You’re out for a stroll and spot a house with its front door wide open. Out of concern, you try to inform the owner about the door. Unexpectedly, the owner snaps back, insisting the door is shut. This is a story about the worst vulnerability disclosure process I’ve ever experienced.
你出去散步,发现一栋房子的前门敞开着。出于关心,你试图将门告知主人。出乎意料的是,店主猛地回击,坚持说门是关着的。这是一个关于我经历过的最糟糕的漏洞披露过程的故事。
The world of vulnerability disclosure and research is really confusing, with lots of different opinions on what’s right or wrong. No matter what you do as a researcher, someone is likely to say you’re doing it wrong.
漏洞披露和研究的世界真的很混乱,对什么是对的,什么是错的,有很多不同的看法。无论你作为研究人员做什么,都可能会有人说你做错了。
All you can do is carefully find your way through the unclear laws. If you discover something, try to handle it responsibly so it doesn’t end up in bad hands. After all, the main goal is to keep people safe, isn’t it?
你所能做的就是小心翼翼地通过不明确的法律找到自己的出路。如果您发现某些东西,请尝试负责任地处理它,以免它落入坏人之手。毕竟,主要目标是确保人们的安全,不是吗?
Vulnerability Discovery 漏洞发现
During a recent security assessment for a client, I had permission to examine all aspects of their online presence. As a part of that I chose to investigate whether they had any exposed S3 buckets or Azure storage accounts that permitted public file listing and access.
在最近对客户进行安全评估时,我被允许检查他们在线状态的各个方面。作为其中的一部分,我选择调查他们是否有任何公开的 S3 存储桶或允许公共文件列表和访问的 Azure 存储帐户。
Luckily for my client, I didn’t come across any buckets linked to them. However, during my investigation, I stumbled upon two buckets belonging to other companies, both loaded with sensitive data.
幸运的是,对于我的客户来说,我没有遇到任何与他们相关的存储桶。然而,在我的调查过程中,我偶然发现了两个属于其他公司的存储桶,都加载了敏感数据。
Vulnerability Disclosure?
漏洞披露?
Knowing about these vulnerabilities, am I now required, even though I have no affiliation with the impacted companies, to report these issues?
知道这些漏洞后,即使我与受影响的公司没有任何关系,我现在是否需要报告这些问题?
A frequent point raised is that reporters shouldn’t even be aware of these issues. However, especially when it comes to this class of vulnerabilities, the counterpoint is that you don’t need any specialized skills or to perform any scanning yourself to find them. Search engines like Gray Hat Warfare make it easy to locate exposed buckets by typing in a few keywords.
经常被提出的一个观点是,记者甚至不应该意识到这些问题。但是,尤其是当涉及到此类漏洞时,与之相反的是,您不需要任何专业技能或自己执行任何扫描即可找到它们。像 Gray Hat Warfare 这样的搜索引擎可以通过输入几个关键字轻松找到暴露的存储桶。
The purpose of this website is to raise awareness on the open buckets issue. – Gray Hat Warfare
本网站的目的是提高人们对开放桶问题的认识。- 灰帽战争
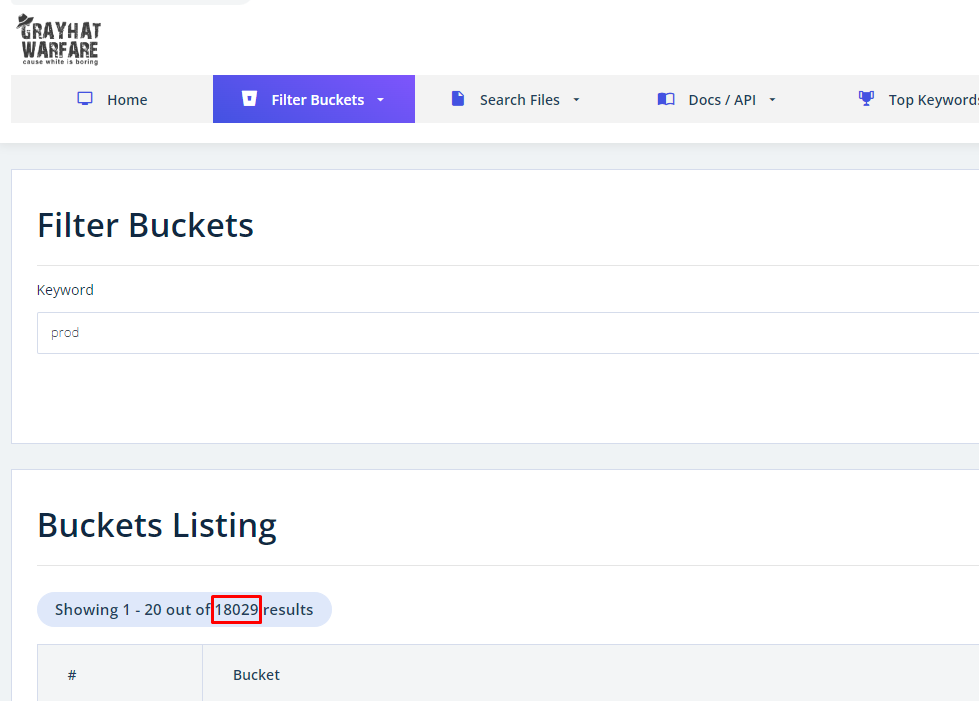
For instance, a simple search for the term ‘prod,’ often short for ‘production,’ turns up 18,029 public buckets. I’m sure none of these buckets contain sensitive information /s.
