Note: As of 2022/10/25 the information in this series is slightly outdated. See Part 5 for more up to date information.
注意:截至 2022 年 10 月 25 日,本系列中的信息略有过时。有关更多最新信息,请参阅第 5 部分。
The Car 汽车 ⌗
Last summer I bought a 2021 Hyundai Ioniq SEL. It is a nice fuel-efficient hybrid with a decent amount of features like wireless Android Auto/Apple CarPlay, wireless phone charging, heated seats, & a sunroof.
去年夏天,我买了一辆 2021 款现代 Ioniq SEL。这是一款不错的省油混合动力车,具有相当多的功能,如无线Android Auto / Apple CarPlay,无线手机充电,加热座椅和天窗。
One thing I particularly liked about this vehicle was the In-Vehicle Infotainment (IVI) system. As I mentioned before it had wireless Android Auto which seemed to be uncommon in this price range, and it had pretty nice, smooth animations in its menus which told me the CPU/GPU in it wasn’t completely underpowered, or at least the software it was running wasn’t super bloated.
我特别喜欢这辆车的一件事是车载信息娱乐 (IVI) 系统。正如我之前提到的,它有无线 Android Auto,这在这个价格范围内似乎并不常见,而且它的菜单中有相当漂亮、流畅的动画,告诉我它的 CPU/GPU 并没有完全不足,或者至少它运行的软件不是超级臃肿。
As with many new gadgets I get, I wanted to play around with it and ultimately see what I could do with it.
就像我得到的许多新小工具一样,我想玩一玩,最终看看我能用它做什么。
The Goal 目标 ⌗
The IVI in the car, like many things these days, is just a computer. My goal was to hack the IVI to get root access and hopefully be able to run my own software on it. Of course, the first step in hacking a device like this is research.
车里的IVI和现在的许多东西一样,只是一台电脑。我的目标是破解 IVI 以获得 root 访问权限,并希望能够在其上运行我自己的软件。当然,破解此类设备的第一步是研究。
Some of the obvious things that I looked up were:
我查到的一些明显的东西是:
- What is the device running?
设备正在运行什么?- There are two versions of the IVI, the navigation one that runs Android, and a Linux based one.
IVI 有两个版本,一个是运行 Android 的导航版本,另一个是基于 Linux 的版本。
- There are two versions of the IVI, the navigation one that runs Android, and a Linux based one.
- Has anyone else hacked this before?
以前有没有人破解过这个?- The Android based, navigation version is easy to hack by installing your own APKs through the engineering menu.
基于 Android 的导航版本很容易通过工程菜单安装您自己的 APK 来破解。 - The linux based one has not been hacked.
基于 linux 的尚未被黑客入侵。
- The Android based, navigation version is easy to hack by installing your own APKs through the engineering menu.
- Does the non-navigation IVI have an Engineering Mode?
非导航 IVI 是否具有工程模式?
Enginering Mode 发动机环模式 ⌗
I love developer settings and test apps. There is usually tons of fun to be had playing around with them. I thought I might even get lucky and it would have an option to enable an SSH server or the like.
我喜欢开发人员设置和测试应用程序。和他们一起玩通常会有很多乐趣。我想我什至可能会很幸运,它会有一个选项来启用 SSH 服务器或类似的东西。
I figured out with my IVI that I could enter its Engineering Mode by going to the Software Update screen, quickly pressing to the left of the Update button 10 times, and then once to the right of the button.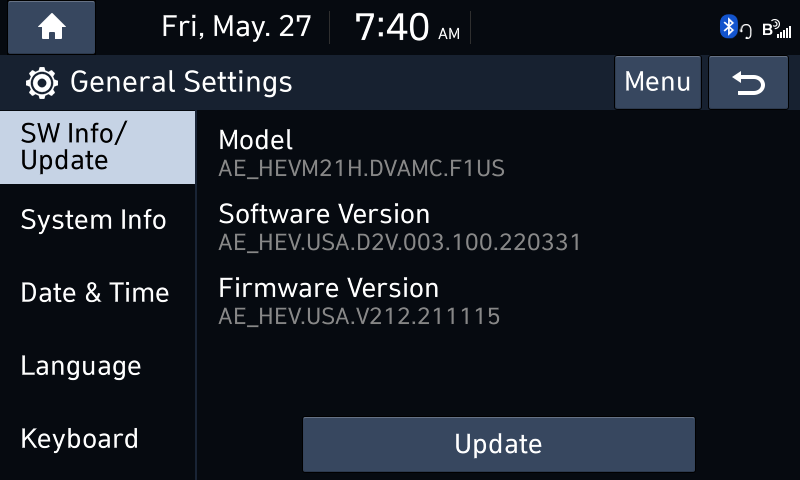 If a screen didn’t appear right away the presses would just be repeated until it worked.
If a screen didn’t appear right away the presses would just be repeated until it worked.
我用我的 IVI 发现我可以通过转到软件更新屏幕来进入其工程模式,快速按下更新按钮的左侧 10 次,然后按下按钮右侧一次。如果没有立即出现屏幕,则只会重复按压,直到它工作为止。
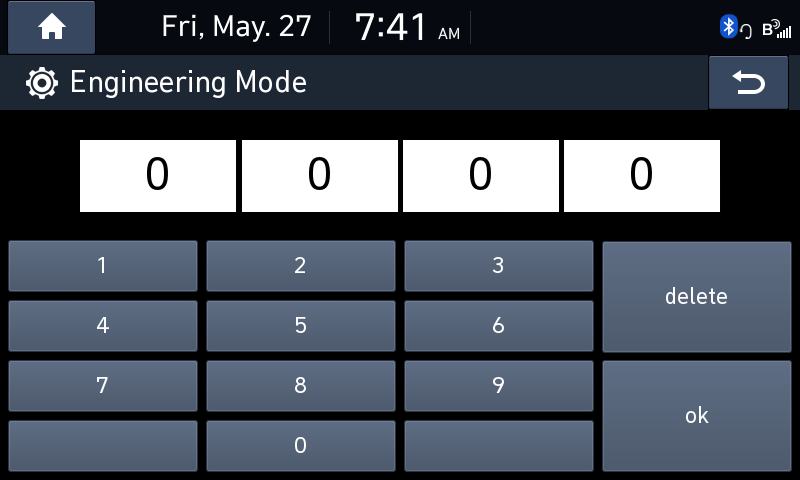
The Engineering Mode was secured by a 4 digit pin. This guide helped my figure out the pin was “2400”.
工程模式由 4 位引脚固定。本指南帮助我确定引脚是“2400”。
Upon entering the Enginering Mode I scrubbed through the menus looking at all of the available options. There were a ton of diagnostics, debug readouts, and hidden settings. A few of the menus caught my eye:
进入 Enginering 模式后,我浏览了菜单,查看了所有可用选项。有大量的诊断、调试读数和隐藏设置。一些菜单引起了我的注意:
- USB copy USB复印
- This menu had suboptions to copy logs to a USB drive or update individual parts of the system from a USB.
此菜单具有将日志复制到 USB 驱动器或从 USB 更新系统各个部分的子选项。 - One of the options indicated holding the “Radio” button on the IVI would trigger log collection too.
其中一个选项指示按住 IVI 上的“单选”按钮也会触发日志收集。
- This menu had suboptions to copy logs to a USB drive or update individual parts of the system from a USB.
- Module Info > ISV Setting
ISV 设置>模块信息- This menu had an ADB TCP option, as well as radio buttons for “SW Test Tools”.
此菜单具有 ADB TCP 选项,以及“软件测试工具”的单选按钮。
- This menu had an ADB TCP option, as well as radio buttons for “SW Test Tools”.
Using these settings I gathered a bunch of logs onto my USB drive and attempted to use ADB to connect to the IVI.
使用这些设置,我收集了一堆日志到我的 USB 驱动器上,并尝试使用 ADB 连接到 IVI。
ADB TCP 亚行 TCP ⌗
I connected my phone with wireless Android Auto to get on the IVI’s Wi-Fi network and tried to port scan the device, but I was not able to find any open ADB port. 🙁 I eventually found out this settings doesn’t really do anything.
