Malware research involves studying threat actor TTPs, mapping infrastructure, analyzing novel techniques… And while most of these investigations build on existing research, sometimes they start from a hunch, something that looks too simple. At the end of 2023, we stumbled upon an installer named HotPage.exe that deploys a driver capable of injecting code into remote processes, and two libraries capable of intercepting and tampering with browsers’ network traffic. The malware can modify or replace the contents of a requested page, redirect the user to another page, or open a new page in a new tab based on certain conditions.
恶意软件研究涉及研究威胁行为者TTP、绘制基础设施图、分析新技术.虽然这些调查大多建立在现有研究的基础上,但有时它们是从直觉开始的,这看起来太简单了。在2023年底,我们偶然发现了一个名为HotPage.exe的安装程序,它部署了一个能够将代码注入远程进程的驱动程序,以及两个能够拦截和篡改浏览器网络流量的库。恶意软件可以修改或替换所请求页面的内容,将用户重定向到另一个页面,或者基于某些条件在新选项卡中打开新页面。
The installer was detected by most security products as an adware component but what really piqued our interest was the embedded driver signed by Microsoft. According to its signature, it was developed by a Chinese company named 湖北盾网网络科技有限公司 (machine translation: Hubei Dunwang Network Technology Co., Ltd), the lack of information about which was intriguing. The distribution method is still unclear but according to our research, this software was advertised as an “Internet café security solution” aimed at Chinese-speaking individuals. It purports to improve the web browsing experience by blocking ads and malicious websites, but the reality is quite different – it leverages its browser traffic interception and filtering capabilities to display game-related ads. It also sends some information about the computer to the company’s server, most likely to gather installation statistics.
安装程序被大多数安全产品检测为广告软件组件,但真正引起我们兴趣的是由Microsoft签署的嵌入式驱动程序。根据其署名,它是由一家名为湖北盾网网络科技有限公司(机器翻译:湖北盾网网络科技有限公司有限公司),缺乏有关这方面的信息是耐人寻味的。分发方式尚不清楚,但根据我们的研究,该软件被宣传为针对讲中文的个人的“网吧安全解决方案”。它声称通过阻止广告和恶意网站来改善网络浏览体验,但现实情况却完全不同-它利用其浏览器流量拦截和过滤功能来显示与游戏相关的广告。它还将有关计算机的一些信息发送到公司的服务器,最有可能收集安装统计数据。
On top of its obvious mischievous behavior, this kernel component unintentionally leaves the door open for other threats to run code at the highest privilege level available in the Windows operating system: the SYSTEM account. Due to improper access restrictions to this kernel component, any processes can communicate with it and leverage its code injection capability to target any non-protected processes.
除了其明显的恶作剧行为之外,该内核组件还无意中为其他威胁打开了大门,使其能够以Windows操作系统中可用的最高特权级别运行代码:系统帐户。由于对该内核组件的访问限制不当,任何进程都可以与它通信,并利用其代码注入功能来攻击任何不受保护的进程。
We reported this driver to Microsoft on March 18th, 2024 and followed their coordinated vulnerability disclosure process. Microsoft Security Response Center (MSRC) determined that this is no longer a vulnerability as the offending driver was removed from the Windows Server Catalog on May 1st, 2024. ESET technologies detect this threat as Win{32|64}/HotPage.A and Win{32|64}/HotPage.B.
我们于2024年3月18日 th 向Microsoft报告了此驱动程序,并遵循了他们协调的漏洞披露流程。Microsoft安全响应中心(MSRC)确定这不再是一个漏洞,因为该驱动程序已于2024年5月1日从Windows Server目录中删除。ESET技术将此威胁检测为Win{32| 64}/HotPage.A和Win{32| 64}/HotPage.B.
Who is 湖北盾网网络科技有限公司 ?
During its execution, the HotPage malware installs a driver, but before diving into the technical details of its inner workings, we wanted to learn more about the code-signing signature of this driver. What first caught our attention was the signing certificate’s owner, as illustrated in Figure 1.
在执行过程中,HotPage恶意软件会安装一个驱动程序,但在深入了解其内部工作原理的技术细节之前,我们想了解更多有关此驱动程序的代码签名签名的信息。首先引起我们注意的是签名证书的所有者,如图1所示。
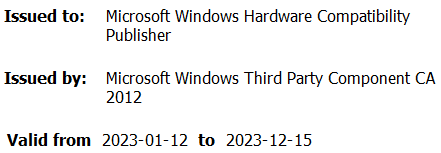
图1. HotPage驱动程序数字签名的所有者
Since the 64-bit version of Windows 7, kernel-mode drivers have been required to be signed to be loaded by the operating system. As previously detailed by Mandiant Intelligence, SentinelLabs, and G DATA teams, the signing process is built on trust but there have been cases where this was abused. It seems that the Chinese company went through Microsoft’s driver code-signing requirements and managed to obtain an Extended Verification (EV) certificate as shown in Figure 2.
自64位版本的Windows 7以来,内核模式驱动程序需要签名才能由操作系统加载。正如Mandiant Intelligence,SentinelLabs和G DATA团队之前所详细介绍的那样,签名过程是建立在信任的基础上的,但也有被滥用的情况。看起来这家中国公司通过了微软的驱动程序代码签名要求,并设法获得了扩展验证(EV)证书,如图2所示。
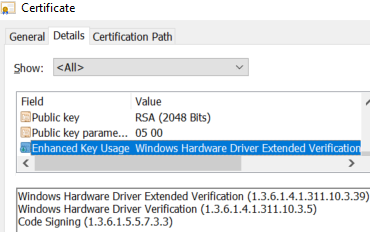
图2. HotPage驱动程序的证书扩展验证和代码签名属性
In order to retrieve the company name associated with this signature, the extraction of the signers’ attributes was necessary. Figure 3 shows the SpcSpOpusInfo attribute identified by the object ID 1.3.6.1.4.1.311.2.1.12.
为了检索与此签名相关联的公司名称,必须提取签名者的属性。图3显示了由对象ID 1.3.6.1.4.1.311.2.1.12标识的SpcSpOpusInfo属性。
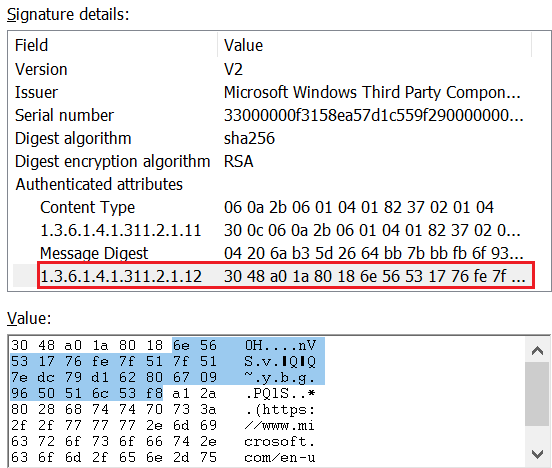
图3. HotPage驱动程序的证书SpcSpOpusInfo属性
Using the LIEF binary parser, it is possible to extract the structure member programName that identifies the company behind this signature, as displayed in Figure 4.
使用LIEF二进制解析器,可以提取标识此签名背后的公司的结构成员programName,如图4所示。
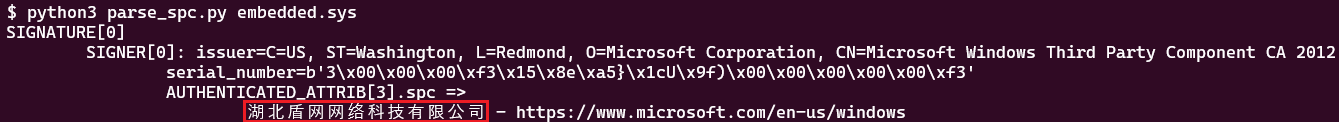
图4.从HotPage驱动程序的证书中提取公司名称
We found a reference to this company in the Windows Server Catalog, as shown in Figure 5. The company used various product categories when submitting its drivers for certification. Based on its name, it appears the company developed two network filtering programs: a netfilter component and the HotPage driver referred as adsafe or by its internal name KNewTalbeBase (Note the [Tt]albe typo, which also occurs elsewhere in the HotPage code).
