Hello everyone! 大家好!
Welcome to my first blog post! I’m excited to be here ![]()
欢迎来到我的第一篇博文!我很高兴来到这里 ![]()
Today, I’m going to share with you my own research methodology for analyzing and reviewing source code applications to identify vulnerabilities on Whitebox engagements.
今天,我将与您分享我自己的研究方法,用于分析和审查源代码应用程序以识别白盒参与中的漏洞。
Whitebox assessments refer to a specific security testing scenario where the attacker/tester has prior access to the internal workings of the application, including its architecture, schemas or source code files. This access enables them to identify vulnerabilities more quickly and efficiently compared to the blackbox approach, which is what this article will be talking about.
白盒评估是指攻击者/测试人员可以事先访问应用程序的内部工作原理的特定安全测试方案,包括其架构、架构或源代码文件。与黑盒方法相比,这种访问使他们能够更快、更有效地识别漏洞,这正是本文将要讨论的内容。
The following article will focus on source code files that we are able to obtain or find using some Recon techniques (which will be explore in a future blog posts).
以下文章将重点介绍我们能够使用某些 Recon 技术获取或找到的源代码文件(将在以后的博客文章中探讨)。
The skill of finding bugs and weaknesses inside a code that you don’t familiar with and getting into the developer mind’s required to be experienced with code reading – and a lot of it, but I can promise to you, it will get much easier over time as long as you practice and deal with code on your daily basis.
在代码中发现你不熟悉的错误和弱点并进入开发人员头脑的技能需要有代码阅读的经验 – 而且很多,但我可以向你保证,只要你每天练习和处理代码,随着时间的推移,它会变得容易得多。

So let’s get started…
所以让我们开始吧……
Approaches to perform Code Review:
执行代码审查的方法:
There are numerous different ways to investigate code, which are:
有许多不同的方法可以调查代码,它们是:
- Covering code line by line
逐行覆盖代码 - Focusing on low-hanging fruit functions such as Login, Registration, and Password Reset mechanisms
专注于低垂的果实功能,如登录、注册和密码重置机制 - Greping regex keywords for quick-wins
Greping 正则表达式关键字以实现快速获胜 - Following user input using bottom-up and top-down approaches
使用自下而上和自上而下的方法遵循用户输入
Let’s break those things up:
让我们把这些东西分解一下:
Covering line by line:
逐行覆盖:
In cases where the project we are checking is considered large, this approach will consume a significant amount of time to cover end to end. Therefore, it is more suitable for projects with a small number of code files to cover.
如果我们正在检查的项目被认为是大型的,这种方法将消耗大量时间来覆盖端到端。因此,它更适合代码文件数量较少的项目。
Focus on Low-hanging fruit functions:
专注于唾手可得的功能:
This approach involves prioritizing web application mechanisms where the severity of identifying weaknesses and vulnerabilities is higher due to the complexity of requirements, such as validations, checks, and dependencies on other internal functions, thus we will focus on functions such as Login, Register, Forgot Password, Upload Files, and more.
这种方法涉及优先考虑 Web 应用程序机制,其中由于需求的复杂性(例如验证、检查和对其他内部函数的依赖)而识别弱点和漏洞的严重性较高,因此我们将重点关注登录、注册、忘记密码、上传文件等功能。
Greping regex keywords for quick-wins:
Greping 正则表达式关键字以快速获胜:
One of the fastest and quickest ways to achieve success in finding vulnerabilities is by looking after a list of keywords and dangerous functions that could potentially lead to weaknesses. Examples include username, password, token, system, shell_exec move_uploaded_file, file_get_contents, and other equivalent functions.
成功发现漏洞的最快方法之一是查看可能导致弱点的关键字和危险函数列表。示例包括 username 、 、 password token system shell_exec move_uploaded_file file_get_contents 和其他等效函数。
Note: Don’t forget to adapt your keyword vocabulary to the programming language you’re researching.
注意:不要忘记根据您正在研究的编程语言调整您的关键字词汇。
Following user input using bottom-up and top-down approaches:
使用自下而上和自上而下的方法遵循用户输入:
This strategy is based on the functionality of web applications, which rely on user input and are controlled by it in order to work appropriately. For example, variables like $_GET, $_POST, $_COOKIE, and $_REQUEST are commonly used.
