Summary 总结
Increased global trade and the growth of the Latin American (LATAM) market has made the region an increasingly attractive target for cyber criminals in recent years. The World Economic Forum noted in their January 2024 Global Cybersecurity Outlook report that LATAM had a high number of “insufficiently cyber-resilient organizations,” with government and financial institutions topping the list of targets.
近年来,全球贸易的增加和拉丁美洲 (LATAM) 市场的增长使该地区成为网络犯罪分子越来越有吸引力的目标。世界经济论坛在其 2024 年 1 月的《全球网络安全展望》报告中指出,拉丁美洲拥有大量“网络弹性不足的组织”,其中政府和金融机构位居目标之首。
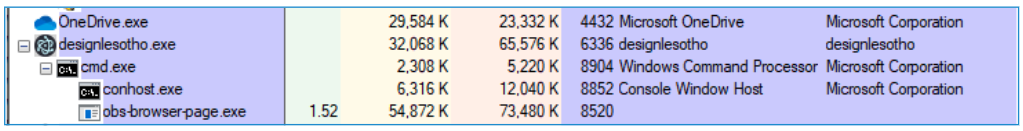
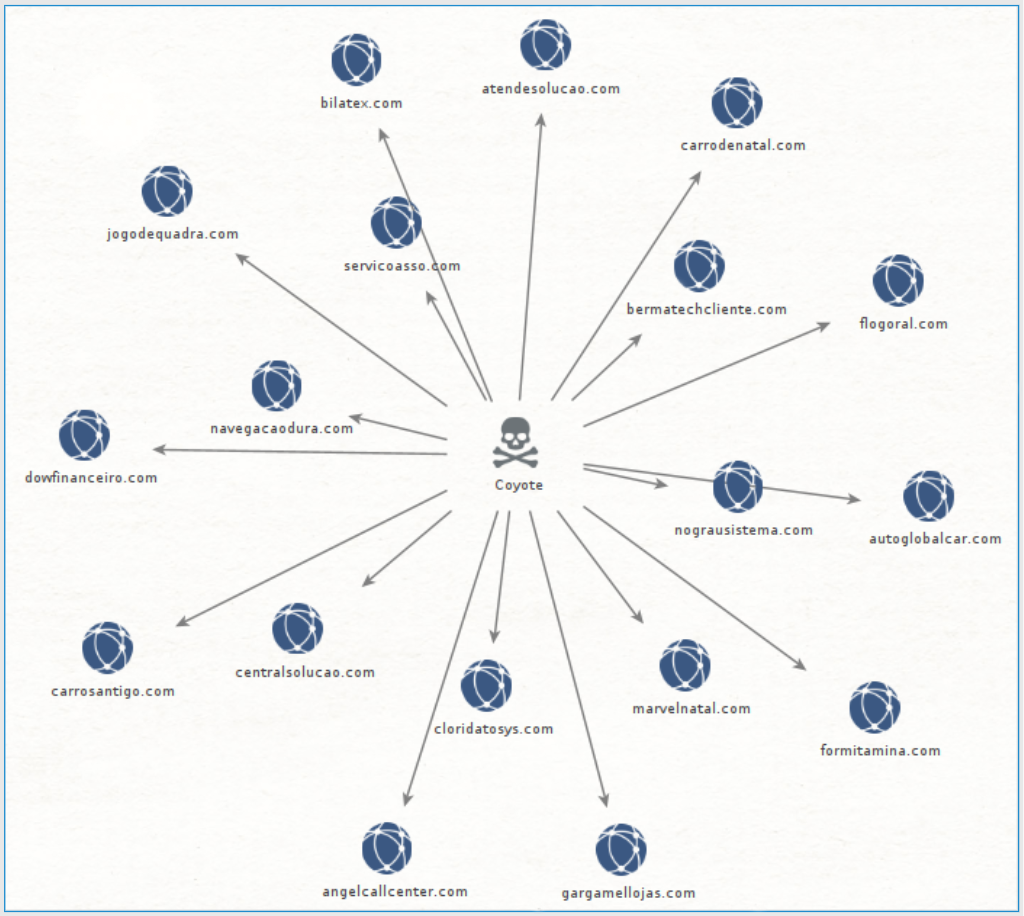
Coyote is a .NET banking Trojan that has been observed targeting Brazilian financial institutions, primarily banks. It has an execution chain that clearly distinguishes it from other banking Trojans. First identified by researchers in February 2024, Coyote got its name due to the fact it abuses Squirrel, a valid non-malicious software to manage the installation and update of Windows applications.