我们在Windows Server Catalog中找到了对该公司的引用,如图5所示。该公司在提交其驱动程序进行认证时使用了各种产品类别。根据其名称,该公司似乎开发了两个网络过滤程序:netfilter组件和HotPage驱动程序,称为adsafe或其内部名称KNewTalbeBase(注意[Tt]albe错字,这也出现在HotPage代码的其他地方)。
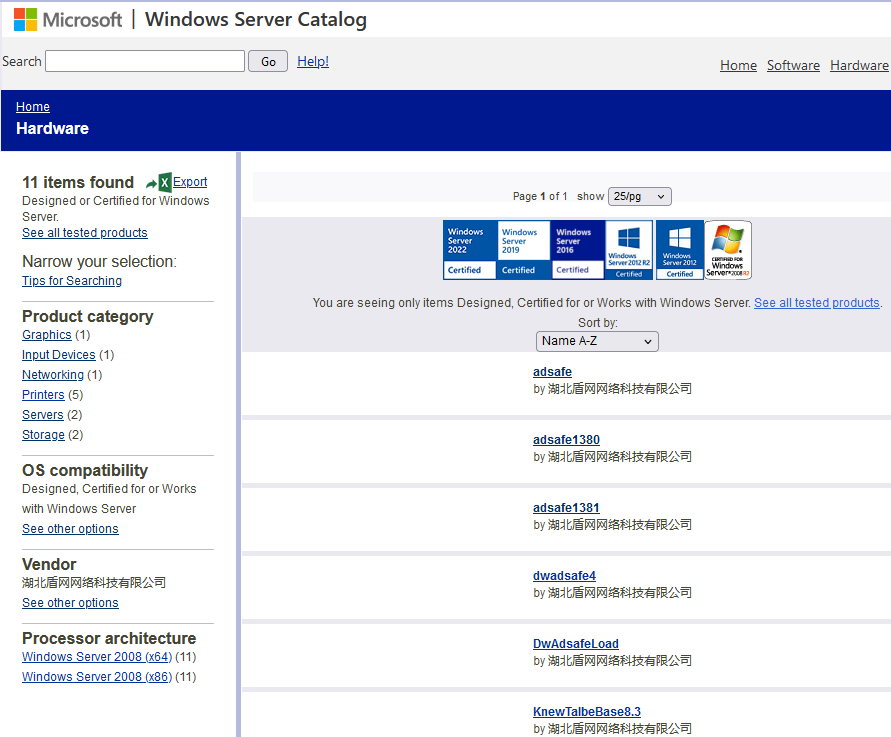
图5.中国公司在Windows Server目录中列出的认证产品
Investigating the company through search engines didn’t yield many results. According to the company register dingtalk, we discovered that the company was created on January 6th, 2022 and provided the email address dwadsafe@mail[.]io. The business scope includes: technology-related activities such as development, services, consulting, etc., but also advertising activities. As translated in Figure 6, the principal shareholder is now Wuhan Yishun Baishun Culture Media Co., Ltd, a very small company that looks to be specialized in advertising and marketing.
通过搜索引擎调查该公司并没有得到很多结果。根据公司注册dingtalk,我们发现该公司成立于2022年1月6日 th ,并提供了电子邮件地址dwadsafe@mail[。io.经营范围包括:开发、服务、咨询等与技术相关的活动,而且还有广告活动。如图6所示,主要股东现为武汉亿顺百顺文化传媒有限公司,有限公司,一个非常小的公司,看起来是专门从事广告和营销。
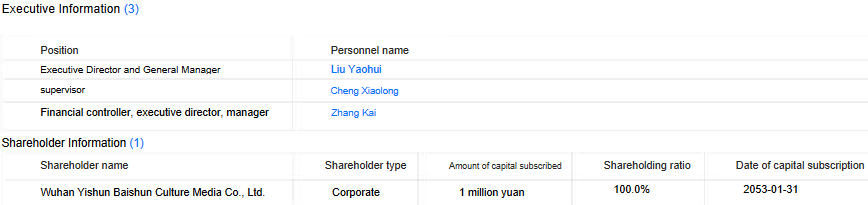
图6.翻译有关公司的执行和股东信息
From the Intellectual Property tab, we learned that in April and May 2022 the company applied for the trade name Shield Internet Café Security Defense and the website dwadsafe[.]com was created on February 22nd, 2022. The domain now resolves to localhost (127.0.0.1) and is therefore inaccessible. However, a screenshot of the website was taken on November 10th, 2023 by a web crawler, as seen in Figure 7.
从“知识产权”选项卡中,我们了解到,该公司在2022年4月和5月申请了“Shield Internet Café Security Defense”的商标名称和网站dwadsafe[。com创建于2022年2月22日 nd 。该域现在解析为localhost(127.0.0.1),因此无法访问。然而,该网站的屏幕截图是由网络爬虫在2023年11月10日 th 拍摄的,如图7所示。
图7. DWADSAFE的截图[.]由zhizhuyinqing.com制作的com网页(浅蓝色水印)
The HTTP body of the URL https://www.dwadsafe[.]com/login/reg.html (SHA-1: 744FFC3D8ECE37898A0559B62CC9F814006A1218) was also captured by VirusTotal. The source code contains the description 网吧主动防御云平台 (machine translation: Internet café active defense cloud platform). This page includes a license agreement that details the purpose of the software, albeit with contradictions. Table 1 lists some interesting bits of that information.
URL https://www.dwadsafe [.]的HTTP正文com/login/reg.html(SHA-1:744 FFC 3D 8 ECE 37898 A0559 B62 CC 9 F814006 A1218)也被VirusTotal捕获。网吧主动防御云平台(机器翻译:网吧主动防御云平台)。此页面包含一份许可协议,详细说明了软件的用途,尽管存在矛盾。表1列出了一些有趣的信息。
Table 1. Translation of the relevant parts of the license agreement
表1.许可协议相关部分的翻译
|
Original text 原文 |
Translated text (via Google Translate; emphasis ours) |
|
6、DwAdsafe作为一款主动防御系统,自身并不具有任何拦截功能,单独运行本软件不会对现有任何软件或者程序有拦截、破坏、修改等操作,也不会拦截任何病毒程序。用户只有在编写相关过滤规则后,才会开始生效;用户可以根据自己的实际需要,选择是否使用这些规则. |
6. As an active defense system, DwAdsafe does not have any interception function. Running this software alone will not intercept, destroy or modify any existing software or programs, nor will it intercept any virus programs. Only after users write relevant filtering rules will they take effect; users can choose whether to use these rules according to their actual needs. |
|
7、DwAdsafe是应用户的强烈需求而开发的:目前,有部分软件和网站的广告对用户存在较大的骚扰和误导,严重影响用户的上网体验。应广大用户提出要求,本公司开发并提供网吧环境下的安全监视、监控、过滤等功能的软件——DwAdsafe。DwAdsafe中所有的过滤规则均由网友提供并共享,通过DwAdsafe发布。用户可以根据自己的实际需要,选择是否使用这些功能。 |
7. DwAdsafe was developed in response to the strong needs of users: At present, the advertisements of some software and websites are quite harassing and misleading to users, seriously affecting users’ online experience. In response to requests from users, our company develops and provides software for security monitoring, monitoring, filtering and other functions in Internet café environments – DwAdsafe. All filtering rules in DwAdsafe are provided and shared by netizens and published through DwAdsafe. Users can choose whether to use these functions according to their actual needs. |
|
8、DwAdsafe是主动防御型软件,故包括但不限于拦截、监视、删除、结束等功能。使用DwAdsafe会对计算机信息系统的部分或全部有对应的控制及处理权限, |
8. DwAdsafe is an active defense software, so it includes but is not limited to interception, monitoring, deletion, termination and other functions. Using DwAdsafe will have corresponding control and processing authority over part or all of the computer information system. |
According to the license agreement, the software is indeed marketed as a security solution for internet cafés to block ads. However, despite the company’s claims that DwAdsafe does not have any interception capability, our investigation revealed that the software does have a rather intrusive one and comes with pre-written, unmodifiable rules.
根据许可协议,该软件确实是作为网吧屏蔽广告的安全解决方案销售的。然而,尽管该公司声称DwAdsafe没有任何拦截能力,但我们的调查显示,该软件确实具有相当侵入性的功能,并且带有预先编写的不可修改的规则。
Apart from these bits of information, the company behind this malicious component remains a mystery.
除了这些信息,这个恶意组件背后的公司仍然是一个谜。
HotPage analysis HotPage分析
In this section we describe how the different components are installed and interact with each other to achieve their purpose: injecting ads into the browser. So far, we haven’t found out how the malware was distributed but we believe, with low confidence, that it might have been bundled with another software package or advertised as a security product due to the level of privileges needed to install the driver. A few references advertising the product were found in some forums in 2022; an example is seen in Figure 8.
在本节中,我们将介绍如何安装不同的组件并相互交互以实现其目的:将广告注入浏览器。到目前为止,我们还没有发现恶意软件是如何分发的,但我们相信,由于安装驱动程序所需的特权级别,它可能与另一个软件包捆绑在一起,或者作为安全产品进行宣传。在2022年的一些论坛中发现了一些关于该产品的广告引用;图8中显示了一个示例。
![Figure 8. Mention of dwadsafe[.]com in a forum dedicated to Internet café maintenance HotPage: Story of a signed, vulnerable, ad-injecting driver](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-8-mention-of-dwadsafe-com-in-a-forum-dedicated-to-internet-cafe-maintenance.png)
图8.关于dwadsafe[.] com在一个致力于网吧维护的论坛上
The installer drops the driver on disk and starts a service to execute it. It decrypts its configuration file, which contains a list of target Chromium-based browsers and libraries. If such executables are found running or being loaded, the driver tries to inject one of the listed libraries into the browser process. After hooking network-based Windows API functions, the injected library checks the URL being accessed and under certain conditions, it displays another page to the user through diverse means.
安装程序将驱动程序放到磁盘上,并启动一个服务来执行它。它解密其配置文件,其中包含基于Chromium的目标浏览器和库的列表。如果发现这样的可执行文件正在运行或正在加载,驱动程序会尝试将列出的库之一注入浏览器进程。在钩住基于网络的Windows API函数之后,注入的库检查正在访问的URL,并且在某些条件下,它通过不同的方式向用户显示另一个页面。
The installer 安装程序
The installer we analyzed (SHA-1: 941F0D2D4589FB8ADF224C8969F74633267B2561) is a UPX-compressed file that was uploaded to VirusTotal on 2023-08-26. Figure 9 provides a high-level overview of the driver installation.