此策略基于 Web 应用程序的功能,这些应用程序依赖于用户输入并由其控制以正常工作。例如,常用的变量,如 $_GET 、 、 $_POST $_COOKIE 和 $_REQUEST 。
The bottom-up and top-down approaches is based on the concepts of sink and source terms. The former refer to any part of the program that may be influenced by external data, while the latter refer any input or external data that enters a system.
自下而上和自上而下的方法基于概念 sink 和 source 术语。前者是指程序中可能受外部数据影响的任何部分,而后者是指进入系统的任何输入或外部数据。
The Power of Tools
工具的力量
A Security Researcher without his tools is like a baker without his mixer gentlemens, so we need to discuss on some tools that can save us a lot of time during our research and automate our efforts.
没有工具的安全研究员就像没有混音师的面包师一样,因此我们需要讨论一些工具,这些工具可以在研究过程中为我们节省大量时间并自动化我们的工作。
One of the main thoughts that need to be in your head is – ‘How can I save time to make the process more efficient and more focused to achieving better results than the manual process?’
您需要思考的主要想法之一是 – “我怎样才能节省时间,使流程比手动流程更高效、更专注地获得更好的结果?
As discussed earlier, the process of covering line by line, code by code is very time-consuming process that we want to avoid. Therefore, we seek to apply the best fit approach presented above to the specific code project we are handle with.
如前所述,逐行、逐个代码覆盖的过程是非常耗时的过程,我们希望避免。因此,我们寻求将上面介绍的最佳拟合方法应用于我们正在处理的特定代码项目。
Let’s explore some awesome tools:
让我们来探索一些很棒的工具:
- cloc 氯氯
- graudit GR审计
- TruffleHog 松露猪
- Driftwood 浮木
cloc: 氯化物:
A cool tool that I’ve discovered recently called cloc1 (‘Count Lines of Code’) that quickly assess the files content – such as comments, blank lines, and the actual code count. This tool can give us some first imperssions on the material before we get our hands dirty with the code:
我最近发现了一个很酷的工具,叫做 cloc 1 (“计算代码行数”),可以快速评估文件内容 – 例如注释、空行和实际代码计数。这个工具可以在我们亲自动手编写代码之前,先对材料进行一些初步的处理:
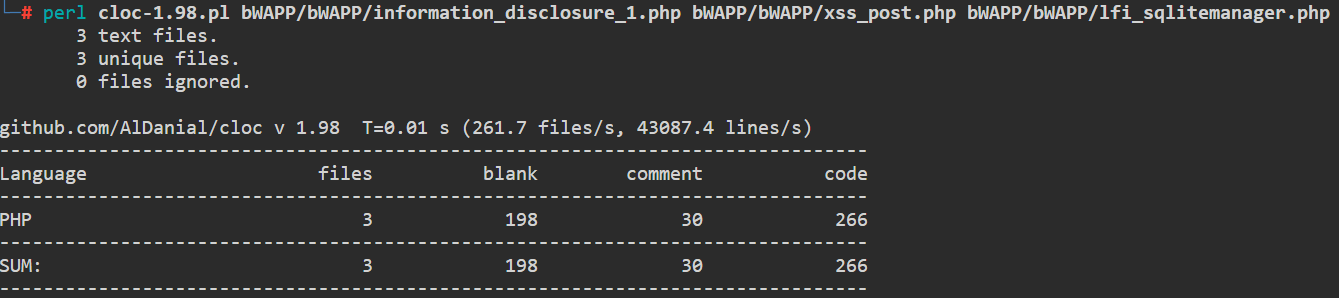
cloc categorized the code content by its counts
CLOC 按其计数对代码内容进行分类
Note: The ‘cloc –show-lang’ command will shows us the code languages that supported by this tool:
注意:’cloc –show-lang’命令将向我们显示此工具支持的代码语言:
ABAP (abap) ABAP (阿巴)
ActionScript (as) ActionScript(作为)
Ada (ada, adb, ads, pad)
艾达(ada、adb、广告、pad)
ADSO/IDSM (adso) ADSO/IDSM (adso)
Agda (agda, lagda) 阿格达 (agda, lagda)
AMPLE (ample, dofile, startup)
AMPLE (ample, dofile, 启动)
Ant (build.xml, build.xml)
蚂蚁 (build.xml, build.xml)
ANTLR Grammar (g, g4)
ANTLR 语法 (g, g4)
Apex Class (cls) Apex 类 (cls)
Apex Trigger (trigger) Apex Trigger(触发器)
APL (apl, apla, aplc, aplf, apli, apln, aplo, dyalog, dyapp, mipage)
APL(apl、apla、aplc、aplf、apli、apln、aplo、dyalog、dyapp、mipage)
Arduino Sketch (ino, pde)
Arduino Sketch (ino, pde)
AsciiDoc (adoc, asciidoc)
AsciiDoc (adoc, asciidoc)
ASP (asa, ashx, asp, axd)
ASP(asa、ashx、asp、axd)
..