例如,简单地搜索术语“prod”(通常是“production”的缩写),就会发现 18,029 个公共存储桶。我敢肯定这些存储桶中没有一个包含敏感信息/s。
希望所有这些桶都装满了猫的照片。
Tale 1: The Gold Standard
故事 1:黄金标准
When it comes to encouraging the public to report vulnerabilities to you (and trust me, you want to be in the loop on these matters), there are a few basics to follow:
在鼓励公众向你报告漏洞时(相信我,你想在这些问题上了解情况),有一些基本原则需要遵循:
- At the very least, make a public security contact available.
至少,提供公共安全联系人。
Look into publishing a security.txt file, this is so easy!
考虑发布安全.txt文件,这太容易了! - Confirm that you’ve received any reports, so the person reporting knows they’ve been heard.
确认您已收到任何举报,以便举报人知道他们已被听到。 - Extend a simple ‘thank you.’
说一句简单的“谢谢”。 - Optional Bonus – Offer some form of recognition to the reporter, like adding them to a ‘Hall of Fame’, giving them kudos on a platform, or sending them some swag.
可选奖金 – 为记者提供某种形式的认可,例如将他们添加到“名人堂”,在平台上给予他们荣誉,或向他们发送一些赃物。
With permission from the affected, Tale 1 is about my amazing experience reporting an open bucket to Monash University.
在受影响者的许可下,故事 1 讲述了我向莫纳什大学报告一个打开的桶的惊人经历。
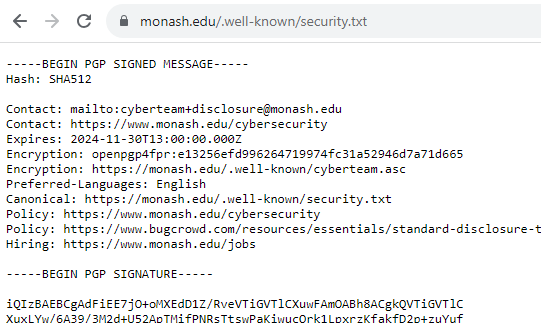
Step 1, they publish a security.txt file. ★★★☆☆
第 1 步,他们发布安全 .txt 文件。★★★☆☆
Step 2 and 3, they acknowledged my report within 24 hours despite me emailing on a Saturday and thanked me! ★★★★★
第 2 步和第 3 步,尽管我在周六发送电子邮件,但他们还是在 24 小时内确认了我的报告并感谢我!★★★★★

Step 4, they invited me to put the report in Bugcrowd so I could get recognized for the report. ★★★★★ BONUS ★
第 4 步,他们邀请我把报告放在 Bugcrowd 中,这样我就可以得到报告的认可。★★★★★ 奖金 ★

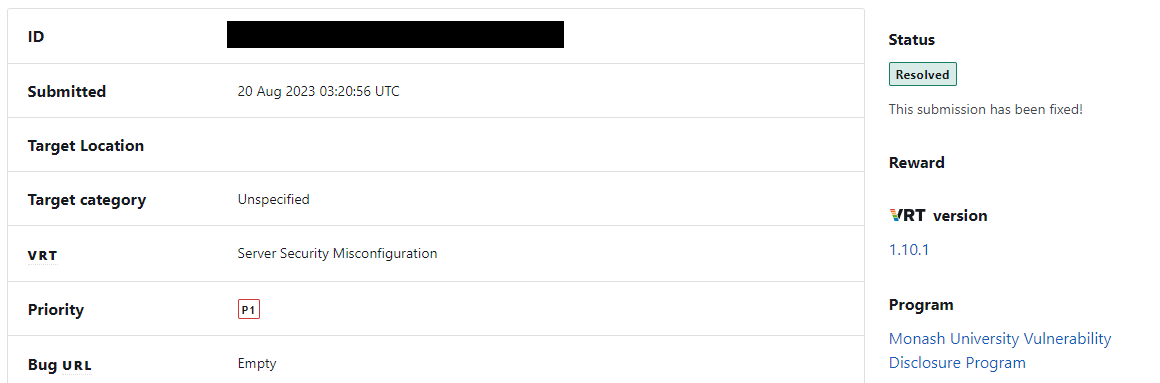
They even kept me in the loop about the issue getting resolved.
