File name: 6558073e997da5ca440b5a4b.exe 文件名: 6558073e997da5ca440b5a4b.exe
Size: 13 MB
大小: 13 MB
Type: PE Windows Executable
类型: PE Windows Executable
Mime: application/x-dosexec
MIME: application/x-dosexec
SHA256: 7f731d2502dd39cbc16193ca7e9d147fe158c10236e00c634bb0680e2bfc4bfa
SHA256: 7f731d2502dd39cbc16193ca7e9d147fe158c10236e00c634bb0680e2bfc4bfa
Last VirusTotal Scan: 11/18/2023 00:20:37
最后病毒总扫描: 2023-11-18 00:20:37
Last Sandbox Report: 11/18/2023 00:22:13
上次沙盒报告: 11/18/2023 00:22:13
Malware Family: IPStorm Label: Trojan:Win32/Fsysna
恶意软件家族: IPStorm 标签: Trojan:Win32/Delf.AO32/Delf.AO
0x01 IPStorm 0x01 IPStorm
This post is still a work in progress. I will update it as I make progress with this malware and will remove this comment when I am finished.
这篇文章仍在进行中。当我在这个恶意软件方面取得进展时,我会更新它,并在完成后删除此评论。
Earlier this week, several sites reported that the FBI dismantled the IPStorm botnet. The botnet was shut down on Tuesday, and Sergei Makinin has pleaded guilty to developing and deploying it.
本周早些时候,一些网站报道称,联邦调查局拆除了IPStorm僵尸网络。该僵尸网络于周二关闭,谢尔盖·马基宁(Sergei Makinin)已承认开发和部署该僵尸网络。
What interested me about this article was learning that IPStorm was written in Go, allowing it to easily be compiled for different operating systems. Many sites have already written about the Linux variant of the malware, so I thought I’d take a look at a Windows sample.
这篇文章让我感兴趣的是了解到 IPStorm 是用 Go 编写的,可以很容易地针对不同的操作系统进行编译。许多网站已经写过关于恶意软件的 Linux 变体的文章,所以我想我应该看一下 Windows 示例。
The file details are listed above. All the Windows samples I could find were quite large for malware, over 13 MB. This will make analysis more difficult as the disassembled and decompiled code file will be full of spaghetti code.
上面列出了文件详细信息。我能找到的所有 Windows 样本对于恶意软件来说都非常大,超过 13 MB。这将使分析更加困难,因为反汇编和反编译的代码文件将充满意大利面条代码。
0x02 Static Anaylsis 0x02静态分析
Go files, in general, are usually difficult to analyze as they are statically built and stripped. This results in very large files with hundreds or thousands of unlabeled functions. This sample was no different. Loading the sample in Ghidra revealed nothing but functions labeled as FUN_00XXXX, the default format Ghidra uses with unknown functions.
一般来说,Go 文件通常很难分析,因为它们是静态构建和剥离的。这会导致包含数百或数千个未标记函数的非常大的文件。这个样本也不例外。在 Ghidra 中加载示例时,只显示标记为 的 FUN_00XXXX 函数,这是 Ghidra 用于未知函数的默认格式。
I installed the GolangAnalyzerExtension plugin to make analysis more manageable. This renamed all the random FUN_00XXXX functions to their proper names.
我安装了 GolangAnalyzerExtension 插件,使分析更易于管理。这会将所有随机 FUN_00XXXX 函数重命名为它们的专有名称。
After loading the plugin, we can see the source path used by the malware author. The main file was saved at /Users/brokleg/go/src/storm/storm.go – here we can see why the malware was dubbed IPStorm, a combination of ipfs and storm.
加载插件后,我们可以看到恶意软件作者使用的源路径。主文件保存在 /Users/brokleg/go/src/storm/storm.go – 在这里我们可以看到为什么恶意软件被称为 IPStorm ,ipfs 和 storm 的组合。
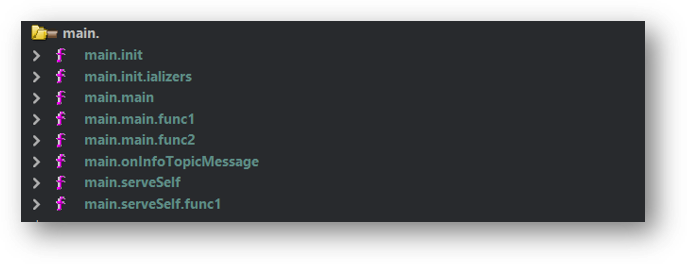
Main Function 主要功能
IPStorm implements its main logic in a package helpfully called main.
IPStorm 在一个名为 main 的包中实现了其主要逻辑。
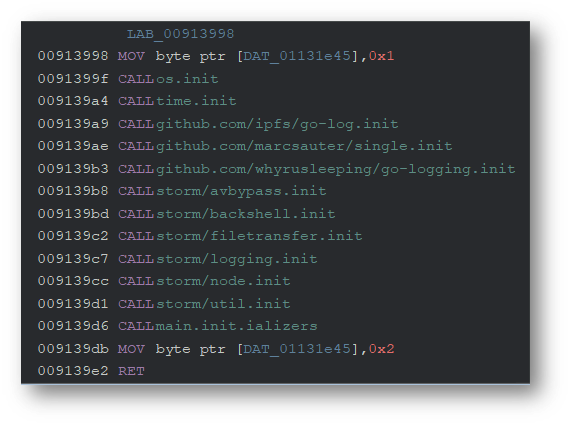
Upon execution, the main.main function starts its logging capability. It then begins calling functions from the storm package to bypass antivirus, set up file transfer, collect system runtime information, and add a new firewall rule using Powershell. The function also calls the single package to ensure that no other IPStorm processes are running.
执行时,该 main.main 函数将启动其日志记录功能。然后,它开始从 storm 包中调用函数,以绕过防病毒、设置文件传输、收集系统运行时信息,并使用 Powershell 添加新的防火墙规则。该函数还调用包以确保 single 没有其他 IPStorm 进程正在运行。
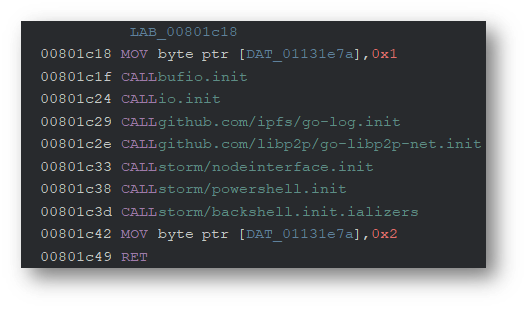
Looking at function main.init, we can see a list of the packages called.
查看 function main.init ,我们可以看到调用的包列表。
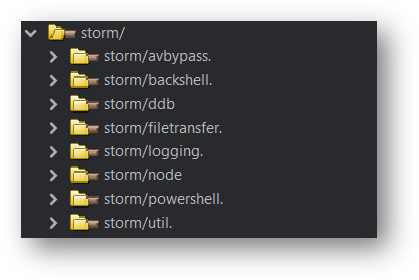
The main package of the malware is helpfully labeled as storm:
恶意软件的主包被标记为 storm :
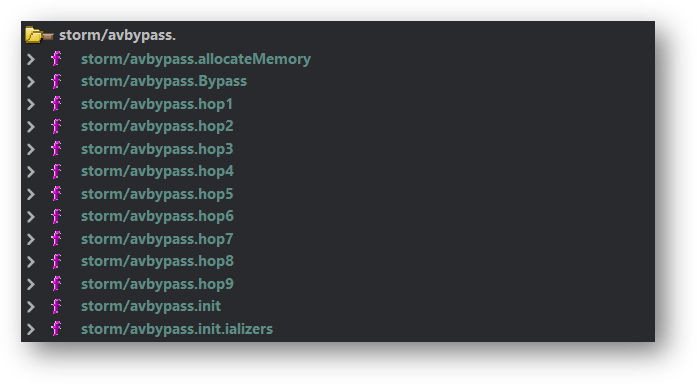
Antivirus Evasion 防病毒规避
The Windows variant contains several functions to bypass any antivirus engines running on the host.
