
Malicious actors have been abusing Ethereum’s ‘Create2’ function to bypass wallet security alerts and poison cryptocurrency addresses, which led to stealing $60,000,000 worth of cryptocurrency from 99,000 people in six months.
恶意行为者一直在滥用以太坊的“Create2”功能来绕过钱包安全警报并毒害加密货币地址,这导致在六个月内从 99,000 人那里窃取了价值 60,000,000 美元的加密货币。
This is reported by Web3 anti-scam specialists at ‘Scam Sniffer,’ who observed several cases of in-the-wild exploitation of the function, in some cases losses incurred by one individual reaching up to $1.6 million.
这是由“Scam Sniffer”的 Web3 反诈骗专家报告的,他们观察到几起野外利用该功能的案例,在某些情况下,一个人造成的损失高达 160 万美元。
Legitimate function 合法功能
Create2 is an opcode in Ethereum, introduced in the ‘Constantinople’ upgrade, that allows creating smart contracts on the blockchain.
Create2 是以太坊中的一个操作码,在“君士坦丁堡”升级中引入,允许在区块链上创建智能合约。
Gamaredon’s LittleDrifter USB malwarespreads beyond Ukraine
Unlike the original Create opcode, which generated new addresses based on the creator’s address and nonce, Create2 allows calculating addresses before the deployment of the contract.
与原始的 Create 操作码不同,Create2 根据创建者的地址和随机数生成新地址,Create2 允许在部署合约之前计算地址。
It’s a powerful tool for Ethereum developers, enabling advanced and flexible contract interactions, parameter-based contract address pre-calculation, deployment flexibility, suitability for off-chain transactions and certain dApps.
对于以太坊开发人员来说,它是一个强大的工具,可实现高级灵活的合约交互、基于参数的合约地址预计算、部署灵活性、链下交易和某些 dApp 的适用性。
Create2 introduced significant benefits, but several security implications and new attack vectors also came along with them.
Create2 带来了显著的好处,但也带来了一些安全隐患和新的攻击媒介。
Create2 opcode abuse Create2 操作码滥用
Scam Sniffer’s report explains that Create2 can be abused to generate fresh contract addresses with no history of malicious/reported transactions, hence bypassing wallet security alerts.
Scam Sniffer 的报告解释说,Create2 可以被滥用来生成没有恶意/报告交易历史的新合约地址,从而绕过钱包安全警报。
When a victim signs a malicious transaction, the attacker deploys a contract at the pre-calculated address and transfers the victim’s assets to it, a non-reversible process.
当受害者签署恶意交易时,攻击者会在预先计算的地址部署合约,并将受害者的资产转移到该地址,这是一个不可逆的过程。
In a recent case analysts observed, a victim lost $927,000 worth of GMX after they were tricked into signing a transfer contract that sent the assets to a pre-computed address.
在最近的一个案例中,分析师观察到,一名受害者在被诱骗签署转让合同后损失了价值 927,000 美元的 GMX,该合同将资产发送到预先计算的地址。