graudit: GR审计:
Another tool that can save us time during our research is the graudit2 (‘grep rough audit’) tool. This tool is signature-based that utilizes a large dataset of popular programming codes. Behind the scenes, it runs predefined keywords using the grep utility with severity to identify vulnerabilities in a code section:
另一个可以在研究过程中节省我们时间的工具是 graudit 2 (“grep rough audit”)工具。该工具是基于签名的,利用了大量流行的编程代码。在后台,它使用具有严重性的 grep 实用程序运行预定义的关键字,以识别代码部分中的漏洞:
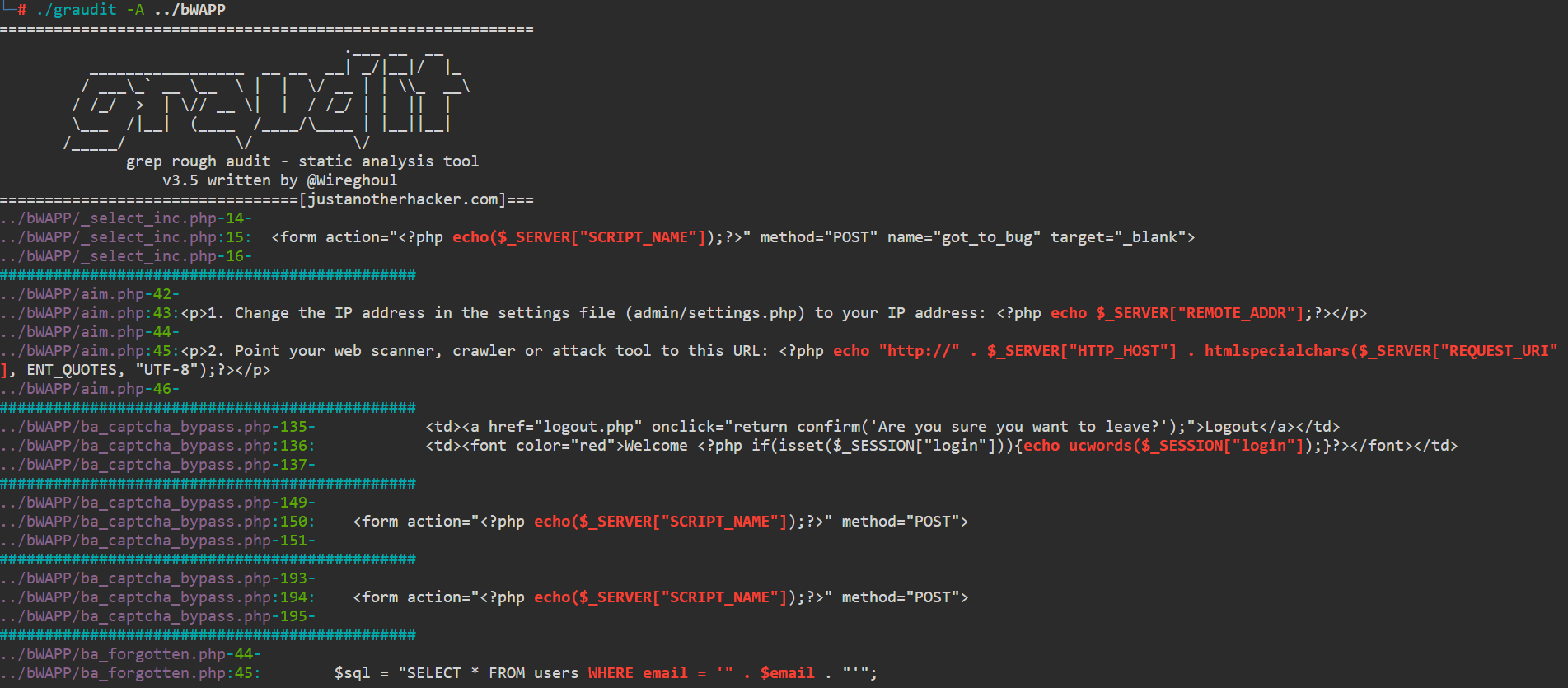
graudit detected some potential vulnerable code requiring further examination
GRDodio检测到一些潜在的易受攻击的代码,需要进一步检查
An output results of this tool could be a line focus on a function that depends on user input or an SQL statement executed without passing through a sanitation check before, or for god’s sake – existence of command execution functions that controlled by the end user:
此工具的输出结果可能是依赖于用户输入的函数的行焦点,或者是之前未通过卫生检查而执行的 SQL 语句,或者看在上帝的份上 – 存在由最终用户控制的命令执行函数:

TruffleHog 松露猪