Windows 变体包含多个功能,可绕过主机上运行的任何防病毒引擎。
The malware makes several passes at evasion. In each pass, it calls the util.RandomInt and time.Sleep functions to pause for a random amount of time.
该恶意软件在逃避时进行了多次传递。在每次传递中,它都会调用 util.RandomInt and time.Sleep 函数来暂停随机时间。
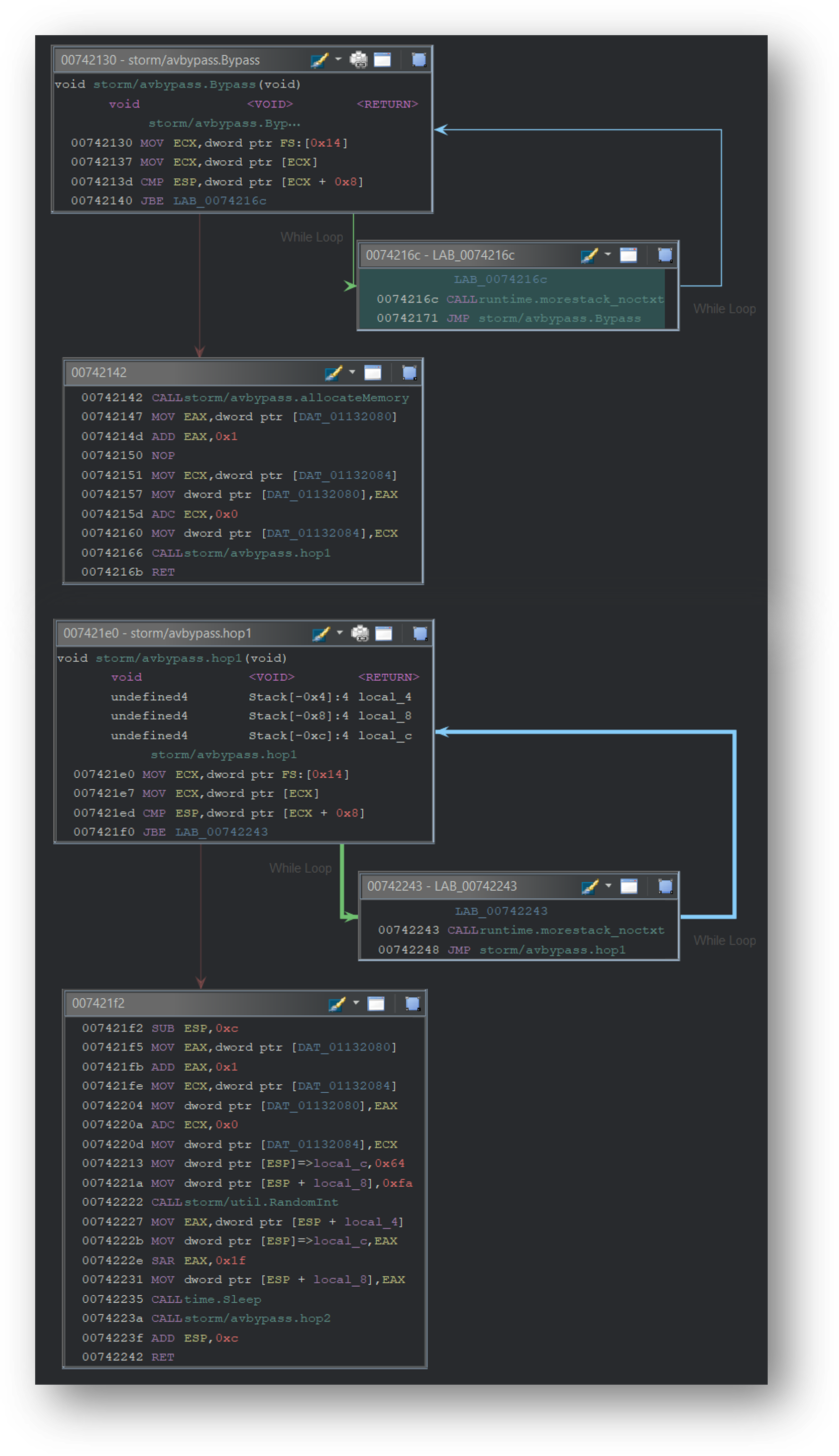
Installation and Persistence
安装和持久性
The storm/util package is responsible for installing the malware and gaining a persistent foothold on the host OS. The malware uses several functions to achieve this goal.
该 storm/util 软件包负责安装恶意软件并在主机操作系统上获得持久的立足点。该恶意软件使用多种功能来实现此目标。
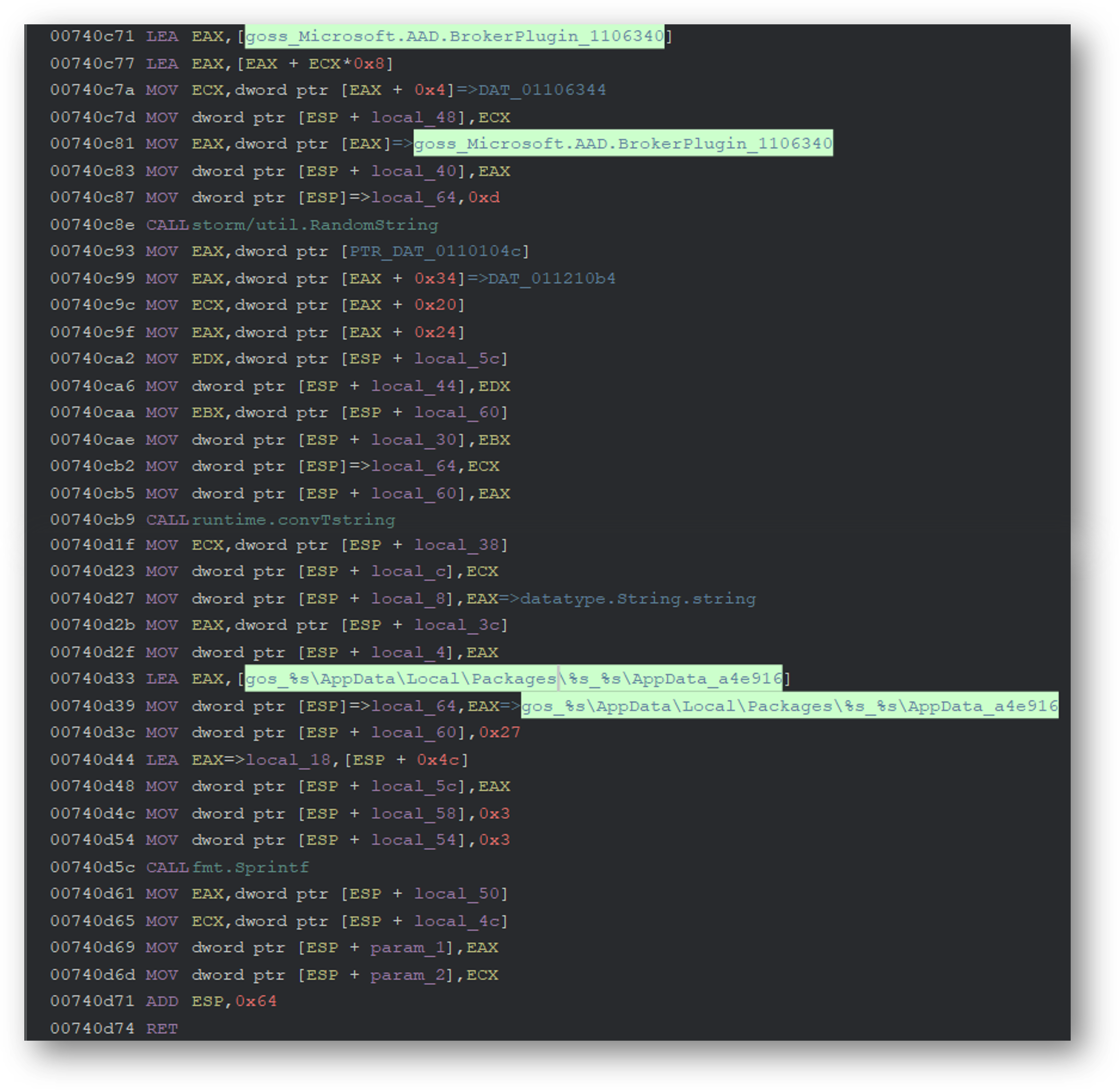
The util package contains code to generate random folder and file names. It also references Microsoft.AAD.BrokerPlugin, which is part of Microsoft OneDrive.