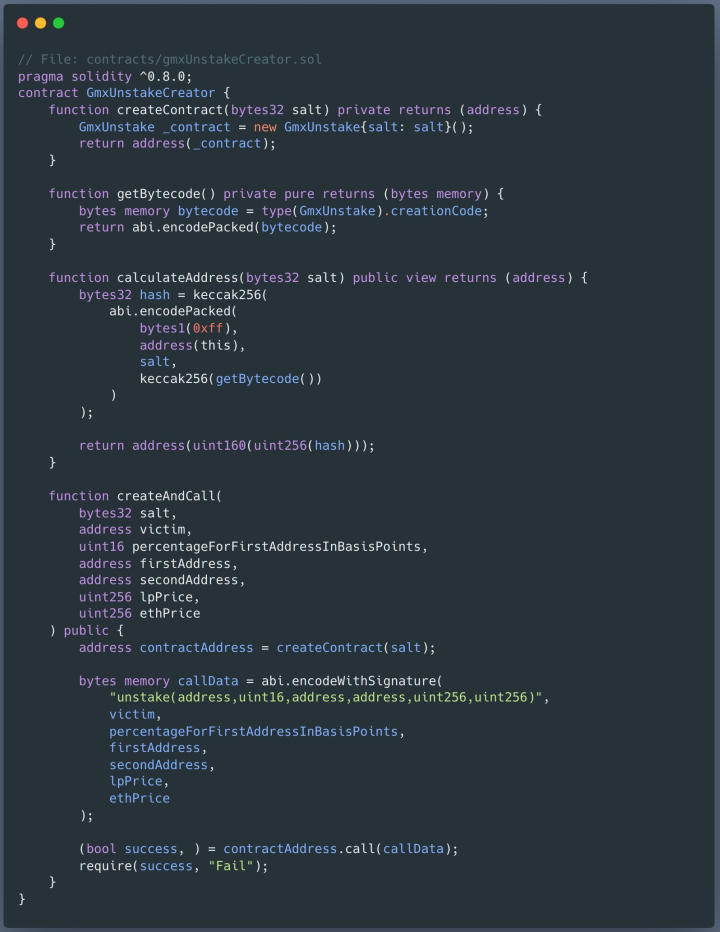
攻击中使用的智能合约(Scam Sniffer)
The second type of Create2 abuse is generating addresses similar to legitimate ones owned by the recipient, thus tricking users into sending assets to the threat actors, thinking they’re sending it to a known address.
第二种类型的 Create2 滥用是生成类似于收件人拥有的合法地址的地址,从而诱骗用户将资产发送给威胁行为者,认为他们正在将其发送到已知地址。
The scheme, which is named ‘address poisoning,’ involves generating a large number of addresses and then picking those that match their specific phishing needs each time to trick their targets.
该方案名为“地址中毒”,涉及生成大量地址,然后每次选择符合其特定网络钓鱼需求的地址来欺骗目标。
Since August 2023, Scam Sniffer has recorded 11 victims losing nearly $3 million, with one of them transferring $1.6 million to an address resembling one they had sent money to recently.
自 2023 年 8 月以来,Scam Sniffer 已记录了 11 名受害者损失近 300 万美元,其中一人将 160 万美元转移到与他们最近汇款的地址相似的地址。
Most of these attacks went under the radar, silently siphoning millions, but some have caught the attention of the community.
这些攻击大多不为人知,默默地吸走了数百万人,但有些已经引起了社区的注意。
At the beginning of the year, MetaMask warned about scammers using freshly-generated addresses that match those used by the victim in recent transactions.
今年年初,MetaMask 警告诈骗者使用新生成的地址,这些地址与受害者在最近交易中使用的地址相匹配。
In the scam, the threat actor may also send the victim a small amount in crypto to register the address in the wallet’s history, thus increasing the chances of the victim making the payment.
在骗局中,威胁行为者还可能向受害者发送少量加密货币以在钱包历史记录中注册地址,从而增加受害者付款的机会。
In early August 2023, a Binance operator mistakenly sent $20 million to scammers who employed the ‘address poisoning’ trick but noticed the error quickly and froze the recipient’s address.
2023 年 8 月初,一名币安运营商错误地向采用“地址中毒”伎俩的骗子发送了 2000 万美元,但很快就注意到了错误并冻结了收件人的地址。
Notably, using lookalike cryptocurrency addresses is a trick seen in clipboard-hijacking malware tools, like the Laplas Clipper, highlighting the method’s effectiveness.
值得注意的是,使用相似的加密货币地址是剪贴板劫持恶意软件工具(如 Laplas Clipper)中的一种技巧,突出了该方法的有效性。
When performing cryptocurrency transactions, it is always recommended to check the recipient’s address thoroughly, and not just the first and last three-four characters, before approving it.
在进行加密货币交易时,始终建议在批准之前彻底检查收件人的地址,而不仅仅是前三个和最后一个三四个字符。
原文始发于Bill Toulas:Ethereum feature abused to steal $60 million from 99K victims
转载请注明:Ethereum feature abused to steal $60 million from 99K victims | CTF导航