TruffleHog3 is a powerful open-source tool designed to detect secrets and leaked credentials that might be accidentally or intentionally left behind within Git repositories or raw filesystems. It achieves this by scanning all commit histories to identify high-entropy strings, which may indicate the presence of API keys, passwords, and other types of credentials.
TruffleHog 3 是一个功能强大的开源工具,旨在检测可能意外或有意遗留在 Git 存储库或原始文件系统中的机密和泄露的凭据。它通过扫描所有提交历史记录来识别高熵字符串来实现这一点,这些字符串可能指示存在 API 密钥、密码和其他类型的凭据。
As discussed previously, our goal is to identify the quickest wins and expose the crown jewel assets, and this tool comes to help us achieving this.
如前所述,我们的目标是确定最快的胜利并展示皇冠上的明珠资产,而这个工具可以帮助我们实现这一目标。

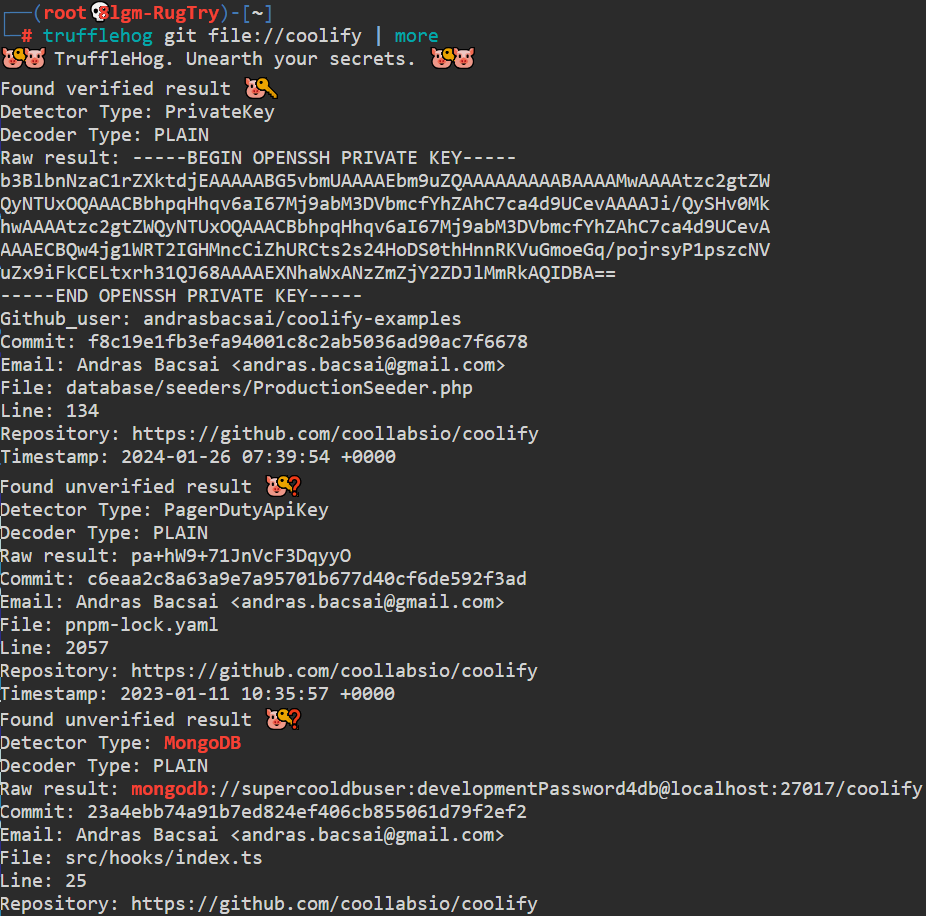
In the picture below, while running the tool against a GitHub repo, we can see the tool is able to find an exposed SSH private key, an API key of the PagerDuty asset, and even a MongoDB database connection string:
