In part one of this series, we constructed a virtual factory using a simulation and training platform called factory.io. We included all the components needed to build a real-world assembly line in a virtual setting. To conclude this series, we’ll come to our factory from an attacker’s perspective and explain the attacks and techniques at their disposal to disrupt automation processes.
在本系列的第一部分中,我们使用名为 factory.io 的模拟和培训平台构建了一个虚拟工厂。我们包括了在虚拟环境中构建真实世界装配线所需的所有组件。作为本系列文章的最后,我们将从攻击者的角度来了解我们的工厂,并解释他们用来破坏自动化流程的攻击和技术。
We assume in our scenario started in part one that the attackers have already figured out a way to gain access to the OT network and are able to communicate with SCADA devices. Their main objective is to cause harm and disrupt the industrial process happening in our factory.
我们假设在第一部分开始的场景中,攻击者已经找到了一种访问 OT 网络的方法,并且能够与 SCADA 设备进行通信。他们的主要目标是造成伤害并破坏我们工厂发生的工业流程。
Defending against potential attackers in the industrial landscape requires understanding an adversary’s incentives and methodologies. First, let’s enumerate the different incentives that may motivate an attacker to go after an automation environment:
防御工业环境中的潜在攻击者需要了解对手的动机和方法。首先,让我们列举一下可能促使攻击者攻击自动化环境的不同诱因:
-
Financial Gain: Automation is critical to many industries and is at the core of companies’ profit and the delivery of indispensable services worldwide. An attacker seeking financial gain may disrupt a facility with little effort and, oftentimes extort victims with extravagant ransom demands. The attacker benefits from the fact that time plays against the victim because it loses revenue and profits with each passing minute without production or services up and running.
财务收益:自动化对许多行业都至关重要,是公司利润和在全球范围内提供不可或缺的服务的核心。寻求经济利益的攻击者可能会不费吹灰之力就破坏设施,并且经常以奢侈的赎金要求勒索受害者。攻击者受益于时间对受害者不利的事实,因为如果没有生产或服务启动和运行,它就会随着时间的推移而失去收入和利润。 -
Physical Process Disruption: An attacker may also seek to disrupt operations of industrial facilities from a competitive standpoint. For example, a rival factory trying to push other facilities out of business.
物理过程中断:攻击者还可能从竞争的角度寻求破坏工业设施的运营。例如,一家竞争对手的工厂试图将其他工厂赶出市场。 -
Espionage: An attacker may try to steal secrets for political or financial gain. Nation states may seek intellectual property to further their own geopolitical motives, or rival businesses may seek to put competitors at a disadvantage by stealing trade secrets.
间谍活动:攻击者可能试图窃取机密以获取政治或经济利益。民族国家可能会寻求知识产权来推进自己的地缘政治动机,或者竞争对手可能会试图通过窃取商业机密来使竞争对手处于不利地位。
Those three motivations cover the “why” attackers may target factories and other automated environments. The “how” is what we’ll cover in the remainder of this blog as we attempt to simulate an adversary’s actions and the different factory components that may be targeted in such an attack.
这三个动机涵盖了攻击者可能以工厂和其他自动化环境为目标的“原因”。“如何”是我们将在本博客的其余部分介绍的内容,因为我们试图模拟对手的行为以及此类攻击中可能针对的不同工厂组件。
MITRE ATT&CK as a Baseline
MITRE ATT&CK 作为基线
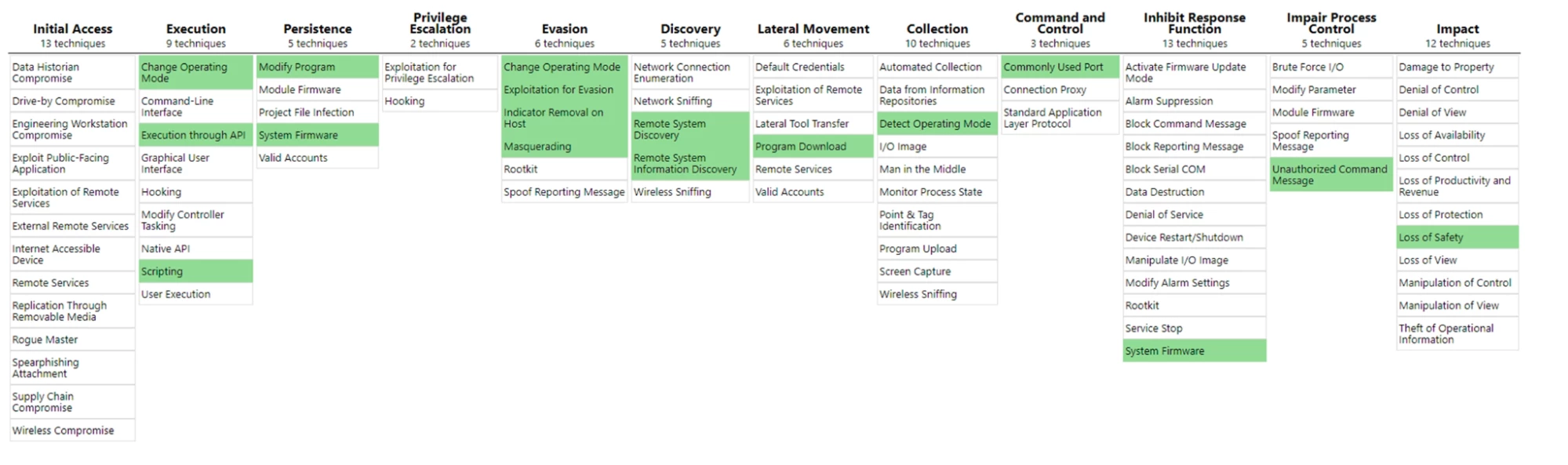
We are tracking different attacks using the MITRE ATT&CK ICS framework. This matrix is an effective tool security pros can use to identify, assess, and mitigate cyberattacks against industrial networks. For example, here are the relevant attack techniques and tactics used by the infamous Triton ICS malware.