util 包包含用于生成随机文件夹和文件名的代码。它还引用了 Microsoft.AAD.BrokerPlugin ,它是 Microsoft OneDrive 的一部分。
The malware then uses Powershell to access the Windows registry. The code contains logic to access registry keys at HKCU:\Software\Microsoft\FixDrive\Registration and HKCU:\Software\Microsoft\Windows\CurrentVersion\Run. The CurrentVersion\Run key is used by programs to ensure that their executable starts every time the user logs in to Windows.
然后,恶意软件使用 Powershell 访问 Windows 注册表。该代码包含访问 和 处 HKCU:\Software\Microsoft\FixDrive\Registration 的注册表项的逻辑 HKCU:\Software\Microsoft\Windows\CurrentVersion\Run 。程序使用该 CurrentVersion\Run 密钥来确保每次用户登录 Windows 时都启动其可执行文件。
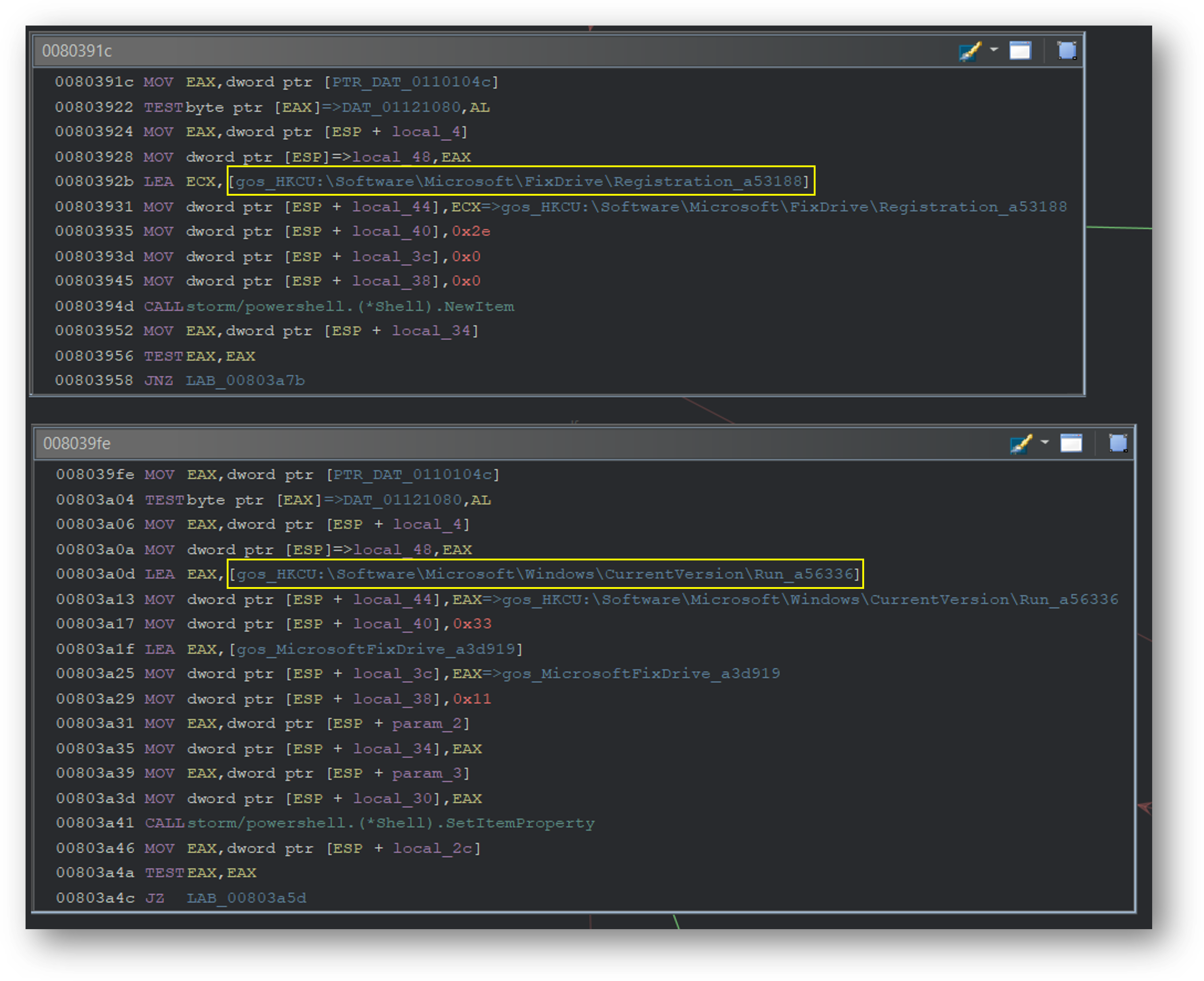
It later confirms it has been added to the registry keys by calling the storm.util.IsPersisted function.
稍后,它通过调用该 storm.util.IsPersisted 函数确认它已添加到注册表项中。
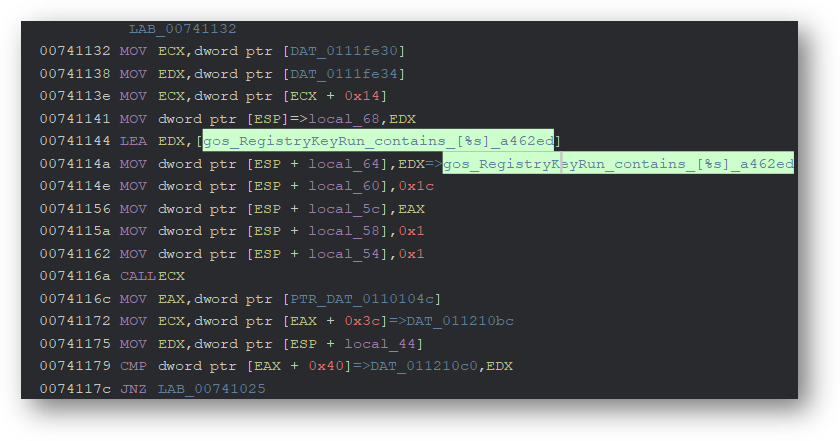
Using Powershell, it creates a new firewall rule for itself to ensure it can communicate with its C2.