我们分析的安装程序(SHA-1:941 F0 D2 D4589 FB 8ADF 224 C8969 F74633267 B2561)是一个UPX压缩文件,于2023-08-26上传到VirusTotal。图9提供了驱动程序安装的高级概述。
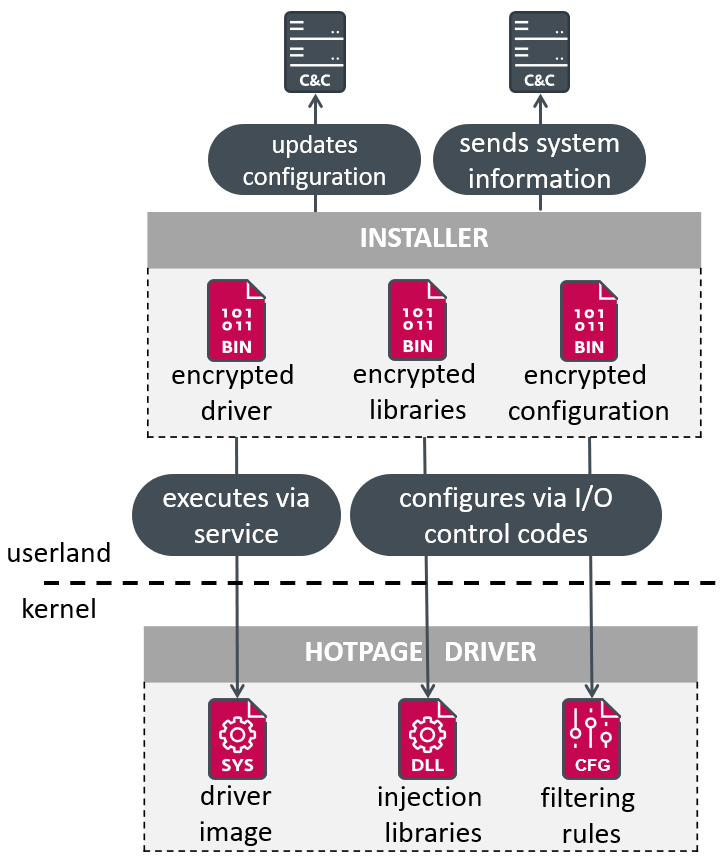
图9.安装程序工作流程概述
The installer contains the encrypted versions (single-byte XOR operation with the key 0xE3) of the driver component, the libraries that will be injected into web browser processes, and three JSON-formatted configuration files:
安装程序包含驱动程序组件的加密版本(密钥为0xE3的单字节XOR操作),将注入Web浏览器进程的库,以及三个JSON格式的配置文件:
- chromedll contains the names of the targeted browser libraries to hook and the targeted functions’ pattern for hooking them,
chromedll包含要挂钩的目标浏览器库的名称和用于挂钩它们的目标函数的模式, - hotPage (unused) contains the list of targeted browsers, allowlists of command line parameters and websites, and the homepage URL that could be used, and
hotPage(未使用)包含目标浏览器列表、命令行参数和网站的允许列表以及可以使用的主页URL, - newtalbe contains filtering rules, an API endpoint to send basic information about the compromised computer, and another one to manage configuration updates.
newtalbe包含过滤规则,一个API端点用于发送有关受损计算机的基本信息,另一个端点用于管理配置更新。
The malware starts by executing the CPUID instruction (see Hypervisor Discovery), to check whether it’s running within a virtualized environment. Then it checks if the driver’s device filename .KNewTableBaseIo exists and if not, it decrypts the driver and stores it in C:WindowsShieldNetWorkBusiness. Its name is a randomly generated 7-character string followed by the .sys extension. A service is created with the file path of the stored driver, and the random string is used as the service name. Since the start type is set to SERVICE_DEMAND_START, the service needs to be explicitly started in order to load the driver. Oddly, this adware doesn’t implement any persistence mechanisms, or at least not in this version.
恶意软件通过执行CPUID指令(参见Hypervisor Discovery)来启动,以检查它是否在虚拟化环境中运行。然后它检查驱动程序的设备文件名.KNewTableBaseIo是否存在,如果不存在,它将解密驱动程序并将其存储在C:WindowsShieldNetWorkBusiness中。它的名称是随机生成的7个字符的字符串,后跟.sys扩展名。使用存储的驱动程序的文件路径创建服务,并将随机字符串用作服务名称。由于启动类型设置为SERVICE_DEMAND_START,因此需要显式启动服务才能加载驱动程序。奇怪的是,这个广告软件没有实现任何持久性机制,或者至少在这个版本中没有。
The installer proceeds to communicate with and configure the driver via its device filename using I/O control codes in the following order:
安装程序继续通过其设备文件名使用I/O控制代码按以下顺序与驱动程序通信并对其进行配置:
- 0x9C4013FC – send the 32-bit hooking library that will be injected into target web browser processes.
0x 9 C4013 FC-发送将注入目标Web浏览器进程的32位挂钩库。 - 0x9C400FFC – send the 64-bit hooking library that will be injected into target web browser processes.
0x 9 C400 FFC-发送64位挂钩库,该库将被注入目标Web浏览器进程。 - 0x9C40173C – send the chromedll configuration.
0x 9 C40173 C-发送chromedll配置。
The installer retrieves the registry key associated with the created service and checks to see if the values IP and port are present. These values are never set by this code so they are presumably created by another component. Without going into the details of the network protocol, the remote server should serve an update of the newtalbe configuration. The communication is encrypted with RC4, using a key derived from the string ID:f~WdH+K?KD)r*sD4mk using the Windows BCryptGenerateSymmetricKey function. Figure 10 shows the content of the configuration file.
安装程序检索与创建的服务关联的注册表项,并检查是否存在IP和port值。这些值从未被此代码设置,因此它们可能是由其他组件创建的。在不深入网络协议细节的情况下,远程服务器应该提供newtalbe配置的更新。通信是用RC 4加密的,使用的密钥来自字符串ID:f~WdH+K?KD)r* sD 4使用Windows BCryptGenerateSymmetricKey函数。图10显示了配置文件的内容。
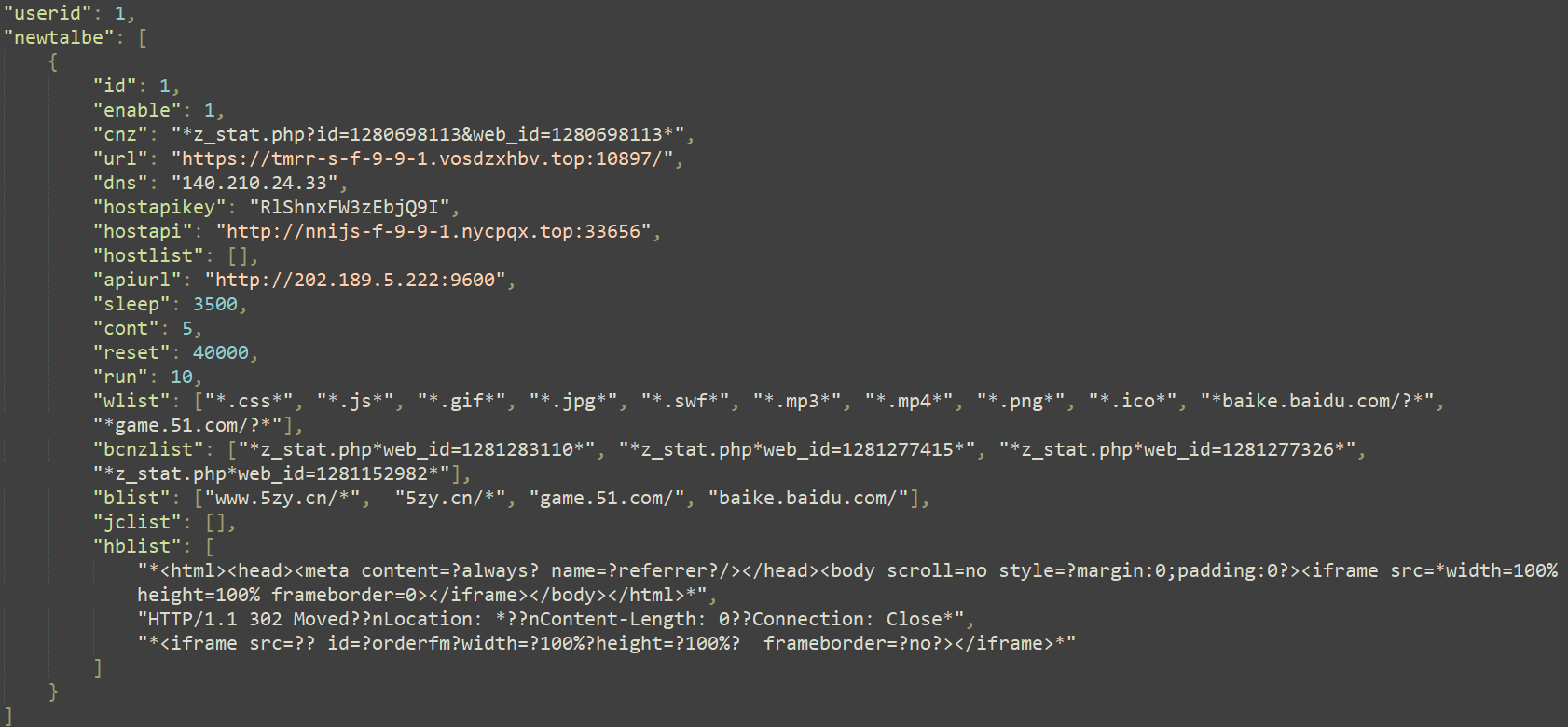
图10.纽塔贝组态
Table 2 describes the important values used from this file, listed in the order that they appear in the configuration file (Figure 10).