在下图中,在针对 GitHub 存储库运行该工具时,我们可以看到该工具能够找到公开的 SSH 私钥、PagerDuty 资产的 API 密钥,甚至 MongoDB 数据库连接字符串:
By the way, there is also a cool TruffleHog extension specifically built for the Google Chrome4 that monitors API keys and credentials on websites we visit. Once the extension found one, it immediately alerts with a popup on the screen:
顺便说一句,还有一个很酷的 TruffleHog 扩展程序,专门用于 Google Chrome 4 监控我们访问的网站上的 API 密钥和凭据。一旦扩展程序找到一个,它会立即在屏幕上弹出一个弹出窗口发出警报:
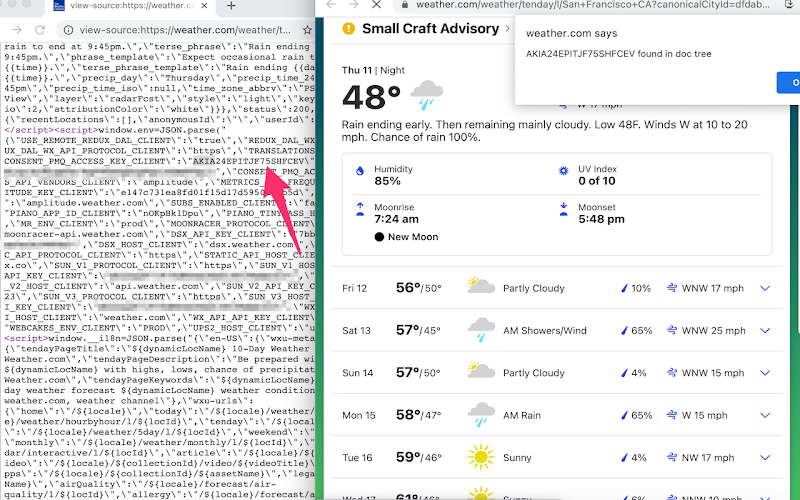
Secrets revealed without the need to dig into the source code
无需深入研究源代码即可揭示秘密
Driftwood 浮木
Additional tool from the same open-source creators is Driftwood5, which continues the process of TruffleHog’s tool output once a private key is found.
来自同一开源创建者的其他工具是 Driftwood 5 ,一旦找到私钥,它就会继续 TruffleHog 的工具输出过程。
Many times, we come a across hard-coded private SSH/TLS keys, and we’re not always certain about which asset they belong to. Private keys have a small number of use cases that typically used for TLS and SSH protocols.