使用 Powershell,它为自己创建新的防火墙规则,以确保它可以与其 C2 通信。
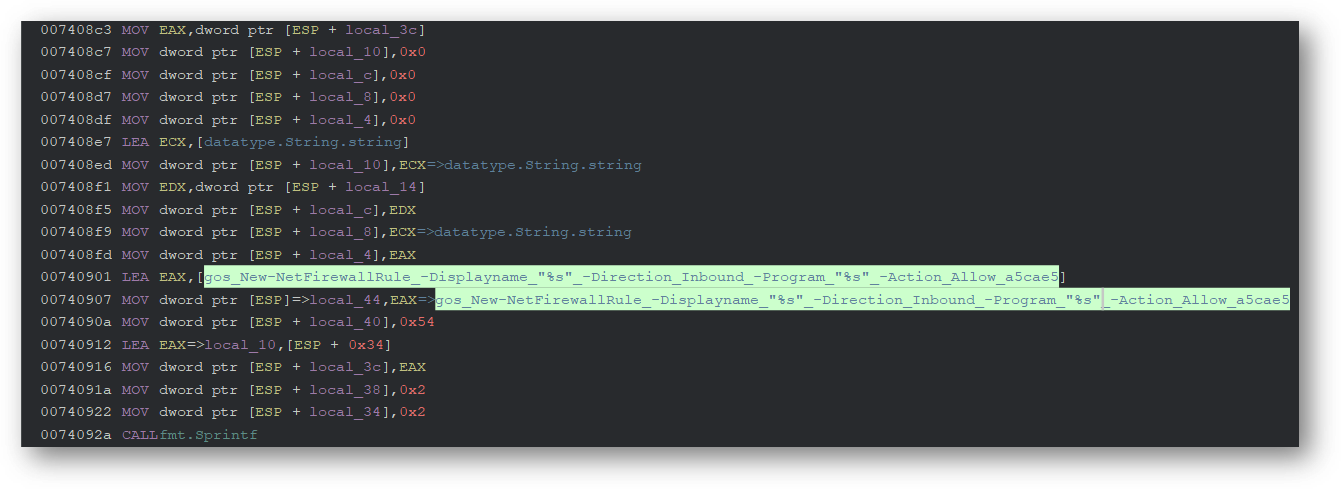
Powershell Feature Powershell 功能
The Windows version of IPStorm uses Powershell to perform various tasks, including creating a reverse shell.
Windows 版本的 IPStorm 使用 Powershell 执行各种任务,包括创建反向 shell。
Reverse Shell 反壳
The backshell package uses Powershell to create a reverse shell on the system.
该 backshell 包使用 Powershell 在系统上创建反向 shell。
The reverse shell capability is the main threat posed by this malware, allowing the attacker to execute system commands on the infected system.
反向 shell 功能是该恶意软件构成的主要威胁,允许攻击者在受感染的系统上执行系统命令。
Other Interesting Functions
其他有趣的功能
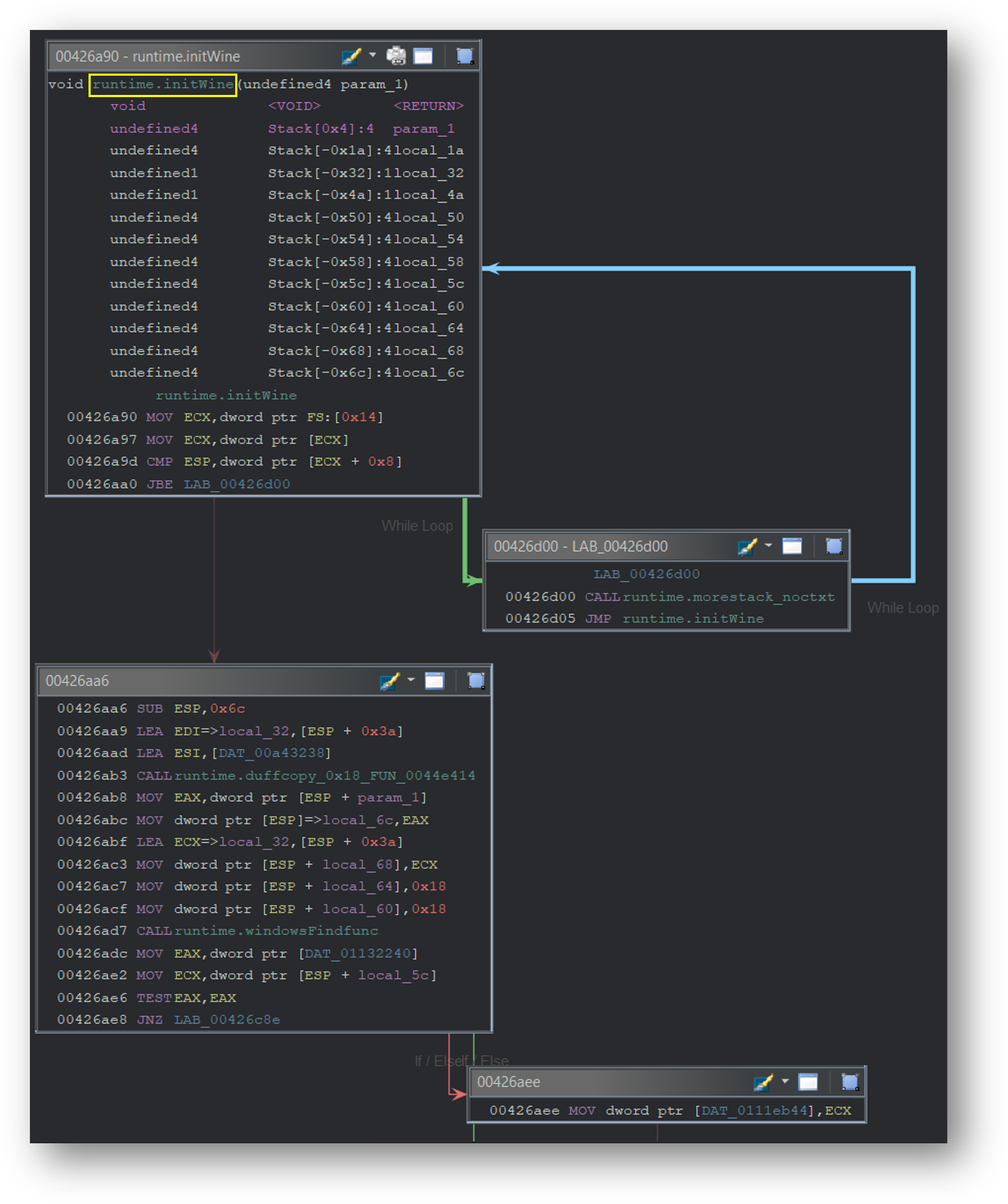
The malware checks if it is running in Wine, a compatibility layer that lets users run Windows programs on Linux.
该恶意软件会检查它是否在 Wine 中运行,Wine 是一个允许用户在 Linux 上运行 Windows 程序的兼容层。
0x03 Dynamic Analysis 0x03动态分析
Execution 执行
To simplify the analysis, I renamed my malware sample ipstorm.exe. After running VMWare Cloak, I took a snapshot and detonated the malware. Immediately upon execution, the process creates a lock file at C:\<USER>\AppData\Local\Temp\n3R1PYfY.lock.
为了简化分析,我重命名了我的恶意软件样本 ipstorm.exe 。运行 VMWare Cloak 后,我拍摄了快照并引爆了恶意软件。执行后,该进程会立即在 处 C:\<USER>\AppData\Local\Temp\n3R1PYfY.lock 创建一个锁定文件。
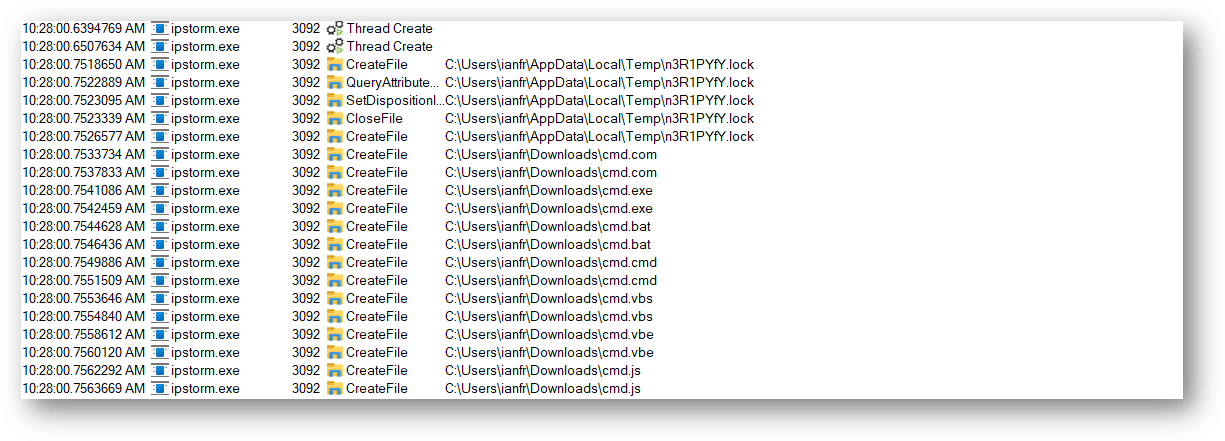
If the malware is started with elevated privileges, it drops the file at C:\Windows\Temp\n3R1PYfY.lock.