表2描述了该文件中使用的重要值,并按照它们在配置文件中出现的顺序列出(图10)。
Table 2. newtalbe configuration description
表2. Newtalbe配置描述
|
Value 值 |
Description 描述 |
|
cnz |
URI pattern matching URLs used to collect statistics when visiting the URL specified by the url value. |
|
url and dns URL和DNS |
If one of the URLs listed in blist is being accessed, a new tab pointing to the url value will be opened. The dns value is IP address of the domain. |
|
hostapikey, hostapi, hostapikey,hostapi, |
The URL value of hostapi is used to update the hostlist, a dictionary comprised of game-related domains along with their corresponding IP addresses. The hostapikey is the decryption key. |
|
apiurl 阿皮乌尔 |
List of endpoints to send information about the compromised computer to. |
|
Wlist, 李斯特, |
Lists of patterns (URI, domains, file extensions, HTML code, and HTTP response headers) to match to apply redirection rules (see the Hooking NtDeviceIoControlFile and inspecting incoming and outgoing data section). |
Using the hostapi URL value of this file, an HTTP GET request is made over TLS with a generic User-Agent string. The received data is decrypted using RC4 with the hostapikey value; it contains a dictionary of gaming-related hostnames with their corresponding resolved address.
使用此文件的hostapi URL值,通过TLS使用通用User-Agent字符串发出HTTP GET请求。接收到的数据使用具有hostapikey值的RC 4进行解密;它包含与游戏相关的主机名及其相应解析地址的字典。
Once these updates are done, the installer sends the updated newtalbe configuration to the driver by issuing an I/O request with the control code 0x9C400BFC
完成这些更新后,安装程序通过发出带有控制代码0x 9 C400 BFC的I/O请求,将更新后的newtalbe配置发送给驱动程序.
Finally, the malware iterates over the list of endpoints provided by the JSON element apiurl and for each one of them it creates a JSON-formatted string containing information about the compromised computer, encrypts it with RC4 using the key Abc123!@#&XM derived via the Windows API BcryptGenerateSymmetricKey, and sends the collected information to the remote server via an HTTP POST request. The collected information includes the computer name, the network interface MAC address, the version of the operating system, and the dimensions of the screen.
最后,恶意软件迭代JSON元素apiurl提供的端点列表,并为每个端点创建包含有关受损计算机信息的JSON格式字符串,使用密钥Abc123!@#& XM通过Windows API BcryptGenerateSymmetricKey派生,并通过HTTP POST请求将收集的信息发送到远程服务器。收集的信息包括计算机名称、网络接口MAC地址、操作系统版本和屏幕尺寸。
Injector driver 喷射器驱动器
The driver’s main purpose is to inject libraries into browser applications and alter their execution flow to change the URL being accessed or open a page in a new tab. Two threads are created to handle requests for opening a new tab and injecting libraries using the publicly available Blackbone project. Additionally, process creation and image loading notification routines are set to monitor newly created processes and executable images being loaded. The simplified logic of the driver is illustrated in Figure 11.
驱动程序的主要目的是将库注入浏览器应用程序,并改变其执行流,以更改正在访问的URL或在新选项卡中打开页面。创建了两个线程来处理打开新选项卡和使用公开可用的Blackbone项目注入库的请求。此外,进程创建和映像加载通知例程被设置为监视新创建的进程和正在加载的可执行映像。驱动程序的简化逻辑如图11所示。
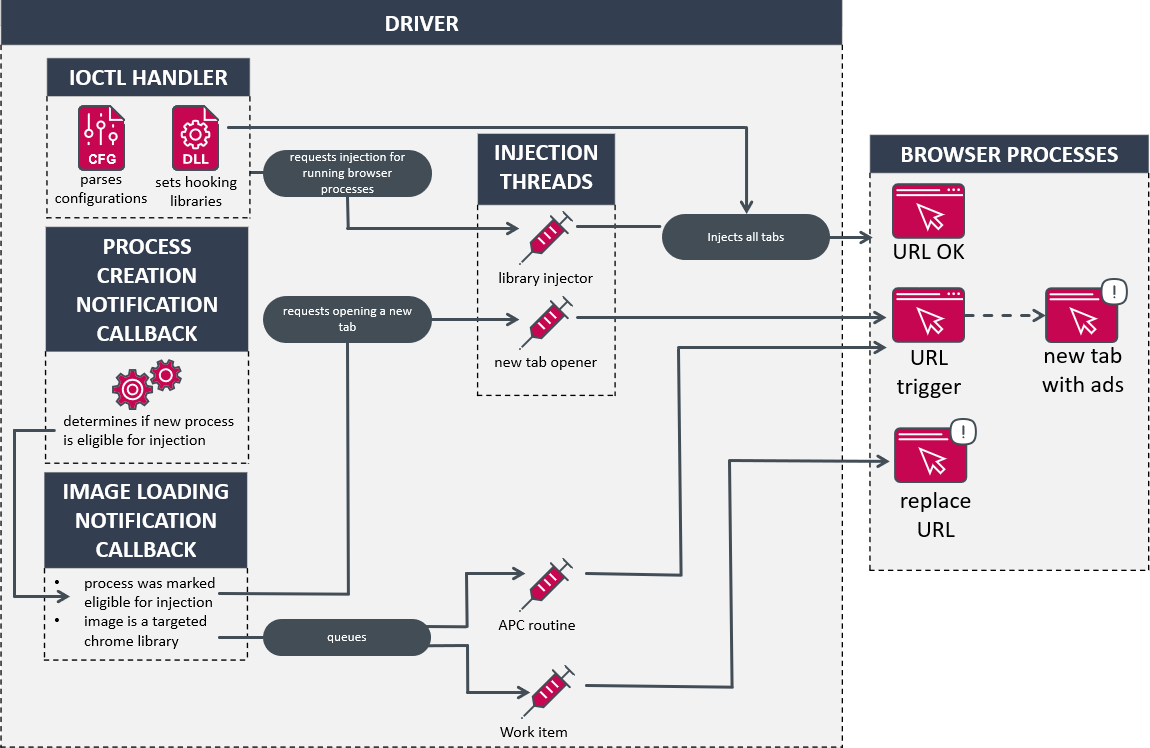
图11.简化的驱动程序逻辑
For an unknown reason, the driver starts by deleting its image from the disk. Afterwards it creates a device object named .KNewTableBaseIo and sets its IRP_MJ_DEVICE_CONTROL routine to handle the various I/O requests listed in Table 3. The control codes (IOCTL) used for configuration or setting the injected libraries can only be called once; therefore the settings cannot be updated. These special control codes are protected by checking that the caller’s file path matches the regular expression *ShieldNetWorkBusinessDwBusiness_*.
由于未知的原因,驱动程序开始从磁盘中删除其映像。然后,它创建一个名为.KNewTableBaseIo的设备对象,并设置其IRP_MJ_DEVICE_CONTROL例程来处理表3中列出的各种I/O请求。用于配置或设置注入库的控制代码(IOCTL)只能调用一次;因此无法更新设置。通过检查调用方的文件路径是否与正则表达式 *ShieldNetWorkBusinessDwBusiness_* 匹配,可以保护这些特殊的控制代码。
Table 3. List of available IOCTLs and their description
表3.可用IOCTL及其描述列表
| IOCTL |
Action 行动 |
|
0x9C400BFC |
Parses the newtalbe configuration passed as an argument. |
|
0x9C400FFC |
Sets the 64-bit library to be injected. |
|
0x9C4013FC |
Sets the 32-bit library to be injected. |
|
0x9C40173C |
Parses the chromedll configuration passed as an argument. |
|
0x9C401EC4 |
Receives a list of browser tabs (processes) to kill. |
|
0x9C4027A8 |
Returns the hotPage configuration. |
|
0x9C4027AC |
Returns the size of the hotPage configuration. |
|
0x9C4027E8 |
Returns the newtalbe configuration. |
|
0x9C4027EC |
Returns the size of the newtalbe configuration. |
|
0x9C4027FC |
Parses the hotPage configuration passed as an argument. |
When handling the control codes 0x9C400BFC and 0x9C40173C, the driver iterates over the loaded modules of all the running processes. If one of the targeted modules listed in the chromedll configuration is found, a request to inject a library into that process is queued.
在处理控制代码0x9C400BFC和0x9C40173C时,驱动程序会遍历所有正在运行的进程的已加载模块。如果找到chromedll配置中列出的目标模块之一,则将向该进程注入库的请求排入队列。
Finally, the driver ends its initialization by creating two threads and setting the notification routines mentioned above.