我们正在使用 MITRE ATT&CK ICS 框架跟踪不同的攻击。该矩阵是安全专业人员可用于识别、评估和缓解针对工业网络的网络攻击的有效工具。例如,以下是臭名昭著的 Triton ICS 恶意软件使用的相关攻击技术和策略。
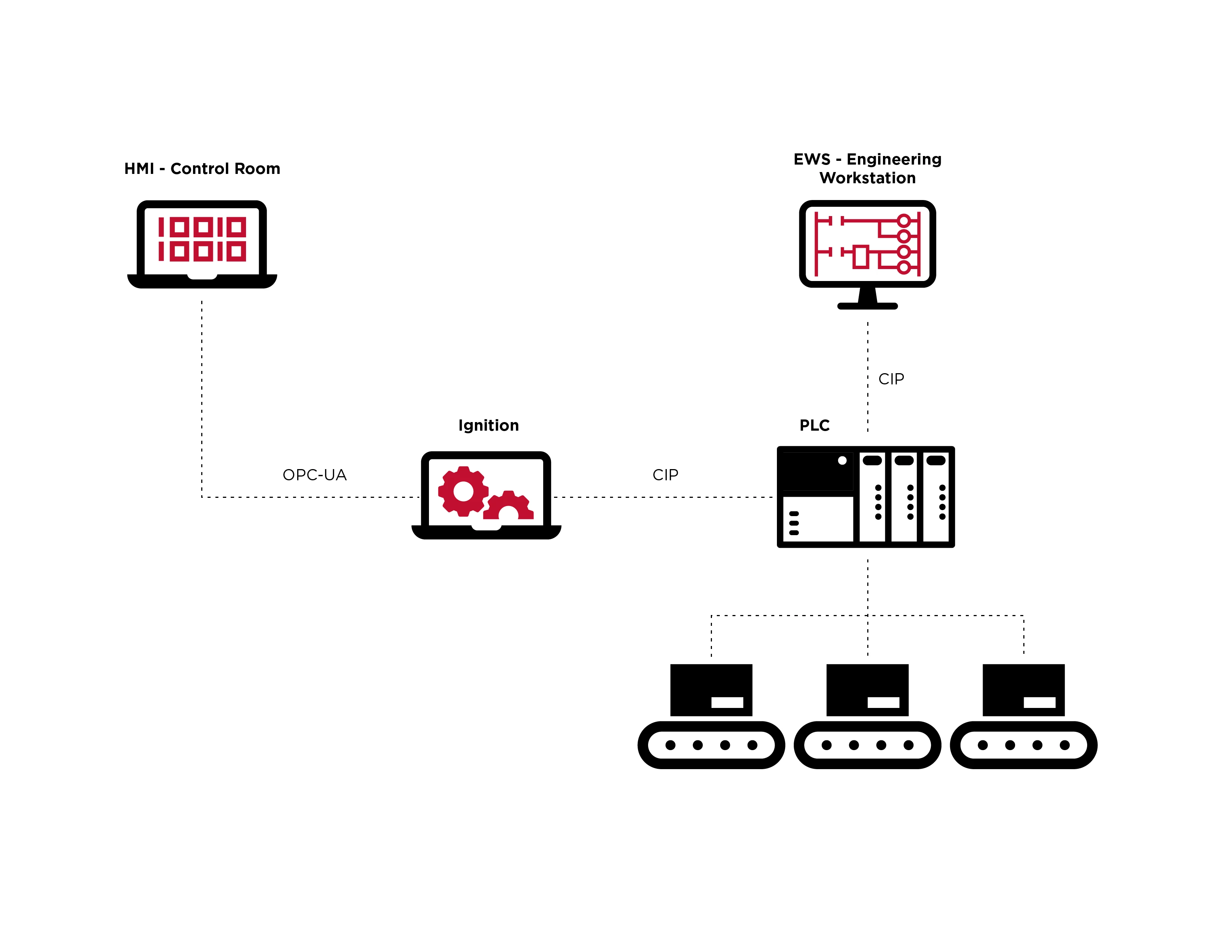
With the MITRE ATT&CK ICS framework as a reference guide, we’re going to explore a number of possible attacks and consequences that can be modeled out within our virtual factory environment. The attacks we’ll cover target different components in our factory, such as the HMI, engineering workstation, and PLCs, using a number of techniques after initial access has been established. These attacks threaten physical processes with disruption or manipulation, and can include a number of techniques explained in the framework, especially “Impair Process Control” and “Impact.”
以 MITRE ATT&CK ICS 框架为参考指南,我们将探索一些可能的攻击和后果,这些攻击和后果可以在我们的虚拟工厂环境中建模。我们将介绍的攻击针对我们工厂中的不同组件,例如 HMI、工程工作站和 PLC,在建立初始访问权限后使用多种技术。这些攻击通过破坏或操纵来威胁物理过程,并且可能包括框架中解释的许多技术,特别是“损害过程控制”和“影响”。
Here’s a rundown of our attacks and the tactics, techniques and procedures at the disposal of an attacker targeting our factory:
以下是我们的攻击以及针对我们工厂的攻击者可以使用的策略、技术和程序的概要:
Attacking The HMI 攻击 HMI
-
Memory Intervention and Modification: Changing memory of the HMI process while it is running
内存干预和修改:在 HMI 进程运行时更改其内存 -
DLL Hijacking (T0874): Replacing DLLs used by the HMI executable
DLL 劫持 (T0874):替换 HMI 可执行文件使用的 DLL -
Front End Manipulation: Changing UI artifacts presented on the HMI panel
前端操作:更改 HMI 面板上显示的 UI 工件 -
Project File Injection (T0873): Changing the Project files consisting of HMI event scripts
项目文件注入 (T0873):更改由 HMI 事件脚本组成的项目文件
Attacking The EWS 攻击 EWS
-
Memory Intervening: Changing memory of the PLC programming process while it is running to change the programs downloaded to the PLC
内存干预:在运行时更改 PLC 编程进程的内存,以更改下载到 PLC 的程序 -
DLL Hijacking (T0874): Replacing DLLs used by the Programming software executable
DLL 劫持 (T0874):替换编程软件可执行文件使用的 DLL -
Project File Injection (T0873): Changing the Project files consisting of PLC programs
项目文件注入 (T0873):更改由 PLC 程序组成的项目文件 -
Network Interception (MiTM) (T0830): Changning the PLC programs bytecode when they are being downloaded
网络拦截 (MiTM) ( T0830):在下载 PLC 程序时更改 PLC 程序的字节码
Attacking the PLC 攻击 PLC
-
Remote Code Execution (T0851): Remotely executing code natively on the PLC will enable attackers to modify the business logic while staying fully hidden in memory.