如果恶意软件是以提升的权限启动的,则会将文件放在 C:\Windows\Temp\n3R1PYfY.lock 。
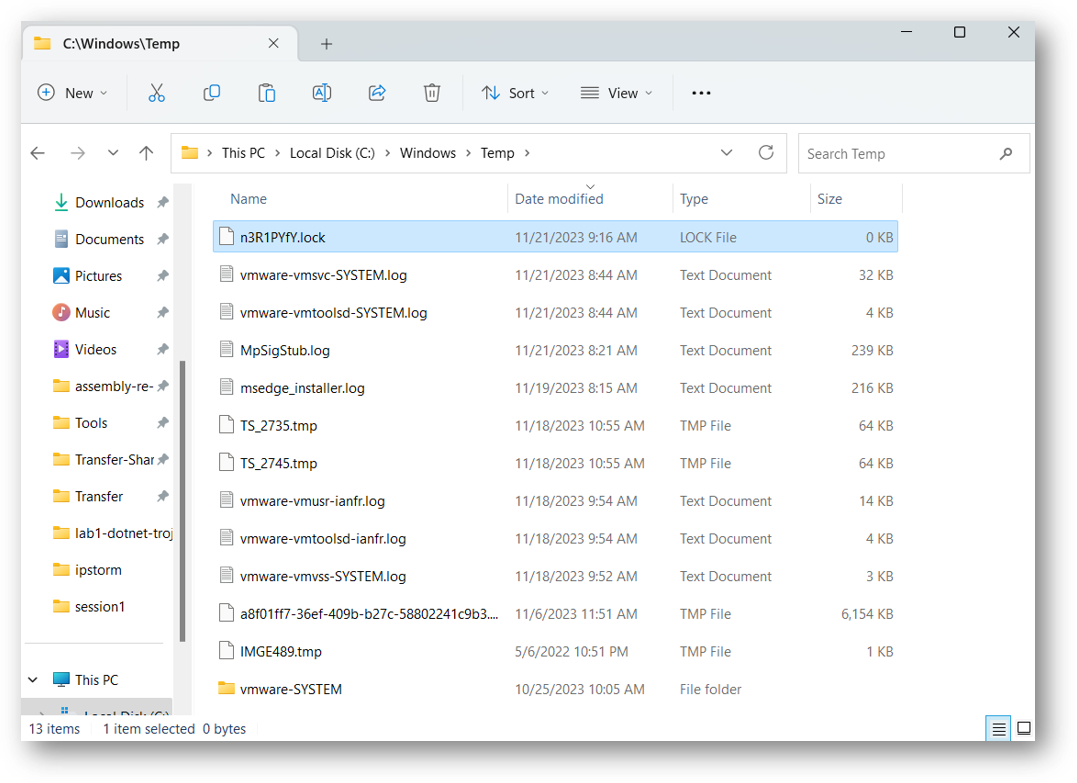
The process then launches cmd.exe, which launches powershell.exe -NoExit -Command -. Using Powershell, IPStorm creates a firewall rule and writes data to a file named StartupProfileData-Interactve.
然后,该进程将启动 ,该进程将启动 cmd.exe powershell.exe -NoExit -Command - 。使用 Powershell,IPStorm 创建防火墙规则并将数据写入名为 StartupProfileData-Interactve .
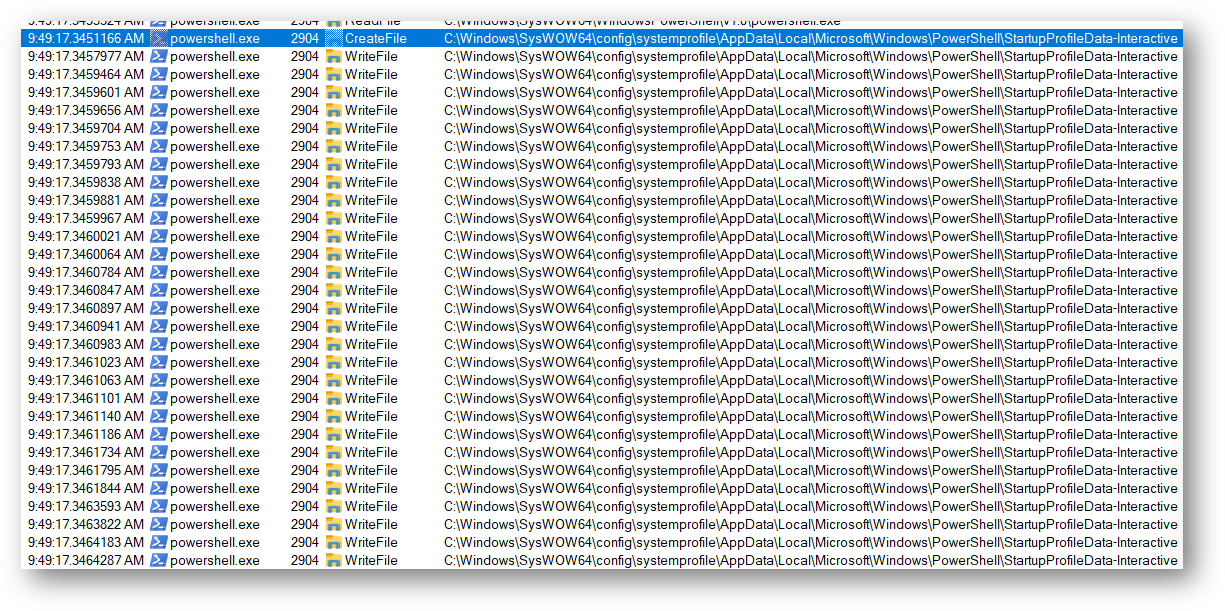
The malware opens several TCP sockets and communicates with several hosts.
该恶意软件打开多个 TCP 套接字并与多个主机通信。
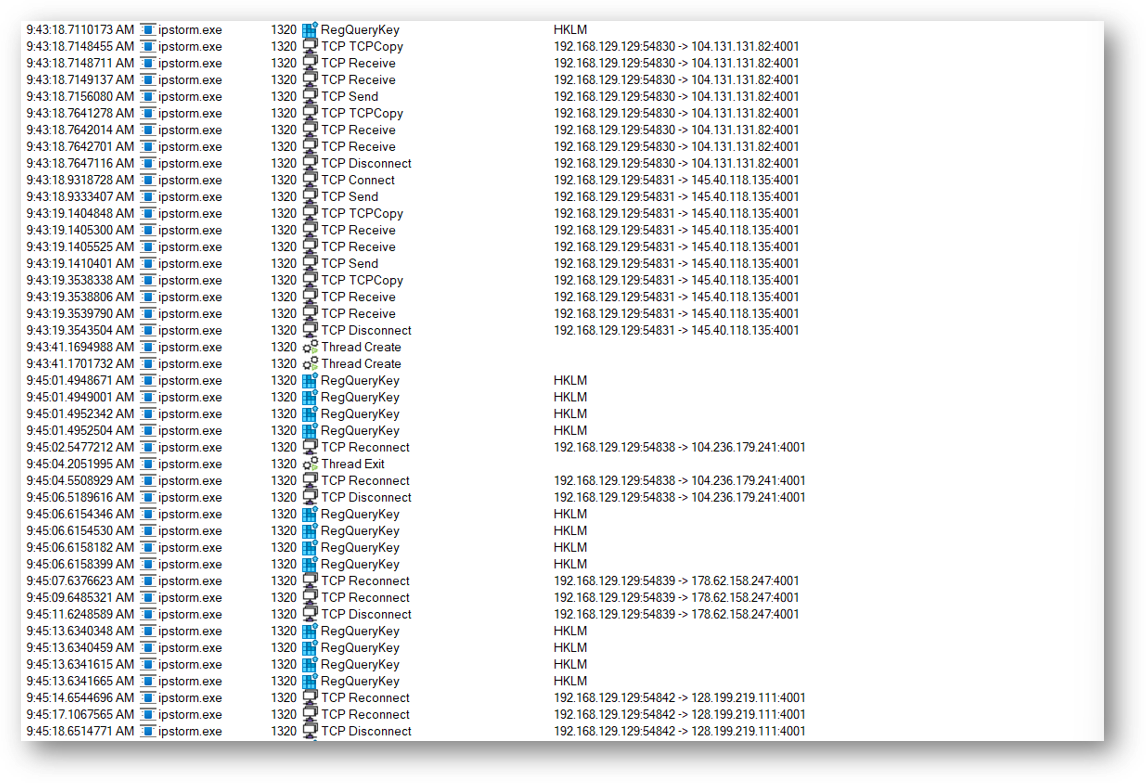
Network Calls 网络呼叫
The sample attempts to connect to several different IPs and domains. Examining the strings in the process memory can give us more insight into what network activity is happening.
