
Over the weekend, I was taking a look at an application which implemented SSL pinning. Here’s the technique I used to bypass pinning and view the raw requests sent to the application server which then helped me to uncover crucial details about the application’s functionality.
上周末,我看了一个实现SSL固定的应用程序。这是我用来绕过固定并查看发送到应用程序服务器的原始请求的技术,然后帮助我发现有关应用程序功能的关键细节。
Prerequisites 先决条件
-
An android emulator of choice
首选的安卓模拟器 -
Burpsuite (installed on host machine)
Burpsuite(安装在主机上) -
Python packages Python 包
-
objectionIf you face issues post-installation:
如果您在安装后遇到问题:pip install --upgrade setuptools -
frida -
frida-tools
-
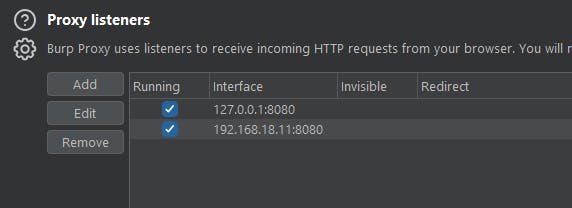
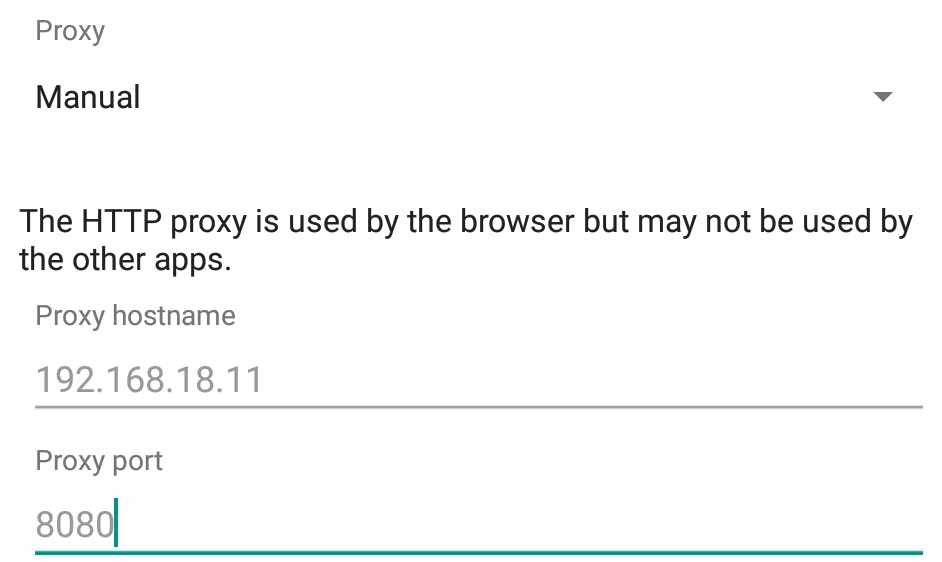
Configure Burp Proxy 配置 Burp 代理
on host
on emulator
Install Certificate onto emulator
将证书安装到模拟器上
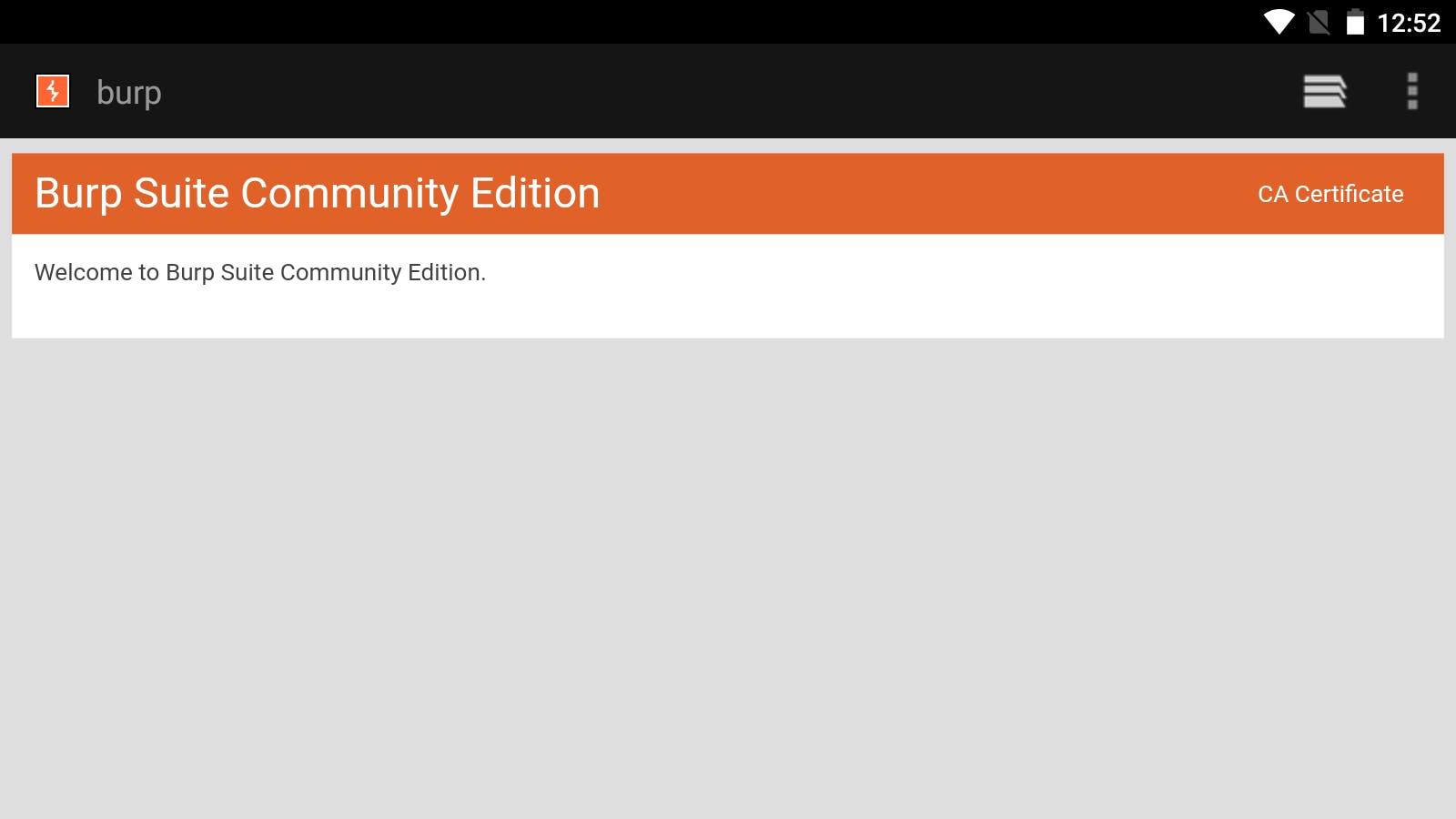
Launch the browser and head to http://burp and download the CA Certificate.