我将手机与无线 Android Auto 连接以进入 IVI 的 Wi-Fi 网络并尝试端口扫描设备,但我无法找到任何打开的 ADB 端口。:(我最终发现这个设置并没有真正做任何事情。
The Logs 日志 ⌗
The logs turned out to be a treasure trove of information on how the IVI works under the hood.
事实证明,这些日志是关于IVI如何在引擎盖下工作的信息宝库。
The logs are transfered to the USB in one big tar.gz named “daudio2.0v_{Date}-{Time}.tar.gz”.
日志在一个名为“daudio2.0v_{Date}-{Time}.tar.gz”的大tar.gz中传输到 USB。

The archive contains many files including the kernel log, output of the “top” command, logcat logs, and the logs from BlueLink.
归档文件包含许多文件,包括内核日志、“top”命令的输出、logcat 日志和来自 BlueLink 的日志。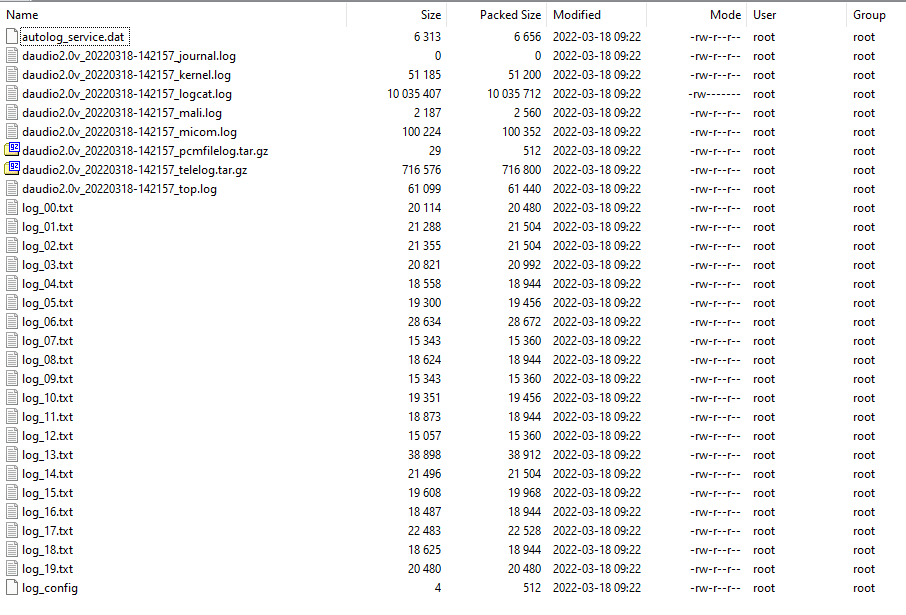
The most interesting of the log files is the logcat file. Basically every application running on the IVI is heavily logged, and all of it is piped to this file.
最有趣的日志文件是 logcat 文件。基本上,在 IVI 上运行的每个应用程序都会被大量记录,并且所有应用程序都通过管道传输到此文件。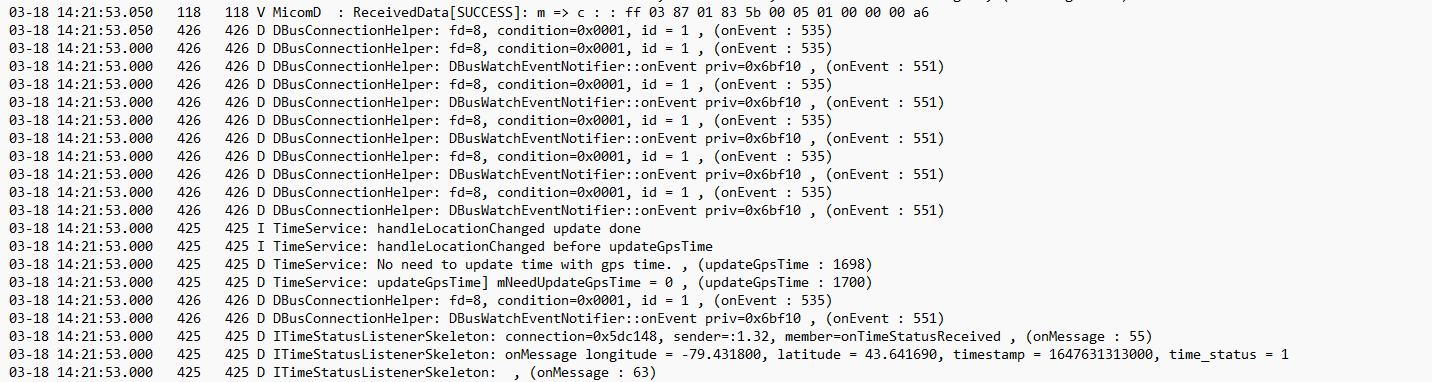
Hacking It 黑客攻击 ⌗
At that point, I knew getting into the system wasn’t going to be as easy as turning on a setting. I would need to actually exploit something to get access.
在那一刻,我知道进入系统并不像打开设置那么容易。我需要实际利用一些东西来获得访问权限。
I decided the best way to figure out how to get in was to reverse engineer the applications running on the IVI. But to do that I needed the application’s files. I figured the easiest way to do that would be simply getting a firmware update and unpacking it.
我决定弄清楚如何进入的最好方法是对在 IVI 上运行的应用程序进行逆向工程。但要做到这一点,我需要应用程序的文件。我认为最简单的方法是简单地获取固件更新并解压缩它。
The Firmware 固件 ⌗
I ended up doing some more research and skimming through logs. I found out these IVIs run “D-Audio2V” by Hyundai Mobis. D-Audio2V is the second generation of Hyundai’s Display Audio OS and is used in a variety of vehicles from Hyundai and Kia. I found that Hyundai Mobis’s site had some of D-Audio2’s source code available to download. I skimmed through it, but most of it was just minor patches to various open source projects to get the Wi-Fi system to work. The firmware updates for D-Audio2 systems was found at update.hyundai.com under “Display Audio Software Update”. Unfortunately, there was not an update for my specific vehicle, so I just downloaded the updates for a couple of other vehicles instead.
我最终做了更多的研究并浏览了日志。我发现这些 IVI 运行现代摩比斯的“D-Audio2V”。D-Audio2V 是现代汽车的第二代显示音频操作系统,用于现代和起亚的各种车辆。我发现现代摩比斯的网站上有一些 D-Audio2 的源代码可供下载。我浏览了一下,但其中大部分只是对各种开源项目的小补丁,以使 Wi-Fi 系统正常工作。D-Audio2 系统的固件更新位于“显示音频软件更新”下的 update.hyundai.com。不幸的是,我的特定车辆没有更新,所以我只是下载了其他几辆车的更新。
The firmware files came in a simple .zip file that contained another zip file. The inner zip was named enc_system_package_{version}.zip. Looking inside the system_package zip, it appears it contained the firmware for the various modules in the IVI like the GPS and HD Radio, as well as the system image itself.
固件文件位于一个简单的.zip文件中,其中包含另一个 zip 文件。内部拉链被命名为 enc_system_package_{version}.zip。查看system_package拉链内部,它似乎包含IVI中各种模块的固件,如GPS和HD Radio,以及系统映像本身。
The update was looking promising, I attempted to extract the system image and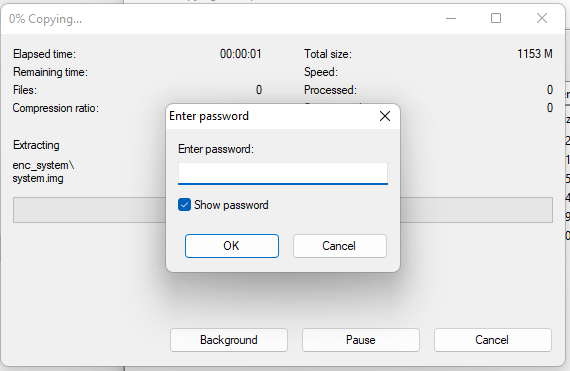 The entire zip was encrypted.