此示例尝试连接到多个不同的 IP 和域。检查进程内存中的字符串可以让我们更深入地了解正在发生的网络活动。
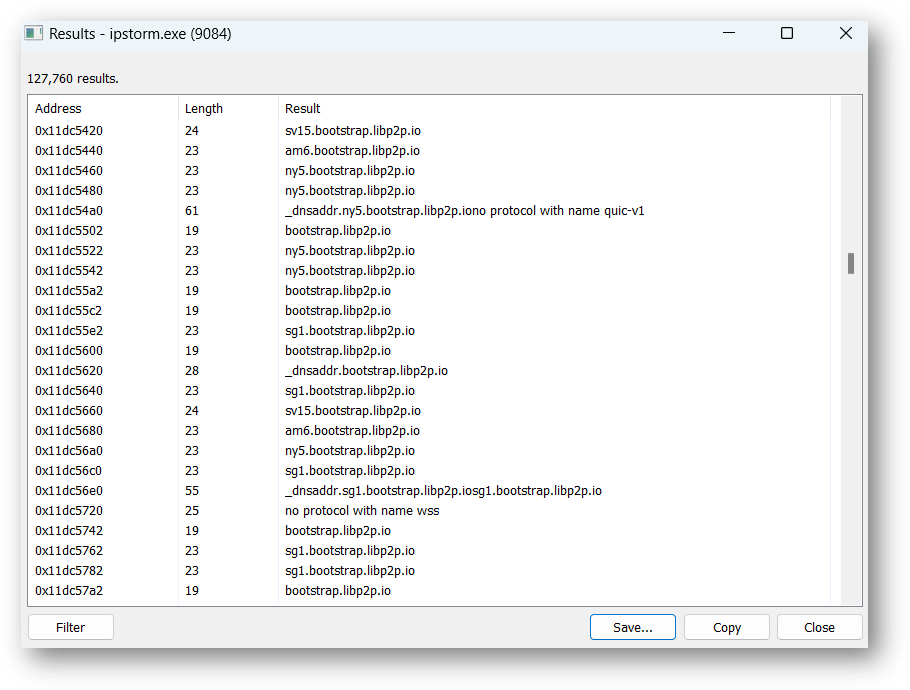
We can see some of the IPFS requests being made as well:
我们也可以看到一些 IPFS 请求:
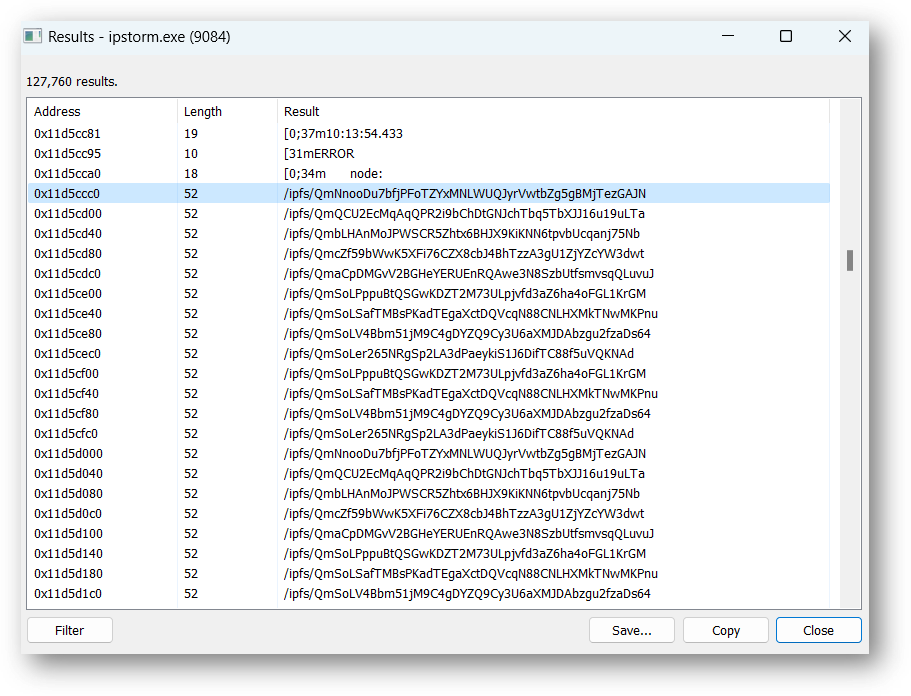
I’ve resolved a few of the domains to their IPs below:
我已经将一些域解析为它们的 IP:
104.131.131.82:4001 (mars.i.ipfs.io)Possible C2104.131.131.82:4001 (mars.i.ipfs.io)可能的 C2178.62.158.247:4001128.199.219.111:4001104.236.76.40:4001104.236.179.241:4001_dnsaddr.sv15.bootstrap.libp2p.io (139.178.91.71)
All hosts except 104.131.131.82 and 139.178.91.71 are down. We can see some preliminary evidence that an IPFS service is running on at least one of the hosts:
除 和 139.178.91.71 之外 104.131.131.82 的所有主机都已关闭。我们可以看到一些初步证据,表明IPFS服务至少在一台主机上运行:
sudo nmap -sV 104.131.131.82 -p 8080,4001
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-18 08:49 PST
Nmap scan report for mars.i.ipfs.io (104.131.131.82)
Host is up (0.020s latency).