启动浏览器并下载 http://burp CA证书。
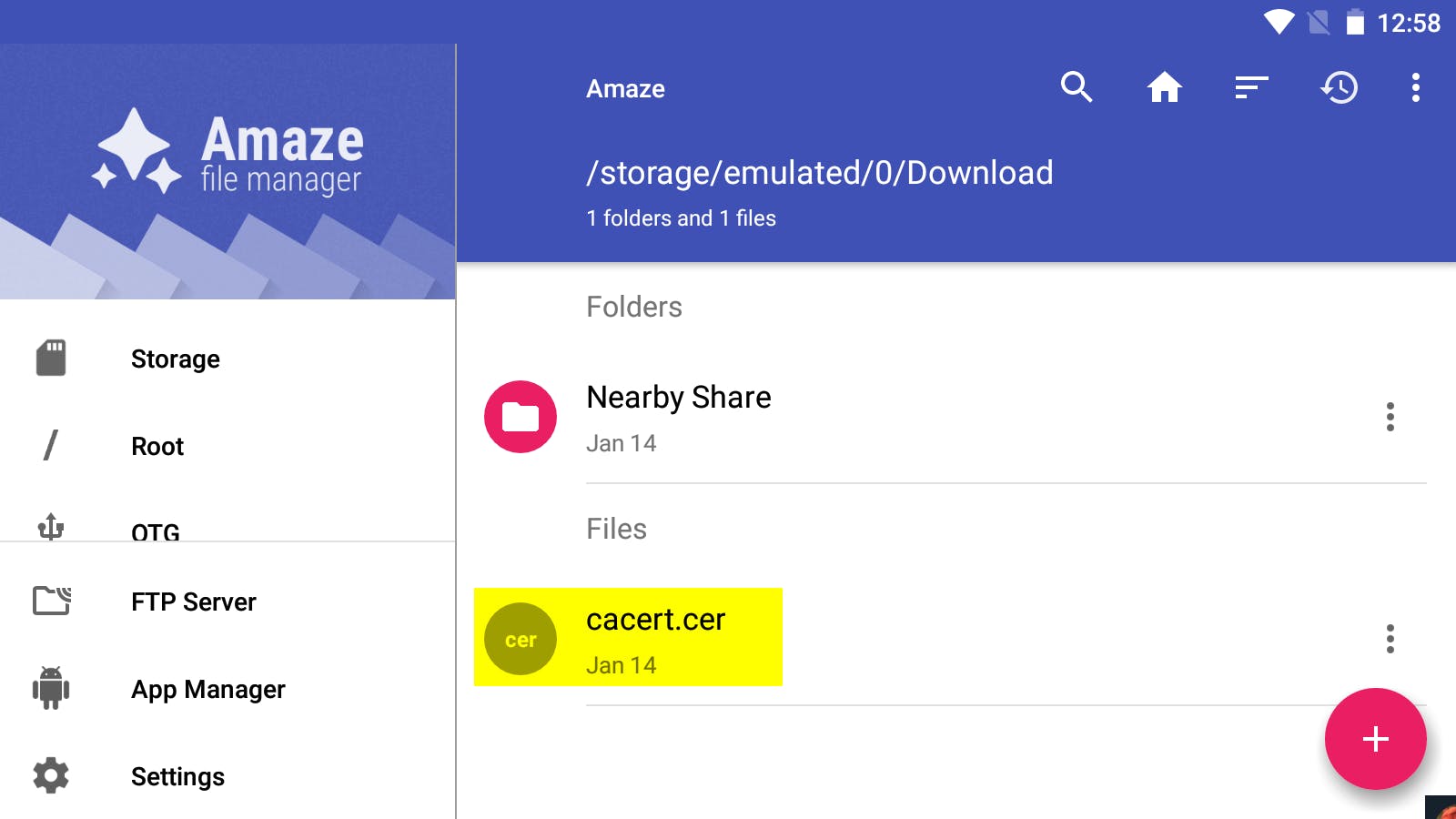
Make sure to rename the cert to <name>.cer via the file manager.
确保通过文件管理器将证书重命名为 <name>.cer 。
Then head to the certificate settings on the respective emulator and install the newly downloaded certificate.
