
We’ve been testing the security of a number of different electronic flight bag, or EFB, applications for a few years now. Here’s the latest on that now it has been remediated, 19 months after our initial disclosure to Airbus.
几年来,我们一直在测试一些不同的电子飞行包(EFB)应用程序的安全性。这是最新的,现在它已经得到了补救,19个月后,我们首次披露给空中客车公司。
TL;DR 左心室,右心室
- Flysmart+ is a suite of apps for pilot EFBs, helping deliver efficient and safe departure and arrival of flights
Flysmart+是一套适用于飞行员EFB的应用程序,可帮助提供高效安全的航班起飞和抵达 - One of the iOS appshad ATS (App Transport Security) intentionally disabled, together with any form of certificate validation, exposing the app to interception attacks over Wi-Fi
其中一个iOS应用程序ATS(应用程序传输安全性)故意禁用,以及任何形式的证书验证,使应用程序暴露于Wi-Fi拦截攻击 - This could enable tampering with, for example, the engine performance calculations, potentially resulting in a tailstrike or runway excursion on departure
这可能会导致篡改,例如,发动机性能计算,可能导致离港时的尾部撞击或跑道偏移 - Airline EFBs can be exposed to interception on untrusted networks given pilot layover hotels are well known and used consistently each night
航空公司的EFB可能会在不受信任的网络上被拦截,因为飞行员中途停留的酒店是众所周知的,并且每晚都在使用 - Airline Standard Operating Procedures (SOP) during cross checks would be unlikely to detect any tampering
交叉检查期间的航空公司标准操作程序(SOP)不太可能检测到任何篡改 - Airbus responded quickly to our disclosure and resolved the issue
空客对我们的披露迅速做出了回应,并解决了这个问题
NAVBLUE are an Airbus owned IT services company. This post is about their EFB management app called Flysmart+ Manager. This how they describe it:
NAVBLUE是空客旗下的IT服务公司。这篇文章是关于他们的EFB管理应用程序称为Flysmart+ Manager。他们是这样描述的:
“Flysmart+ for iPad FS+ Manager is an application developed by NAVBLUE enabling the synchronization and the installation of the Airline’s data into the other available Flysmart+ for iPad Apps.”
FlysmartTM + for iPad FS+ Manager是NAVBLUE开发的一款应用程序,可以将航空公司的数据同步并安装到其他可用的FlysmartTM + for iPad应用程序中。”
“The FS+ Manger App is the center of the Apps Suite.”
“FS+ Manger应用程序是应用程序套件的中心。”
We found that the Flysmart+ Manager application had an important security control disabled, meaning that it could communicate with servers using insecure methods. With that control disabled an attacker could potentially modify aircraft performance data or adjust airport information e.g. runway lengths.
我们发现Flysmart+ Manager应用程序禁用了一个重要的安全控制,这意味着它可以使用不安全的方法与服务器通信。在该控制被禁用的情况下,攻击者可能会修改飞机性能数据或调整机场信息,例如跑道长度。
The details 细节
The app did not have any ATS protection, it had been disabled. We think this was probably done at some point in the past to suit a particular airline client that was struggling to implement Flysmart+. It affected all users of the app though.
该应用程序没有任何ATS保护,它已被禁用。我们认为,这可能是在过去的某个时候为了满足某个航空公司客户的需求而做的,该客户当时正在努力实施Flysmart+。它影响了所有应用程序的用户。
ATS is a security mechanism that forces the application to use HTTPS, preventing unencrypted communications. An attacker could use this weakness to intercept and decrypt potentially sensitive information in transit.
ATS是一种安全机制,强制应用程序使用HTTPS,防止未加密的通信。攻击者可以利用此弱点拦截和解密传输中的潜在敏感信息。
With ATS disabled, insecure communication happens. It makes the app susceptible to interception where an attacker could force a victim to use the unencrypted HTTP protocol while forwarding the data to the real server, encrypted.
禁用ATS时,会发生不安全的通信。这使得应用程序容易被拦截,攻击者可以迫使受害者使用未加密的HTTP协议,同时将数据转发到加密的真实的服务器。
An entry in the info.plist file alongside the app allows insecure HTTP loads to any domain. In the code excerpt below NSAllowsArbitraryLoads is included with the value set to true, which disables ATS:
在应用程序旁边的info.plist文件中的一个条目允许向任何域加载不安全的HTTP。在下面的代码摘录中,NSAllowslogaryLoads被包含在设置为true的值中,这将禁用ATS:
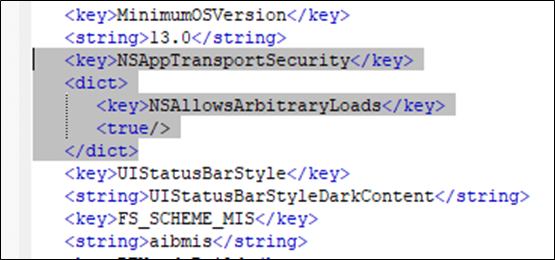
Current Apple guidelines state:
目前苹果的指导方针规定:
“You must supply a justification during App Store review if you set the key’s value to YES (true), as described in Provide Justification for Exceptions. Use this key with caution because it significantly reduces the security of your app. In most cases, it’s better to upgrade your servers to meet the requirements imposed by ATS, or at least to use a narrower exception.”