The entire zip was encrypted.
更新看起来很有希望,我试图提取系统映像,整个zip都被加密了。
I wasn’t totally discouraged though, I already had some tools on my PC like John The Ripper and Hashcat which could be used to brute force zip passwords. I attempted to brute force the password up to 8 characters since that is what my system could do in a reasonable amount of time, but that didn’t work. I also attempted to use some of my wordlists, but that also failed.
不过,我并没有完全气馁,我的 PC 上已经有一些工具,例如 John The Ripper 和 Hashcat,它们可用于暴力破解 zip 密码。我试图将密码暴力破解到 8 个字符,因为这是我的系统在合理的时间内可以做到的,但这不起作用。我还尝试使用我的一些单词表,但也失败了。
(bk)Cracking it (黑色)破解它⌗
At this point I started researching other tools or services I might be able to use. That was when I came across bkcrack. Apparently traditional zip encryption can be broken using a known-plaintext attack. This means if I could find at least 12 bytes of one of the files that is inside the encrypted zip, I could potentially unencrypt the entire zip.
在这一点上,我开始研究我可能能够使用的其他工具或服务。就在那时,我遇到了 bkcrack。显然,传统的zip加密可以使用已知的明文攻击来破解。这意味着,如果我能找到加密 zip 中至少 12 个字节的其中一个文件,我就有可能解密整个 zip。
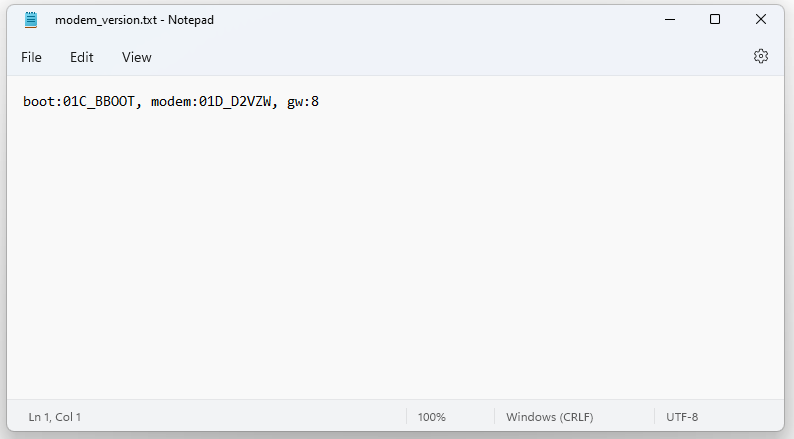
The hunt was one for a matching file. I looked through the encrypted zip’s file listing and saw a couple of good candidates for the attack. Inside the “MODEM\us” folder there was a modem_version.txt file that was 37 bytes long. Since it was a text file it was probably in a human readable format.
搜寻是针对匹配文件的搜寻。我查看了加密的 zip 文件列表,看到了几个很好的攻击候选者。在“MODEM\us”文件夹中,有一个 37 字节长的modem_version.txt文件。由于它是一个文本文件,它可能是人类可读的格式。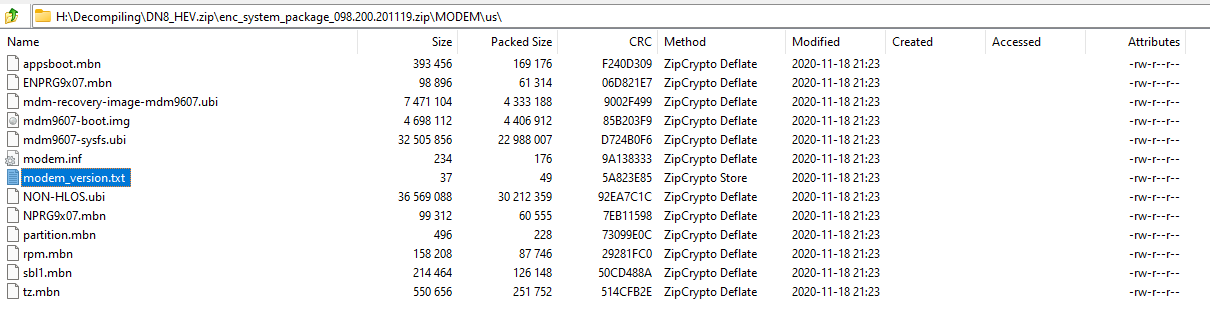
Initially I googled around for the file on the internet hoping I would find a match, but it mostly turned up dead FTP links, so I took another approach.
最初,我在互联网上搜索了这个文件,希望能找到一个匹配的文件,但它大多是死的FTP链接,所以我采取了另一种方法。
I hoped that Hyundai would reuse the modem modules in their IVIs and therefore the modem’s firmware files. If I could find an unencrypted modem update for another IVI, I could hopefully find a matching modem_version.txt file.
我希望现代汽车能够在他们的 IVI 中重用调制解调器模块,从而重用调制解调器的固件文件。如果我能找到另一个 IVI 的未加密调制解调器更新,我希望能找到匹配的 modem_version.txt 文件。
From Hyundai’s update site, I found out Hyundai has a special updater for their navigation IVIs.
从现代的更新网站上,我发现现代有一个特殊的导航IVI更新器。
I installed the Navigation Updater software and downloaded the latest update for the 2020-2021 Hyundai Ioniq Navigation IVI.
我安装了 Navigation Updater 软件并下载了 2020-2021 Hyundai Ioniq Navigation IVI 的最新更新。
I went to where the updater downloaded the files and opened up the system_package tar file.
我去了更新程序下载文件并打开system_package tar 文件的地方。
Inside there was a modem folder, and inside that was a very familar looking set of files! But the modem_version.txt file was the wrong size. 🙁
里面有一个调制解调器文件夹,里面有一组非常熟悉的文件!但是modem_version.txt文件的大小是错误的。:(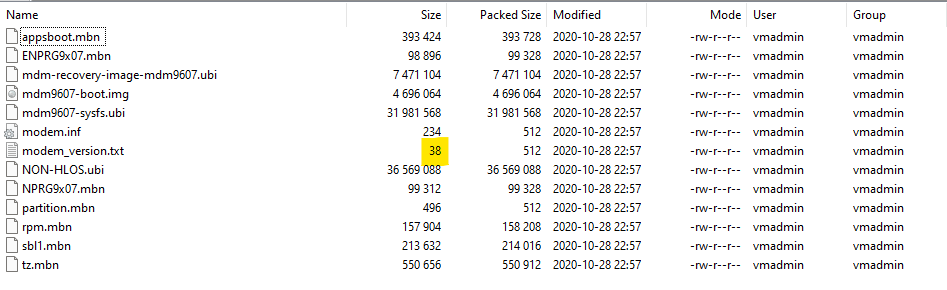
But, I knew that there were a ton of other files in there that could also be matches. But which ones were matches?
但是,我知道那里还有很多其他文件也可能是匹配的。但哪些是匹配的呢?
Comparing the two sets of files there were a few that were the same size, but there was no guarantee that the files has the same contents.
比较两组文件,有几组文件大小相同,但不能保证文件具有相同的内容。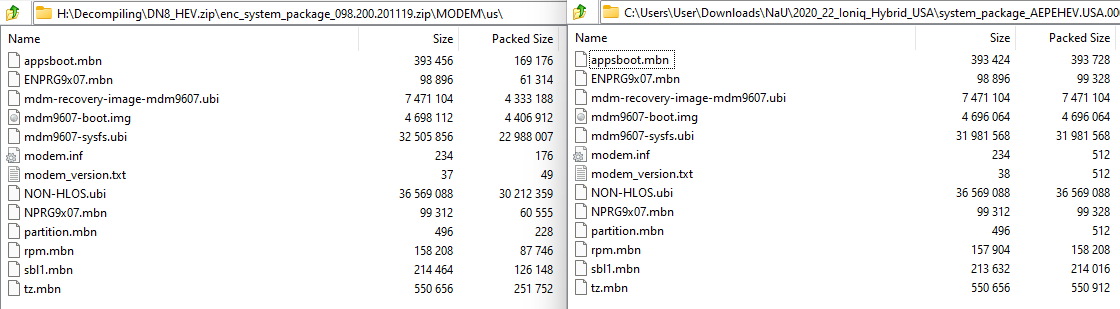
Luckily, zip came to my rescue. When a zip file is made, a CRC is calculated of each file within it. A CRC is a cyclic redundancy check which a zip extractor program uses to verify that the file was unencrypted/decompressed correctly. The same file should create the same CRC. Since the navigation’s update files were in a tar file and not a zip, I extracted them and then zipped them up. There was one pair of files that matched: “partition.mbn”. I found my plaintext.