很多时候,我们会遇到硬编码的私有 SSH/TLS 密钥,但我们并不总是确定它们属于哪个资产。私钥具有少量通常用于 TLS 和 SSH 协议的用例。
So, the purpose of this tool is to take a given Private Key, derive its Public Key component, and then perform lookups on a large database set of known exposed public keys in order to determine its belonging asset:
因此,此工具的目的是获取给定的私钥,派生其公钥组件,然后对已知公开公钥的大型数据库集执行查找,以确定其所属资产:
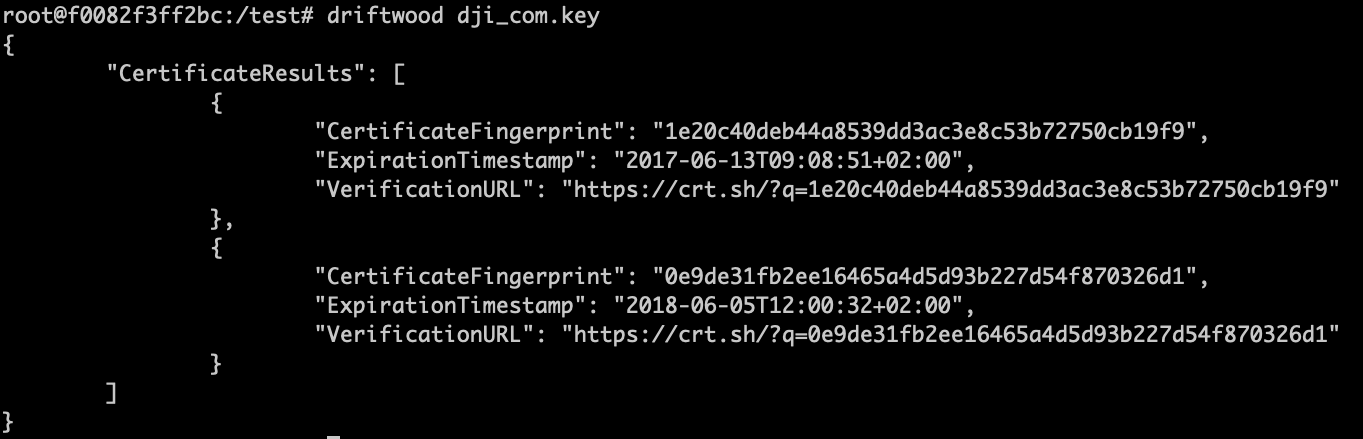
Found 2 matches of TLS certificates to a given Private Key
找到 2 个与给定私钥匹配的 TLS 证书
You can read more about here to figure out how it really works behind the scenes.
您可以在此处阅读更多相关信息,以了解它在幕后的真正工作原理。
Wrapping Up 结束语
The ideas and techniques presented in this article are just the tip of the iceberg in becoming a Code Reviewer master. I hope you learned one or two things you didn’t knew before.
本文中介绍的想法和技术只是成为 Code Reviewer 大师的冰山一角。我希望你学到了一两件你以前不知道的东西。
For those who want to take this a step further, I highly recommend the OSWE6 course by Offensive Security to gain additional hands-on practice covering all the necessary knowledge and techniques to achive this goal.
对于那些想更进一步的人,我强烈推荐 Offensive Security 的 OSWE 6 课程,以获得额外的实践练习,涵盖实现这一目标所需的所有知识和技术。
Thank you for reading!
感谢您的阅读!
Disclaimer: This material is for informational purposes only, and should not be construed as legal advice or opinion. For actual legal advice, you should consult with professional legal services.
免责声明:本材料仅供参考,不应被解释为法律建议或意见。如需实际法律意见,请咨询专业法律服务。
-
cloc – https://github.com/AlDanial/cloc. ↩
氯 – https://github.com/AlDanial/cloc。↩ -
graudit – https://github.com/wireghoul/graudit. ↩
GRaudit-https://github.com/wireghoul/graudit。↩ -
TruffleHog – https://github.com/trufflesecurity/trufflehog. ↩
松露猪 – https://github.com/trufflesecurity/trufflehog。↩ -
TruffleHog for Chrome – https://chromewebstore.google.com/detail/trufflehog/. ↩
适用于 Chrome 的 TruffleHog – https://chromewebstore.google.com/detail/trufflehog/。↩ -
Driftwood – https://github.com/trufflesecurity/driftwood. ↩
浮木 – https://github.com/trufflesecurity/driftwood。↩ -
WEB-300 – https://www.offsec.com/courses/web-300/. ↩
WEB-300 – https://www.offsec.com/courses/web-300/。↩
原文始发于haymiz@kali:Code Review Like a Pro