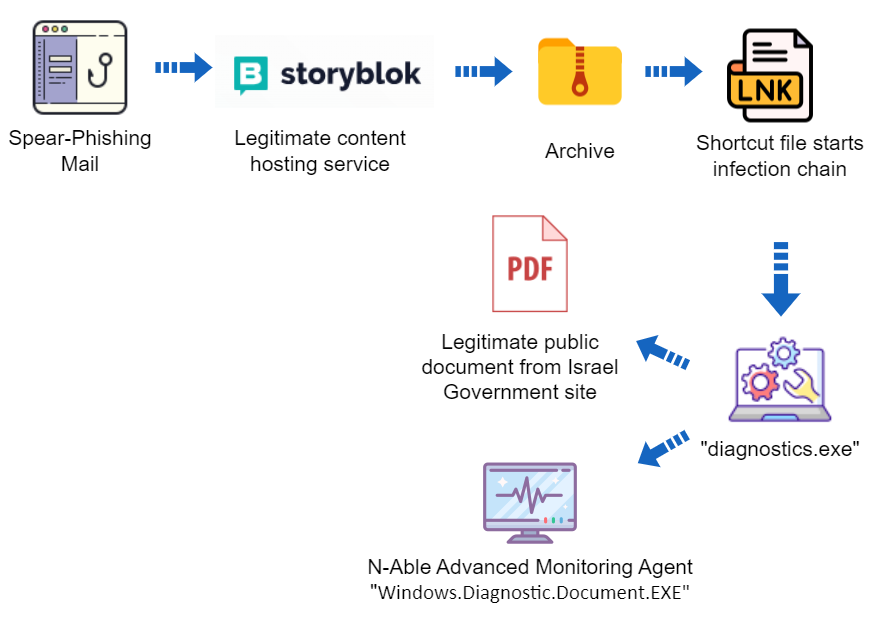
图 1:广告系列概览
Introduction 介绍
Previous research showed that MuddyWater has sent spear-phishing emails, starting back in 2020, with direct links, as well as PDF, RTF, and HTML attachments containing links to archives hosted on various file-sharing platforms.
先前的研究表明,MuddyWater 早在 2020 年就发送了鱼叉式网络钓鱼电子邮件,其中包含直接链接,以及 PDF、RTF 和 HTML 附件,其中包含指向托管在各种文件共享平台上的档案的链接。
Those archives contained installers for various legitimate remote administration tools.
这些存档包含各种合法远程管理工具的安装程序。
Before launching the new campaign during the Israel-Hamas war, MuddyWater reused previously known remote administration tools, utilizing a new file-sharing service called “Storyblok.”
在以色列-哈马斯战争期间发起新活动之前,MuddyWater 利用名为“Storyblok”的新文件共享服务,重复使用了以前已知的远程管理工具。
On October 30th Deep Instinct identified two archives hosted on “Storyblok” containing a new multi-stage infection vector. It contains hidden files, an LNK file that initiates the infection, and an executable file designed to unhide a decoy document while executing Advanced Monitoring Agent, a remote administration tool.
10 月 30 日,Deep Instinct 确定了托管在“Storyblok”上的两个档案,其中包含一个新的多阶段感染载体。它包含隐藏文件,启动感染的LNK文件,以及旨在在执行高级监视代理(远程管理工具)时取消隐藏诱饵文档的可执行文件。
This is the first public report about MuddyWater utilizing this remote administration tool.
这是第一份关于MuddyWater使用这种远程管理工具的公开报告。
The Multi-stage Social Engineering Campaign
多阶段社会工程运动
While Deep Instinct could not verify the spreading mechanism of the new campaign, it most likely starts with a spear-phishing email, similar to previous campaigns.
虽然 Deep Instinct 无法验证新活动的传播机制,但它很可能从鱼叉式网络钓鱼电子邮件开始,类似于以前的活动。
The content of the email lures the victim into downloading an archive hosted at “a.storyblok[.]com”
电子邮件的内容引诱受害者下载托管在“a.storyblok[.]com”
In this analysis, we examine the “defense-video.zip” file.