最后,驱动程序通过创建两个线程并设置上面提到的通知例程来结束其初始化。
It is important to note that the hotPage configuration is never set. Any mentions of this file are solely made to describe how it would be used according to the driver’s control flow. Essentially the hotPage configuration is used to redirect the user to a specific page (or homepage) filled with ads when a targeted browser is launched.
需要注意的是,从未设置过hotPage配置。任何提到这个文件的地方都只是为了描述如何根据驱动程序的控制流来使用它。本质上,hotPage配置用于在目标浏览器启动时将用户重定向到充满广告的特定页面(或主页)。
The version of the software we analyzed relied only on the chromedll and newtalbe configurations to achieve its ad injection.
我们分析的软件版本仅依赖于chromedll和newtalbe配置来实现广告注入。
Library injection thread
库注入线程
This thread checks the queued injection requests, and for each of them, it attaches itself to the targeted process via KeStackAttachProcess, allocates chunks of memory, and copies its shellcode. Using the Blackbone library function ZwCreateThreadEx, the driver calls the shellcode, which implements its own PE loader and calls the entry point of the injected library.
这个线程检查排队的注入请求,对于每个请求,它通过KeStackAttachProcess将自己附加到目标进程,分配内存块,并复制其shellcode。通过使用Blackbone库函数Zwavelet ThreadEx,驱动程序调用shellcode,shellcode实现自己的PE加载器并调用注入库的入口点。
New tab thread 新标签线程
The second thread uses the same logic; however, the injected shellcode is different. It calls the Windows API function CreateProcessW with the command line parameter being the process name of the targeted process concatenated with the URL that should be opened. The latter is made of the URL followed by the sum of the idindex and the userid variables from the hotPage configuration. For instance, the configuration shown in Figure 12 would create the string https://www.hao774[.]com/?90386-00001. Since Chromium-based browsers create a new process for each new tab, creating a process from the browser process will effectively create a new tab.
第二个线程使用相同的逻辑;但是,注入的shellcode不同。它使用命令行参数调用Windows API函数ProcessW,命令行参数是目标进程的进程名,并与应打开的URL连接在一起。后者由URL和hotPage配置中的idindex和userid变量之和组成。例如,图12所示的配置将创建字符串https://www.hao774 [.] com/?90386-00001.由于基于Chromium的浏览器为每个新标签创建一个新进程,因此从浏览器进程创建一个进程将有效地创建一个新标签。
Figure 12 shows the content of the hotPage configuration file.
图12显示了hotPage配置文件的内容。
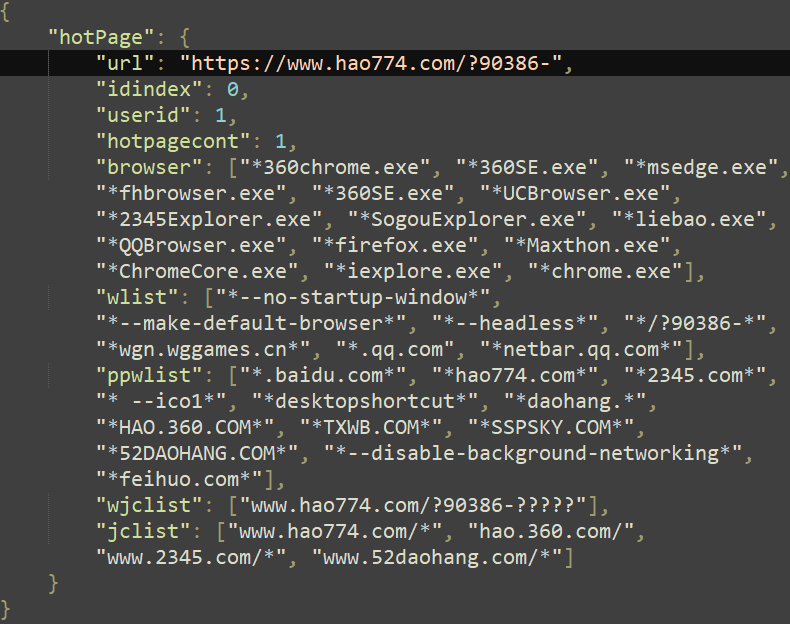
图12. hotPage配置
This configuration file contains the list of targeted web browsers and command line parameters that determine whether the process should be injected. The domain names are either related to gaming ads or internet café maintenance.
此配置文件包含目标Web浏览器和命令行参数的列表,这些参数决定是否应注入进程。这些域名要么与游戏广告有关,要么与网吧维护有关。
Process creation notification routine
进程创建通知例程
Essentially, this routine makes sure the homepage of the new web browser instance is redirected to a specific URL present in the hotPage configuration. This section describes how the driver implements this feature even if it’s not used, since this version of the installer never sends this configuration to the driver.
本质上,这个例程确保新Web浏览器实例的主页被重定向到hotPage配置中的特定URL。本节描述驱动程序如何实现此功能,即使它不使用,因为此版本的安装程序从不将此配置发送到驱动程序。
Depending on the following conditions, the web browser process will be marked as eligible for opening the URL in the hotPage configuration:
根据以下条件,Web浏览器进程将在hotPage配置中被标记为有资格打开URL:
- this is the first instance of the browser and not a new tab being opened,
这是浏览器的第一个实例,而不是正在打开的新选项卡, - the process’s file path matches one of the regular expressions in the browser list in the hotPage configuration,
进程的文件路径与hotPage配置中浏览器列表中的一个正则表达式匹配, - the command line of the process does not match any regular expression in the wlist list of the hotPage configuration, and
进程的命令行不匹配hotPage配置的wlist列表中的任何正则表达式,并且 - if the process’s command line includes its own file path, it must not match any regular expressions in the ppwlist list of the hotPage configuration.
如果进程的命令行包含它自己的文件路径,它不能与hotPage配置的ppwlist列表中的任何正则表达式匹配。
As detailed in the next section, when the browser process starts loading the first executable images, a request to open a new tab is queued. Figure 13 and Figure 14, respectively, show the difference between the legitimate web directory 2345[.]com and the ad-riddled page displayed to the user.
如下一节所述,当浏览器进程开始加载第一个可执行图像时,打开新选项卡的请求将排队。图13和图14分别示出了合法web目录2345[.] com和显示给用户的充满广告的页面。
![Figure 13. Legitimate main page of the web directory 2345[.]com HotPage: Story of a signed, vulnerable, ad-injecting driver](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-13-legitimate-main-page-of-the-web-directory-2345-com.png)
图13.网站目录的合法主页2345[.]网
![Figure 14. Ad-riddled page mimicking the homepage of 2345[.]com HotPage: Story of a signed, vulnerable, ad-injecting driver](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-14-ad-riddled-page-mimicking-the-homepage-of-2345-com.png)
图14.模仿2345主页的广告页面[.]网
Image loading notification routine
图象装入通知程序
This routine essentially handles two types of scenarios. If the image being loaded is in the chromedll list, an APC routine is queued that will load one of the hooking libraries via its own PE loader.
这个例程主要处理两种类型的场景。如果正在加载的图像在chromedll列表中,则APC例程排队,该例程将通过其自己的PE加载器加载其中一个挂钩库。
Otherwise, if the process was marked eligible for opening a new page, the malware achieves this either by opening it in a new tab or in the current one. If the process filename matches one of the regular expressions in the browser1 list of the hotPage configuration, a request to open a new tab is queued and will be handled by the appropriate thread (note that the browser1 list element was not present in the configuration file we retrieved). In the other case, the page will be opened in the tab being created by queuing a work item (via IoQueueWorkItemEx) that will modify the command line of the process being created. The latter attaches itself to the process, finds the export address of GetCommandLineA and GetCommandlineW inside the kernelbase.dll library, and modifies the Unicode string stored in BaseAnsiCommandLine. The command line is replaced with the process’s executable file path concatenated with the URL in the hotPage configuration. Figure 15 shows a side-by-side comparison of the code responsible for finding the command line buffer and the disassembly of the GetCommandLineA function.
否则,如果进程被标记为有资格打开新页面,恶意软件将通过在新选项卡或当前选项卡中打开它来实现这一点。如果进程文件名与hotPage配置的browser1列表中的一个正则表达式匹配,则打开新选项卡的请求将排队,并由相应的线程处理(注意,browser1列表元素不存在于我们检索的配置文件中)。在另一种情况下,页面将在正在创建的选项卡中打开,方法是将一个工作项(通过IoCineWorkItemEx)排队,该工作项将修改正在创建的流程的命令行。后者将自身附加到进程,在kernelbase.dll库中查找GetCommandLineA和GetCommandlineW的导出地址,并修改BaseAnsiCommandLine中存储的Unicode字符串。命令行被替换为进程的可执行文件路径,该路径与hotPage配置中的URL连接在一起。 图15显示了负责查找命令行缓冲区的代码和GetCommandLineA函数的反汇编代码的并排比较。
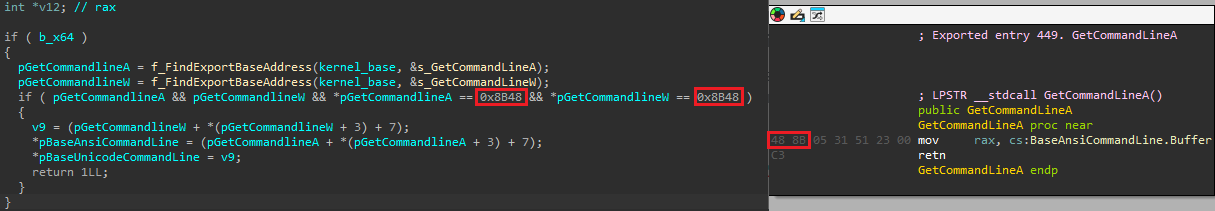
图15.查找命令行缓冲区的函数(左)和GetCommandlineA函数的反汇编(右)
Injected library 注入库
The first thing that the injected library does is to retrieve the hotPage and newtalbe configurations by querying the driver. If the injected browser filename is 360Chrome, it deletes the registry key HKCUSoftware360chromeHomepage and patches the Preferences file (located under the browser’s default directory 360chromechromeUser DataDefaultPreferences) to make the homepage point to the URL value of the hotPage configuration.