远程代码执行 (T0851):在 PLC 上远程本地执行代码将使攻击者能够修改业务逻辑,同时完全隐藏在内存中。 -
Logic Download (T0843): Modifying the logic on the controller using the commercial tools.
逻辑下载 ( T0843):使用商业工具修改控制器上的逻辑。 -
Code Hiding (T0821, T0849): Decoupling and hiding different bytecodes on the PLC while having the original source code
代码隐藏(T0821、T0849):在保留原始源代码的同时解耦和隐藏 PLC 上的不同字节码 -
Tag Manipulation (T0871): Remotely manipulating PLC tags
标签操作 (T0871):远程操作 PLC 标签

对我们的模拟工厂的成功攻击会导致我们的虚拟装配线中断和损坏。
Attacking the HMI 攻击 HMI
The HMI as presented in part one is utilized by industrial engineers to monitor and control the industrial operations in a facility. Attacking this component is beneficial when an attacker needs to masquerade active interference with the facility’s physical operation or disrupt its operation over long time periods.
工业工程师使用第一部分中介绍的 HMI 来监视和控制设施中的工业操作。当攻击者需要伪装对设施物理操作的主动干扰或长时间中断其运行时,攻击此组件是有益的。
This scenario is very problematic because without proper monitoring and maintenance issues in the factory accumulate over time without any given attention or proper treatment. The infamous Stuxnet malware was one such incident where the malware misled operators monitoring centrifuges. The operators believed the HMI, which told them the centrifuges inside the Natanz plant in Iran were operating as expected, while in fact they were spinning out of control and being irreparably damaged.
这种情况是非常有问题的,因为如果没有适当的监控和维护,工厂中的问题会随着时间的推移而积累,而没有任何给予关注或适当的处理。臭名昭著的Stuxnet恶意软件就是这样一种事件,恶意软件误导了监控离心机的操作员。操作员认为HMI告诉他们,伊朗纳坦兹工厂内的离心机按预期运行,而实际上它们正在失控并受到不可挽回的损坏。
In many cases, the first step for an attacker will be to achieve full control over the HMI. Meaning an attacker would need to find a vulnerability allowing remote control over the HMI. For example, at Pwn2Own Miami 2020, Team82 and other researchers found, demonstrated and disclosed such exploits against Inductive Automation’s Ignition, the vendor’s HMI product.
In the following section we assume the attacker already gained access to the HMI operating system. The following attacks could be used to disrupt the proper operation of an HMI, such as the one in our virtual factory.
在下一节中,我们假设攻击者已经获得了对 HMI 操作系统的访问权限。以下攻击可用于破坏 HMI 的正常运行,例如我们虚拟工厂中的 HMI。
Memory Intervening 内存干预
-
Likelihood: Low 可能性:低
-
Complexity: High 复杂度:高
-
Impact: High 影响:高
An attacker infects the host machine running the HMI process, then the attacker provides an implant that manipulates memory in the RAM of the HMI process, and misleads operators into thinking the process is running as expected.
攻击者感染运行 HMI 进程的主机,然后攻击者提供植入物来操纵 HMI 进程 RAM 中的内存,并误导操作员认为该进程正在按预期运行。
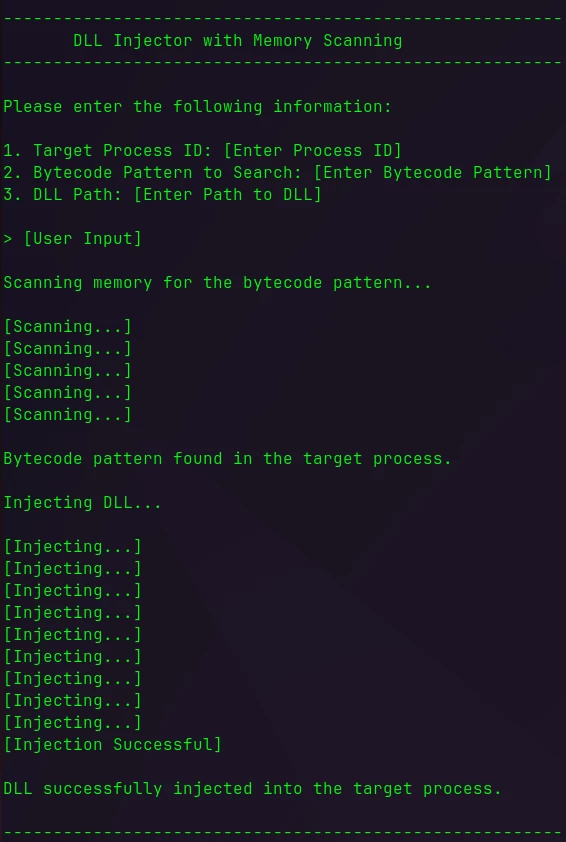
The implant the attacker brings can attach to the running HMI process and change memory content or inject a maliciously crafted DLL. This implant can utilize mechanisms used by other utilities such as Cheat-Engine, which can be used to modify raw memory, and DLL injectors.
攻击者带来的植入物可以附加到正在运行的 HMI 进程并更改内存内容或注入恶意制作的 DLL。该植入程序可以利用其他实用程序使用的机制,例如可用于修改原始内存的 Cheat-Engine 和 DLL 注入器。
DLL Hijacking
-
Likelihood: High
-
Complexity: Medium
-
Impact: High
An attacker infects the host machine running the HMI process, then the attacker injects an implant that replaces the DLL used by the HMI process to manipulate monitored values by operators.
The DLL most likely to get replaced will probably be related to handling of OPC UA communication or even to HMI event script handling.