There was one pair of files that matched: “partition.mbn”. I found my plaintext.
幸运的是,zip救了我。制作 zip 文件时,会计算其中每个文件的 CRC。CRC 是一种循环冗余检查,zip 提取程序使用它来验证文件是否正确未加密/解压缩。同一文件应创建相同的 CRC。由于导航的更新文件位于 tar 文件而不是 zip 文件中,因此我提取了它们,然后将它们压缩起来。有一对文件匹配:“partition.mbn”。我找到了我的明文。
I loaded up bkcrack with my newly found plaintext and…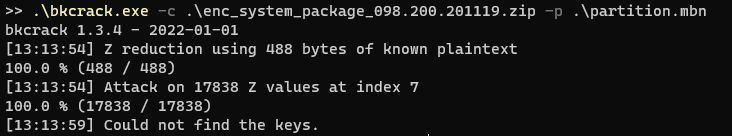 It didn’t work? But why?
It didn’t work? But why?
我用我新发现的明文加载了 bkcrack,然后……没用?但是为什么?
I ended up just throwing whatever I could at it to see if I could get some keys. As I found out, there are a lot of false positives especially if you limit bkcrack to the minimum 12 bytes of plaintext.
最后,我只能尽我所能,看看能不能拿到一些钥匙。正如我所发现的,有很多误报,特别是如果你将 bkcrack 限制在最小 12 字节的明文中。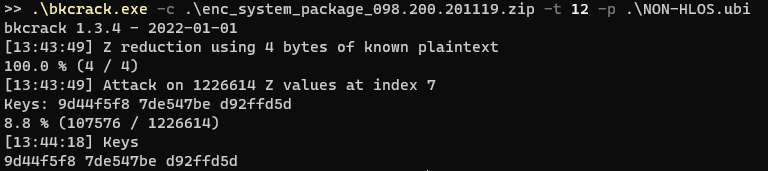
But trying to use these keys would simply result in an invalid zip file
但是尝试使用这些键只会导致无效的 zip 文件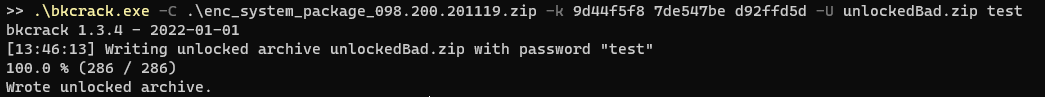
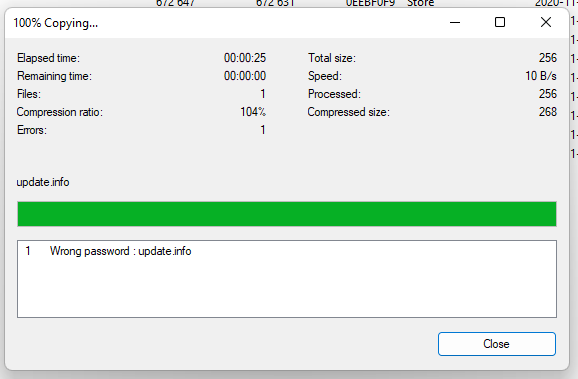
I went back to the bkcrack Github issues page and read through all of the issues. It was there I found out that the “plaintext” needed was not the original file itself, but the correctly compressed version of the original file.
我回到了 bkcrack Github 问题页面并通读了所有问题。在那里,我发现所需的“明文”不是原始文件本身,而是原始文件的正确压缩版本。
I needed to figure out the exact program and parameters that Hyundai Mobis used to compress the original zip.
我需要弄清楚现代摩比斯用来压缩原始拉链的确切程序和参数。
I zipped up my partition.mbn file using the built in zip creator in Windows. That did not work. I then tried every single combination of parameters I could in 7Zip.
我使用 Windows 中内置的 zip 创建器压缩了我的 partition.mbn 文件。那没有用。然后,我在7Zip中尝试了所有可能的参数组合。
I even made a program in C# that used a compression library to create every combination it could. But nothing worked. I figured that it was unlikely Hyundai used an esoteric Windows zip program, so I moved to Linux.
我甚至用 C# 制作了一个程序,它使用压缩库来创建它所能创建的所有组合。但没有任何效果。我认为现代不太可能使用深奥的 Windows zip 程序,所以我转向了 Linux。
I created a ton of zip files with various settings using the zip command line tool that came with my install of Kali.
我使用安装 Kali 时附带的 zip 命令行工具创建了大量具有各种设置的 zip 文件。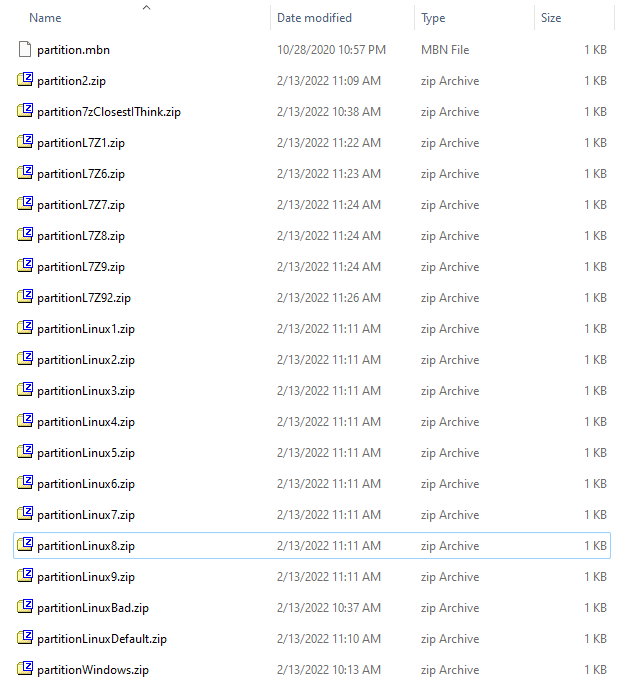
I then went through each one by one, during which I also found out I was using the wrong parameters for bkcrack. I needed to specifiy the file entry inside the zip instead of the zip itself. After going through my list multiple times and trying multiple possible keys, bkcrack found it.