注入的库所做的第一件事是通过查询驱动程序来检索hotPage和newtalbe配置。如果被注入的浏览器文件名是360Chrome,它会删除注册表项hksoftware360chromeHomepage,并修补Preferences文件(位于浏览器的默认目录360chromechromeUser DataDefaultPreferences下),使主页指向hotPage配置的URL值。
Using the Microsoft Detours hooking library, the sample hooks SetProcessMitigationPolicy to make it return 1 in order to prevent security policies from being applied to the process, thereby allowing code injection. Then getaddrinfo is hooked to force the browser to resolve certain hostnames to specific IP addresses to ensure the redirection is made to the right server in case the domain names do not exist anymore.
使用Microsoft Detours挂钩库,该示例挂钩SetProcessMitigationPolicy,使其返回1,以防止安全策略应用于进程,从而允许代码注入。然后,getaddrinfo被挂接,以强制浏览器将某些主机名解析为特定的IP地址,以确保在域名不再存在的情况下重定向到正确的服务器。
Hooking SSL_read and SSL_write
连接SSL_read和SSL_write
The malware hooks the SSL_read and SSL_write functions to allow the manipulation of the browser’s decrypted TLS traffic; it does so by searching for specific patterns inside the loaded modules, since these functions are not exported. For instance, the chromewrite dictionary inside the chromedll configuration contains two types of patterns, sslcode and oldchrome, as seen in Figure 16. They are, respectively, used for finding newer and older versions of the DoPayloadWrite function. We tested and confirmed that the patterns match the Microsoft Edge library msedge.dll version 122.0.2365.80.
恶意软件挂钩SSL_read和SSL_write函数以允许操纵浏览器的解密TLS流量;它通过搜索加载模块内的特定模式来实现这一点,因为这些函数不会导出。例如,chromedll配置中的chromewrite字典包含两种模式,sslcode和oldchrome,如图16所示。它们分别用于查找DoPayloadWrite函数的新版本和旧版本。我们测试并确认模式与微软Edge库msedge.dll版本122.0.2365.80匹配。
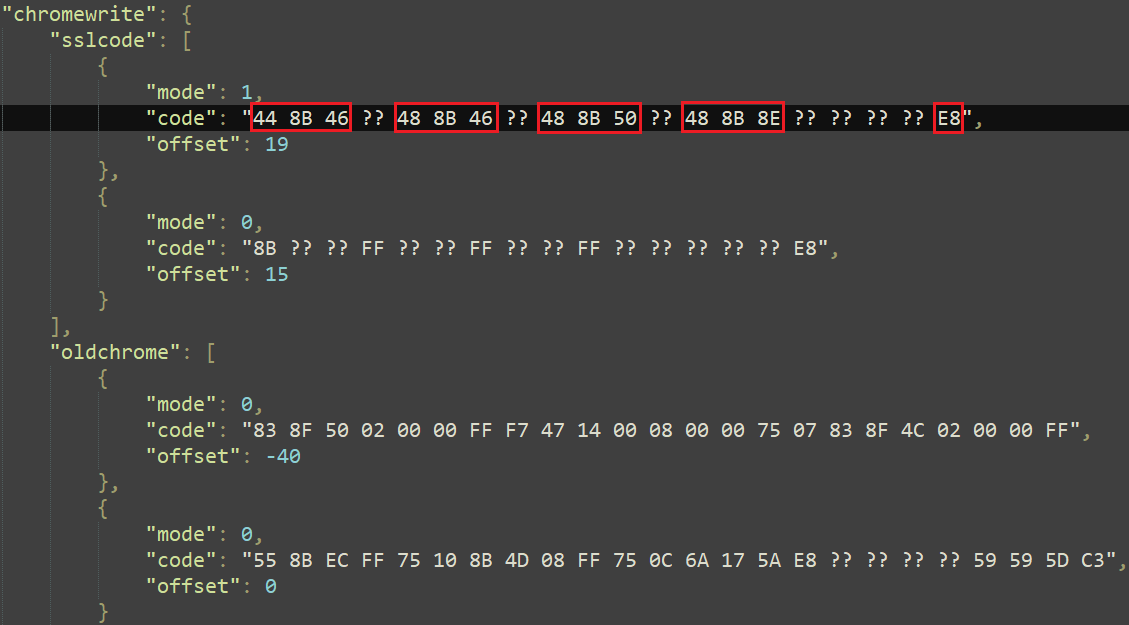
图16.用于查找DoPayloadWrite函数的模式
The mode value is used to determine the version of the pattern, either 32-bit or 64-bit; the code value is the actual byte pattern, and the offset is the distance from the start of the pattern to the pointer to the SSL_write function (see Figure 17).
模式值用于确定模式的版本,是32位还是64位;代码值是实际的字节模式,偏移量是从模式的开始到指向SSL_write函数的指针的距离(参见图17)。
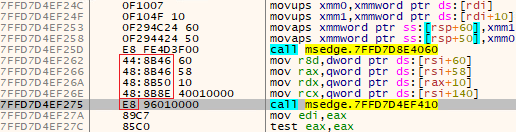
图17.查找指向SSL_write函数的指针
Once SSL_write and SSL_read are found, they are hooked using the Detours library. For the former, the malware inspects the data and then calls the original function, which encrypts and sends it. As for the latter, the injected library does the opposite in order to manipulate decrypted data. For both functions, the data is inspected by the code that respectively handles the AFD_SEND and AFD_RECV control codes in the function hooking NtDeviceIoControlFile.
一旦找到SSL_write和SSL_read,就可以使用Detours库将它们挂钩。对于前者,恶意软件检查数据,然后调用原始函数,加密并发送数据。至于后者,注入的库则相反,以操纵解密的数据。对于这两个函数,数据由分别处理挂接NtDeviceIoControlFile的函数中的AFD_SEND和AFD_RECV控制代码的代码检查。
Hooking NtDeviceIoControlFile and inspecting incoming and outgoing data
挂接NtDeviceIoControlFile并检查传入和传出数据
The malicious library hooks the NtDeviceIoControlFile function to handle specific IOCTL codes as seen in Figure 18.
恶意库挂钩NtDeviceIoControlFile函数来处理特定的IOCTL代码,如图18所示。
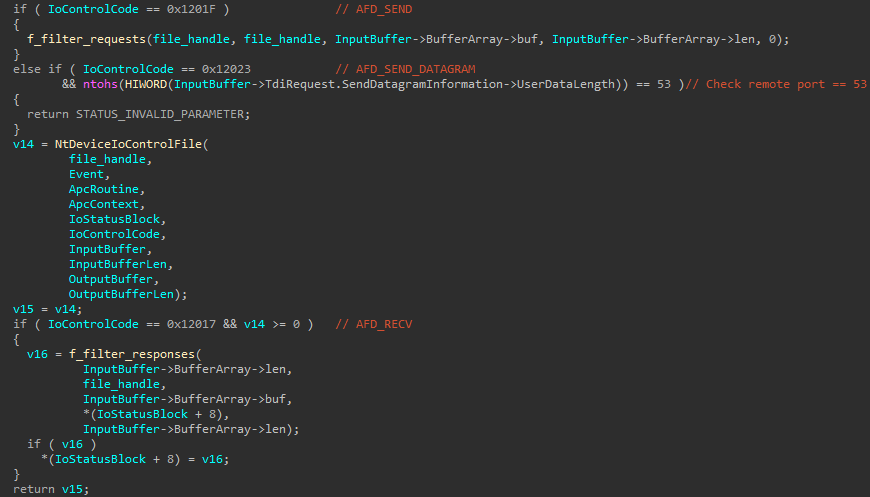
图18. NtDeviceIoControlFile API函数的钩子例程
For the control code 0x12023 (AFD_SEND_DATAGRAM used when sending UDP packets), the malware cancels any DNS requests by returning STATUS_INVALID_PARAMETER if the remote port number is 53. This ensures that the web browser only uses the hosts provided by the newtalbe configuration.
对于控制代码0x12023(发送UDP数据包时使用的AFD_SEND_DATAGRAM),如果远程端口号为53,则恶意软件通过返回STATUS_INVALID_PARAMETER来取消任何DNS请求。这样可以确保Web浏览器只使用newtalbe配置提供的主机。
The routine that handles the control code 0x1201F (AFD_SEND) starts by extracting the URL and the Referrer header from the request. Based on the URL matching certain values in the newtalbe and hotPage configurations, the malware performs assorted actions, as described in Table 4. In some cases, the request is sent but the response is modified in the routine handling the AFD_RECV control code by different redirection methods explained afterwards.