PORT STATE SERVICE VERSION
4001/tcp open libp2p-multistream libp2p multistream protocol 1.0.0
8080/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
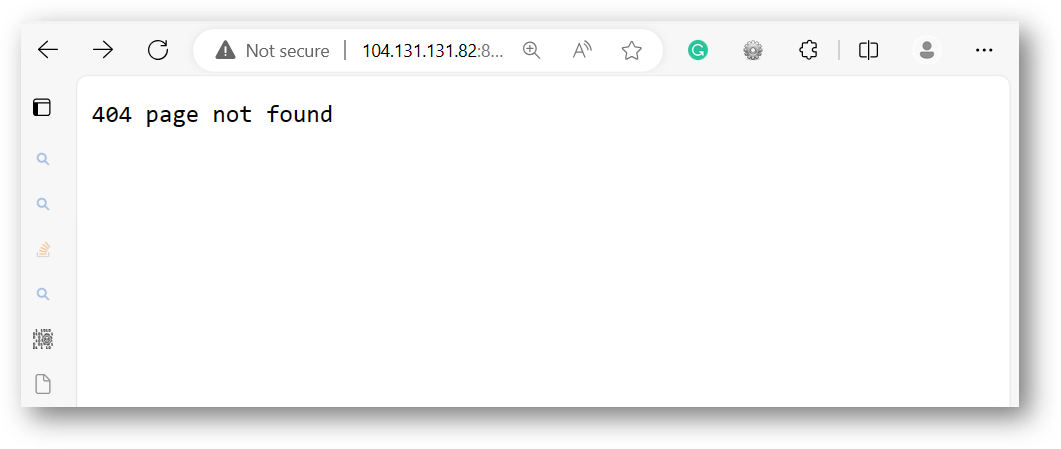
Trying to navigate to port 8080 in a browser gives a very non-descript 404:
尝试在浏览器中导航到端口 8080 时,会出现一个非常不起眼的 404:
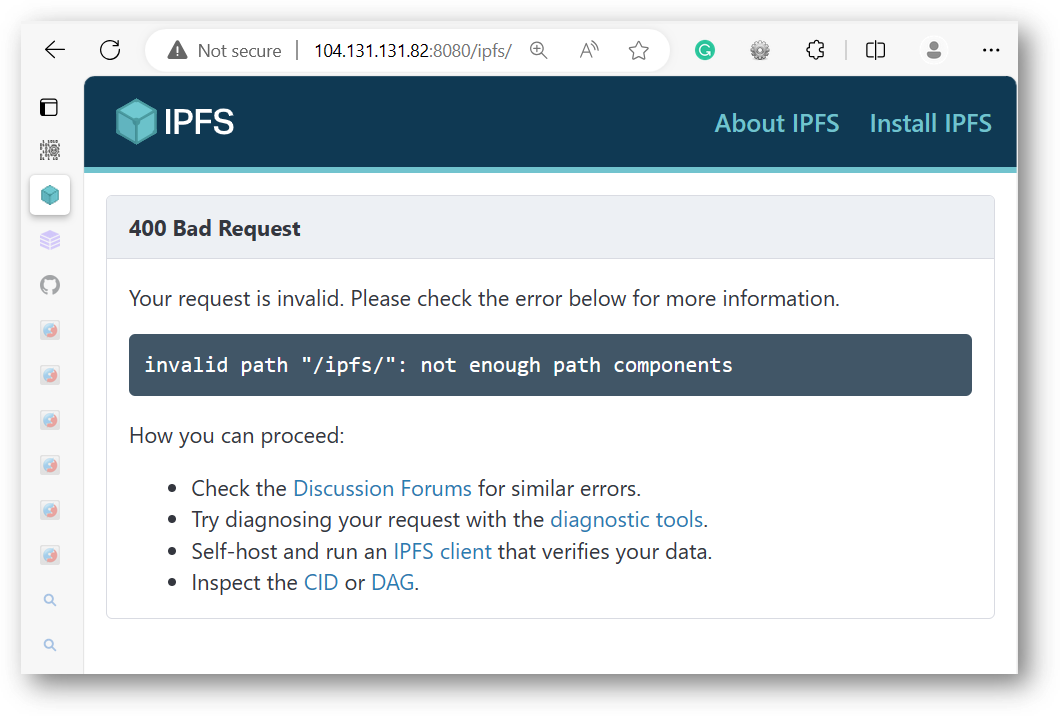
By playing with the URL path a bit, we can see a descriptive error message clearly showing IPFS:
通过稍微调整一下 URL 路径,我们可以看到一个描述性的错误消息,清楚地显示 IPFS:
Thus far, every sample of IPStorm I’ve looked at contacts this host and the one below (sv15.bootstrap.libp2p.io).
到目前为止,我看过的每个 IPStorm 示例都与该主机和下面的主机(sv15.bootstrap.libp2p.io)相关联。
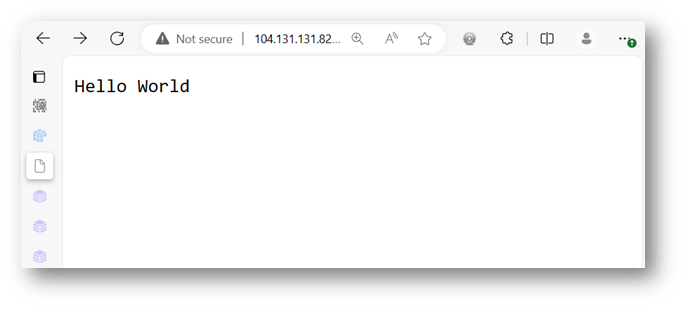
This application needs an IPFS content identifier or CID. This can be a string or a file. IPFS encodes all content into a base58 encoded hash called a multihash. As an example, we can have the application display back a message by navigating to http://104.131.131.82:8080/ipfs/QmWATWQ7fVPP2EFGu71UkfnqhYXDYH566qy47CnJDgvs8u:
此应用程序需要 IPFS 内容标识符或 CID。这可以是字符串或文件。IPFS 将所有内容编码为称为多哈希的 base58 编码哈希。例如,我们可以通过导航到以下位置 http://104.131.131.82:8080/ipfs/QmWATWQ7fVPP2EFGu71UkfnqhYXDYH566qy47CnJDgvs8u 来让应用程序显示一条消息:
The last address – _dnsaddr.bootstrap.libp2p.io – is interesting as it appears to be using multiaddr. Here is an excerpt from their github
最后一个地址 – – _dnsaddr.bootstrap.libp2p.io 很有趣,因为它似乎使用了 multiaddr。这是他们github的摘录
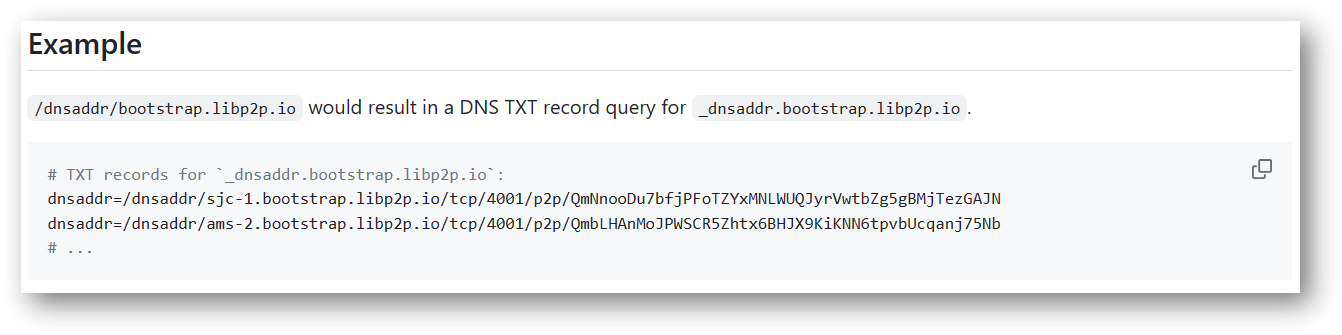
Without multiaddr support, the domain is unreachable as-is, possibly another built-in defense mechanism to evade analysis in a sandbox.
如果没有 multiaddr 支持,该域将无法按原样访问,这可能是另一种内置的防御机制,用于逃避沙盒中的分析。
nslookup _dnsaddr.sv15.bootstrap.libp2p.io
Server: 172.31.80.1
Address: 172.31.80.1#53
Non-authoritative answer:
*** Can't find _dnsaddr.sv15.bootstrap.libp2p.io: No answer
Removing the _dnsaddr gives a little more info:
删除 _dnsaddr 会提供更多信息:
nslookup sv15.bootstrap.libp2p.io
Server: 172.31.80.1
Address: 172.31.80.1#53
Non-authoritative answer:
Name: sv15.bootstrap.libp2p.io
Address: 139.178.91.71
Name: sv15.bootstrap.libp2p.io
Address: 2604:1380:45e3:6e00::1
Running a whois 139.178.91.71 reveals that the IP is assigned to Equinix Services, a network provider and data center based in New York.