在此分析中,我们检查“defense-video.zip”文件。
When the archive is extracted, several folders must be navigated until a LNK shortcut, which looks like another folder named “Attachments,” is found:
提取存档时,必须导航多个文件夹,直到找到 LNK 快捷方式,该快捷方式类似于另一个名为“附件”的文件夹:
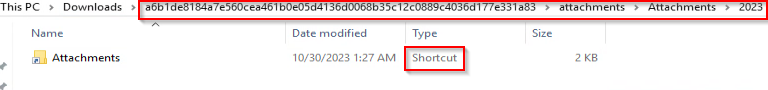
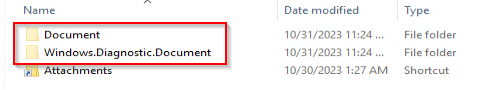
However, there are additional hidden folders and files extracted from the archive:
但是,从存档中提取了其他隐藏文件夹和文件:
When the victim opens the LNK file, the infection chain starts.
当受害者打开 LNK 文件时,感染链开始。
By examining the LNK file, we can see that it executes an executable from one of the hidden directories:
通过检查 LNK 文件,我们可以看到它从其中一个隐藏目录执行可执行文件:
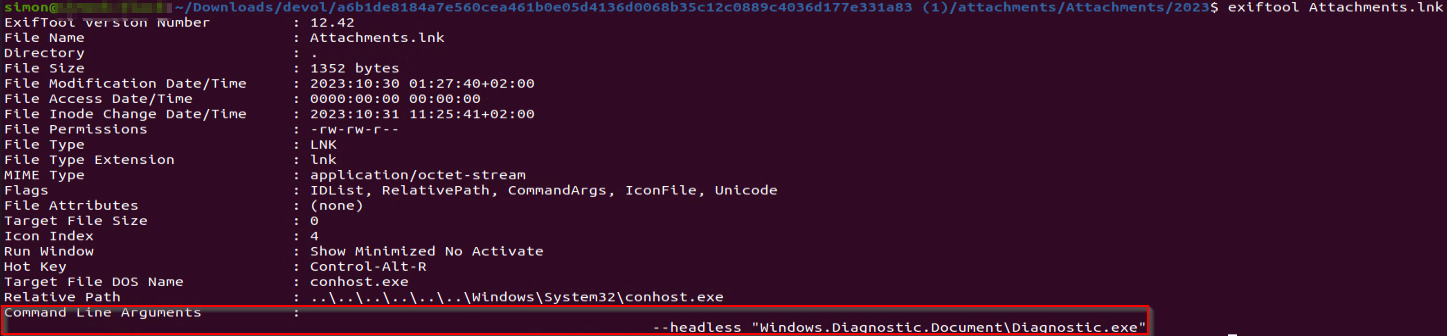
图 4:LNK 命令行参数
The file “Diagnostic.exe” has been used in both archives Deep Instinct observed. The purpose of this file is to execute another executable called “Windows.Diagnostic.Document.EXE,” which is located in the hidden directory named “.end” under a “Windows.Diagnostic.Document” hidden directory.
文件“Diagnostic.exe”已在两个档案中使用,Deep Instinct观察到。此文件的用途是执行另一个名为“Windows.Diagnostic.Document.EXE”的可执行文件,该可执行文件位于“Windows.Diagnostic.Document”隐藏目录下名为“.end”的隐藏目录中。
The file named “Windows.Diagnostic.Document.EXE” is a signed, legitimate installer for “Advanced Monitoring Agent.”
名为“Windows.Diagnostic.Document.EXE”的文件是“高级监视代理”的已签名合法安装程序。
In addition to executing the remote administration tool, “Diagnostic.exe” also opens a new Windows Explorer window of the hidden “Document” folder. This is done to fool the victim that opened the LNK file into thinking that it was indeed a folder.
除了执行远程管理工具外,“Diagnostic.exe”还会打开隐藏的“文档”文件夹的新 Windows 资源管理器窗口。这样做是为了欺骗打开 LNK 文件的受害者,让他们认为它确实是一个文件夹。
The decoy document is an official memo from the Israeli Civil Service Commission, which can be publicly downloaded from their website.
诱饵文件是以色列公务员制度委员会的官方备忘录,可以从他们的网站上公开下载。
The memo describes what to do in case a government worker expresses opinions against the Israeli state on social networks:
该备忘录描述了如果政府工作人员在社交网络上表达反对以色列国家的意见该怎么办:

Conclusion 结论
MuddyWater continues to attack Israeli targets in various ongoing campaigns.
MuddyWater继续在各种正在进行的战役中攻击以色列目标。
In this campaign, MuddyWater employs updated TTPs. These include a new public hosting service, employing a LNK file to initiate the infection, and utilizing intermediate malware that mimics the opening of a directory while executing a new remote administration tool.