处理控制代码0x1201F(AFD_SEND)的例程首先从请求中提取URL和Referrer头。基于URL匹配newtalbe和hotPage配置中的某些值,恶意软件执行各种操作,如表4所示。在某些情况下,请求被发送,但响应在处理AFD_RECV控制代码的例程中通过稍后解释的不同重定向方法被修改。
Table 4. List of actions performed under certain conditions when sending HTTP requests
表4.发送HTTP请求时在特定条件下执行的操作列表
|
Configuration 配置 |
Matching value 匹配值 |
Action 行动 |
|
newtalbe 纽塔尔贝 |
cnz |
Sends info about the compromised computer to the apiurl (similar to the end of the installer). |
|
hotPage |
whomepage |
Increases internal homepage hit counter. |
|
hotPage |
wjclist 韦克利斯特 |
Sends the data without any modifications. |
|
newtalbe 纽塔尔贝 |
url or wlist url或wlist |
Sends the data without any modifications. |
|
newtalbe 纽塔尔贝 |
blist b列表 |
Sends the data but modifies the response using redirection method 0. The response is opened in a new browser tab. |
|
newtalbe 纽塔尔贝 |
jclist |
Sends the data but modifies the response using redirection method 1. |
|
newtalbe 纽塔尔贝 |
bcnzlist |
Sends the data but modifies the response using redirection method 2. |
|
hotPage |
jclist |
Sends the data but modifies the response using redirection method 3. |
For control code 0x12017 (AFD_RECV), the malware first retrieves the data received by the client and checks if the response was marked eligible for redirection. There are four types of redirections as described in Table 5. The xxx string in the modified response is changed for the URL in the newtalbe configuration.
对于控制代码0x 12017(AFD_RECV),恶意软件首先检索客户端接收的数据,并检查响应是否标记为符合重定向条件。有四种类型的重定向,如表5所示。修改后的响应中的xxx字符串将针对newtalbe配置中的URL进行更改。
Table 5. Redirection methods
表5.重定向方法
|
Redirection method 重定向方法 |
Modified response 修改的响应 |
Description 描述 |
| 0 |
HTTP/1.1 302 Moved Temporarily Server: nginx 服务器:nginx Content-Type: text/html Content-Type:text/html Connection: close Connection:close Location: xxx 地点:xxx |
Redirect the user to another page using the HTTP code 302; an internal redirection counter is incremented. |
| 1 |
<html><head><meta charset=”utf-8″><meta content=”always” name=”referrer”></head><body scroll=no style=”margin:0;padding:0″><iframe src=”xxx” width=100% height=100% frameborder=0></iframe></body></html> |
Replace the content of the current page with an iframe pointing to a new URL. |
| 2 |
location.replace(“xxx”) location.replace(“xxx”) |
Redirect the current page using the replace method of the Location interface. |
| 3 |
HTTP/1.1 302 Moved Temporarily Server: nginx 服务器:nginx Content-Type: text/html Content-Type:text/html Connection: close Connection:close Location: xxx 地点:xxx |
Same as redirection 0 but the redirection counter is not incremented. |
Figure 19 illustrates redirection method 0 being applied after navigating to a URL matching one of the blist URL patterns of the newtalbe configuration (www.5zy[.]cn). Another tab is opened and points to the url specified in the same configuration.
图19示出了在导航到与newtalbe配置的blist URL模式之一匹配的URL(www.5zy[.] cn)。另一个选项卡将打开并指向同一配置中指定的url。
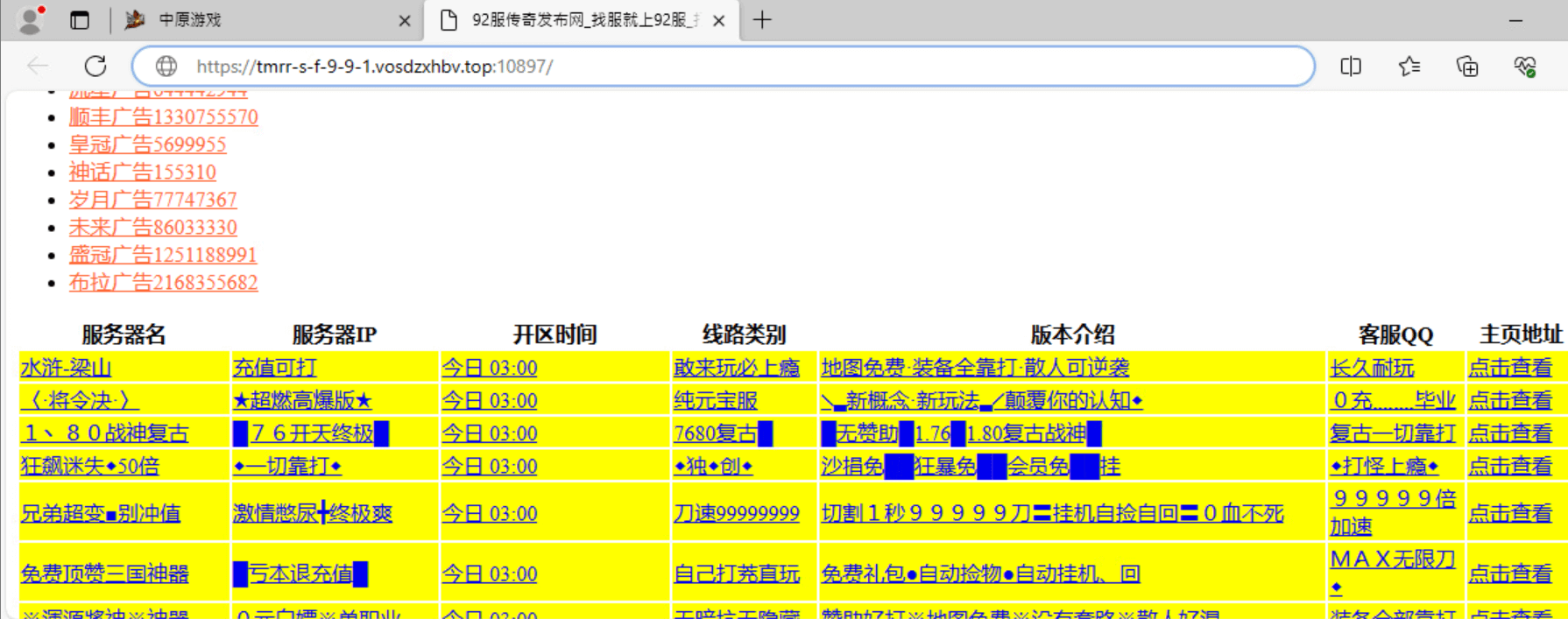
图19.重定向方法% 0
Security issues and privilege escalation
安全问题和权限升级
When initializing its device object, the driver does not specify any access control lists (ACLs) to restrict who can communicate with it; therefore, anyone can send I/O requests to it. As mentioned previously, some I/O control codes require the requesting process to be in a path matching the regex:
当初始化设备对象时,驱动程序不指定任何访问控制列表(Access Control List,简称ACL)来限制谁可以与它通信;因此,任何人都可以向它发送I/O请求。如前所述,一些I/O控制代码要求请求进程位于与正则表达式匹配的路径中:
*ShieldNetWorkBusinessDwBusiness_*
This is clearly not sufficient to check whether the communicating process is one of the HotPage components and can easily be bypassed by creating the required directories under a user-writable folder.
这显然不足以检查通信进程是否是HotPage组件之一,并且可以通过在用户可写的文件夹下创建所需的目录来轻松绕过。
We came up with two scenarios that would allow a user with the HotPage driver running on their system to run code as the NT AUTHORITYSystem account. We created a proof-of-concept (PoC) script in Python to achieve both scenarios.
我们提出了两个场景,允许在系统上运行HotPage驱动程序的用户以NT客户端系统帐户运行代码。我们在Python中创建了一个概念验证(proof-of-concept,缩写为PROC)脚本来实现这两个场景。
Scenario #1: Privilege escalation via arbitrary DLL injection in arbitrary processes
场景#1:通过在任意进程中注入任意DLL来升级开销
In this first scenario, we assume that the driver was loaded but that the chromedll configuration and the libraries to inject it were not set. In that case, it is possible to create and set our own library to inject. We created a small library that would simply log the PID of the injected process, whether it is running with administrator privileges, and the injected process’s file path.
在第一个场景中,我们假设驱动程序已经加载,但是chromedll配置和注入它的库还没有设置。在这种情况下,可以创建并设置我们自己的库来注入。我们创建了一个小的库,它将简单地记录注入进程的PID,无论它是否以管理员权限运行,以及注入进程的文件路径。
As seen in the screenshot of the log file in Figure 20, a lot of processes were injected with our library including processes with administrator privileges.