他们甚至让我了解问题得到解决的情况。
So easy right? Why can’t all vulnerability disclosures go this well.
这么简单吧?为什么不能所有的漏洞披露都这么顺利。
Tale 2: The Sassy CIO
故事 2:时髦的 CIO
Note: For those who’ve already seen this saga on LinkedIn (follow us), to your potential dismay, I will not be disclosing the company name or those involved. The bucket is still open after all this time.
注意:对于那些已经在LinkedIn上看到这个传奇故事的人(关注我们),令你感到沮丧的是,我不会透露公司名称或相关人员。经过这么长时间,水桶仍然打开。
Proceeding to the next tale, let’s now take a look at the worst vulnerability disclosure process I’ve ever experienced.
继续下一个故事,现在让我们来看看我经历过的最糟糕的漏洞披露过程。
The affected company didn’t provide any dedicated security contact details, leaving me with just their generic contact forms. Given this scenario, I decided to reach out directly to their CEO and CIO on LinkedIn.
受影响的公司没有提供任何专门的安全联系方式,只给我留下了他们的通用联系表格。鉴于这种情况,我决定直接在LinkedIn上联系他们的首席执行官和CIO。
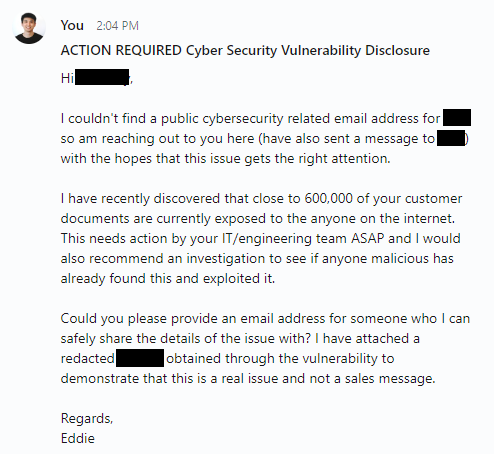
我在 8 月 20 日发给他们的消息。
To my complete astonishment and dismay, I received this response the following morning.
令我完全惊讶和沮丧的是,第二天早上我收到了这个回复。
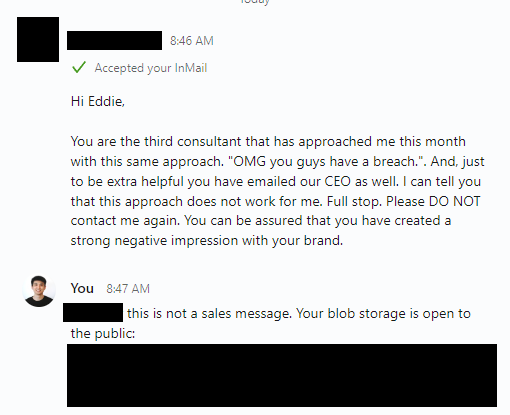
这甚至不是一封电子邮件。
Did the other 2 consultants, just give up? or were they actually sales messages.
其他 2 位顾问就这样放弃了吗?或者他们实际上是销售信息。
I guess they at least get 1 star for acknowledging my report within 24 hours? ★☆☆☆☆
我想他们至少会在 24 小时内确认我的报告而获得 1 颗星?★☆☆☆☆
To add to that amazing response, our sassy CIO also blocked me on LinkedIn. I never heard back from the CEO at all.
为了增加惊人的反应,我们时髦的CIO也在LinkedIn上屏蔽了我。我根本没有收到首席执行官的回复。

Amidst my confusion, I decided to ask my LinkedIn network about what I should do. As I should’ve expected, the internet just wanted to see the world burn. 😂
在我的困惑中,我决定问我的LinkedIn网络我应该做什么。正如我所预料的那样,互联网只是想看到世界燃烧。😂
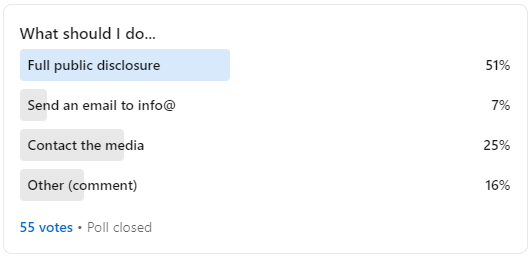
Getting a Third Party Involved
让第三方参与进来
I don’t usually involve a third party, but in this case, it seemed worth a try. The intent was to share enough evidence of the issue with this third party so they could verify it. Then they could approach the impacted company as a trusted intermediary.