在这次活动中,MuddyWater 采用了更新的 TTP。其中包括新的公共托管服务,使用LNK文件来启动感染,以及利用中间恶意软件在执行新的远程管理工具时模仿目录的打开。
After the victim has been infected, the MuddyWater operator will connect to the infected host using the legitimate remote administration tool and will start doing reconnaissance on the target.
受害者被感染后,MuddyWater 操作员将使用合法的远程管理工具连接到受感染的主机,并开始对目标进行侦察。
After the reconnaissance phase, the operator will likely execute PowerShell code which will cause the infected host to beacon to a custom C2 server.
在侦测阶段之后,操作员可能会执行 PowerShell 代码,这将导致受感染的主机信标到自定义 C2 服务器。
MuddyWater has used PhonyC2 in the past. However, Deep Instinct recently observed MuddyWater using a new C2 framework named MuddyC2Go – a detailed blog will be published soon, stay tuned.
MuddyWater 过去曾使用过 PhonyC2。然而,Deep Instinct 最近使用一个名为 MuddyC2Go 的新 C2 框架观察了 MuddyWater——详细的博客将很快发布,敬请期待。
IOCs: 国际奥委会:
File 文件
|
MD5 |
Description 描述 |
|---|---|
|
37c3f5b3c814e2c014abc1210e8e69a2 |
Archive containing Atera Agent |
|
16923d827a440161217fb66a04e8b40a |
Atera Agent Installer Atera 代理安装程序 |
|
7568062ad4b22963f3930205d1a14df7 |
Archive containing Atera Agent |
|
39eea24572c14910b67242a16e24b768 |
Archive containing Atera Agent |
|
2e09e53135376258a03b7d793706b70f |
Atera Agent Installer Atera 代理安装程序 |
|
1f0b9aed4b2c8d958a9b396852a62c9d |
Archive containing SimpleHelp |
|
065f0871b6025b8e61f35a188bca1d5c |
SimpleHelp Installer SimpleHelp 安装程序 |
|
146cc3a1a68be349e70b79f9115c496b |
defense-video.zip 防御视频.zip |
|
dd247ccd7cc3a13e1c72bb01cf3a816d |
Attachments.lnk 附件.lnk |
|
8d2199fa11c6a8d95c1c2b4add70373a |
Diagnostic.exe 诊断 .exe |
|
04afff1465a223a806774104b652a4f0 |
Advanced Monitoring Agent Installer |
|
6167f03c8b2734c20eb02d406d3ba651 |
Decoy Document (defense-video.zip) |
|
e8f3ecc0456fcbbb029b1c27dc1faad0 |
attachments.zip 附件 .zip |
|
952cc4e278051e349e870aa80babc755 |
Decoy Document (attachments.zip) |
Network 网络
|
IP or URL IP 或 URL |
Description 描述 |
|---|---|
|
ws.onehub[.]com/files/7f9dxtt6 |
URL to Archive of Atera Agent |
|
a.storyblok[.]com/f/253959/x/b92ea48421/form.zip |
URL to Archive of Atera Agent |
|
a.storyblok[.]com/f/255988/x/5e0186f61d/questionnaire.zip |
URL to Archive of Atera Agent |
|
a.storyblok[.]com/f/259791/x/94f59e378f/questionnaire.zip |
URL to Archive of SimpleHelp |
|
146.70.149[.]61 |
MuddyWater’s SimpleHelp server |
|
146.70.124[.]102 |
Suspected MuddyWater’s SimpleHelp server |
|
37.120.237[.]204 |
Suspected MuddyWater’s SimpleHelp server |
|
37.120.237[.]248 |
Suspected MuddyWater’s SimpleHelp server |
|
a.storyblok[.]com/f/259837/x/21e6a04837/defense-video.zip |
URL to Archive of Advanced Monitoring Agent |
|
a.storyblok[.]com/f/259791/x/91e2f5fa2f/attachments.zip |
URL to Archive of Advanced Monitoring Agent |
Additional IOCs regarding MuddyWater can be found in our GitHub page:
有关 MuddyWater 的其他 IOC 可以在我们的 GitHub 页面中找到:
https://github.com/deepinstinct/Israel-Cyber-Warfare-Threat-Actors
原文始发于Simon Kenin:MuddyWater eN-Able spear-phishing with new TTPs