“如果您将键的值设置为YES(true),则必须在App Store审核期间提供理由,如提供验证理由中所述。请谨慎使用此密钥,因为它会显著降低应用的安全性。在大多数情况下,最好升级服务器以满足ATS的要求,或者至少使用范围更窄的例外。”
This requirement is not enforced on applications which were uploaded before this it was introduced.
此要求不适用于在此之前上传的应用程序。
The issue allowed us to view the data being downloaded from the NAVBLUE Servers:
该问题允许我们查看从NAVBLUE服务器下载的数据:

A lot of these files were SQLite databases containing information on specific aircraft, as well as take-off performance data (PERF). An example of one database contained the following tables names:
这些文件中有很多是SQLite数据库,包含特定飞机的信息以及起飞性能数据(PERF)。一个数据库的示例包含以下表名:
Database tables 数据库表
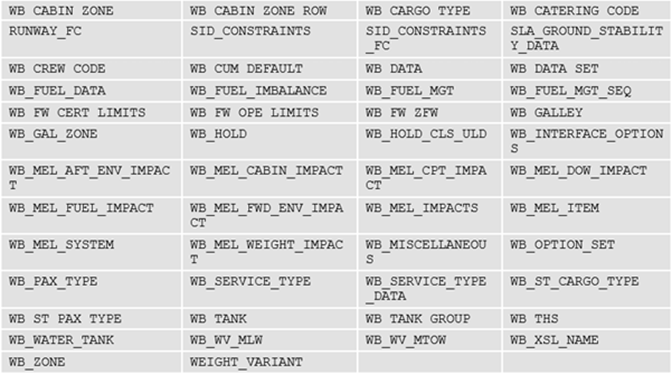
Many of these database tables are important to the performance, or weight and balance (see ‘WB’ above) of an aircraft
这些数据库表中的许多表对于飞机的性能或重量和平衡(见上面的’WB’)都很重要
‘MEL’ refers to the Minimum Equipment List, so which systems are permitted to be inoperative for a flight. Changing this risks in-flight issues. The Gimli Glider incident is an example of a MEL misunderstanding contributing to a flight safety problem.
“MEL”指的是最低设备清单,因此哪些系统允许在飞行中被禁用。改变这一点会带来飞行中的问题。Gimli Glider事件是MEL误解导致飞行安全问题的一个例子。
‘SID’ refers to a Standard Instrument Departure, so how an aircraft safely departs from an airport.
“SID”指的是标准仪表离场,即飞机如何安全地离开机场。
Even something as simple as the choice of units has led to safety problems. Confusion between US gallons, imperial gallons, litres, kilograms and pounds caused the Gimli Glider fuel starvation incident.
即使是像选择单位这样简单的事情也会导致安全问题。美制加仑、英制加仑、升、公斤和磅之间的混淆导致了金利滑翔机燃料短缺事件。
Further analysis of the database suggested that integrity checks were being performed locally:
对数据库的进一步分析表明,正在当地进行完整性检查:
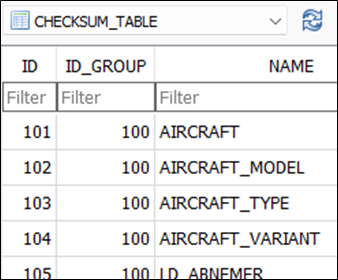
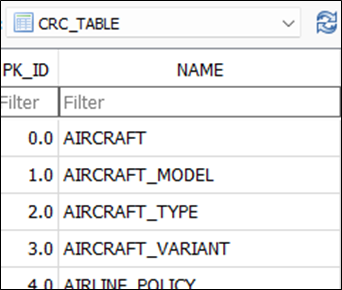
That would allow, for example, tampering with all engine performance calculation data, though the checksum issue is mitigated by the fix to the ATS issue.
例如,这将允许篡改所有发动机性能计算数据,尽管对ATS问题的修复缓解了校验和问题。
Practical attack 实际攻击
The application update cycle is in-line with updates to the Aeronautical Information Regulation and Control (AIRAC) database:
应用程序更新周期与航空信息监管和控制(AIRAC)数据库的更新一致:
“Aeronautical information is constantly changing: airspace structures and routes are revised, navigation aids change, SIDs and STARs are amended, runway and taxiway information changes. It is essential, for both efficiency and safety, that pilots, dispatchers, air traffic controllers, air traffic flow managers, flight management systems and aeronautical charts all have the same information working from the same information base.