最有可能被替换的 DLL 可能与 OPC UA 通信的处理有关,甚至与 HMI 事件脚本处理有关。
Front End Manipulation 前端操作
-
Likelihood: High 可能性:高
-
Complexity: Low-to-Medium
复杂度:低到中等 -
Impact: High 影响:高
Another method an attacker might employ is to intercept WebSocket responses from the Ignition HMI’s web server. The websocket is used to update the state of the gauge presented to the operator’s browser. An attacker might then manipulate the values transmitted to the client on the fly.
攻击者可能采用的另一种方法是拦截来自 Ignition HMI 的 Web 服务器的 WebSocket 响应。websocket 用于更新呈现给操作员浏览器的仪表的状态。然后,攻击者可能会动态操纵传输到客户端的值。
As a demonstration, we could launch our panel browser and proxy the web traffic through burpsuite in order to intercept WebSocket packets and manipulate the value presented in the operator panel.
作为演示,我们可以启动面板浏览器并代理 Web 流量 burpsuite ,以拦截 WebSocket 数据包并操作操作面板中显示的值。
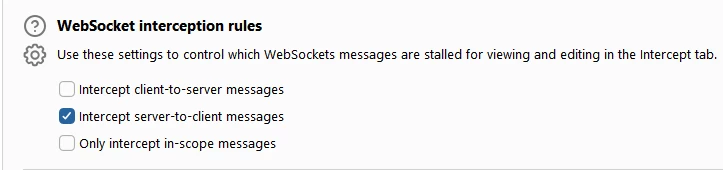
在 burpsuite 设置窗口中启用服务器到客户端消息的拦截。
Now we intercept the responses from the WebSocket server and manipulate the value indicating the amount of pallets handled.
现在,我们截获来自 WebSocket 服务器的响应,并操作指示已处理托盘数量的值。
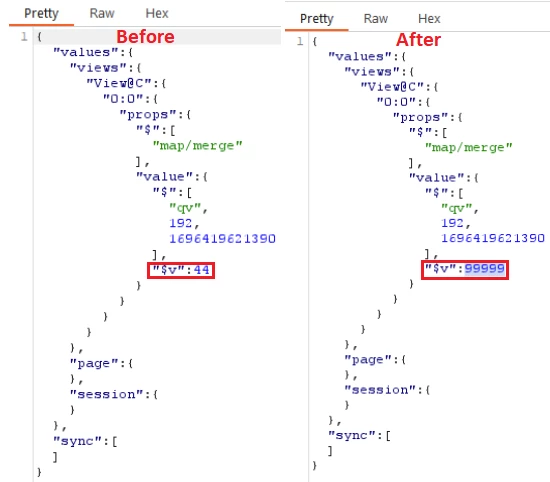
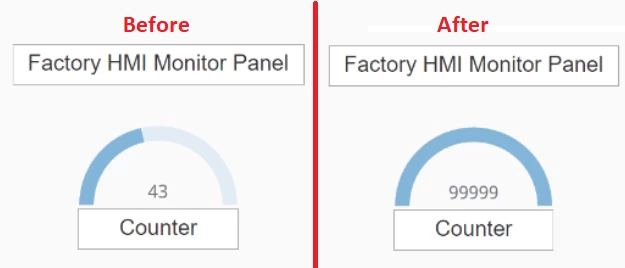
我们中断之前和之后的监控面板。
Project File Injection 项目文件注入
-
Likelihood: High 可能性:高
-
Complexity: Low-Medium 复杂度:低-中等
-
Impact: High 影响:高
Another method that might be used by attackers is to change the configuration of the project file behind the scenes, altering the logic implemented, and disrupt the HMI.
攻击者可能使用的另一种方法是在后台更改项目文件的配置,更改实现的逻辑并破坏 HMI。
In our case, the project file consists of several elements, the most important being the config.idb which contains the event scripts for our gauge artifact.
在我们的例子中,项目文件由几个元素组成,最重要的是config.idb,它包含仪表工件的事件脚本。
The sqlite3 db is located at:
sqlite3 db 位于:
C:\Program Files\Inductive Automation\Ignition\data\db\config.idb
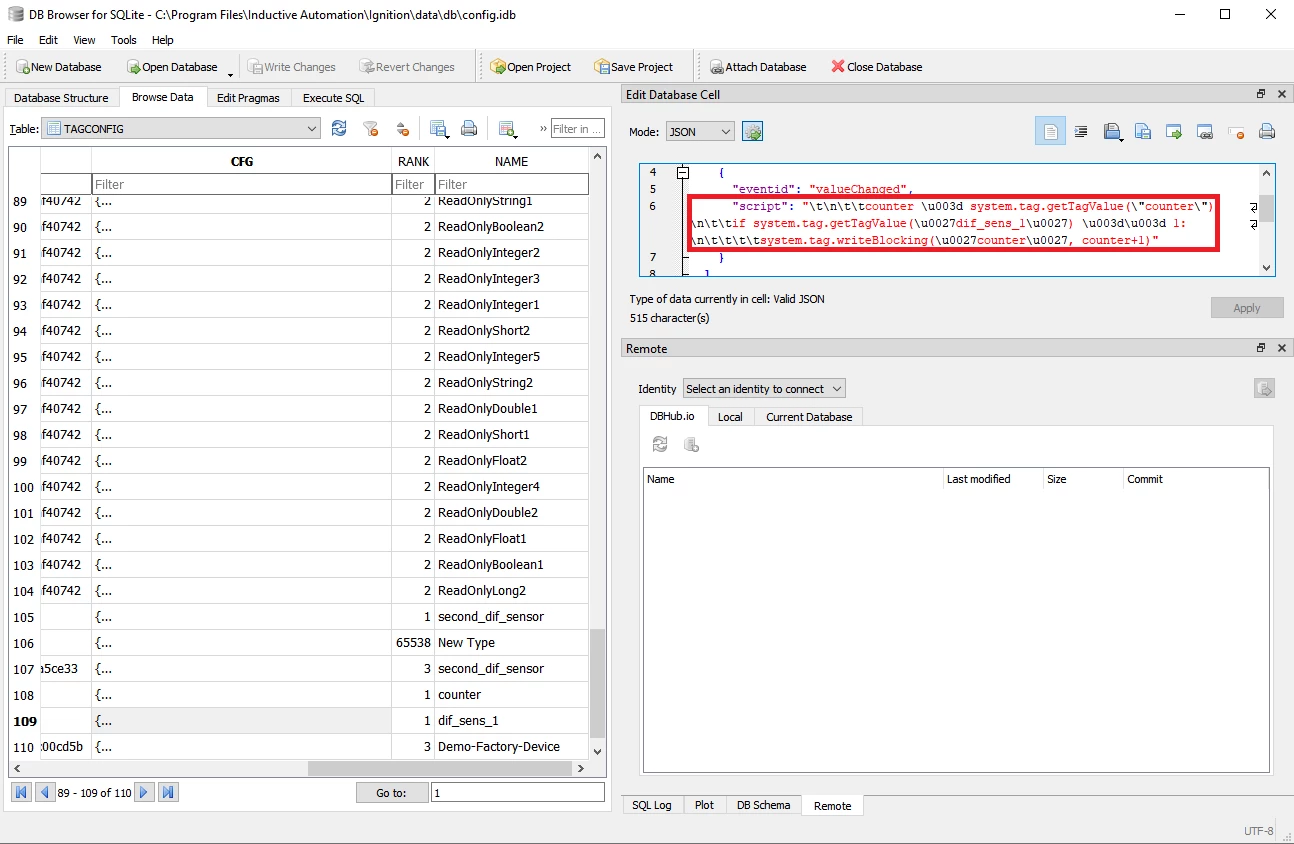
DB 浏览器中的 config.idb SQLite DB,其中突出显示了脚本内容。
Network Interception (MiTM)
网络拦截 (MiTM)
-
Likelihood: Low 可能性:低
-
Complexity: High 复杂度:高
-
Impact: High 影响:高
Another method that might be used by attackers would be to Man-In-The-Middle network traffic, which means to intercept network communication between devices on the network and actively alter transferred data. For instance, an attacker targeting our simulated factory may want to intercept transmitted traffic over the OPC UA protocol on the local network and alter the transferred information. Attacking OPC UA has also been extensively researched by Team82 and our group found and disclosed numerous vulnerabilities against this component.
攻击者可能使用的另一种方法是中间人网络流量,这意味着拦截网络上设备之间的网络通信并主动更改传输的数据。例如,以我们的模拟工厂为目标的攻击者可能希望拦截通过本地网络上的 OPC UA 协议传输的流量并更改传输的信息。Team82 也对攻击 OPC UA 进行了广泛的研究,我们的小组发现并披露了针对该组件的许多漏洞。
Attacking the EWS 攻击 EWS
The engineering workstation is a valuable target. Having control over this system allows the attacker to manipulate the PLC and change in a drastic manner its operational procedures. We observed three potential methods to influence the EWS and attack an industrial process in our virtual factory.
