原文始发于Dragos:CHERNOVITE’s PIPEDREAM Malware Targeting Industrial Control Systems (ICS)
CHERNOVITE’s PIPEDREAM Malware Targeting Industrial Control Systems (ICS)

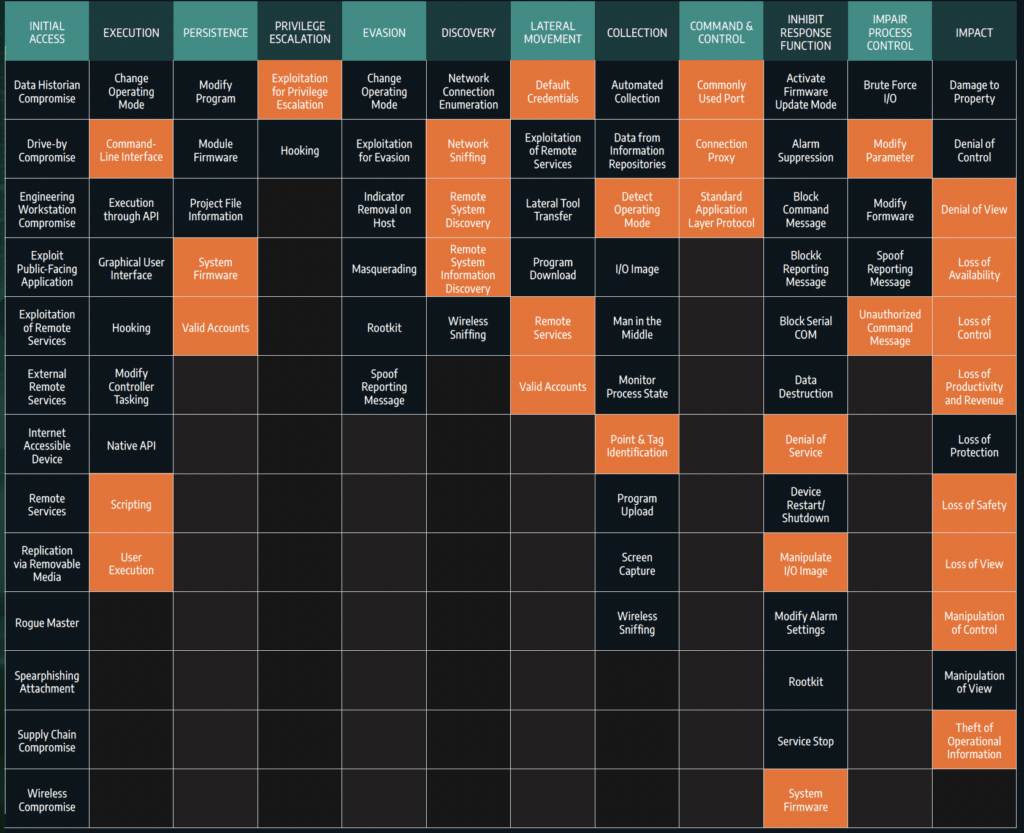
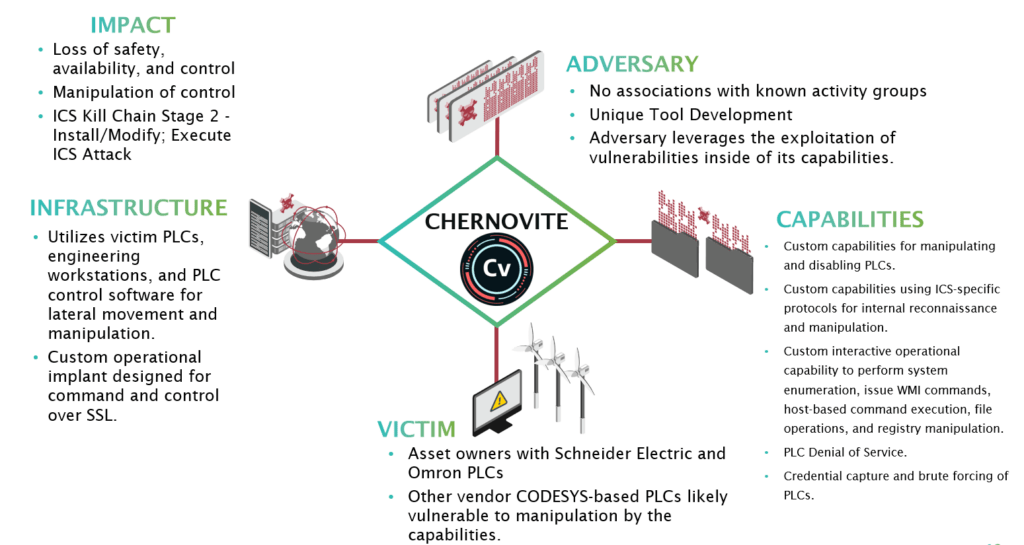
PIPEDREAM can execute 38 percent of known ICS attack techniques and 83 percent of known ICS attack tactics.1 PIPEDREAM can manipulate a wide variety of industrial control programmable logic controllers (PLC) and industrial software, including Omron and Schneider Electric controllers, and can attack ubiquitous industrial technologies including CODESYS, Modbus, and Open Platform Communications Unified Architecture (OPC UA). Together, PIPEDREAM can affect a significant percentage of industrial assets worldwide. PIPEDREAM is not currently taking advantage of any Schneider or Omron vulnerabilities, instead it leverages native functionality.
While CHERNOVITE is specifically targeting Schneider Electric and Omron PLCs, there could be other modules targeting other vendors as well, and PIPEDREAM’s functionality could work across hundreds of different controllers. Said simply, a focus on the equipment vendor is misplaced, and instead the focus should be placed on the tactics and techniques the adversary is leveraging.
PIPEDREAM accomplishes this far-reaching impact through a series of five components that Dragos labels:
- EVILSCHOLAR
- BADOMEN
- DUSTTUNNEL
- MOUSEHOLE
- LAZYCARGO
These combined components allow CHERNOVITE to enumerate an industrial environment, infiltrate engineering workstations, exploit process controllers, cross security and process zones, fundamentally disable controllers, and manipulate executed logic and programming. All of these capabilities can lead to a loss of safety, availability, and control of an industrial environment, dramatically increasing time-to-recovery, while potentially placing lives, livelihoods, and communities at risk.
Due to the historic and expansive nature of PIPEDREAM, mitigating the CHERNOVITE threat will require a robust strategy, and not simply applying cybersecurity fundamentals. Dragos recommends the following defensive mitigations.
Recommendations
- Monitor industrial environments for all threat behaviors in the MITRE ATT&CK for ICS matrix as adversaries are increasing their scope and scale of capabilities.
- Ensure ICS visibility and threat detection include all ICS North-South and East-West communications — network edge and perimeter monitoring are insufficient for PIPEDREAM.
- Maintain knowledge and control of all assets within Operational Technology (OT) environments, including details such as ensuring only known-good firmware and controller configuration files are in use.
- Utilize a fully researched and rehearsed industrial incident response plan that includes attempts by adversaries to deny, disrupt, and destroy processes ensuring an extended time-to-recovery.
CHERNOVITE Diamond Model Diagram
Get the complete analysis
References
1 As measured against the MITRE ATT&CK for ICS malicious behavior matrix.
转载请注明:CHERNOVITE’s PIPEDREAM Malware Targeting Industrial Control Systems (ICS) | CTF导航