“航空信息在不断变化:空域结构和航线在修改,导航设备在变化,SID和STAR在修改,跑道和滑行道信息在变化。为了效率和安全,飞行员、调度员、空中交通管制员、空中交通流量管理员、飞行管理系统和航空图表都必须从同一个信息库获得相同的信息。
This can only be achieved by adhering to the AIRAC schedule.”
这只能通过遵守AIRAC时间表来实现。”
This means that pilots would likely update the application once a month.
这意味着飞行员可能会每月更新一次应用程序。
Given that airlines typically use the same hotel for pilots who are down route / on a layover, an attacker could target the hotel’s Wi-Fi networks with the goal of modifying aircraft performance data.
考虑到航空公司通常会将同一家酒店用于中途停留的飞行员,攻击者可以将酒店的Wi-Fi网络作为目标,以修改飞机性能数据。
It’s quite easy to identify pilots in layover hotels. It’s also fairly easy to identify the airline and therefore the suite of EFB apps they are likely to be using.
在中途停留的旅馆里很容易辨认飞行员。它也相当容易识别航空公司,因此,套件的EFB应用程序,他们可能会使用。
Disclosure timeline 披露时间轴
28th June 2022: vulnerability report sent to [email protected] using the PGP key, as described on the Airbus ‘contact us’ page here: https://www.airbus.com/en/airbus-contact-us
28 th 2022年6月:使用PGP密钥将漏洞报告发送到[email protected],如空客“联系我们”页面所述https://www.airbus.com/en/airbus-contact-us
29th June 2022: receipt acknowledged, tracking reference was provided.
29 th 2022年6月:确认接收,提供跟踪参考。
25th July 2022: response from Airbus, confirming that they had replicated the issue. A fix would be provided for the next version of Flysmart+, due by the end of 2022.
25 th 2022年7月:空客的回应,确认他们已经复制了这个问题。Flysmart+的下一个版本将在2022年底之前提供修复程序。
We understand that aviation software has to be certified to be safe so were not overly surprised by the expected remediation timeline.
我们理解航空软件必须经过安全认证,因此对预期的补救时间轴并不感到过度惊讶。
22nd Feb 2023: We contacted the Airbus VDP team to ask if the fix had been pushed in the latest version of Flysmart+, given we were well in to the new year.
22 nd 2023年2月:我们联系了空客VDP团队,询问是否在最新版本的Flysmart+中推出了修复程序,因为我们已经进入了新的一年。
26th May 2023: Airbus replied, confirming that the ‘mitigation measure’ had been communicated to customers.
2023年5月26日:空客回复,确认已将“缓解措施”传达给客户。
We asked if we could blog about the issue, now that it had been fixed. We referenced successful coordinated disclosure of similar EFB issues with Boeing and Lufthansa Systems.
我们问我们是否可以在博客上讨论这个问题,现在它已经被修复了。我们参考了与波音和汉莎航空系统公司成功协调披露的类似EFB问题。
We finally heard back from Airbus on 24th October, declining to comment on the blog or thank us publicly, but asking for one change, which we were happy to agree to.
我们终于在10月24日收到了空客的回复,拒绝在博客上发表评论或公开感谢我们,但要求我们做出一个改变,我们很高兴地同意了。
We presented our findings at the DEF CON 31 Aerospace Village in August, and also at the Aviation ISAC in Dublin .
我们在8月的DEF CON 31航空航天村和9月的都柏林航空ISAC上展示了我们的发现。
Since then, we have asked Airbus several times for further updates and for any words or comment they would like included in this post, but we’ve had no response.
从那以后,我们多次要求空中客车公司提供进一步的更新,以及他们希望在这篇文章中包含的任何文字或评论,但我们没有得到回应。
Conclusion 结论
We’ve now worked on disclosures with Boeing, Lufthansa, and Airbus. These experiences have shown how different disclosure in aviation is compared with other industries. The biggest difference is in the timescales, from the initial disclosure, to remediation, to publishing.
我们现在已经与波音、汉莎航空和空中客车公司合作披露。这些经验表明,与其他行业相比,航空业的披露有多么不同。最大的区别在于时间尺度,从最初的披露,到补救,再到发布。
Given the challenges of aviation cyber we’re sympathetic to long remediation times. For this reason it’s important to understand the nuances of the industry and avoid hasty public disclosure.
考虑到航空网络的挑战,我们对漫长的修复时间表示同情。出于这个原因,重要的是要了解行业的细微差别,避免仓促公开披露。
We’re really pleased that the vulnerability was successfully closed which is a win for aviation safety and security.
我们非常高兴漏洞被成功关闭,这是航空安全和保障的胜利。
原文始发于AVIATION CYBER SECURITY:Hacking Electronic Flight Bags. Airbus NAVBLUE Flysmart+ Manager
转载请注明:Hacking Electronic Flight Bags. Airbus NAVBLUE Flysmart+ Manager | CTF导航