Coyote 是一种 .NET 银行木马,已被观察到针对巴西金融机构(主要是银行)的木马。它有一个执行链,可以清楚地将其与其他银行木马区分开来。Coyote 于 2024 年 2 月首次被研究人员发现,因其滥用 Squirrel 而得名,Squirrel 是一种有效的非恶意软件,用于管理 Windows 应用程序的安装和更新。
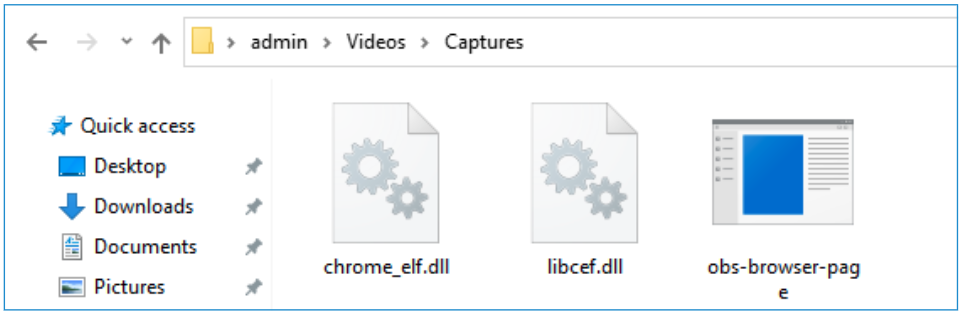
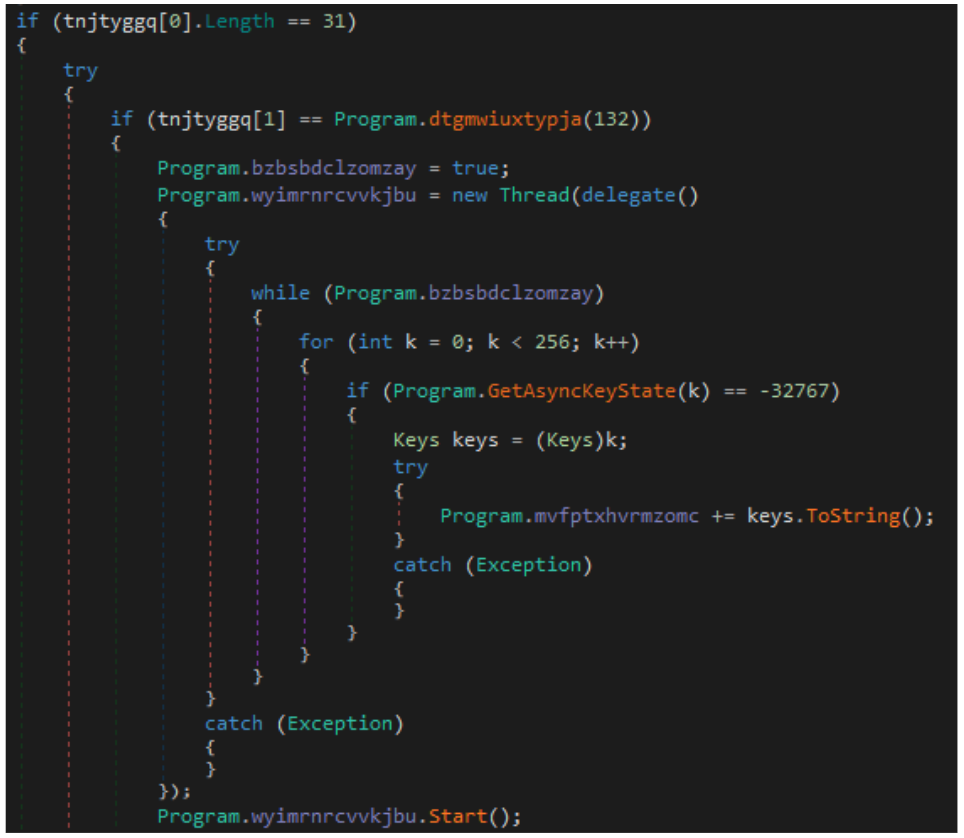
During a Coyote attack, a legitimate open-source OBS file and the Chromium Embedded Framework (CEF) dynamic linked library (DLL) are injected with a compromised DLL. The compromised DLL uses the Nim programming language to load the Coyote banking Trojan and harvest user financial information, with persistence on the system.
在 Coyote 攻击期间,合法的开源 OBS 文件和 Chromium 嵌入式框架 (CEF) 动态链接库 (DLL) 被注入了受损的 DLL。受感染的 DLL 使用 Nim 编程语言加载 Coyote 银行木马并收集用户财务信息,并在系统上持久化。
In this blog we’ll take a closer look at Coyote’s infection vector and execution chain.
在这篇博客中,我们将仔细研究 Coyote 的感染媒介和执行链。