然后我逐一检查了一遍,在此期间,我还发现我为 bkcrack 使用了错误的参数。我需要在 zip 中指定文件条目,而不是 zip 本身。在多次浏览我的列表并尝试多个可能的键后,bkcrack 找到了它。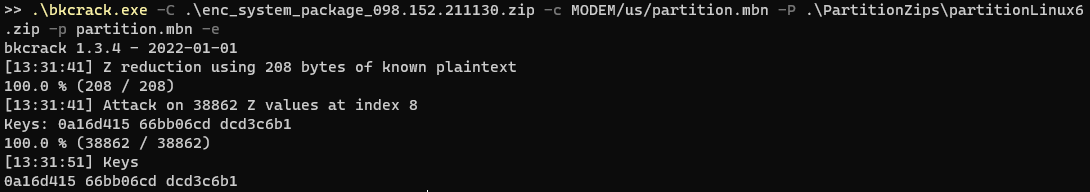
I used the “master keys” bkcrack found to make a zip and…
我使用bkcrack找到的“万能钥匙”来制作拉链和…
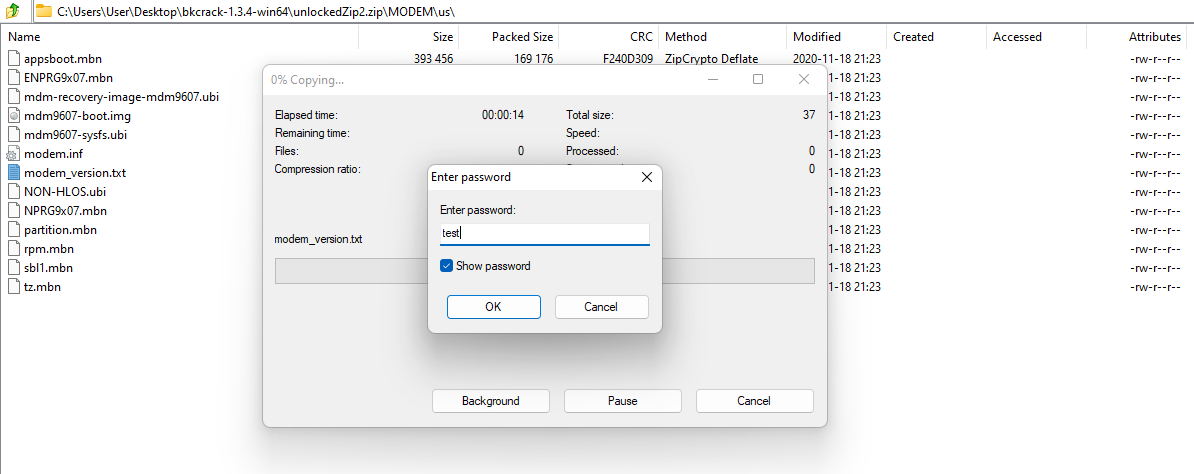
Finally? 最后?⌗
I was able to successfully extract every file from the encrypted zip!
我能够成功地从加密的zip中提取每个文件!
bkcrack also allows you to recover the password of the zip from the master keys it finds, so I tried that, but it wasn’t able to find anything up to 16 characters long which was a long as I could reasonably crack on my PC.
bkcrack还允许您从它找到的主密钥中恢复zip的密码,所以我尝试了一下,但是它找不到任何长达16个字符的内容,这是我可以在PC上合理破解的长度。
But since everything was available to me now, I extracted the system.img file that was inside the enc_system folder. I learned many things from just the files available, like how Python and Perl was installed in the system. I thought that might come in handy for making a reverse shell in the future.
但是由于现在一切都可用,因此我提取了 enc_system 文件夹中的 system.img 文件。我从可用的文件中学到了很多东西,比如 Python 和 Perl 是如何在系统中安装的。我认为这可能会在未来制作反向外壳时派上用场。
I eventually found where the apps were stored and started reverse engineering them. Luckily, since the apps had tons of debug info being printed out to the Logcat file, a lot of the important functions were trivial to label and reverse engineer.
我最终找到了应用程序的存储位置,并开始对它们进行逆向工程。幸运的是,由于这些应用程序将大量调试信息打印到 Logcat 文件中,因此许多重要功能对于标记和逆向工程来说都是微不足道的。
Network Access 网络接入 ⌗
I also found out that the driver for RTL8152/8153 USB ethernet adapters was installed.
我还发现安装了 RTL8152/8153 USB 以太网适配器的驱动程序。
I bought multiple RTL8153 based USB ethernet adapters in hope that there was some open ports. One of the adapters I bought had a built in USB hub that made it incompatible with the IVI, but the second one I bought was a direct ethernet adapter which allowed me to successfully hook up to the system. Unfortunately it only allowed me access to the CarPlay and Android Auto servers, there was no other ports available.
我购买了多个基于RTL8153的 USB 以太网适配器,希望有一些开放端口。我购买的一个适配器有一个内置的 USB 集线器,使其与 IVI 不兼容,但我购买的第二个适配器是直接以太网适配器,它允许我成功连接到系统。不幸的是,它只允许我访问 CarPlay 和 Android Auto 服务器,没有其他可用的端口。
While reverse engineering the “automotivefw” binary I found out that the ADB TCP setting in the Engineering Mode set the IP address of eth0 to 192.168.7.110.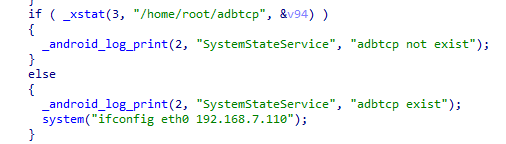 Using the logs I found out that eth0 was supposed to have a MAC address of “F4:50:EB:2E:58:00”. I hoped that if I could change the MAC address of my RTL8153 adapter I could get access to this network which would hopefully have ADB access.
Using the logs I found out that eth0 was supposed to have a MAC address of “F4:50:EB:2E:58:00”. I hoped that if I could change the MAC address of my RTL8153 adapter I could get access to this network which would hopefully have ADB access.
在对“automotivefw”二进制文件进行逆向工程时,我发现工程模式下的 ADB TCP 设置将 eth0 的 IP 地址设置为 192.168.7.110。使用日志,我发现 eth0 的 MAC 地址应该为“F4:50:EB:2E:58:00”。我希望如果我可以更改RTL8153适配器的MAC地址,我就可以访问这个网络,希望该网络可以访问ADB。
I passed my RTL dongle to my Kali VM and attempted to use ethtool to burn in a new MAC address to it. I quickly found out though that the RTL8153’s MAC address could not be edited using ethtool.
我将我的 RTL 加密狗传递到我的 Kali VM,并尝试使用 ethtool 将新的 MAC 地址刻录到它。我很快发现,RTL8153的MAC地址无法使用ethtool进行编辑。
I searched online for any tool that could help me with this, but everything I read lead me to believe that the MAC address settings on these chips could not be edited. After hours of searching online I found images of Realtek’s RtPGtoolUI utility. Based on what I could find out about it, it looked like it was the utility used by the manufacturers to setup these USB ethernet adapters, including burning in their MAC addresses. Through all of the documentation I read I also found out many of these adapters used something called EFuses instead of traditional flash storage. If my adapter used EFuses there was a chance I could not update it even with the correct tool, but I held on to hope and kept searching.
我在网上搜索了任何可以帮助我的工具,但我读到的所有内容都让我相信这些芯片上的MAC地址设置无法编辑。经过几个小时的在线搜索,我找到了 Realtek 的 RtPGtoolUI 实用程序的图像。根据我能找到的信息,它看起来像是制造商用来设置这些 USB 以太网适配器的实用程序,包括刻录他们的 MAC 地址。通过我阅读的所有文档,我还发现其中许多适配器都使用称为 EFuses 的东西,而不是传统的闪存。如果我的适配器使用 EFuses,即使使用正确的工具,我也有可能无法更新它,但我抱有希望并继续寻找。
I spent countless hours trying to find a download of the application. Eventually I found the right sketchy Chinese forum with a download.
我花了无数个小时试图找到该应用程序的下载。最终,我找到了一个合适的粗略的中文论坛,并下载了。
With a little bit of fiddling I was able to successfuly flash a new MAC address to my adapter, even though it used EFuses.
通过一点点摆弄,我能够成功地将新的MAC地址刷新到我的适配器,即使它使用了EFuses。
Network Access? 网络访问?⌗
I plugged my newly flashed ethernet adapter into my car’s USB port, only to find nothing changed. I saw no different traffic through Wireshark. I could see the MAC address change was successful, but it did not give me additional access or even an IPv4 address.
我将新刷新的以太网适配器插入汽车的 USB 端口,却发现没有任何变化。我没有看到通过 Wireshark 的不同流量。我可以看到MAC地址更改成功,但它没有给我额外的访问权限,甚至没有IPv4地址。
I scanned the 192.168.7.110 address which did point to the IVI, but it only had the same CarPlay/Android Auto ports open.