工程工作站是一个有价值的目标。控制该系统允许攻击者操纵 PLC 并以彻底的方式更改其操作程序。我们观察到三种潜在的方法来影响EWS并攻击我们虚拟工厂中的工业流程。
An attacker wanting to have a firm grip over any industrial operation will mostly target this component because it is where PLCs are programmed and the operation of a facility is developed, implemented and maintained. As such this component is crucial for an attacker to gain a foothold into industrial business logic.
想要牢牢控制任何工业操作的攻击者将主要针对此组件,因为它是对 PLC 进行编程以及开发、实施和维护设施操作的地方。因此,此组件对于攻击者在工业业务逻辑中站稳脚跟至关重要。
To carry out these attacks, the attacker would need to have some remote access to the workstation, mainly using a vulnerability that allows for remote control over a standard computer system, Attackers then need to elevate their privileges and gain access to the actual engineering workstation programming software, which in most cases runs as an elevated process on the computer system. Team82 has previously disclosed multiple exploits against various EWS applications.
为了进行这些攻击,攻击者需要对工作站进行一些远程访问,主要使用允许对标准计算机系统进行远程控制的漏洞,然后攻击者需要提升其权限并访问实际的工程工作站编程软件,在大多数情况下,该软件在计算机系统上作为提升的进程运行。Team82 之前曾披露过针对各种 EWS 应用程序的多个漏洞。
Memory Intervention and Modification
记忆干预和修改
-
Likelihood: Low 可能性:低
-
Complexity: High 复杂度:高
-
Impact: High 影响:高
An attacker creates a malware that infects the EWS and manipulates memory belonging to the programming process of the PLC.
攻击者创建一种恶意软件,该恶意软件会感染 EWS 并操纵属于 PLC 编程过程的内存。
This method can be executed by executing code on the engineering workstation that attaches to the PLC programming software process and in memory editing its content to manipulate the program that will be downloaded to the PLC or even blocking and locking the software.
此方法可以通过在连接到PLC编程软件进程的工程工作站上执行代码并在内存中编辑其内容以操作将下载到PLC的程序,甚至阻止和锁定软件来执行。
CLI 中 DLL 注入过程的图示。
DLL Hijacking DLL 劫持
-
Likelihood: High 可能性:高
-
Complexity: Medium 复杂度:中等
-
Impact: High 影响:高
An attacker infects the host machine running the PLC programming process, then provides an implant that replaces the DLL used by the PLC programming process to meddle with the program logic that is going to be downloaded into the PLC.
攻击者感染运行 PLC 编程进程的主机,然后提供植入程序来替换 PLC 编程进程使用的 DLL,以干扰将要下载到 PLC 中的程序逻辑。
This attack was also implemented in the famously known attack by Stuxnet malware. When Stuxnet targeted the Siemens programming software called STEP7 it replaced the s7otbxdx.dll. and by doing so managed to meddle with the programming of the PLC.
这种攻击也是在著名的Stuxnet恶意软件攻击中实施的。当Stuxnet瞄准名为STEP7的西门子编程软件时,它取代了s7otbxdx.dll。通过这样做,设法干预了PLC的编程。
Project File Injection 项目文件注入
-
Likelihood: High
-
Complexity: Medium
-
Impact: High 影响:高
A simpler way to introduce malicious code that can be effective is the manipulation of the project file bundled with the PLC program logic. An attacker can achieve this by implementing a malware that overwrites the project file consisting of the PLC program before it is downloaded to the controller.