如图20中日志文件的屏幕截图所示,我们的库中注入了很多进程,包括具有管理员权限的进程。
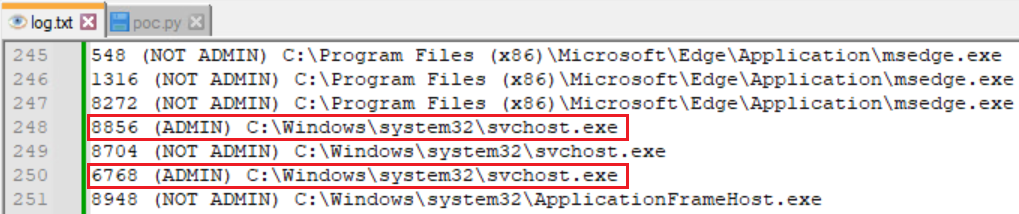
图20.我们注入的库的日志文件
It should be noted, however, that protected processes cannot be injected using this technique.
然而,应该注意的是,受保护的进程不能使用这种技术注入。
Scenario #2: Privilege escalation via changing the command line of newly created processes
场景#2:通过更改新创建的进程的命令行来进行升级
In the first scenario, we relied on the fact that both the injected libraries and the chromedll configuration were not set, but, as seen in the installer analysis, they are both set as soon as the driver is initially loaded. However, the hotPage configuration never gets set. Based on the control flow analysis, we devised a way to leverage the driver’s process creation and image loading notification routines’ logic to execute the same executable again but with a different command line.
在第一个场景中,我们依赖于这样一个事实,即注入的库和chromedll配置都没有设置,但是,正如安装程序分析中所看到的那样,它们都在驱动程序最初加载时设置。但是,hotPage配置永远不会设置。基于控制流分析,我们设计了一种方法来利用驱动程序的进程创建和图像加载通知例程的逻辑,再次执行相同的可执行文件,但使用不同的命令行。
Under certain conditions, as explained in the Process creation notification routine and Image loading notification routine sections, the driver can open a new tab pointing to the URL present in the hotPage configuration. This is achieved either by replacing the command line of the newly created browser process or by duplicating the browser process and changing its command line to the URL in the hotPage configuration. If we specify which process can be duplicated and the new command line, we can achieve privilege escalation by targeting a process with SYSTEM privileges, for instance.
在某些情况下,如进程创建通知例程和映像加载通知例程部分所述,驱动程序可以打开一个新选项卡,指向hotPage配置中存在的URL。这可以通过替换新创建的浏览器进程的命令行或复制浏览器进程并将其命令行更改为hotPage配置中的URL来实现。例如,如果我们指定可以复制哪个进程和新的命令行,我们可以通过以具有SYSTEM权限的进程为目标来实现权限提升。
Conclusion 结论
The analysis of this rather generic-looking piece of malware has proven, once again, that adware developers are still willing to go the extra mile to achieve their goals. Not only that, these have developed a kernel component with a large set of techniques to manipulate processes, but they also went through the requirements imposed by Microsoft to obtain a code-signing certificate for their driver component.
对这个看起来相当普通的恶意软件的分析再次证明,广告软件开发人员仍然愿意付出额外的努力来实现他们的目标。不仅如此,他们还开发了一个内核组件,其中包含大量操作进程的技术,而且他们还通过了微软提出的要求,为他们的驱动程序组件获得代码签名证书。
The HotPage driver reminds us that abusing Extended Verification certificates is still a thing. As a lot of security models are at some point based on trust; threat actors are inclined to play along the line between legitimate and shady. Whether such software is advertised as a security solution or simply bundled with other software, the capabilities granted thanks to this trust expose users to security risks.
HotPage驱动程序提醒我们,滥用扩展验证证书仍然是一件事。由于许多安全模型在某种程度上都是基于信任的;威胁行为者倾向于在合法和可疑之间沿着。无论此类软件是作为安全解决方案宣传,还是与其他软件捆绑在一起,这种信任所授予的功能都会使用户面临安全风险。
As annoying as adware can be, the vulnerabilities introduced by this malware leave the system open to even more dangerous threats. An attacker with a non-privileged account could leverage the vulnerable driver to obtain SYSTEM privileges or inject libraries into remote processes to cause further damage, all while using a legitimate and signed driver.
尽管广告软件很烦人,但这种恶意软件引入的漏洞会使系统面临更危险的威胁。具有非特权帐户的攻击者可以利用易受攻击的驱动程序获取SYSTEM特权或将库注入远程进程以造成进一步的损害,而所有这些都是使用合法和签名的驱动程序。
ESET technologies detect this threat – which Microsoft removed from the Windows Server Catalog on May 1st, 2024 – as Win{32|64}/HotPage.A and Win{32|64}/HotPage.B.
ESET技术将此威胁(Microsoft于2024年5月1日从Windows Server目录中删除)作为Win{32| 64}/HotPage.A和Win{32| 64}/HotPage.B.
For any inquiries about our research published on WeLiveSecurity, please contact us at [email protected]
有关我们在WeLiveSecurity上发表的研究的任何查询,请通过[email protected]与我们联系ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
ESET Research提供私人APT情报报告和数据馈送。有关此服务的任何查询,请访问ESET威胁情报页面。
IoCs
Files 文件
| SHA-1 |
Filename FileName文件 |
Detection |
Description 描述 |
| 0D1D298A3EBCA4ECE0BA 52828DD3B7676D884E7F |
N/A |
Win64/HotPage.B |
HotPage driver. HotPage驱动程序。 |
| DDD82422D418FC8E8748 BCC7BD2E2BC468124A6B |
N/A |
Win32/HotPage.B |
32-bit HotPage hooking library. |
| D5D646B052E8B2572399 1CB4CAB51CB2F9D55906 |
N/A |
Win64/HotPage.A |
64-bit HotPage hooking library. |
| 941F0D2D4589FB8ADF22 4C8969F74633267B2561 |
Hotpage.exe |
Win32/HotPage.A |
HotPage installer. HotPage安装程序。 |
Network 网络
| IP |
Domain 域 |
Hosting provider 托管服务提供商 |
First seen 第一次看到 |
Details |
|
61.147.93[.]49 61.147.93[.] 49 |
nnijs-f-9-9-1.nycpqx[.]top |
CHINATELECOM JiangSu YangZhou IDC. |
2023-10-06 |
Server used to obtain a list of game-related domains with their corresponding IP addresses. |
|
140.210.24[.]33 140.210.24[.] 33 |
tmrr-s-f-9-9-1.vosdzxhbv[.]top |
CHINATELECOM JiangSu YangZhou IDC. |
2023-10-06 |
Compromised users are redirected to this web server that hosts ad-riddled pages. |
|
202.189.5[.]222 202.189.5[.] 222 |
N/A |
Shandong eshinton Network Technology Co., Ltd. |
2023-10-06 |
Former DwAdsafe domain used to collect information about installations. |
MITRE ATT&CK techniques MITRE ATT&CK技术
This table was built using version 15 of the MITRE ATT&CK framework.
此表是使用MITRE ATT&CK框架版本15构建的。
|
Tactic 战术 |
ID |
Name 名称 |
Description 描述 |
|
Resource Development 资源开发 |
T1588.003 |
Obtain Capabilities: Code Signing Certificates |
DwAdsafe’s driver is signed with a valid code-signing certificate. |
|
Execution 执行 |
T1204.002 |
User Execution: Malicious File |
The installer component is an executable application. |
| T1569.002 |
System Services: Service Execution |
DwAdsafe’s driver is loaded by creating a service. |
|
|
Persistence 持久性 |
T1574.013 |
Hijack Execution Flow: KernelCallbackTable |
DwAdsafe’s driver installs kernel callbacks to monitor loaded images and process creation. |
|
Defense Evasion 防御规避 |
T1055.004 |
Process Injection: Asynchronous Procedure Call |
DwAdsafe’s driver can use APC as an injection method. |
| T1553.002 |
Subvert Trust Controls: Code Signing |
DwAdsafe’s driver is signed with a valid code-signing certificate. |
|
| T1140 |
Deobfuscate/Decode Files or Information |
The embedded configuration files are encrypted. |
|
| T1055.001 |
Process Injection: Dynamic-link Library Injection |
DwAdsafe can hijack web browser processes’ control flow by injecting DLLs. |
|
| T1027.009 |
Obfuscated Files or Information: Embedded Payloads |
DwAdsafe’s driver and hooking libraries are embedded inside the installer. |
|
| T1070.004 |
Indicator Removal: File Deletion |
DwAdsafe’s driver deletes itself from disk. |
|
| T1027.002 |
Obfuscated Files or Information: Software Packing |
DwAdsafe’s installer is packed with UPX. |
|
|
Discovery 发现 |
T1033 |
System Owner/User Discovery |
DwAdsafe’s installer and the hooking libraries collect the victim’s username. |
|
Collection 收集 |
T1185 |
Browser Session Hijacking |
DwAdsafe’s hooking libraries can intercept and tamper with network traffic inside web browser processes. |
|
Command and Control 指挥和控制 |
T1071.001 |
Application Layer Protocol: Web Protocols |
The HTTP protocol is used to send collected information about the user and computer to the C&C. |
| T1573.001 |
Encrypted Channel: Symmetric Cryptography |
The RC4 encryption algorithm is used for encrypting communication with the C&C. |
|
|
Impact 影响 |
T1565.002 |
Data Manipulation: Transmitted Data Manipulation |
DwAdsafe’s hooking libraries can intercept and tamper with network traffic inside web browser processes. |
原文始发于ESET-welivesecurity:HotPage: Story of a signed, vulnerable, ad-injecting driver
转载请注明:HotPage: Story of a signed, vulnerable, ad-injecting driver | CTF导航