我扫描了 192.168.7.110 地址,该地址确实指向 IVI,但它只打开了相同的 CarPlay/Android Auto 端口。
After this I looked at the logs and realized that the eth0 device was some sort of built in ethernet adapter that was always offline. Whatever USB adapter I used would always appear as eth1. It was also at this point I realized that the Wi-Fi password was dumped into the logs when it was generated, meaning I could use the Wi-Fi connection instead. Connecting to the Wi-Fi yielded the same access as the ethernet adapter, except my laptop was finally given a proper IPv4 address.
在此之后,我查看了日志,并意识到 eth0 设备是某种始终处于离线状态的内置以太网适配器。无论我使用什么 USB 适配器,都将始终显示为 eth1。也是在这一点上,我意识到 Wi-Fi 密码在生成时被转储到日志中,这意味着我可以改用 Wi-Fi 连接。连接到 Wi-Fi 后,我的访问权限与以太网适配器相同,只是我的笔记本电脑最终获得了正确的 IPv4 地址。
Since the network access route was a bust and I was unable to find any backdoor or easy exploit through reverse engineering, I decided to try to take on the firmware update process.
由于网络访问路线是失败的,我无法通过逆向工程找到任何后门或轻松利用,因此我决定尝试进行固件更新过程。
Firmware Update 固件更新 ⌗
If I could figure out all of the security measures of the firmware updates, I could modify an existing system image with my own backdoors, giving me full access to the IVI.
如果我能弄清楚固件更新的所有安全措施,我就可以用自己的后门修改现有的系统映像,从而让我完全访问 IVI。
I could not find any binary within the system image that handled updating the firmware. The Engineering Mode app and the Setup app indicated once the Update button was pressed in the settings the IVI will boot into a recovery mode. Within the enc_system folder of the firmware update there was an enc_updateboot.img file. I guessed that this image contained the recovery system. Unfortunately 7Zip was not able to extract the image like the system.img file, opening up the image in Notepad++ revealed why.
Within the enc_system folder of the firmware update there was an enc_updateboot.img file. I guessed that this image contained the recovery system. Unfortunately 7Zip was not able to extract the image like the system.img file, opening up the image in Notepad++ revealed why.
我在系统映像中找不到任何处理固件更新的二进制文件。工程模式应用程序和设置应用程序指示,在设置中按下更新按钮后,IVI 将启动到恢复模式。在固件更新的 enc_system 文件夹中,有一个 enc_updateboot.img 文件。我猜这张图片包含恢复系统。不幸的是,7Zip无法像system.img文件那样提取图像,在Notepad ++中打开图像揭示了原因。
There was no readable strings, the file was encrypted. I guess that is what the “enc_” prefix meant ¯\(ツ)/¯.
没有可读的字符串,文件已加密。我想这就是“enc_”前缀的意思 ̄\(ツ)/ ̄。
Looking at the other files in the update, all of them with the “enc_” prefix was encrypted.
查看更新中的其他文件,所有带有“enc_”前缀的文件都已加密。
I was stuck once again. Without the encryption key I wouldn’t be able to figure out any more of the system update process. I decided to continue searching through all of the information I already had. I continued reverse engineering all of the apps I could, I searched through the logs I extracted, and I looked through the open-source code from Mobis’s site I downloaded earlier.
我又一次被困住了。如果没有加密密钥,我将无法再弄清楚系统更新过程。我决定继续搜索我已经拥有的所有信息。我继续对所有可能的应用程序进行逆向工程,我搜索了我提取的日志,并查看了我之前下载的摩比斯网站上的开源代码。
Did I read that right?
我没看错吗?⌗
While looking through the source code avilable from Mobis’s site, I searched for all files that were shell scripts. In the results I found a shell script file called linux_envsetup.sh.
在查看 Mobis 网站上可用的源代码时,我搜索了所有 shell 脚本文件。在结果中,我找到了一个名为 linux_envsetup.sh 的 shell 脚本文件。
This file opened up everything. Turns out this was the script that creates the system update zip file.
这个文件打开了一切。原来这是创建系统更新 zip 文件的脚本。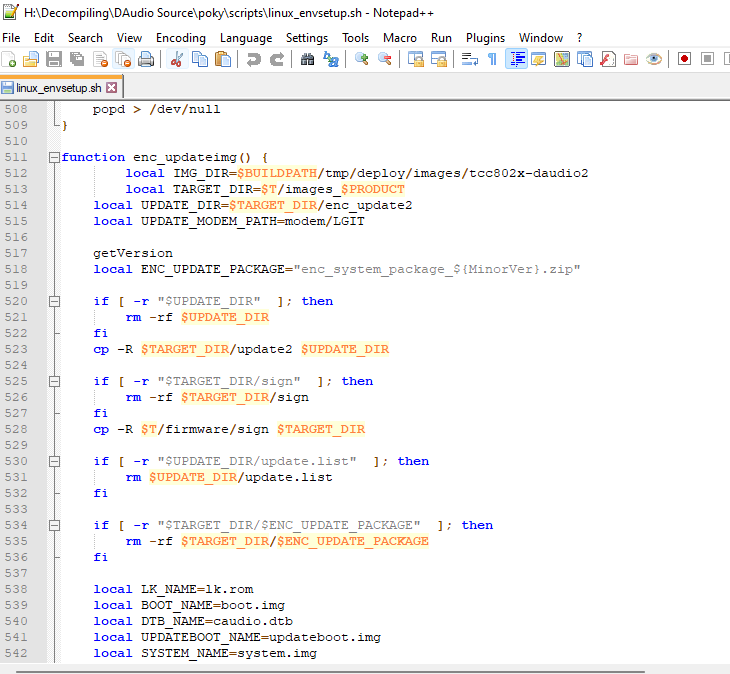
Turns out I had the zip password for the system update on my hard drive the entire time.
事实证明,我的硬盘上一直都有系统更新的zip密码。
And helpfully the encryption method, key, and IV was also in the script.
加密方法、密钥和 IV 也在脚本中。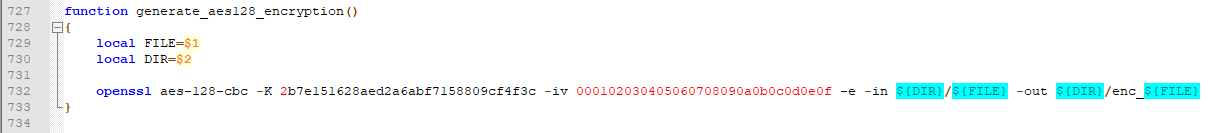
The script also hinted at RSA signing being used, but unfortunately the key used for that was not in the source code.
该脚本还暗示了正在使用 RSA 签名,但不幸的是,用于此的密钥不在源代码中。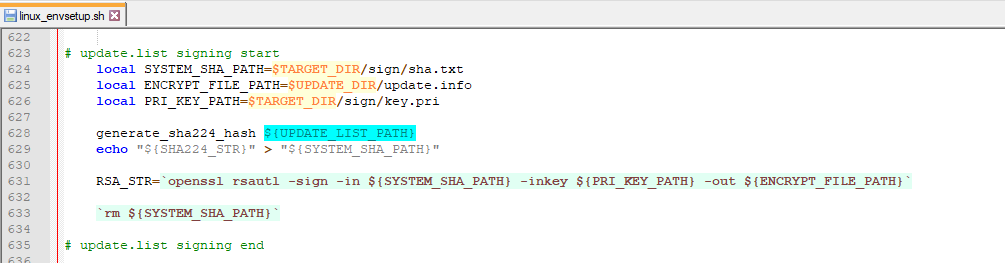
But at least I had the encryption key. To verify that no one else had gotten this far I googled the encryption key.