引入可能有效的恶意代码的一种更简单的方法是操作与 PLC 程序逻辑捆绑在一起的项目文件。攻击者可以通过实施恶意软件来实现此目的,该恶意软件会在将 PLC 程序下载到控制器之前覆盖由 PLC 程序组成的项目文件。
This method is mitigated by some vendors using signature-based mechanisms that validate the project file and prevent malicious altering of the project.
某些供应商使用基于签名的机制来验证项目文件并防止恶意更改项目,从而缓解了此方法。
Network Interception (MiTM)
网络拦截 (MiTM)
-
Likelihood: High 可能性:高
-
Complexity: Medium 复杂度:中等
-
Impact: High 影响:高
Similar to project file injection, attackers can intercept the download of new programs to the PLC and manipulate their content before it reaches the target controller on the factory. This method requires the attacker to thoroughly know the protocol used to program the PLC. For instance, in our case this protocol is CIP.
与项目文件注入类似,攻击者可以拦截新程序下载到 PLC 的过程,并在其内容到达工厂的目标控制器之前对其进行操作。此方法要求攻击者彻底了解用于对 PLC 进行编程的协议。例如,在我们的例子中,这个协议是 CIP。
This form of attack has also been mitigated by implementing a better, more secure form of communication between the EWS and PLC.
通过在 EWS 和 PLC 之间实现更好、更安全的通信形式,这种形式的攻击也得到了缓解。
For example, Rockwell Automation and ODVA developed CIP Security which is a method to secure the old CIP protocol. In essence it’s a communication form that enables three security measures:
例如,罗克韦尔自动化和 ODVA 开发了 CIP Security,这是一种保护旧 CIP 协议的方法。从本质上讲,它是一种通信形式,可实现三种安全措施:
-
Integrity by allowing the rejection of altered data.
通过允许拒绝更改的数据来实现完整性。 -
Authenticity by allowing the rejection of data sent from untrusted sources.
通过允许拒绝从不受信任的来源发送的数据来确保真实性。 -
Authorization by making some requests invalid and rejected upon request.
通过使某些请求无效并在请求时被拒绝来授权。
To deploy this specific solution in an OT environment, one would need to use Rockwell’s Factorytalk Policy Manager and configure the policy for the network. For example, PLC from Zone X will be able to communicate with an HMI and an EWS from Zone Y only. During the configuration, a set of certificates will be generated and sent to each party so they could communicate over a secured channel.
要在 OT 环境中部署此特定解决方案,需要使用罗克韦尔的 Factorytalk 策略管理器并为网络配置策略。例如,来自 X 区的 PLC 将只能与 HMI 和来自 Y 区的 EWS 进行通信。在配置过程中,将生成一组证书并将其发送给每一方,以便它们可以通过安全通道进行通信。
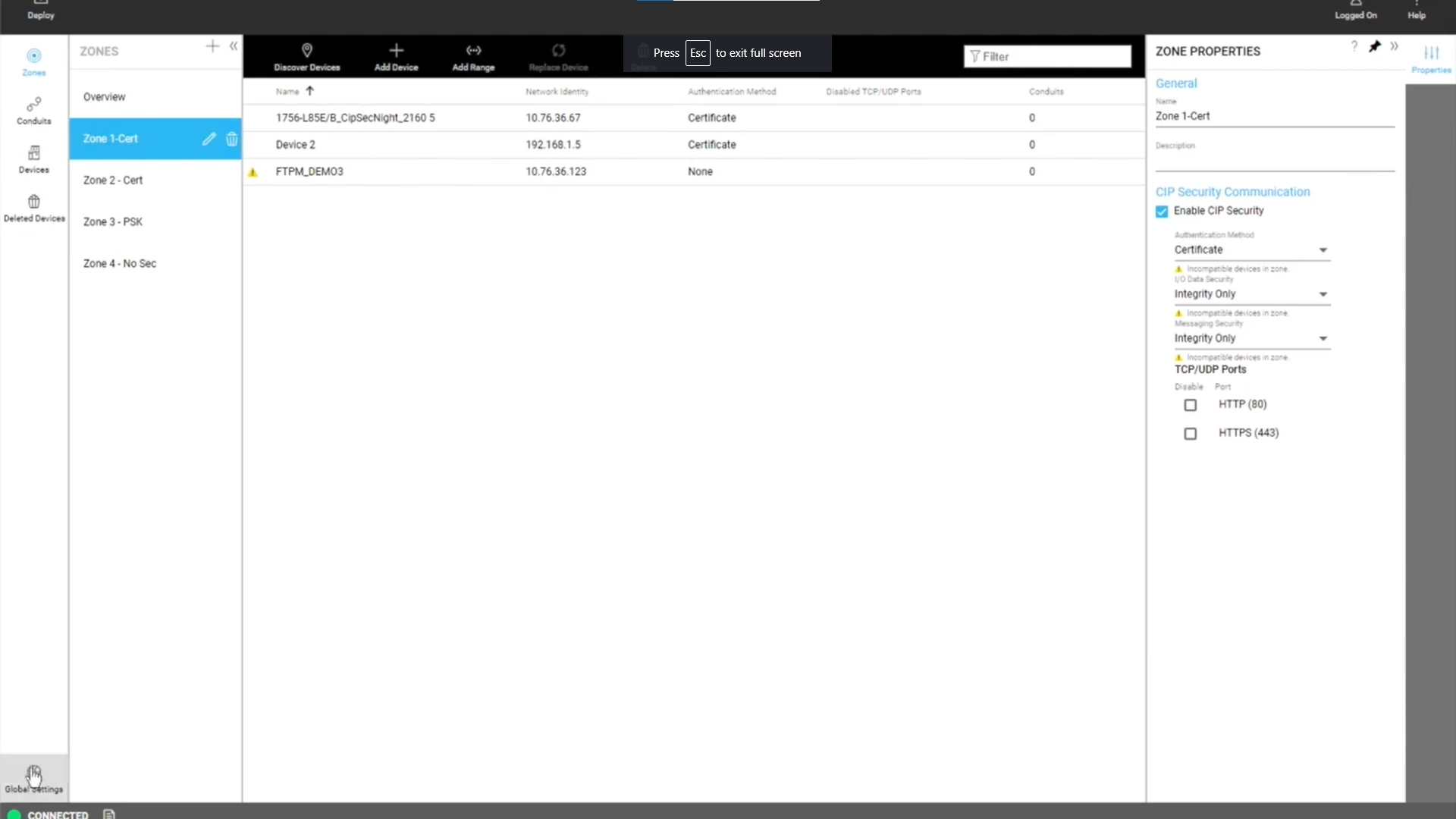
用于实施 CIP Security 的 FactoryTalk Policy Manager 软件的屏幕截图。
Attacking the PLC 攻击 PLC
The PLC is the heart of the factory. This is where business logic is translated to physical actions orchestrated by the PLC using an engineer’s code. As a component that often consists of proprietary systems, this system is both difficult to monitor for odd activity and has fine control over an industrial operation. An attacker with the ability to infect PLCs gains the advantage of being stealthy and also controlling granular aspects of a specific industrial process.