然后前往相应模拟器上的证书设置并安装新下载的证书。
Frida Server Frida 服务器
Releases · frida/frida (github.com)
发布 ·弗里达/弗里达 (github.com)
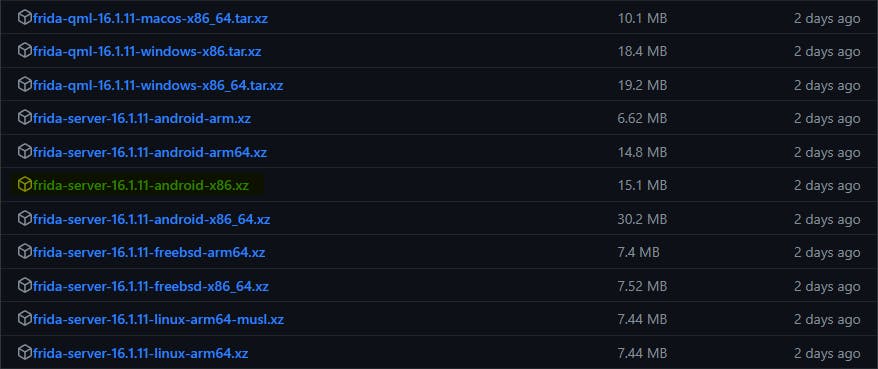
download the unzip the respective frida-server versions, extract it and move it to the bin location of your emulator. In my case : D:\Program Files\Nox\bin
下载解压缩相应的 frida-server 版本,将其解压缩并将其移动到模拟器的 bin 位置。就我而言: D:\Program Files\Nox\bin
adb devices
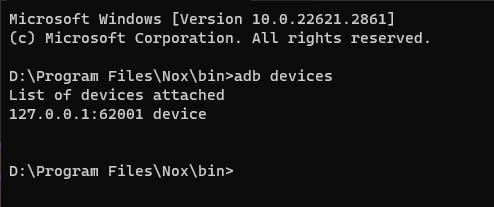
verify that the adb interface is attached to the device.
验证 ADB 接口是否已连接到设备。
adb push frida /data/local/tmp
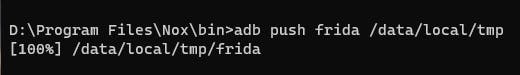
Push the frida binary to the device via ADB.
通过 ADB 将 frida 二进制文件推送到设备。
D:\Program Files\Nox\bin>adb shell
cd /data/local/tmp/