但至少我有加密密钥。为了验证没有其他人走到这一步,我用谷歌搜索了加密密钥。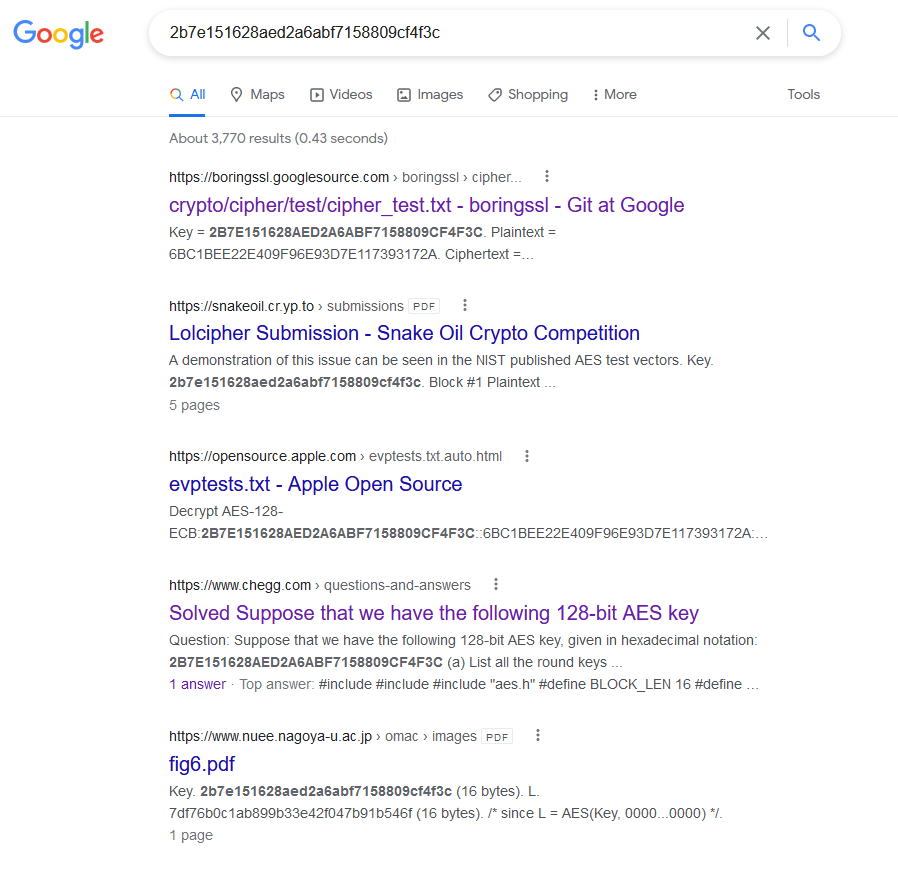
Google Git? Apple? Chegg????
谷歌 Git?苹果?切格????
Turns out the encryption key in that script is the first AES 128bit CBC example key listed in the NIST document SP800-38A.
事实证明,该脚本中的加密密钥是 NIST 文档 SP800-38A 中列出的第一个 AES 128 位 CBC 示例密钥。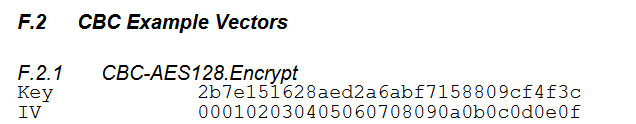
Surely Hyundai Mobis didn’t use this key and this was only used for testing, right?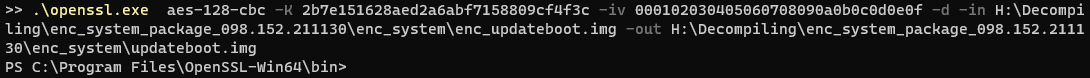 No error? No, it can’t be…
No error? No, it can’t be…
当然,现代摩比斯没有使用这把钥匙,这仅用于测试,对吧?没有错误?不,不可能……
I could open up the file in 7Zip, but it only had a single, corrupt entry.
我可以在7Zip中打开文件,但它只有一个损坏的条目。
But, running binwalk on the file revealed that the updateboot.img file was unencrypted successfully and had a ton in it.
但是,在文件上运行 binwalk 显示 updateboot.img 文件已成功解密并且包含大量文件。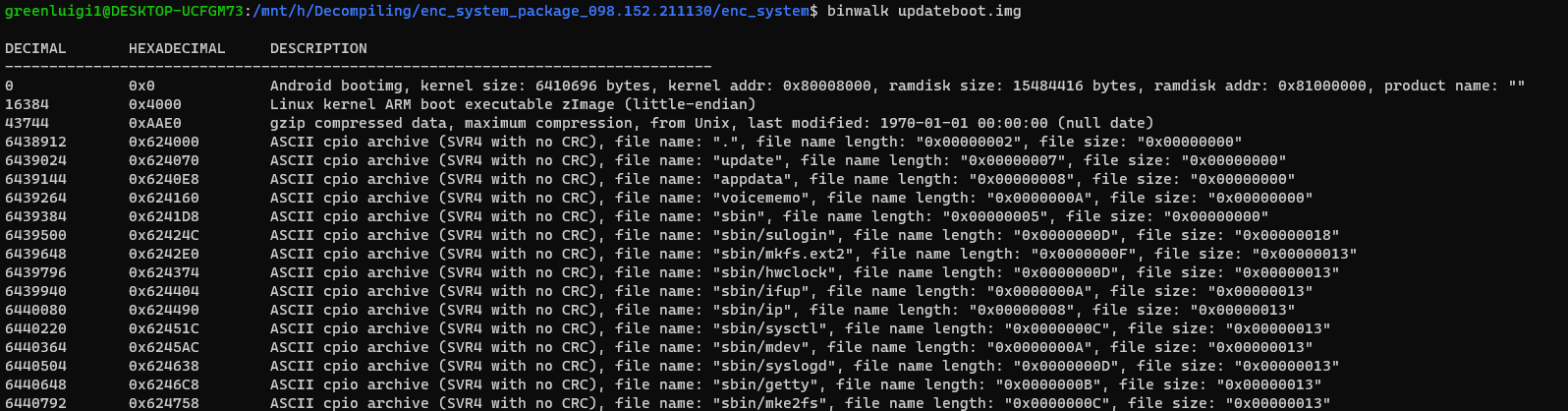
Using the -e (extract) argument with binwalk, I extracted the img file, revealing a barebones linux setup.
使用 binwalk 的 -e(提取)参数,我提取了 img 文件,揭示了准系统 linux 设置。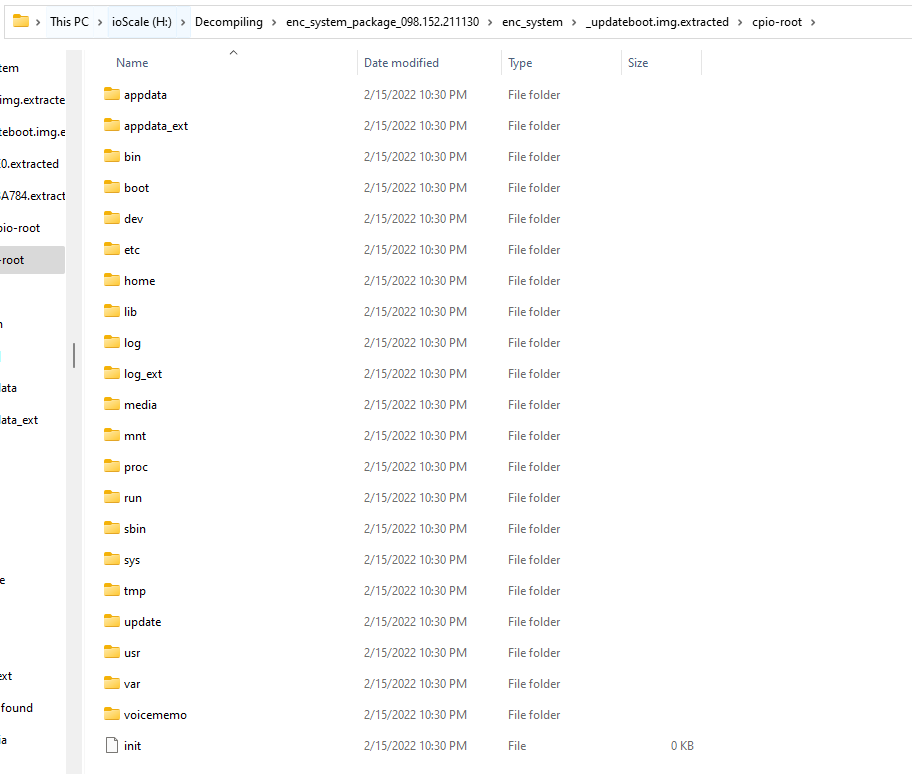
Inside the /usr/bin folder I found a binary called updateAgent which looked promising.