PLC是工厂的核心。在这里,业务逻辑被转换为由PLC使用工程师代码编排的物理操作。作为一个通常由专有系统组成的组件,该系统既难以监控奇怪的活动,又对工业操作有良好的控制。具有感染 PLC 能力的攻击者获得了隐蔽的优势,并且还控制了特定工业过程的细粒度方面。
The PLC is the central component controlling the process and bundles its logic. Successful attacks against the PLC can range in sophistication from remotely manipulating tags, to methods of code hiding, and download manipulations.
PLC 是控制过程的核心组件,并捆绑其逻辑。针对 PLC 的成功攻击的复杂程度可以从远程操作标签到代码隐藏方法和下载操作。
Remote Code Execution 远程代码执行
-
Likelihood: Low 可能性:低
-
Complexity: High 复杂度:高
-
Impact: High 影响:高
Attackers might find zero-day vulnerabilities allowing them to execute code remotely on the PLC. Another potential approach to execute code remotely is the installing of patched firmware on the PLC, which allows the attacker to execute arbitrary code on the PLC.
攻击者可能会发现零日漏洞,允许他们在 PLC 上远程执行代码。远程执行代码的另一种潜在方法是在 PLC 上安装修补固件,这允许攻击者在 PLC 上执行任意代码。
This attack is sophisticated because it requires an attacker to have deep understanding of the specific controller being targeted and gives the attacker firm control over the industrial process managed by the victim PLC. We’ve demonstrated this many times before, for example with CVE-2021-34566 on WAGO PFC PLCs.
这种攻击非常复杂,因为它要求攻击者深入了解所针对的特定控制器,并使攻击者能够牢牢控制由受害者 PLC 管理的工业流程。我们之前已经多次演示了这一点,例如在 WAGO PFC PLC 上的 CVE-2021-34566。
Logic Download Logic 下载
-
Likelihood: High 可能性:高
-
Complexity: Low 复杂度:低
-
Impact: High 影响:高
In many cases, attackers can easily use commercial engineering workstation software to perform a download procedure on the device and essentially modify the logic on the PLC to alter the physical process it controls.
在许多情况下,攻击者可以很容易地使用商业工程工作站软件在设备上执行下载过程,并实质上修改 PLC 上的逻辑以改变其控制的物理过程。
Modern PLCs have password protection and other security features, but from our experience, sometimes they are not enforced or can be bypassed, for example as we demonstrated in our research on Schneider M221 PLCs.
现代 PLC 具有密码保护和其他安全功能,但根据我们的经验,有时它们不会被强制执行或可以绕过,例如,正如我们在对施耐德 M221 PLC 的研究中所证明的那样。
Code Hiding 代码隐藏
-
Likelihood: Low 可能性:低
-
Complexity: High 复杂度:高
-
Impact: High 影响:高
With this kind of attack method, attackers may undermine the PLC’s logic by switching the program logic (bytecode) bundled inside the PLC and decoupling it from the real source code programmed by an industrial engineer. This technique is also showcased in a different blog post called The Old Switcheroo by our team in a much more elaborate manner. From a high level point of view, this method could be carried out in two ways:
使用这种攻击方法,攻击者可以通过切换捆绑在PLC内部的程序逻辑(字节码)并将其与工业工程师编程的真实源代码解耦来破坏PLC的逻辑。我们的团队在另一篇名为 The Old Switcheroo 的博客文章中也以更详细的方式展示了这种技术。从高层次的角度来看,这种方法可以通过两种方式进行:
-
EWS Compiler Intervening: Meddling with the compiling stage of the PLC program source code
EWS编译器介入:干预PLC程序源代码的编译阶段 -
Download Process “DIY”: Build “your own” download process by implementing the entire protocol stack. In Team82’s Evil PLC Attack, we implemented such protocol schemes for PLCs from various vendors to demonstrate a scenario in which a PLC attacks an engineering workstation.
下载过程“DIY”:通过实现整个协议栈来构建“您自己的”下载过程。在 Team82 的 Evil PLC Attack 中,我们为来自不同供应商的 PLC 实施了此类协议方案,以演示 PLC 攻击工程工作站的场景。
Tag Manipulation 标签操作
-
Likelihood: High 可能性:高
-
Complexity: Low 复杂度:低
-
Impact: High 影响:高
A “tag” refers to a label or identifier associated with a specific data point or variable within a PLC. Tags are used to uniquely identify and represent various process variables, equipment statuses, or other data points that are monitored or controlled by a SCADA system.
“标签”是指与PLC中的特定数据点或变量相关联的标签或标识符。 标签用于唯一标识和表示由SCADA系统监控或控制的各种过程变量、设备状态或其他数据点。
This enables engineers and operators to control a certain physical process just by modifying these parameters without changing the entire logic. When we read or write to tags, we usually refer to the process of Data Acquisition by which we exchange information with the SCADA system.
这使得工程师和操作员只需修改这些参数即可控制某个物理过程,而无需更改整个逻辑。当我们读取或写入标签时,我们通常是指与SCADA系统交换信息的数据采集过程。
Remotely controlling tag values on the PLC while running is a feature dedicated for control over the industrial process from remote hosts. Attackers can leverage this feature to their advantage in intervening and capturing control over an industrial process.