我通常不涉及第三方,但在这种情况下,似乎值得一试。目的是与该第三方分享足够的问题证据,以便他们进行验证。然后,他们可以将受影响的公司作为值得信赖的中介机构进行接触。
Let’s list out everyone I tried contacting and what their response was:
让我们列出我尝试联系的每个人以及他们的回应:
- I contacted 6 media outlets.
我联系了 6 家媒体。- Only 1 responded who referred me to the ACSC.
只有 1 人回复将我推荐给 ACSC。
- Only 1 responded who referred me to the ACSC.
- I contacted the ACSC.
我联系了 ACSC。- I called their hotline to ask if they can help me with this, they referred me to submit a ‘general enquiry’ here with feedback type ‘other’.
我打电话给他们的热线,问他们是否可以帮助我解决这个问题,他们建议我在这里提交一个“一般查询”,反馈类型为“其他”。 - The ACSC then referred me to submit a OAIC privacy complaint.
然后,ACSC建议我提交OAIC隐私投诉。
- I called their hotline to ask if they can help me with this, they referred me to submit a ‘general enquiry’ here with feedback type ‘other’.
- I submitted an OAIC privacy complaint.
我提交了OAIC隐私投诉。- I have yet to hear back anything from them (submitted 24 August) apart from an automated acknowledgement of contact.
除了自动确认联系外,我还没有收到他们的任何回复(8月24日提交)。
- I have yet to hear back anything from them (submitted 24 August) apart from an automated acknowledgement of contact.
Side note: OAIC’s automated acknowledgement of contact PDF doesn’t correctly fill out the date. Has this ever been tested by anyone?
旁注:OAIC的联系人自动确认PDF无法正确填写日期。有没有人测试过?
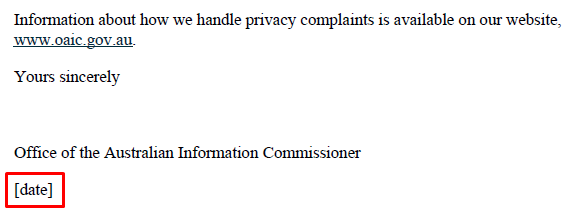
All of that seemed like a dead end.
所有这些似乎都是死胡同。
Troy Hunt – haveibeenpwned
特洛伊·亨特 – haveibeenpwned
As a final option, a friend recommended contacting Troy Hunt. To my relief, he offered to help verify the issue and attempt to elicit a response from the same individuals I had reached out to.
作为最后的选择,一位朋友建议联系特洛伊·亨特。令我松了一口气的是,他主动提出帮助核实这个问题,并试图从我联系过的同一个人那里得到回应。
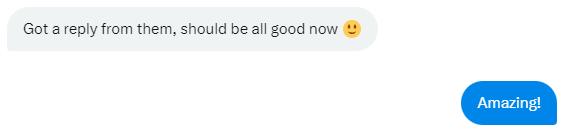
The end. 结束。
Or so I thought. 或者我是这么想的。
As I write this, it is now September 15th. My first message about this was sent to the affected company on August 20th. Their blob storage is still publicly accessible and I’ve moved on to working on other things.
在我写这篇文章的时候,现在是 9 月 15 日。8 月 20 日,我的第一条消息已发送给受影响的公司。他们的 blob 存储仍然可以公开访问,我已开始处理其他事情。
Closing 关闭
In the end, the two tales show two sides of the same coin. The first story serves as an exemplary model of how to successfully handle such disclosures, demonstrating that collaboration with vulnerability researchers can help improve an organisation’s security posture.
最后,这两个故事展示了同一枚硬币的两面。第一个故事是成功处理此类披露的典范,表明与漏洞研究人员的合作有助于改善组织的安全状况。
In contrast, the second story has mostly been a lesson for me in patience and empathy. Maybe our sassy CIO is actually bombarded with sales pitches similar to my message. 🤷
相比之下,第二个故事主要是给我上了一堂耐心和同理心的课。也许我们时髦的首席信息官实际上被类似于我的信息的推销轰炸了。🤷
原文始发于projectblack:A Tale of 2 Vulnerability Disclosures