在 /usr/bin 文件夹中,我发现了一个名为 updateAgent 的二进制文件,它看起来很有前途。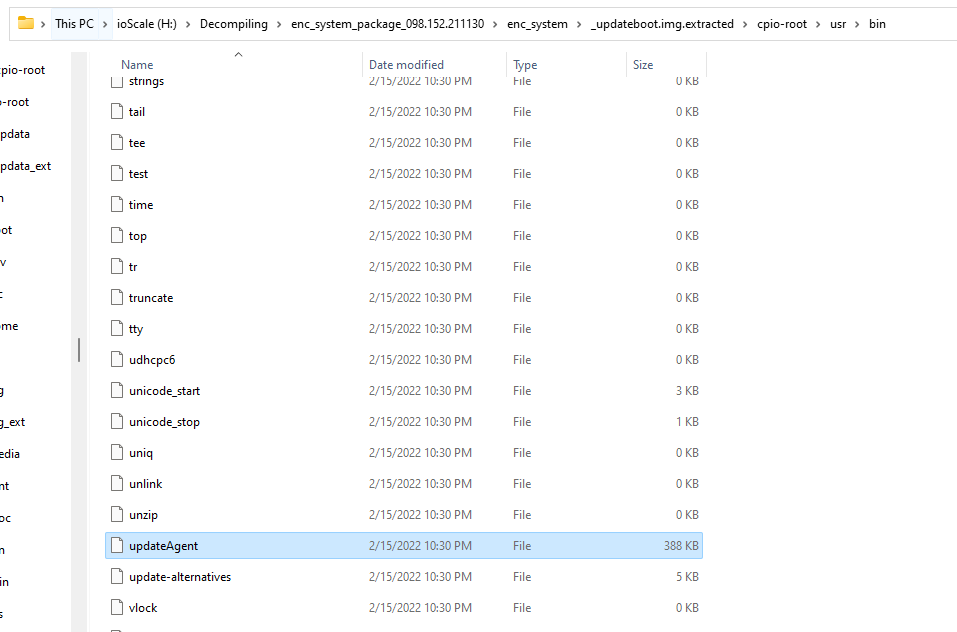
Since I already had the zip password and the encryption key, I decided to look for the signing key, with any luck they left not only the public key but the private key too.
由于我已经有了zip密码和加密密钥,我决定寻找签名密钥,幸运的是,他们不仅留下了公钥,还留下了私钥。
After searching for some keywords like “RSA” I found the public key, but no private key.
在搜索了一些关键字(例如“RSA”)后,我找到了公钥,但没有私钥。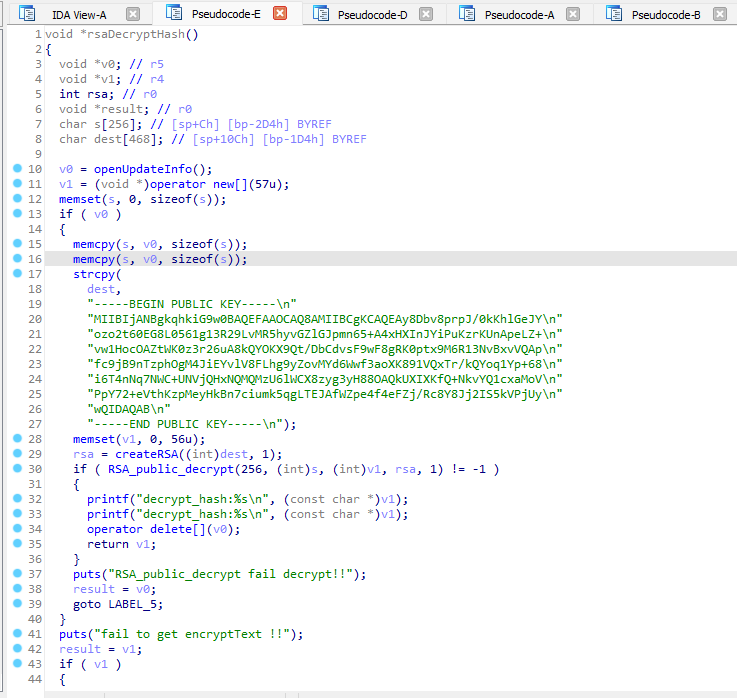
I once again googled a part of the private key as a sanity check.
我再次用谷歌搜索了私钥的一部分作为健全性检查。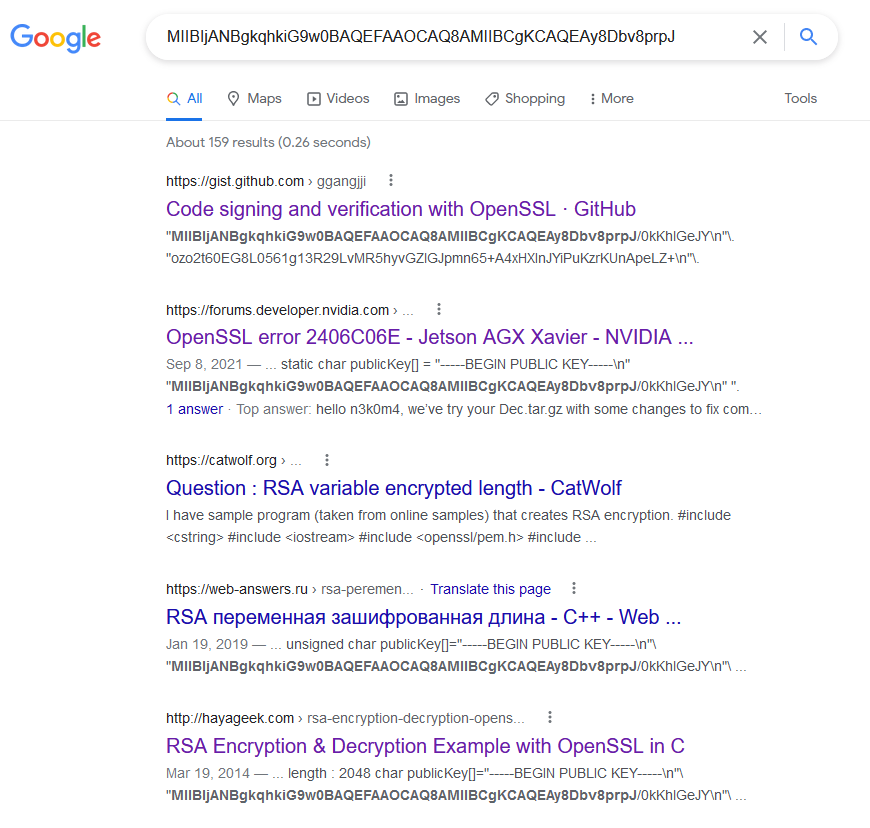
Oh, they used a very common key yet again. I have to wonder if they used that linked “RSA Encryption & Decryption Example with OpenSSL in C” tutorial…
哦,他们又用了一把非常普通的钥匙。我不得不怀疑他们是否使用了链接的“RSA加密和解密示例与C中的OpenSSL”教程…
The Waiting Game
等待游戏 ⌗
Now I had all the keys to the castle but there still wasn’t a firmware update available for my specific car. I did not want to take a chance and ruin my new car’s head unit. So I waited for an update to come.
现在我拥有了城堡的所有钥匙,但我的特定汽车仍然没有可用的固件更新。我不想冒险毁了我的新车的主机。所以我等待更新的到来。
No More Waiting⌗
不再等待 ⌗
Check out How I Hacked my Car Part 2: Making a Backdoor
查看我如何入侵我的车第 2 部分:制作后门
原文始发于Programming With Style:How I Hacked my Car