chmod +x frida
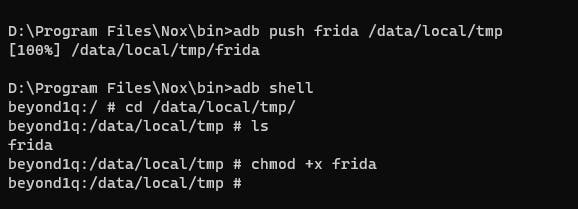
Give the binary execute permissions.
授予二进制执行权限。
./frida &
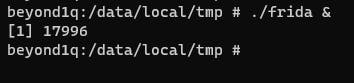
Run frida server in the background.
在后台运行 frida 服务器。
Bypass SSL Pinning 绕过 SSL 固定
There are a ton of scripts developed by the community for frida which you can find here. We’ll be making use of the frida-multiple-unpinning script for our use case.
社区为 frida 开发了大量脚本,您可以在此处找到这些脚本。我们将在用例中使用该 frida-multiple-unpinning 脚本。
frida --codeshare akabe1/frida-multiple-unpinning -U -f com.twitter.android
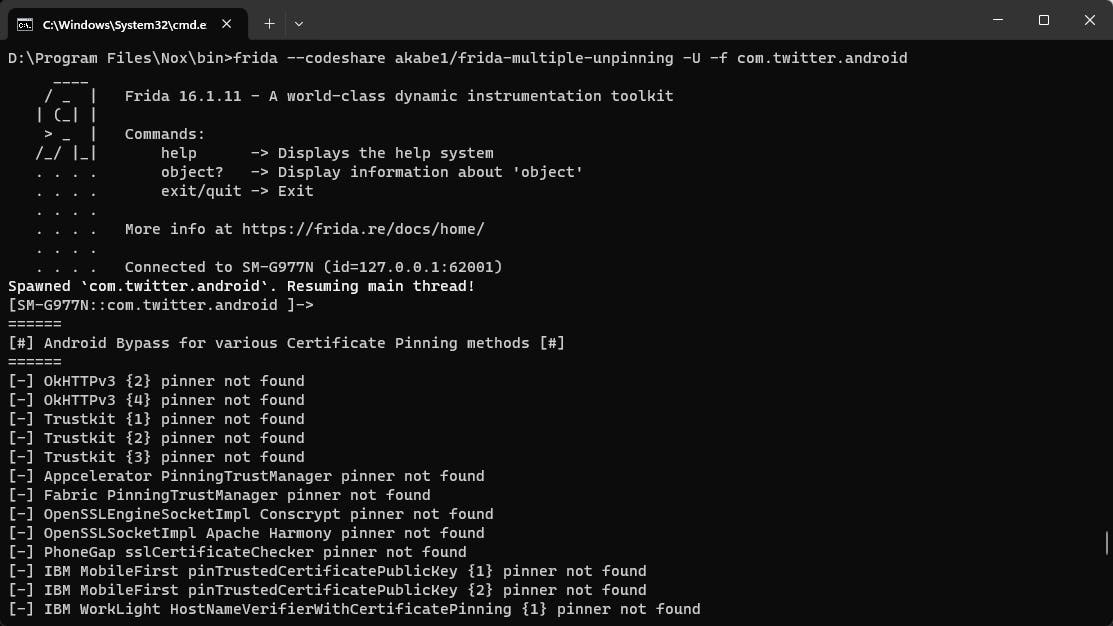
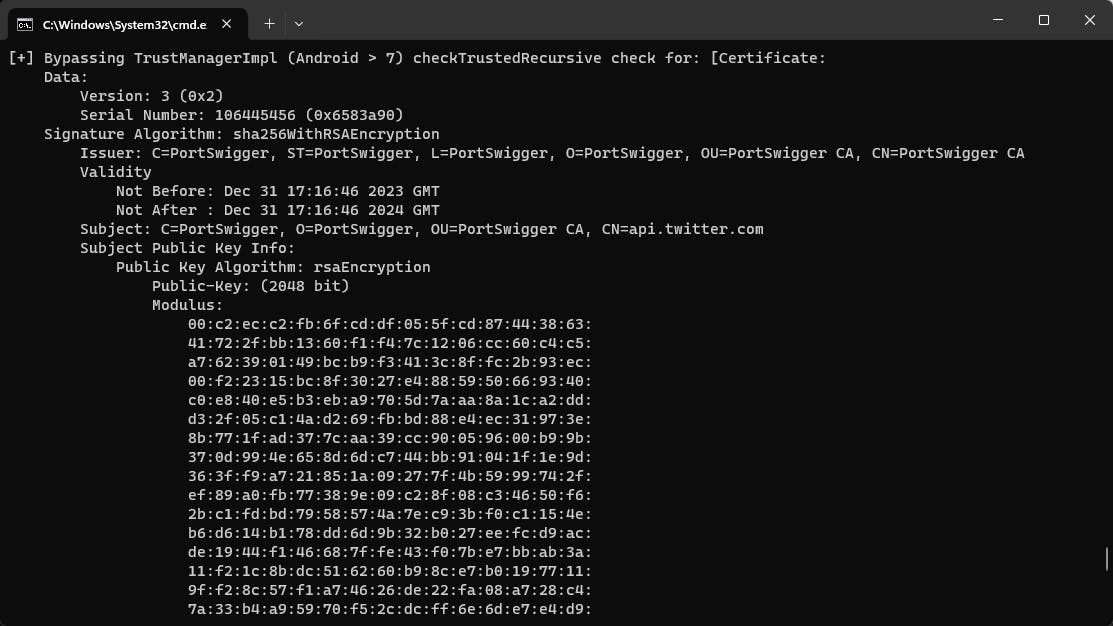
We can verify that the X AKA twitter app has opened up and the SSL pinning bypass is in effect.