在运行时远程控制 PLC 上的标签值是一项专用于从远程主机控制工业过程的功能。攻击者可以利用此功能来干预和夺取对工业过程的控制权。
In our factory we use the ControlLogix5000 PLC. These controllers communicate and exchange data over CIP protocol.
在我们的工厂中,我们使用 ControlLogix5000 PLC。这些控制器通过 CIP 协议进行通信和交换数据。
This kind of attack requires a CIP client able to communicate with remote CIP servers. We will in this case make use of a helpful, simple to use, python library called pylogix. With this library we created a simple script representing what might attackers use to harm an industrial process.
这种攻击需要能够与远程 CIP 服务器通信的 CIP 客户端。在这种情况下,我们将使用一个名为 pylogix 的有用、简单易用的 python 库。通过这个库,我们创建了一个简单的脚本,表示攻击者可能用来破坏工业过程的内容。
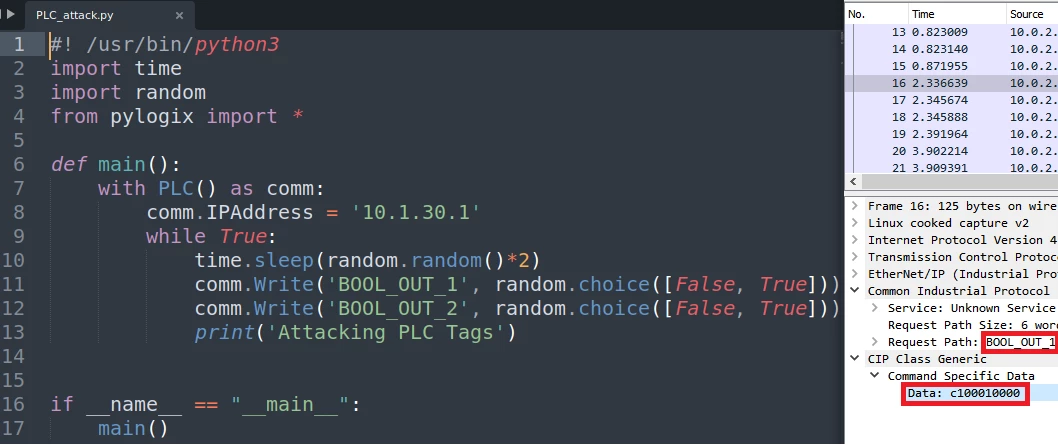
攻击者使用 pylogix 框架标记中断脚本和发送到 PLC 的 CIP 数据包的并排图像。
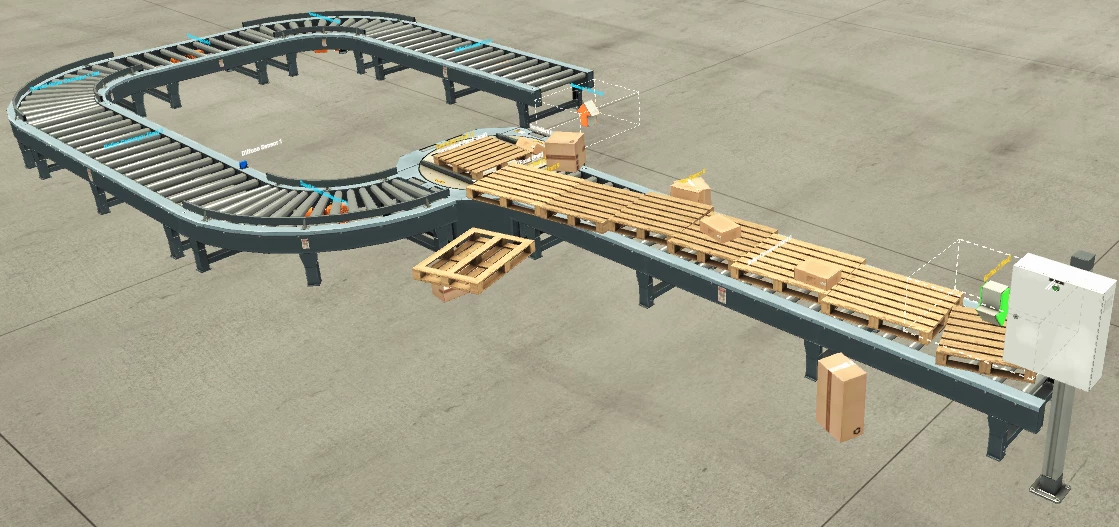
该脚本会导致自动化过程中断。
As can be seen our simple script created massive disorder in our factory and disrupted our assembly line.
可以看出,我们简单的脚本在我们的工厂中造成了巨大的混乱,并扰乱了我们的装配线。
Key Takeaways 关键要点
We started this two-part blog series by building our own virtual factory with an assembly line. We presented the different components of an industrial setting and explained their importance in an industrial process. To complete this series we shifted our focus to the security aspect of OT and automation, and surveyed multiple attack scenarios against industrial processes. These attacks range in sophistication and probability, and help us get a better understanding about this highly important realm in the aspect of cyber security.
我们通过用装配线建立自己的虚拟工厂来开始这个由两部分组成的博客系列。我们介绍了工业环境的不同组成部分,并解释了它们在工业过程中的重要性。为了完成本系列,我们将重点转移到 OT 和自动化的安全方面,并调查了针对工业流程的多种攻击场景。这些攻击的复杂程度和概率各不相同,有助于我们更好地了解网络安全方面这一非常重要的领域。
This information should be especially useful for IT cybersecurity staff who are new to OT. Using this type of modeling and scenario helps visualize where risk may need to be managed and how actual exploits can interrupt or disrupt processes managed by OT equipment and impact the bottom line.
此信息对于不熟悉 OT 的 IT 网络安全人员尤其有用。使用这种类型的建模和场景有助于可视化可能需要管理风险的地方,以及实际漏洞如何中断或破坏 OT 设备管理的流程并影响底线。
原文始发于Tomer Goldschmidt:Practical and Theoretical Attacks in the Industrial Landscape (Part 2)
转载请注明:Practical and Theoretical Attacks in the Industrial Landscape (Part 2) | CTF导航