运行显示 whois 139.178.91.71 IP 已分配给 Equinix Services,这是一家位于纽约的网络提供商和数据中心。
Nmap reveals a little more information about the application running on port 4001:
Nmap 揭示了有关在端口 4001 上运行的应用程序的更多信息:
sudo nmap -sV 139.178.91.71 -p 443,4001
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-18 08:42 PST
Nmap scan report for sv15 (139.178.91.71)
Host is up (0.032s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http nginx 1.16.1
4001/tcp open libp2p-multistream libp2p multistream protocol 1.0.0
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.68 seconds
nc -v 139.178.91.71 4001
Warning: forward host lookup failed for sv15: Unknown host
sv15 [139.178.91.71] 4001 (?) open
/multistream/1.0.0
The web server is a wrapper for the multistream service on port 4001:
Web 服务器是端口 4001 上多流服务的包装器:
curl https://sv15.bootstrap.libp2p.io/
WebSocket protocol violation: Connection header "keep-alive" does not contain Upgrade
Using websocat, we can connect to the server using a websocket:
使用 websocat,我们可以使用 websocket 连接到服务器:
./websocat_max.x86_64-unknown-linux-musl wss://sv15.bootstrap.libp2p.io//multistream/1.0.0
/multistream/1.0.0
Multistream Requests 多流请求
I captured and extracted the following multisteam DNS requests:
我捕获并提取了以下多蒸汽DNS请求:
| Request 请求 | Response 响应 |
|---|---|
| _dnsaddr.bootstrap.libp2p.io | dnsaddr=/dnsaddr/sv15.bootstrap.libp2p.io/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.bootstrap.libp2p.io | dnsaddr=/dnsaddr/sg1.bootstrap.libp2p.io/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.bootstrap.libp2p.io | dnsaddr=/dnsaddr/am6.bootstrap.libp2p.io/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.bootstrap.libp2p.io | dnsaddr=/dnsaddr/ny5.bootstrap.libp2p.io/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/dns4/sv15.bootstrap.libp2p.io/tcp/443/wss/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip4/139.178.91.71/udp/4001/quic-v1/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/dns6/sv15.bootstrap.libp2p.io/tcp/443/wss/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip4/139.178.91.71/tcp/4001/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45e3:6e00::1/udp/4001/quic-v1/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN dnsaddr=/ip6/2604:1380:45e3:6e00::1/udp/4001/quic-v1/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45e3:6e00::1/udp/4001/quic/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN dnsaddr=/ip6/2604:1380:45e3:6e00::1/udp/4001/quic/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip4/139.178.91.71/udp/4001/quic/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.sv15.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45e3:6e00::1/tcp/4001/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN dnsaddr=/ip6/2604:1380:45e3:6e00::1/tcp/4001/p2p/QmNnooDu7bfjPFoTZYxMNLWUQJyrVwtbZg5gBMjTezGAJN |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/dns6/ny5.bootstrap.libp2p.io/tcp/443/wss/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip4/136.144.51.25/udp/4001/quic-v1/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip4/136.144.51.25/tcp/4001/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/dns4/ny5.bootstrap.libp2p.io/tcp/443/wss/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45d2:8100::1/udp/4001/quic-v1/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa dnsaddr=/ip6/2604:1380:45d2:8100::1/udp/4001/quic-v1/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45d2:8100::1/tcp/4001/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa dnsaddr=/ip6/2604:1380:45d2:8100::1/tcp/4001/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip4/139.178.65.157/udp/4001/quic/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.ny5.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:45d2:8100::1/udp/4001/quic/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa dnsaddr=/ip6/2604:1380:45d2:8100::1/udp/4001/quic/p2p/QmQCU2EcMqAqQPR2i9bChDtGNJchTbq5TbXJJ16u19uLTa |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/dns6/sg1.bootstrap.libp2p.io/tcp/443/wss/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip4/145.40.118.135/udp/4001/quic-v1/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/dns4/sg1.bootstrap.libp2p.io/tcp/443/wss/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip4/145.40.118.135/tcp/4001/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:40e1:9c00::1/udp/4001/quic/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt dnsaddr=/ip6/2604:1380:40e1:9c00::1/udp/4001/quic/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:40e1:9c00::1/tcp/4001/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt dnsaddr=/ip6/2604:1380:40e1:9c00::1/tcp/4001/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:40e1:9c00::1/udp/4001/quic-v1/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt dnsaddr=/ip6/2604:1380:40e1:9c00::1/udp/4001/quic-v1/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.sg1.bootstrap.libp2p.io | dnsaddr=/ip4/145.40.118.135/udp/4001/quic/p2p/QmcZf59bWwK5XFi76CZX8cbJ4BhTzzA3gU1ZjYZcYW3dwt |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip4/147.75.87.27/tcp/4001/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/dns4/am6.bootstrap.libp2p.io/tcp/443/wss/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/dns6/am6.bootstrap.libp2p.io/tcp/443/wss/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip4/147.75.87.27/udp/4001/quic-v1/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:4602:5c00::3/udp/4001/quic/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb dnsaddr=/ip6/2604:1380:4602:5c00::3/udp/4001/quic/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:4602:5c00::3/udp/4001/quic-v1/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb dnsaddr=/ip6/2604:1380:4602:5c00::3/udp/4001/quic-v1/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip6/2604:1380:4602:5c00::3/tcp/4001/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb dnsaddr=/ip6/2604:1380:4602:5c00::3/tcp/4001/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
| _dnsaddr.am6.bootstrap.libp2p.io | dnsaddr=/ip4/147.75.87.27/udp/4001/quic/p2p/QmbLHAnMoJPWSCR5Zhtx6BHJX9KiKNN6tpvbUcqanj75Nb |
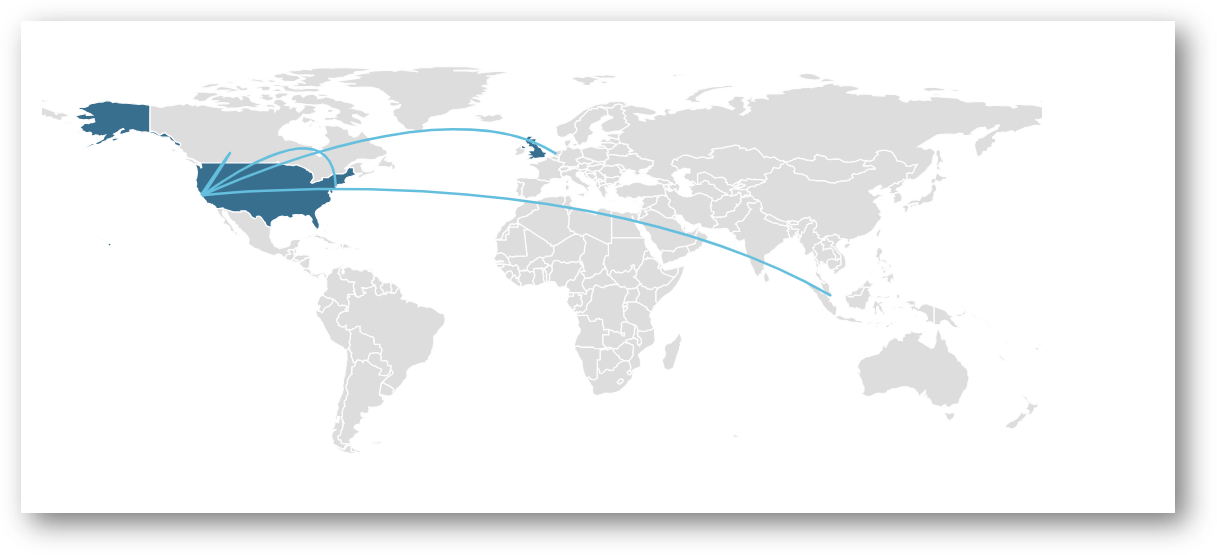
Contacted Countries 联系国家/地区
原文始发于Ian French:A Look at IPStorm – Cross-Platform Malware Written in Go
转载请注明:A Look at IPStorm – Cross-Platform Malware Written in Go | CTF导航