我们可以验证 X AKA twitter 应用程序是否已打开,并且 SSL 固定绕过是否有效。
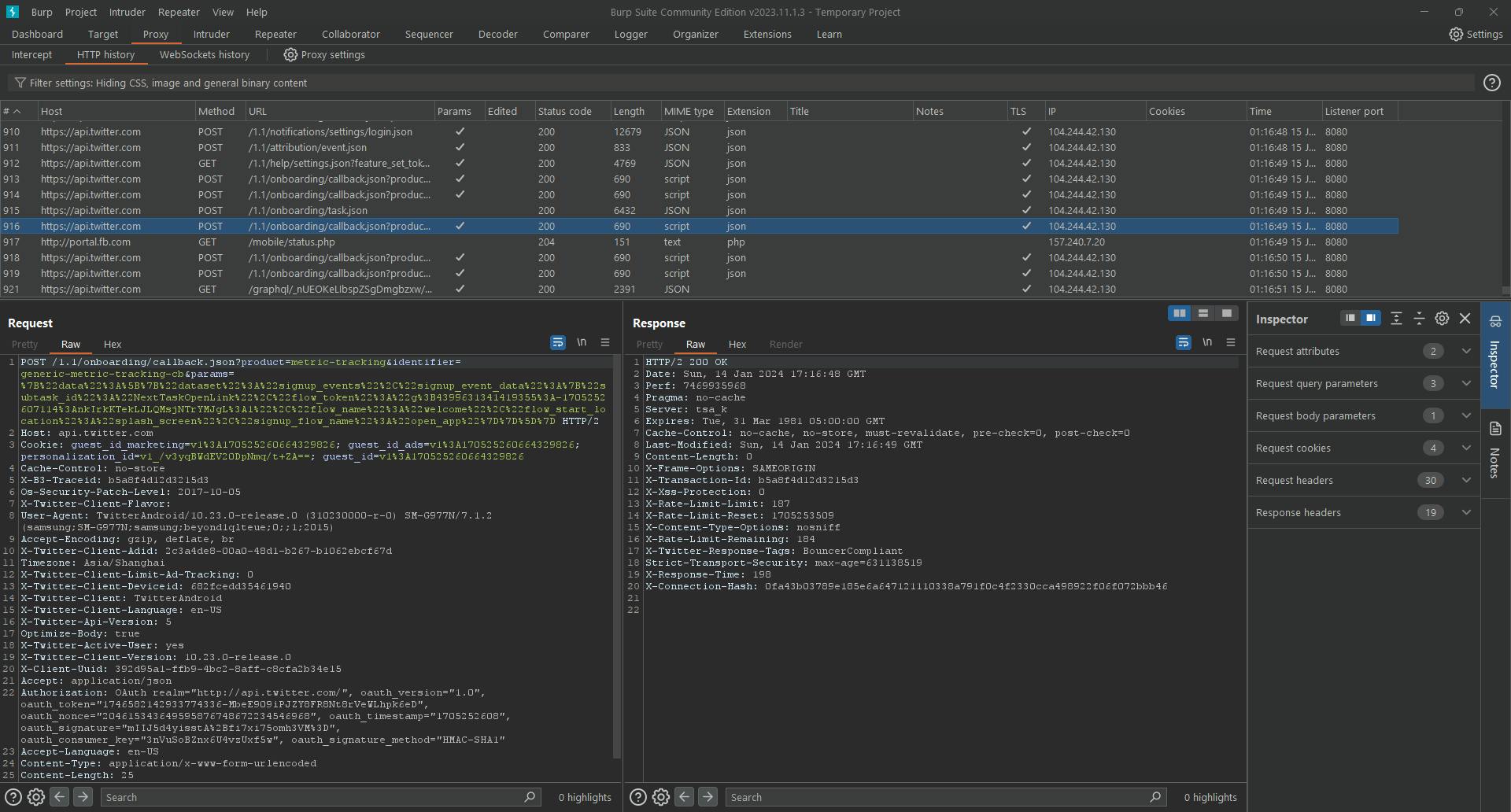
We can then take a look at burp and ensure that we are able to see the raw requests sent by the X app to its api server.
然后,我们可以查看打嗝,并确保我们能够看到 X 应用程序发送到其 api 服务器的原始请求。